The previous article in this series discussed the “Necessity Analysis of Quantum Communication Engineering.” It inferred, through the introduction of two important papers and an analysis of the latest advancements in quantum computing, that public key cryptography will remain sufficiently secure for a considerable period in the future. Therefore, hastily promoting “quantum communication” engineering projects lacks necessity. This article focuses on the analysis of the networking technology of “quantum communication,” further pointing out that the engineering of “quantum communication” currently lacks the feasibility for technical implementation, which is the main reason why it is difficult for “quantum communication” engineering to have practical applications in network communication security.
First, let’s introduce the basic working principles of modern communication networks. When two computers transmit data to each other, a communication line must be established between them, as shown in Figure 1. If five computers need to transmit data to each other, a communication line must be established between each pair, totaling 10 lines, as shown in Figure 2. If there are N computers that need to transmit data to each other, how many communication lines need to be established? This is known as a combinatorial problem in mathematics, with the total number of communication lines given by: N*(N-1)/2. When N is 10,000, the total number of lines needed is approximately 50 million. Today, the number of computers, smartphones, and various digital devices on the internet has reached billions, making the pairwise connection method shown in Figure 2 absolutely impractical.
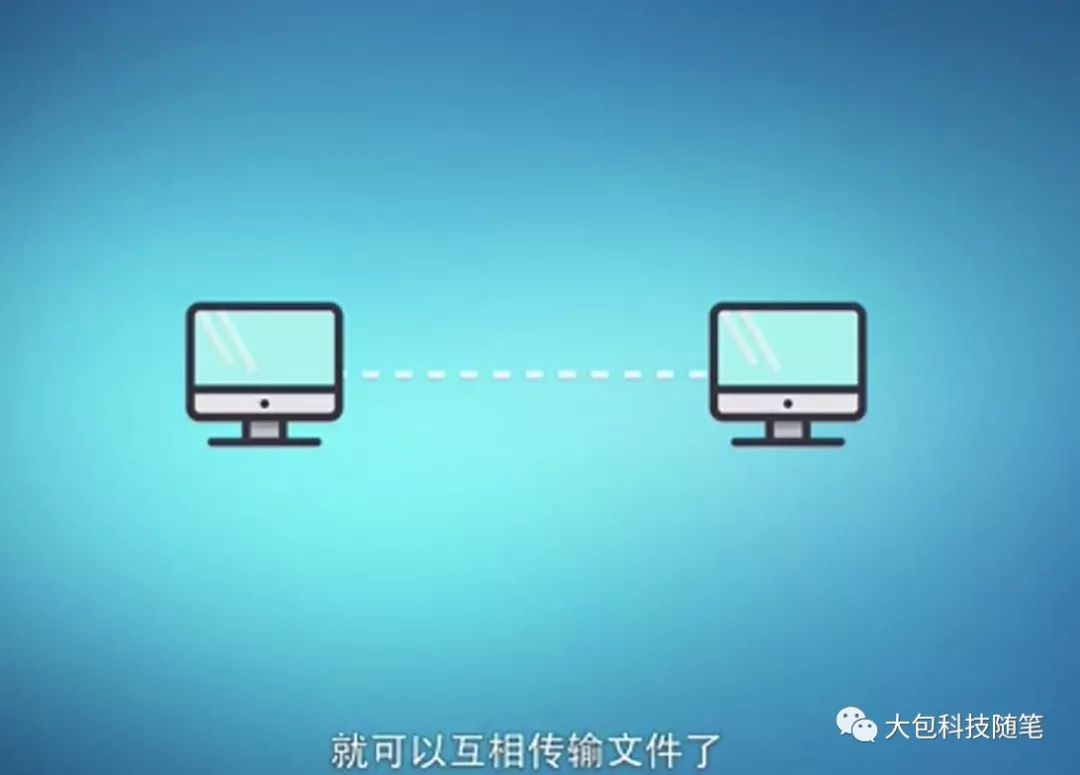
Figure 1
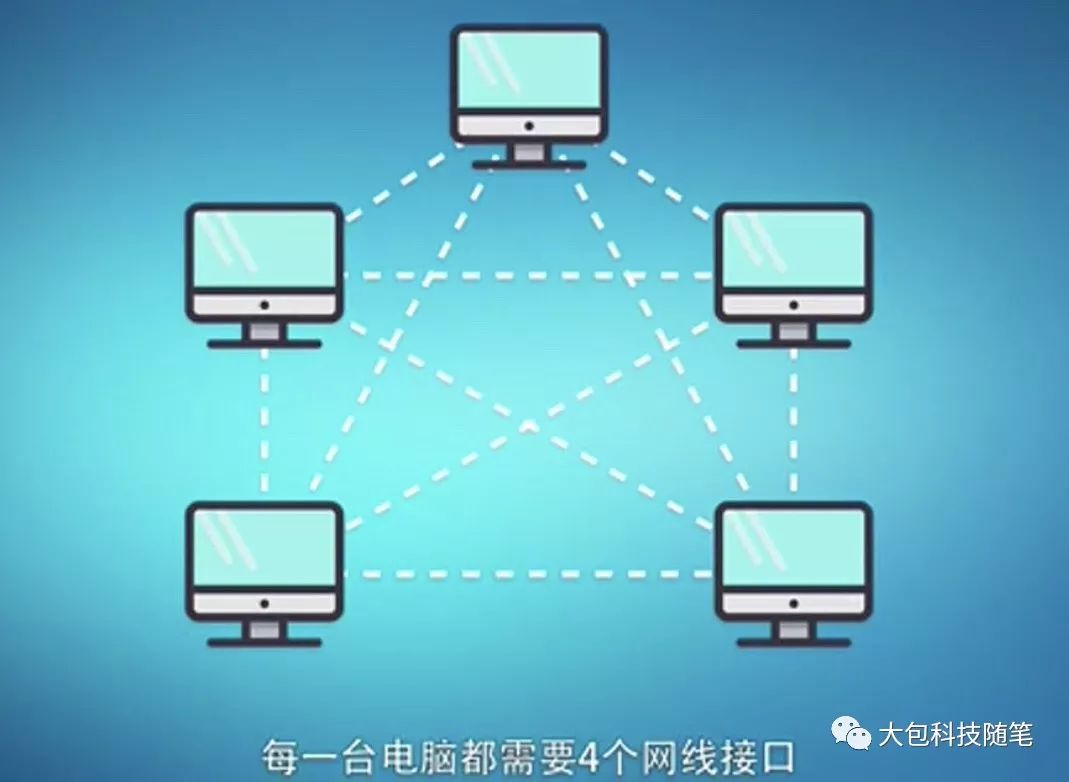
Figure 2
To solve the connection problem of numerous computers communicating with each other, various network structures must be introduced. For example, the star network shown in Figure 3 can connect five computers, reducing the total number of communication lines from 10 to 5, and reducing the number of network interfaces for each computer to one. While this star network reduces the number of communication lines, it increases the need for a network device, which is the data switch or router located in the center of Figure 3. When many devices are connected and the distances are far, it is essential to add network devices to reduce the total number of connection lines.
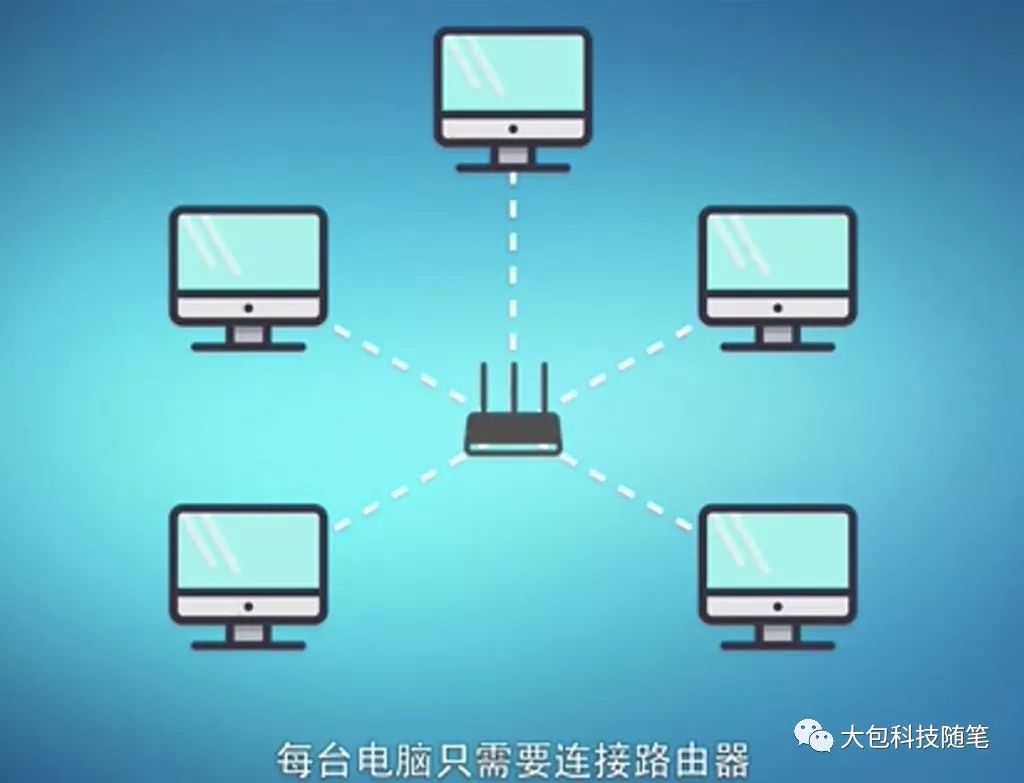
Figure 3
Furthermore, we can connect two distant star networks with a single communication line, allowing any two computers between them to transmit data, as shown in Figure 4. Further, internet service providers can connect four star local area networks into part of the internet using four communication lines and a router, enabling any two computers on this network to communicate with each other, as shown in Figure 5.
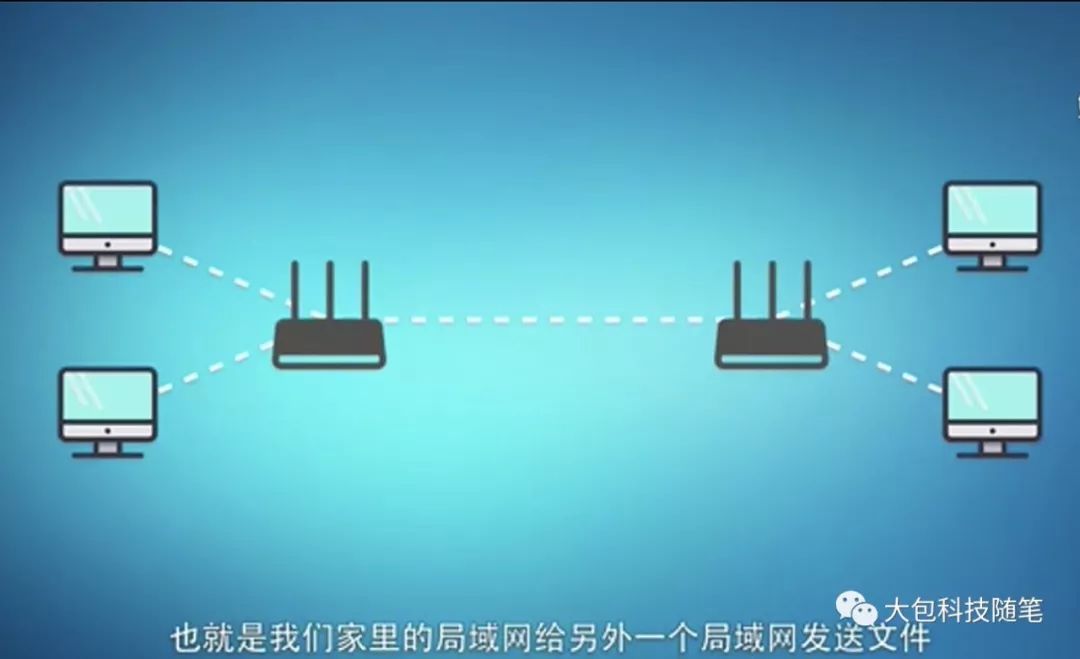
Figure 4
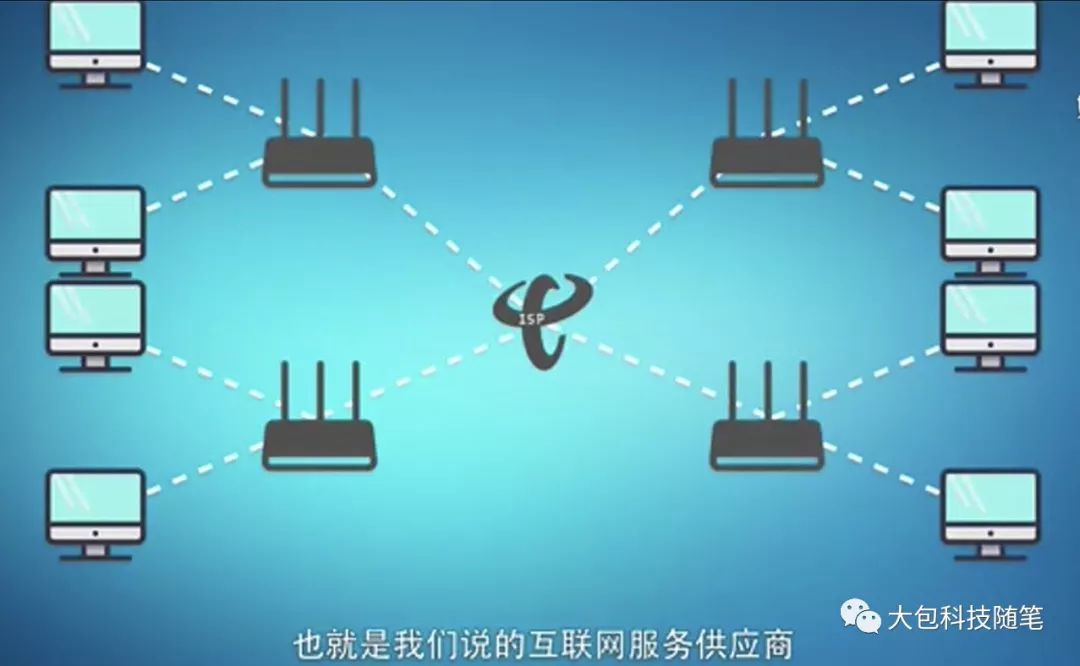
Figure 5
In the complex structure of the internet connecting thousands of computers, how can we ensure that each computer accurately transmits data to the target computer, and how can we avoid congestion and conflicts while efficiently and securely sharing connection lines? The key lies in the use of packet switching technology and the TCP/IP network communication protocol. The data communicated between computers is divided into packets, each containing the address information of the sending and receiving computers. These packets, composed of a series of electrical signals of 0s and 1s, are identified and processed by highly automated switches and routers on the internet, relayed along the way, and delivered accurately to their destination.
The key to the success of today’s internet is the TCP/IP network communication protocol, along with the thousands of switches, routers, and other electronic devices executing this protocol. There are four main characteristics of data transmission over the internet: 1) Data is divided into many packets, which are transmitted over the internet like mail parcels; 2) Each packet carries its own address information; 3) Internet routers, switches, and other network devices act like post offices, relaying packets with address information through various stations until they reach their destination (i.e., the target computer); 4) Packets can be interleaved during transmission over the internet, and if they are lost, they are resent, with the transmission path being completely uncertain.
The foundation for the existence and development of the internet is the numerous routers, switches, and the TCP/IP network communication protocol that coordinates the operation of these network devices. Without these network devices and communication protocols, computers would have to pull a transmission line between each pair, as shown in the network structure of Figure 2. Ultimately, this would lead to the situation depicted in Figure 6. As the total number of computers and digital terminal devices increases, this solution is simply a dead end! The so-called “quantum communication” is attempting to retrace this old, dead-end path.

Figure 6
The quantum key distribution protocol of “quantum communication” (whether BB84 or other new protocols) is an end-to-end protocol, and its information flow cannot be divided into packets. Moreover, the information it carries is not traditional electrical signals, which cannot be processed by the routers and switches on the internet. Therefore, quantum key distribution is fundamentally incompatible with the current structure of the internet; for “quantum communication” to reach households, it would have to reconstruct the terrifying spider web shown in Figure 6, either above or below the city.
To avoid the embarrassment of a spider web, “quantum communication” has only two routes to take for networking, but both are rugged and narrow paths.
The first route:
Using traditional electronic technology to build dedicated routers, switches, and other networking devices, where the quantum key is converted into electrical signals at each network node to be processed by these dedicated networking devices. From a technical perspective, this is at the same level as the trusted relay stations on the Beijing-Shanghai quantum communication trunk line. Because the quantum key is repeatedly converted into traditional electrical signals during the network relay process, the key is transmitted in a bare form, necessitating “physical isolation” at each forwarding node in the network.
What is “physical isolation”? This means that all these dedicated network devices must be guarded 24/7 to prevent any contact. This inevitably raises a series of security concerns: 1) How can we ensure the absolute reliability and loyalty of each member of this guarding team? 2) If a remote monitoring system is used, how can the communication security of these remote monitoring systems be guaranteed? Should we use quantum communication to protect the remote monitoring systems? Is there no end to this? 3) How can we ensure the loyalty and reliability of the design, manufacturing, and maintenance personnel of these dedicated network devices? What kind of company can provide absolutely secure and reliable devices and products?
The third question is essentially unsolvable. Because the manufacturing process of dedicated network devices will inevitably involve numerous component suppliers and integrators, no one can guarantee that the final product will be free of intentional or unintentional security vulnerabilities and hacker backdoors! Builders may consider these dedicated network devices to be “trusted,” but the question is how to gain the trust of others, especially those special users who pursue absolute confidentiality. Note that all of this involves traditional electronic devices, which have nothing to do with quantum physics.
The concept of traditional cryptographic systems, on the other hand, is based on the principle of not trusting anyone. In the design and layout of communication systems, all devices, protocols, and software are completely open and transparent, including encryption and decryption algorithms, without the need for so much “physical isolation.” As long as both parties hold a common key, they can ensure high security in their communication. The text sent, after being encrypted with the key, can be transmitted over any communication device and line, and the ciphertext can be collected, copied, and analyzed by anyone; however, only the recipient who possesses the key can decrypt the ciphertext to obtain the plaintext. Clearly, protecting the key is much more reliable and feasible than protecting the entire communication system (which includes many relay stations, routers, and switches).
The essential difference between classical cryptographic systems and the currently constructed “quantum communication” engineering is not at the technical level, but in the overall layout and thinking. Classical cryptographic systems start from the point of not trusting anyone, while the constructed “quantum communication” engineering must rely on and trust many people! Through this comparative analysis, we can clearly recognize that the first route is fundamentally a dead end; it is unqualified even as a transitional solution.
The second route:
Developing quantum routers, quantum switches, and a series of networking devices that ensure quantum keys can be relayed over the network without being converted into traditional electrical signals. This solution can certainly be discussed on paper, but the foundational engineering implementation currently does not exist. This is not difficult to understand. Traditional routers and switches are essentially specialized electronic computers. Similarly, quantum routers and quantum switches must be specialized quantum computers. These specialized devices must quickly and accurately control and measure quantum information stored in multiple qubits (Qbit) and send the output results to the next station. Essentially, these quantum network devices are quantum computers; compared to general-purpose quantum computers, they may have more fixed algorithms, but they may require higher precision, stability, and processing speed.
Currently, quantum computers only exist in textbooks and laboratories, and there is a long road ahead to develop practical quantum computers. This is because the quantum state of individual atoms or photons is extremely sensitive and fragile, which is precisely why quantum key distribution theoretically has high security; any attempt to steal, observe, or copy the quantum state will cause a change in the quantum state and be detected. However, this also makes normal control and measurement of them very difficult. Even more troubling is that this quantum state will automatically disappear, a phenomenon known as quantum decoherence. To maintain the quantum state, scientists use error correction techniques, employing numerous physical qubits to construct a logical qubit, ensuring the long-term precise maintenance of the quantum state.
Currently, achieving the maintenance of a quantum state for about one millisecond for a logical qubit is considered a good result, and there is still much work to be done to create a truly practical logical qubit. Then, multiple logical qubits must be created before a quantum computer can be constructed. To put it metaphorically, it is somewhat like the late 19th century, when the first practical electronic tube had not yet been created, making the possibility of manufacturing large general-purpose electronic computers nonexistent.
The core technologies of “quantum communication” and quantum computers are interconnected; they are fundamentally related to the preparation, control, and measurement of quantum states. The development of “quantum communication” and quantum computers must proceed on two legs; without significant advancements in quantum computer technology, the unilateral construction of a “quantum communication” network will certainly be unstable and unsustainable.
The practical and engineering realization of quantum computers is a long and arduous process, which determines that there is no possibility of networking for “quantum communication” in the near future, unless the aforementioned first route is adopted, introducing many “physical isolation” devices, leading to security risks far more severe than classical public key cryptographic systems.
Even if one day all the technical issues of quantum computers are resolved, and practical quantum routers, quantum switches, and other network devices are manufactured, that would still not be enough; more critically, effective quantum communication network protocols must be established, and this step is actually the most difficult. Quantum network protocols are the top priority for the engineering of “quantum communication”; they are the controlling engineering of “quantum communication”. Without overcoming this obstacle, the engineering of “quantum communication” lacks feasibility.
[1] There is not even a written draft for the network communication protocol of quantum cryptography; it is too early to discuss the networking devices for “quantum communication.” The introduction of quantum routers, quantum switches, and possibly quantum relay stations in this article is merely for the sake of discussion. These devices do not currently exist and may change in the future, or they may never appear.
[2] The images in this article are sourced from the internet.
Series Review:
Questioning quantum communication is a good thing for compensating for the “shortcomings of the Chinese scientific spirit”.
Referring to quantum communication as a national treasure is too much for the Chinese land to bear (Science Popularization Series Part One).
Here comes the solid content! A comprehensive analysis of the necessity of the Beijing-Shanghai quantum communication project (Science Popularization Series Part Two).