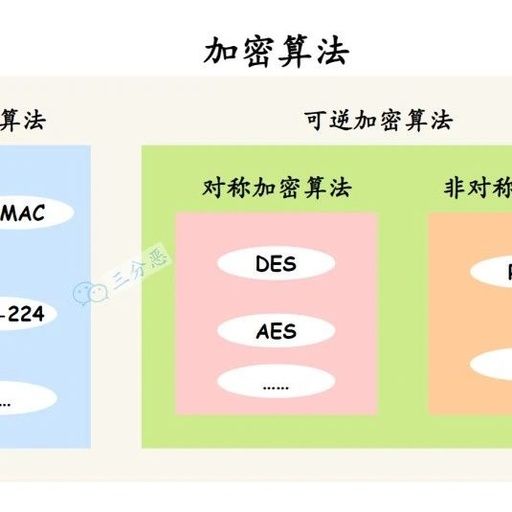
Performance Analysis of Data Encryption Algorithms
This article compares the performance of four commonly used encryption algorithms: DES, 3DES, Blowfish, and AES (Rijndael). By running several encryption settings to process data blocks of different sizes, the encryption/decryption speed of the algorithms is evaluated and compared. The simulation is performed using C#. Keywords: encryption algorithms, performance, analysis, AES, DES, Blowfish, TripleDES, cryptography … Read more