The Hyper Text Transfer Protocol (HTTP) is the core communication protocol used to access the World Wide Web and is the protocol used by all web applications today. Although HTTP is widely used in web applications, its insecurity during transmission has led to its gradual replacement by the HTTPS protocol.
Initially, HTTP was a simple protocol developed for retrieving text-based static resources. As web applications emerged, it was expanded and utilized in various forms to support the complex distributed applications we commonly see today.
The HTTP mechanism involves a client sending a request, followed by the server returning a response message. This protocol is a transport protocol based on the TCP/IP protocol.
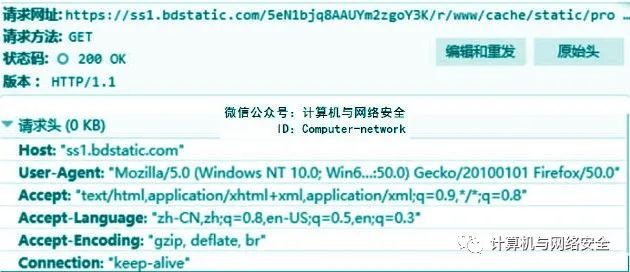
We can view the HTTP request header information in the browser’s console. For example, by entering the URL http://www.example.com and pressing F12 to open the console, as shown in Figure 1.
Figure 1: HTTP Request Header
From Figure 1, we can see that the request header generally consists of the following components:
(1) Access method, with the most common method being GET, which primarily retrieves a resource from the web server.
(3) The HTTP version used. The most common HTTP versions on the Internet are 1.0 and 1.1, with the main difference being that when attacking web applications, the HTTP/1.1 version must use the Host request header.
(4) The User-Agent header provides information related to the browser or other client software generating the request.
(5) The Host header specifies the hostname that appears in the complete URL being accessed.
(6) The Cookie header is used to submit parameters issued by the server to the client.
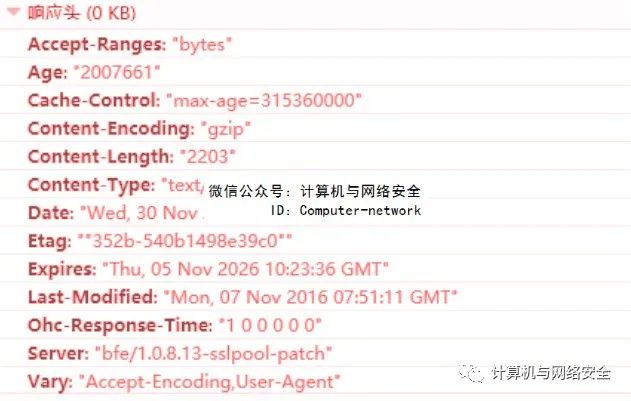
Corresponding to the previously mentioned HTTP requests, response header information can also be found in the browser, as shown in Figure 2.
Figure 2: Response Header Information
Some information in the response header is the same as in the request header, such as the HTTP version.
The response header often indicates the status code of the request result, with 200 being the most normal status code.
Other key points in the response header include: the Server header, which indicates the web server software used; and the Content-Length header, which specifies the byte length of the message body.
When attacking web applications, the two most commonly used methods are GET and POST.
The GET method retrieves resources. It can send parameters to the requested resource in the form of a query string in the URL.
The POST method executes operations. This method can send request parameters in both the URL query string and the message body.
In terms of data transmission, the POST method is more effective than the GET method. GET transmits data not exceeding 2 KB, while POST can transmit a larger amount of data, generally with no default limit. Theoretically, the maximum for IIS4 is 80 KB, and for IIS5 it is 100 KB. Additionally, GET has lower security, while POST encrypts data, making it more secure. Another point is that the execution efficiency of the POST method is higher than that of the GET method.
Source: Computer and Network Security