Hello, everyone!~
I am network engineer Bai Xi! 🌞
This article focuses on the configuration of Huawei IPSec VPN dynamic access scenarios.
It details the barbaric mode negotiation mechanism, policy template application, and NAT priority tuning solutions, providing CLI templates for heterogeneous networking between headquarters and branches.
Note
In this experiment, the branch’s IP address is dynamically obtained, so the mode type is
- Barbaric mode in phase one (Aggressive)
- Quick mode in phase two
Therefore, it is necessary to modify the main mode to barbaric mode in phase one to establish the IKE SA, and both ends (headquarters and branch) need to be changed.
Experiment Background
- R1 is the enterprise headquarters gateway with a fixed address
- R3 is the enterprise branch gateway with a dynamic address
- The branch and headquarters establish communication through the public network
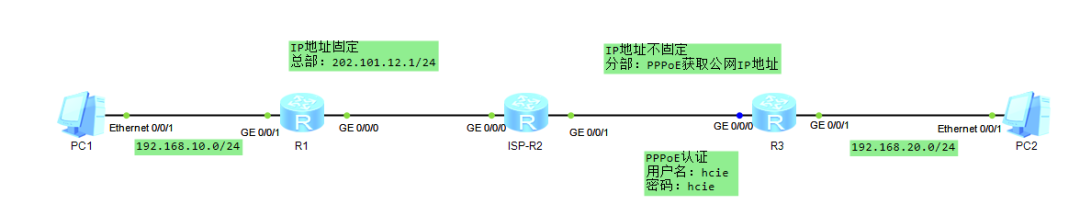
Experiment Environment
This experiment uses the simulator ensp v1.3.00
Experiment device: AR2220
Configuration Considerations
For the fixed address headquarters, the following points need to be noted:
- ① Dynamic template: As shown in the topology, R1 is the fixed address end, and it wants to establish an IPSec VPN with its branch R3. Without knowing R3’s IP address, it cannot be configured in the conventional way, so we can only use a template to establish it~
- ② No need to set ACL: Because we do not know what private network segments are on the branch R3 side
So how to establish IPSec with the branch device that has an unfixed address?
- Use the unfixed address R3 to actively initiate IPSec negotiation with R1
- After negotiating the IPSec SA, R1 will obtain the interest flow that needs protection in the IPSec SA, which is the content of the ACL
The configuration and solutions will be provided later, so if you are interested, you can continue reading.
Experiment Requirements
First, the enterprise hopes to securely protect the traffic between the branch subnet and the headquarters subnet.
-
The branch and headquarters establish communication through the public network, and an IPSec tunnel can be established between the branch gateway and the headquarters gateway for security protection.
-
The branch subnet is unfixed, while the headquarters subnet is fixed at 202.101.12.0/24.
-
The branch R3 obtains the public address through PPPoE, and DHCP is also acceptable, with the subnet being 202.101.23.0/24
-
For the configuration of PPPoE, you can refer to this article Step-by-Step Guide to Configuring Huawei PPPoE Dialing
Second, it is also necessary to allow both headquarters and branches to access the internet, reaching the ISP’s 8.8.8.8 address
- It should be noted that NAT and IPSec deployed on the same device may have a priority conflict, so attention is needed; specific solutions will be provided in the configuration section.
Configuration Ideas
-
Basic Configuration, configure the IP address of the interface and the static route to the opposite end to ensure that the routes at both ends are reachable.
-
Phase One IKE SA
- ① Configure IKE security proposals, defining the method of protecting IKE data streams
- ② Configure IKE peers, defining the attributes during IKE negotiation between peers; here, special care must be taken to change the main mode to barbaric mode, which needs to be modified at both ends
3. Phase Two IPSec SA
- ① Configure ACL to define the data streams that need IPSec protection (the headquarters R1 does not need to configure, while the branch R3 does)
- ② Configure IPSec security proposals, defining the protection methods for IPSec
- ③ Fixed address end (R1): Configure policy templates, the template content (IPSec security proposals and IKE peers, determining what protection methods to apply to which data streams), and reference this policy template in the security policy
- ④ Unfixed address end (R3): Configure security policies, and reference ACL, IPSec security proposals, and IKE peers, determining what protection methods to apply to which data streams
4. Apply the IPSec security policy group on the interface, enabling the interface to have IPSec protection functionality
5. Configure NAT
IPsec VPN essence: Phase one protects phase two, phase two protects data
Configuration Commands
Topology
R1
Basic Configuration
Configure R1’s basic settings, then use the default route to achieve public network reachability
[Huawei]sysn R1
#i Disable CLI system prompt messages, the pop-up is a bit annoying
[R1]undo info-center enable
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip address 202.101.12.1 24
[R1-GigabitEthernet0/0/0]qu
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ip address 192.168.10.254 24
[R1-GigabitEthernet0/0/1]qu
#i Configure the default route pointing to ISP_R2 operator to achieve public network reachability
[R1]ip route-static 0.0.0.0 0.0.0.0 202.101.12.2
Configure Phase One IKE SA
Negotiate IKE SA to protect the negotiation process of phase two IPSec SA
#i Create R1's IKE security proposal, named 1
[R1]ike proposal 1
#i Use 3des-cbc to encrypt IKE
[R1-ike-proposal-1]encryption-algorithm 3des-cbc
#i Use md5 for authentication
[R1-ike-proposal-1]authentication-algorithm md5
#i Enable DH group 5
[R1-ike-proposal-1]dh group5
[R1-ike-proposal-1]qu
#i Create IKEv1 peer, named 1, configure pre-shared key and modify main mode
[R1]ike peer 1 v1
#i Remember to change to barbaric mode
[R1-ike-peer-1]exchange-mode aggressive
#i Reference security proposal 1
[R1-ike-peer-1]ike-proposal 1
#i Pre-shared key is 520
[R1-ike-peer-1]pre-shared-key simple 520
[R1-ike-peer-1]qu
Configure Phase Two IPSec SA
Complete the negotiation of IPSec SA under the protection of the IKE SA established in phase 1
The headquarters has a fixed address and does not know the interest traffic of the branch, so there is no need to write ACL to match
Later, when the branch actively accesses the headquarters, it will generate IPSec SA information, and the interest traffic of the headquarters will be extracted from it
#i Configure IPSec security proposal, named 1
[R1]ipsec proposal 1
#i Use ESP header to encapsulate IPSec, using 3des encryption
[R1-ipsec-proposal-1]esp encryption-algorithm 3des
#i Use ESP header to encapsulate IPSec, using md5 authentication
[R1-ipsec-proposal-1]esp authentication-algorithm md5
#i Use tunnel mode (although it is the default tunnel mode)
[R1-ipsec-proposal-1]encapsulation-mode tunnel
[R1-ipsec-proposal-1]qu
#i Configure policy template, named 1, priority 1
#i And in the policy template, call related content
[R1]ipsec policy-template 1 1
[R1-ipsec-policy-templet-1-1]ike-peer 1
[R1-ipsec-policy-templet-1-1]proposal 1
[R1-ipsec-policy-templet-1-1]qu
#i Security policy named 1, reference policy template 1
[R1]ipsec policy mypolicy 1 isakmp template 1
Interface Invocation
#i Call security policy 1 under the interface
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ipsec policy mypolicy
[R1-GigabitEthernet0/0/0]qu
NAT Configuration
#i This is for NAT, do not conflict with IPSec's ACL number!!!
[R1]acl 3001
#i deny traffic going through IPSec
[R1-acl-adv-3001]rule deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#i permit internal network segment
[R1-acl-adv-3001]rule permit ip source 192.168.10.0 0.0.0.255
[R1-acl-adv-3001]quit
#i Call on the interface and start NAT conversion
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]nat outbound 3001
[R1-GigabitEthernet0/0/0]quit
ISP_R2
Basic Configuration
[Huawei]sysn ISP_R2
[ISP_R2]undo info-center enable
#i Headquarters IP address
[ISP_R2]int g0/0/0
[ISP_R2-GigabitEthernet0/0/0]ip address 202.101.12.2 24
[ISP_R2-GigabitEthernet0/0/0]qu
#i Access public network 8.8.8.8/32
[ISP_R2]int LoopBack 0
[ISP_R2-LoopBack0]ip address 8.8.8.8 32
[ISP_R2-LoopBack0]quit
#i PPPoE server
[ISP_R2]aaa
[ISP_R2-aaa]local-user hcie password cipher hcie
I[ISP_R2-aaa]local-user hcie service-type ppp
[ISP_R2-aaa]quit
[ISP_R2]ip pool R3
[ISP_R2-ip-pool-R3]network 202.101.23.0 mask 255.255.255.0
[ISP_R2-ip-pool-R3]excluded-ip-address 202.101.23.2
[ISP_R2-ip-pool-R3]quit
[ISP_R2]int Virtual-Template 1
[ISP_R2-Virtual-Template1]ip address 202.101.23.2 24
[ISP_R2-Virtual-Template1]ppp authentication-mode pap
[ISP_R2-Virtual-Template1]remote address pool R3
[ISP_R2-Virtual-Template1]quit
[ISP_R2]int g0/0/1
[ISP_R2-GigabitEthernet0/0/1]pppoe-server bind virtual-template 1
[ISP_R2-GigabitEthernet0/0/1]quit
R3
Basic Configuration
Configure R3’s basic settings, then use the default route to achieve public network reachability
In this article, how does the branch R3 achieve an unfixed address?
- ① Obtain via DHCP
- ② Obtain via PPPoE
This experiment uses PPPoE to achieve fixed address acquisition for the branch, mainly to relate to previous articles; of course, for convenience, DHCP can be used, which is faster.
[Huawei]sysn R3
[R3]undo info-center enable
Info: Information center is disabled.
#i PPPoE client configuration
[R3]dialer-rule
[R3-dialer-rule]dialer-rule 1 ip permit
[R3-dialer-rule]quit
[R3]int Dialer 1
[R3-Dialer1]dialer user hcie
[R3-Dialer1]ppp pap local-user hcie password cipher hcie
[R3-Dialer1]ip address ppp-negotiate
[R3-Dialer1]dialer bundle 1
[R3-Dialer1]dialer-group 1
[R3-Dialer1]quit
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]pppoe-client dial-bundle-number 1
[R3-GigabitEthernet0/0/0]quit
[R3]int g0/0/1
[R3-GigabitEthernet0/0/1]ip address 192.168.20.254 24
[R3-GigabitEthernet0/0/1]qu
#i Configure the default route pointing to ISP_R2 operator to achieve public network reachability
[R3]ip route-static 0.0.0.0 0.0.0.0 202.101.23.2
Configure Phase One IKE SA
Negotiate IKE SA to protect the negotiation process of phase two IPSec SA
[R3]ike proposal 1
[R3-ike-proposal-1]encryption-algorithm 3des-cbc
[R3-ike-proposal-1]authentication-algorithm md5
[R3-ike-proposal-1]dh group5
[R3-ike-proposal-1]qu
#i Remember to enable barbaric mode here too!!!
[R3]ike peer 1 v1
[R3-ike-peer-1]exchange-mode aggressive
[R3-ike-peer-1]ike-proposal 1
[R3-ike-peer-1]pre-shared-key simple 520
[R3-ike-peer-1]remote-address 202.101.12.1
[R3-ike-peer-1]qu
Configure Phase Two IPSec SA
Complete the negotiation of IPSec SA under the protection of the IKE SA established in phase 1
[R3]ipsec proposal 1
[R3-ipsec-proposal-1]encapsulation-mode tunnel
[R3-ipsec-proposal-1]esp encryption-algorithm 3des
[R3-ipsec-proposal-1]esp authentication-algorithm md5
[R3-ipsec-proposal-1] qu
#i Here, it is necessary to write the interest traffic to match and then perform IPSec encrypted transmission
[R3]acl 3000
[R3-acl-adv-3000]rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[R3-acl-adv-3000]qu
[R3]ipsec policy mypolicy 1 isakmp
[R3-ipsec-policy-isakmp-mypolicy-1]ike-peer 1
[R3-ipsec-policy-isakmp-mypolicy-1]proposal 1
[R3-ipsec-policy-isakmp-mypolicy-1]security acl 3000
[R3-ipsec-policy-isakmp-mypolicy-1]qu
Interface Invocation
#i Since I am using PPPoE dialing to obtain the public address
#i Therefore, the IPSec security policy needs to be called on the public outgoing interface
#i So it is called on the dialing port
[R3]int Dialer 1
[R3-Dialer1]ipsec policy mypolicy
[R3-Dialer1]quit
NAT Configuration
[R3]acl 3001
[R3-acl-adv-3001]rule deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[R3-acl-adv-3001]rule permit ip source 192.168.20.0 0.0.0.255
[R3-acl-adv-3001]quit
[R3]int Dialer 1
[R3-Dialer1]nat outbound 3001
[R3-Dialer1]quit
PC
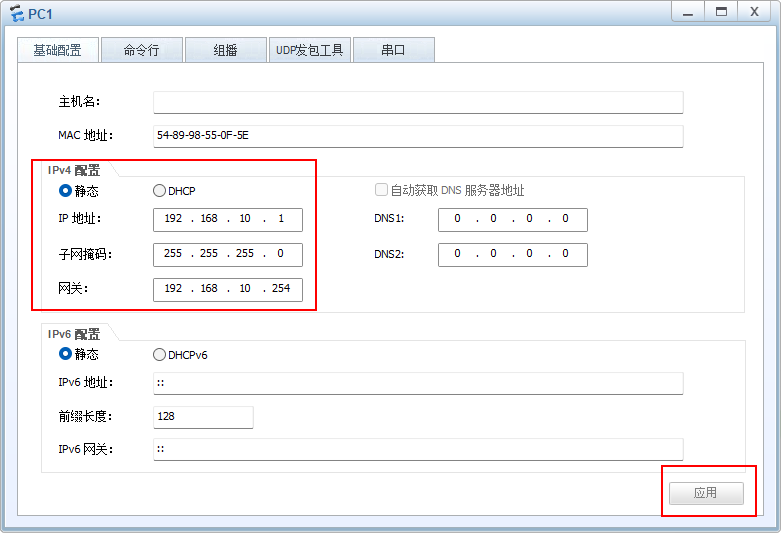
PC1
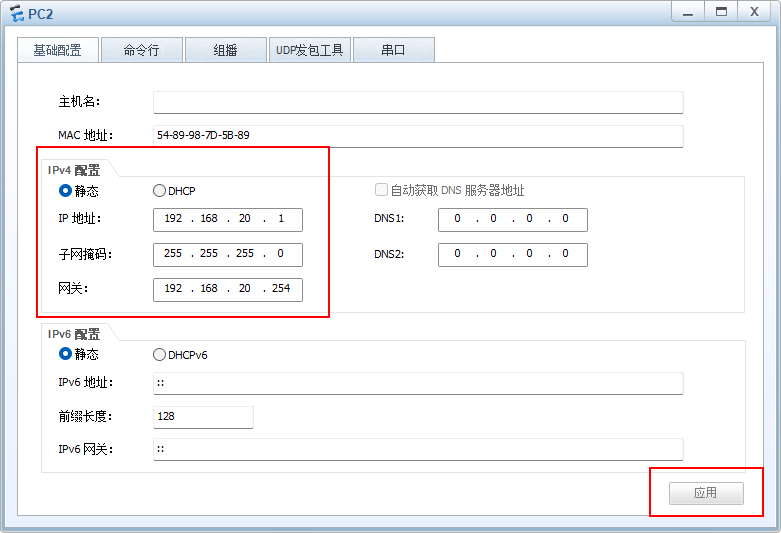
PC2
Check if the service meets requirements
ping
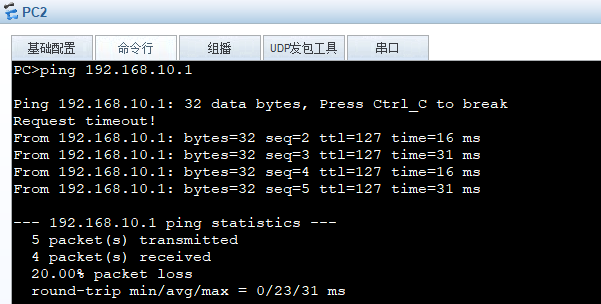
If it doesn’t work after a while, you can turn off the device and restart it, of course, the premise is to save the configuration.
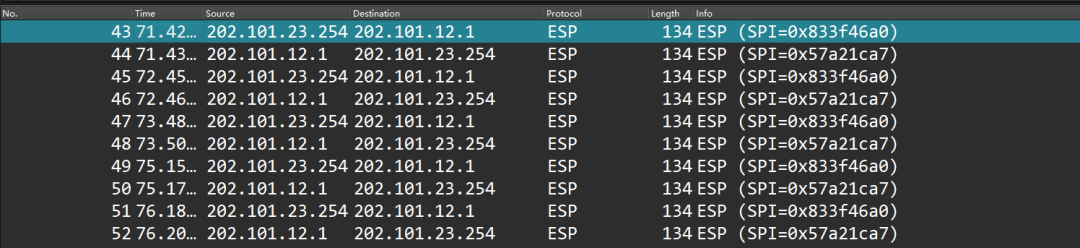
NAT
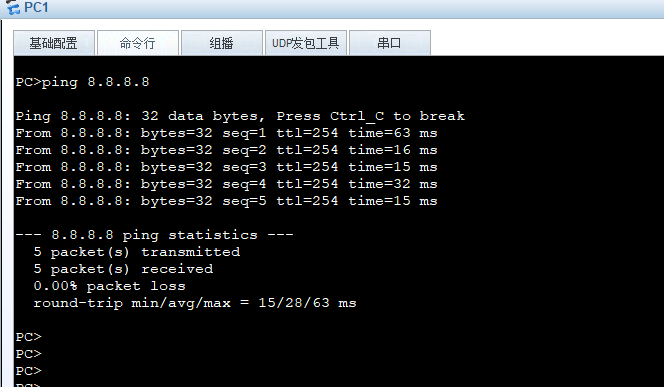
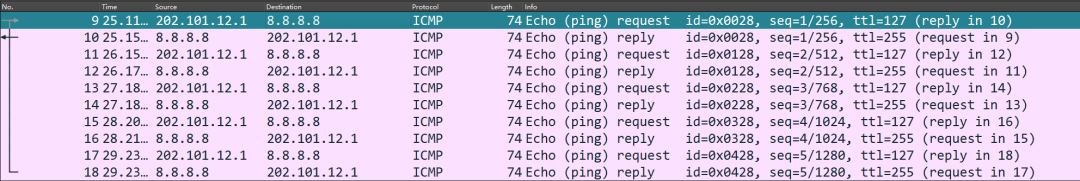
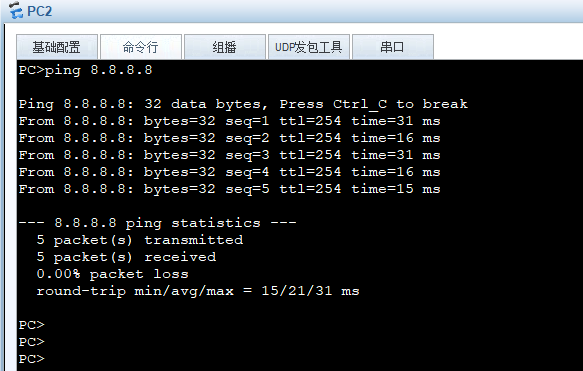
Headquarters and branch subnets can communicate securely, and the internal network can also access the internet to reach 8.8.8.8, indicating that the experiment is complete.
Check
In the case of dynamic address access, we use the host on the branch R3 to initiate the connection because R1 does not know the situation on the other side and can only wait for R3 to initiate the connection.
However, Huawei can automatically initiate the IPSec VPN establishment, but we still need the branch host PC2 to actively ping the headquarters so that headquarters R1 can generate IPSec SA information.
Headquarters R1 will then know the interest traffic based on the generated IPSec SA information.
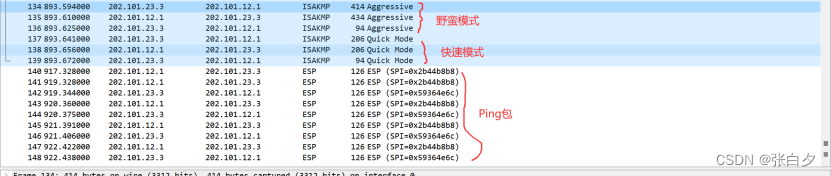
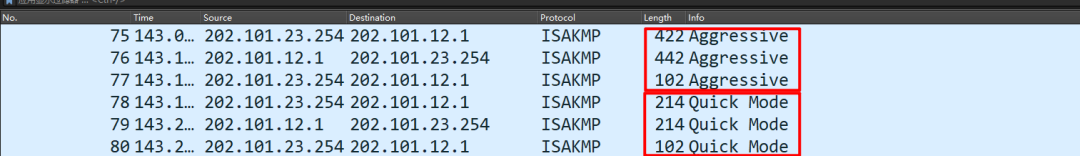
Establishment Successful
Careful observers will notice
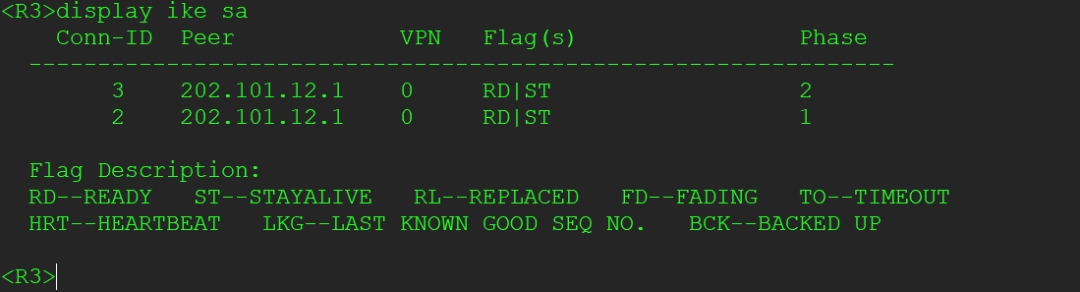
- In barbaric mode, three messages are exchanged, successfully negotiating IKE SA
- While in quick mode, three messages successfully negotiate IPSec SA
These two successfully establish the IPSec VPN, implementing encryption on the traffic~ This distinguishes it from the six messages in main mode.
View Commands
View basic information of IKE SA
- [R1]display ike sa
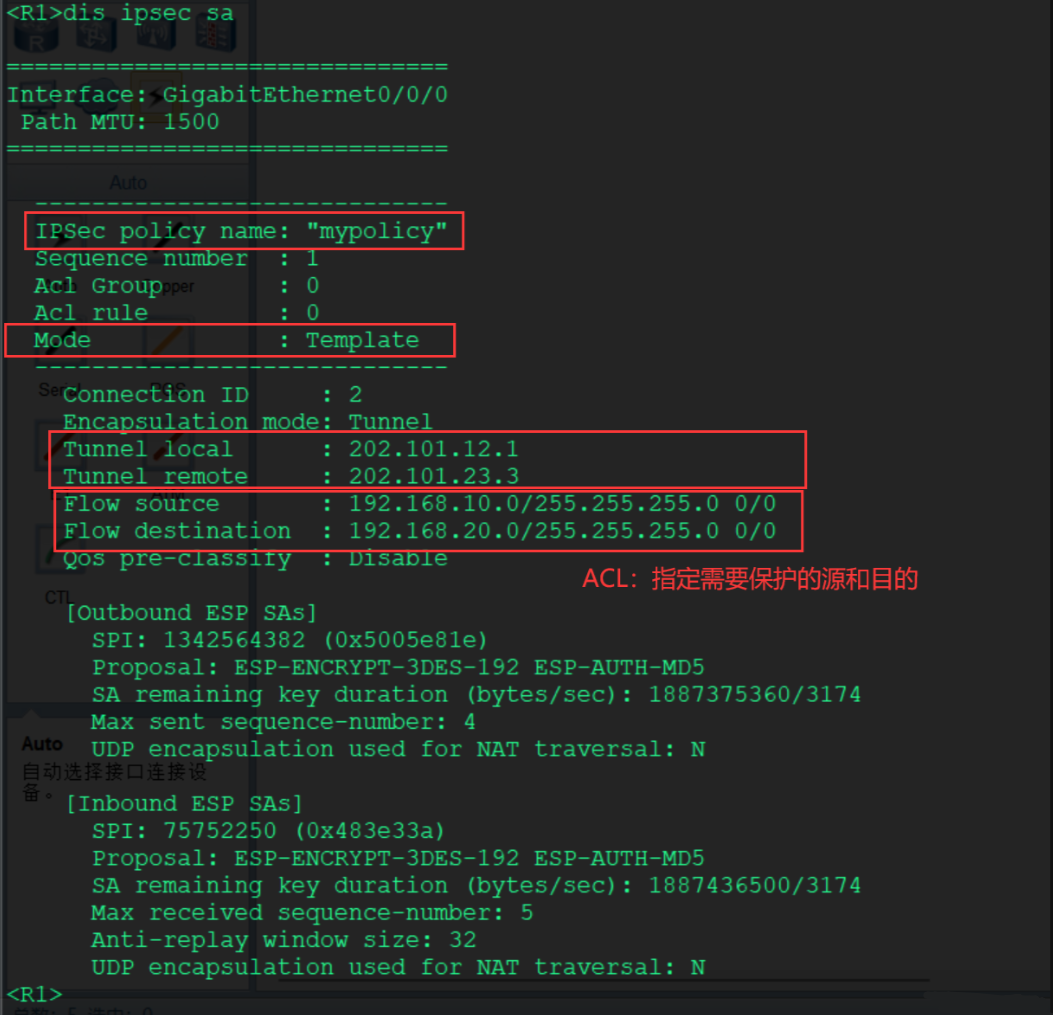
View basic information of IPSec SA
- [R1]display ipsec sa
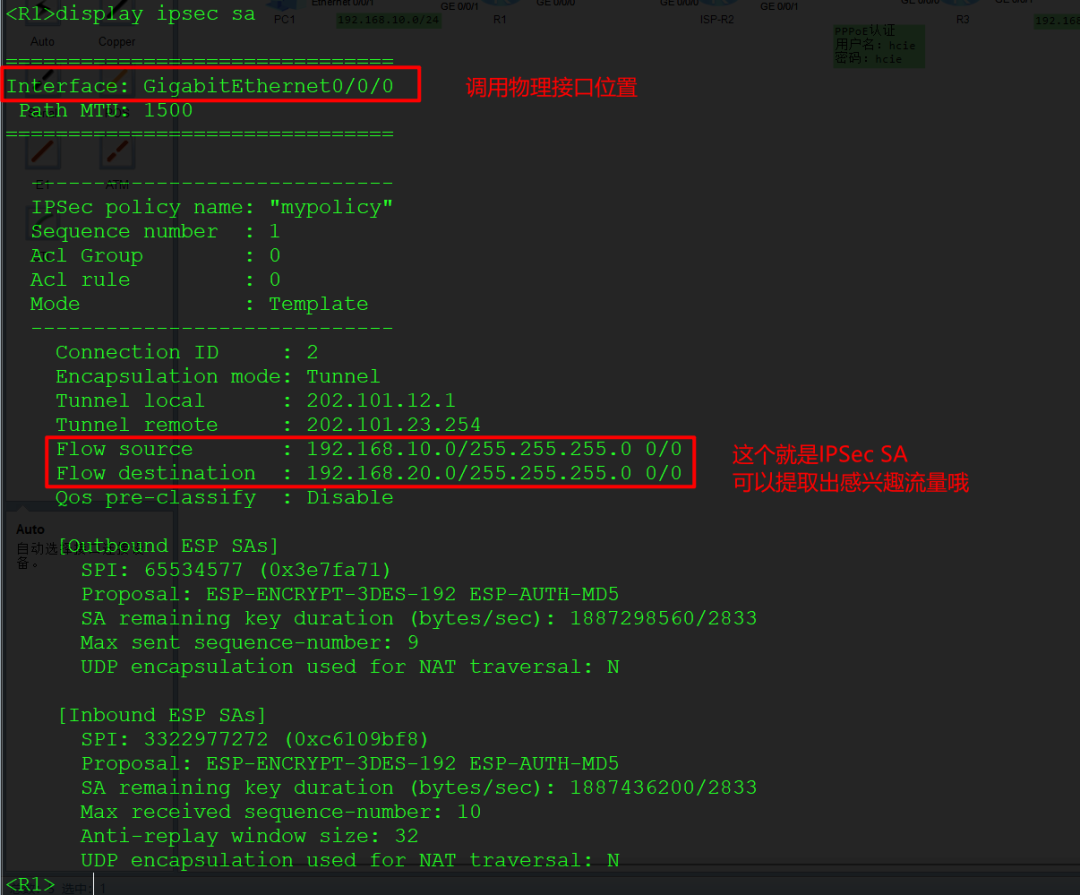
In the image, you can see the source and destination of the tunnel, which is the IPSec SA information viewed on headquarters R1.
You can see that R3’s IP address at this time is 202.101.23.3, which it obtained by itself, and we did not change anything.
Also, R1 can obtain similar information from IPSec SA, which needs to match the protected traffic in the ACL.
So all the above discussions were to lay the groundwork for this.
Clear IKE / IPSec SA Commands
After the IPSec VPN is established, if we want to modify the configuration, we need to clear the SA for the configuration to take effect
Just a reminder, modify the configuration first, then clear the SA.
Because Huawei’s IPSec is established automatically, it will appear that just clearing the SA will immediately re-establish it.

Save Configuration
Saving the configuration is quite important; I don’t know if it’s my computer’s reason, but this ensp doesn’t respond for half an hour, and when I type commands, it just shows ###, which is very annoying 
For Huawei devices, the save command can only be configured in user view by typing save and then entering y to confirm 
Configuration Document
The purpose of the configuration document is that if the above configuration fails, you can use the complete code below to flash it in and see the effect, and compare it.
The configuration document is fine and can successfully establish the connection; the following configuration has been flashed.
As for how to flash this code, WeChat has a bug, which is annoying; directly copying does not work, so I take screenshots and extract text this way. The extracted text may have some errors, such as 0 becoming O, so please pay attention.
R1
sys
#
sysname R1
#
undo info-center enable
#
acl number 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 10 permit ip source 192.168.10.0 0.0.0.255
#
ipsec proposal 1
esp encryption-algorithm 3des
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group5
authentication-algorithm md5
#
ike peer 1 v1
exchange-mode aggressive
pre-shared-key simple 520
ike-proposal 1
#
ipsec policy-template 1 1
ike-peer 1
proposal 1
#
ipsec policy mypolicy 1 isakmp template 1
#
interface GigabitEthernet0/0/0
ip address 202.101.12.1 255.255.255.0
ipsec policy mypolicy
nat outbound 3001
#
interface GigabitEthernet0/0/1
ip address 192.168.10.254 255.255.255.0
#
ip route-static 0.0.0.0 0.0.0.0 202.101.12.2
#
ISP_R2
sys
#
sysname ISP_R2
#
ip pool R3
network 202.101.23.0 mask 255.255.255.0
excluded-ip-address 202.101.23.2
#
aaa
local-user hcie password cipher hcie
local-user hcie service-type ppp
#
interface Virtual-Template 1
ppp authentication-mode pap
remote address pool R3
ip address 202.101.23.2 255.255.255.0
#
interface GigabitEthernet0/0/0
ip address 202.101.12.2 255.255.255.0
#
interface GigabitEthernet0/0/1
pppoe-server bind Virtual-Template 1
#
interface LoopBack0
ip address 8.8.8.8 255.255.255.255
R3
sys
#
sysname R3
#
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
acl number 3001
rule 5 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 10 permit ip source 192.168.20.0 0.0.0.255
#
ipsec proposal 1
esp encryption-algorithm 3des
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group5
authentication-algorithm md5
#
ike peer 1 v1
exchange-mode aggressive
pre-shared-key simple 520
ike-proposal 1
remote-address 202.101.12.1
#
ipsec policy mypolicy 1 isakmp
security acl 3000
ike-peer 1
proposal 1
#
interface Dialer1
link-protocol ppp
ppp pap local-user hcie password cipher hcie
ip address ppp-negotiate
dialer user hcie
dialer bundle 1
dialer-group 1
ipsec policy mypolicy
nat outbound 3001
#
interface GigabitEthernet0/0/0
pppoe-client dial-bundle-number 1
#
interface GigabitEthernet0/0/1
ip address 192.168.20.254 255.255.255.0
#
dialer-rule
dialer-rule 1 ip permit
#
ip route-static 0.0.0.0 0.0.0.0 202.101.23.2