
Source:TECH2IPO/Chuangjian, Aifaner, DOIT
Author: iot101
IoT Think Tank, Organized and Released
Please indicate the source and origin when reprinting
—— [Introduction] ——
As Laozi said: Disaster is the source of fortune!

You are under attack from your refrigerator!
You are under attack from your microwave!
Refuse to be a “zombie device”, resist connecting home appliances to the internet!
This is a rather radical call to action from a friend of iot101 for the “anti-IoT” movement, and the tone is intimidating.
The cause is likely known to everyone; it was the hacker attack last Friday (October 21) that paralyzed half of America’s internet. The media called this attack the “most severe DDoS attack in history”, highlighting its dreadful impact.
Hackers controlled a large number of internet-connected cameras and DVRs in the U.S. and used these “zombie devices” to attack several well-known websites, including Twitter, Paypal, and Spotify, forcing many sites that people use daily to interrupt their services.
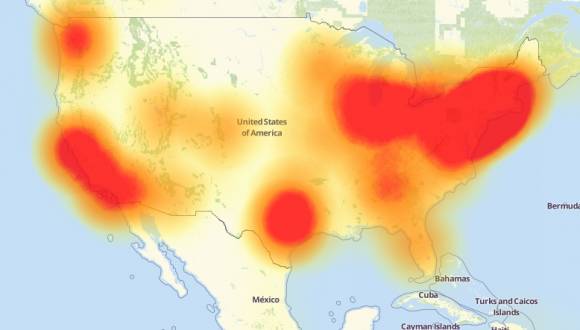 Image: The red part indicates that some users reported they were unable to access the website
Image: The red part indicates that some users reported they were unable to access the website
It is reported that the hackers used a virus called “Mirai”, known as the “IoT Destroyer”, to search for zombie devices. Even more deadly, the source code of the Mirai virus was released by developers in September, leading many hackers to upgrade this virus, making it more contagious and harmful than its predecessors.
The Mirai virus is a type of virus that searches for IoT devices over the internet. When it scans an IoT device (such as a network camera or smart switch), it attempts to log in using default passwords (usually admin/admin, with Mirai carrying 60 common passwords). Once logged in successfully, the IoT device enters the “zombie device” list and begins to be manipulated by hackers to attack other network devices.
This incident has once again pushed IoT security issues to the forefront. Should we lament the security issues of IoT devices and even start to oppose IoT?
Not necessarily.
Mainstream media expresses concern
 Image: The attack on the U.S. internet has pushed IoT security to the forefront
Image: The attack on the U.S. internet has pushed IoT security to the forefront
Foreign media claim that the botnet targeting IoT devices may be a significant source of this DDoS attack. With the widespread use of smart products, hackers can control thousands of connected devices, such as cameras and home routers, without users’ knowledge, using software to launch massive internet traffic against a target.
According to The New York Times, a large number of IoT devices have been connected to the internet over the past few years, and these devices are inexpensive, lack security protection, and their numbers continue to rise.
In an interview with The Guardian, Richard Sims, a product development consultant at Technology Partnership, stated that IoT devices are usually default connected to the internet, and their code is often open source, making them easy targets for hackers.
Additionally, foreign telecom companies have indicated that with the emergence of Mirai variants, botnets will continue to launch DDoS attacks in the future.
Moreover, the use of IoT devices by hackers is not new. In 2014, over 100,000 connected devices, including refrigerators, home routers, and smart TVs, were hacked, and hackers sent a large amount of spam. However, hackers’ methods are becoming increasingly sophisticated.
Looking at the discourse from these mainstream media, it is clear that they are concerned. Although the impact of these events is extremely severe, iot101 believes that from another perspective, the virus is precisely a ladder that promotes the advancement of IoT. If we view these incidents optimistically, we will have a different perspective.
A large-scale virus indicates that IoT development has entered a substantial stage
From the time the concept of IoT was proposed in China in 2009 to now, it has only been 7 years. Many people still shout: IoT is just a concept, just a castle in the air!!
Those who say this, after seeing this incident, I wonder if they feel slapped in the face?
The outbreak of large-scale viruses indicates that IoT has indeed entered a substantial stage; otherwise, large-scale infections would not occur. If only a few devices were connected, hackers wouldn’t bother to attack; after all, hackers’ time is also precious!
To establish a true IoT, scale is one of its necessary conditions. Only with scale can the intelligence of objects be realized.
Cisco estimates that the number of IoT devices will grow from the current 15 billion to 50 billion by 2020, while Intel estimates that there will be 200 billion such devices by 2020.
Once the number of connected devices reaches the level of trillions, IoT will transition from a substantial stage to an explosive stage.
This incident serves as a wake-up call for manufacturers; security issues should be considered from the ground up
Through this incident, IoT device manufacturers should realize this:the public does not prioritize the security of connected devices. People use default passwords and do not think to change them, and these passwords are easily accessible, making connected devices easy to become part of a botnet.
Therefore, if you are a company releasing such products to the consumer market, you cannot expect consumers to have relevant security knowledge; thus, security issues need to be considered from the design phase. Manufacturers cannot neglect the security of connected devices to reduce costs, thereby giving hackers an opportunity.
Currently, aside from some professionally secure IoT devices that are often isolated from the internet and difficult to attack, most devices often do not have security software installed.
Professor Mercedes Bunz from Westminster University said: “You can’t install a firewall on a baby monitor because it doesn’t have enough storage space.”
Traditional security measures, such as antivirus software or firewalls, are not applicable to IoT devices because these devices are not personal computers and are not very intelligent.
Additionally, manufacturers add too many functions when creating connected devices. Why does your baby monitor need to connect to networks outside the home? Perhaps one solution is that some functions should be reduced.
If more effective security measures can be devised, it will be a new blue ocean for wealth!
Viruses and antivirus technologies are in a love-hate relationship, precisely accelerating technological progress
Looking at the development of the internet on computers and the mobile internet on smartphones, viruses have indeed accelerated technological progress.
From the first computer virus born in a U.S. laboratory in 1983; to 1986 when two brothers created the first virus that infected personal computers, the “Pakistani” virus; to the well-known Melissa, worm viruses, Code Red, Shockwave, and Stuxnet, virus technology has continued to evolve, but antivirus technology has also been continuously improved.
The struggle between the two has never ceased since the emergence of viruses.
Early viruses were monomorphic, thus, in the area of automatic detection technology for viruses, antivirus software used signature-based detection methods, which means that when scanning a program, if a specific virus signature is found, it can identify the corresponding computer virus.
However, with the advent of polymorphic viruses that do not have stable signatures, the “signature detection method” has become ineffective. Polymorphic viruses represented by the Transformer virus can change their characteristics based on mathematical principles, making them difficult for antivirus software to detect.
As the saying goes, “the higher the skill, the better the magic”, the emergence of virtual machine technology can entice polymorphic viruses to reveal their true form, thus eliminating them. It features manual analysis, high intelligence, and high accuracy in virus detection.
With the rapid development of the internet, virus technology has also been updated, spreading wider and causing greater destruction, and antivirus technology will innovate again. In the continuous cycle of technological updates, people have gained a deeper understanding of viruses, code, computers, and networks.
The same goes for IoT devices; we should understand that security issues cannot be completely eradicated; they can only be prevented.
To minimize harm as much as possible, device manufacturers need to unite to raise the security threshold for IoT devices, while users should also enhance their safety awareness when using IoT devices.

Previous Hot Articles (Click on the title to read directly):
-
《[Heavyweight] IoT Industry Panorama Report, the first domestic IoT industry two-dimensional perspective panorama
-
《Interview with Academician Wu Hequan: Four good news indicate that the development of IoT is on the right track
-
《The first low-power wide-area network LPWAN market report in China is released: Where is the next IoT opportunity? [Text version]
-
《A comic tells you: What is LoRa that everyone is talking about behind NB-IoT?
-
《A comic tells you: Besides WiFi and Bluetooth, what can the recently popular NB-IoT do?》
-
《McKinsey’s heavyweight report: How can enterprises tap into the value of “Industry 4.0”? (Collectible version)



