
The reason for studying these three protocols together is that they operate at the same layer. The ARP protocol is used to find the Ethernet MAC address of the target host, while IP carries the message to be sent. The data link layer can obtain transmission information from ARP and the data to be transmitted from IP.
IP Protocol
The IP protocol is the core of the TCP/IP protocol suite. All TCP, UDP, ICMP, and IGMP data are transmitted in IP data format. It is important to note that IP is not a reliable protocol, meaning that it does not provide a mechanism for handling undelivered data—this is the responsibility of upper-layer protocols like TCP or UDP. Hence, TCP is considered a reliable protocol, while UDP is not.
IP Header
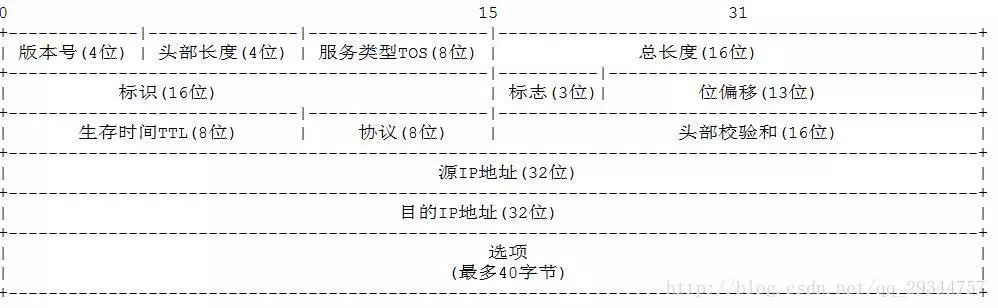
Explaining each part is a textbook task; I am only interested in the eight-bit TTL field. Do you remember what this field does? This field specifies how many routers the packet can pass through before being discarded (showing the unreliability of the IP protocol, which does not guarantee data delivery). Each time an IP packet passes through a router, its TTL value decreases by 1. When the TTL reaches zero, the packet will be automatically discarded. The maximum value of this field is 255, meaning a protocol packet can pass through a maximum of 255 routers before being discarded. Depending on the system, this number can vary, typically being 32 or 64. The Traceroute tool operates on this principle; the -m option in traceroute requires a maximum value of 255, which is because the TTL in the IP protocol is only 8 bits.
The current version of IP is 4, so it is also known as IPv4. There is also IPv6, which is becoming more widely used.
IP Routing
When an IP packet is ready, how does it get delivered to the destination? How does it choose a suitable path for delivery?
The most special case is when the target host is directly connected to the host, meaning the host does not need to look for a route and can directly send the data. For direct transmission, ARP protocol is used, which will be discussed later.
A more common scenario is when the host connects to the target host through several routers. In this case, routers need to use the information in the IP packet to find a suitable target for delivery, such as an appropriate host or router. The router or host will handle an IP packet as follows: if the TTL of the IP packet expires, the packet will be discarded.
Search the routing table, prioritizing matching hosts. If a target host with an exact IP address is found, the packet is sent to that host.
If the host match fails, search for routers in the same subnet, which requires assistance from the subnet mask. If a router is found, the packet is sent to that router.
If the match with the same subnet router fails, search for routers with the same network number (explained in Chapter One). If a router is found, the packet is sent to that router.
If all the above fails, search for the default route. If a default route exists, the packet is sent. If all fail, the packet is discarded.
This once again proves that IP packets are unreliable because they do not guarantee delivery.
Subnet Addressing
The definition of an IP address is the network number + host number. However, all hosts now require subnet addressing, meaning the host number is subdivided into subnet number + host number. Ultimately, an IP address becomes network number + subnet number + host number. For example, a Class B address: 210.30.109.134. Regarding how many bits represent the subnet number, there is no hard rule; instead, it is defined by the subnet mask. Most people have used a campus network, which typically has a subnet mask of 255.255.255.0. This subnet mask is a 32-bit binary sequence, consisting of a series of 1s followed by a series of 0s, for example: 255.255.255.0 (in binary, it is 11111111.11111111.11111111.00000000). For the Class B address mentioned earlier, since 210.30 is the network number, the remaining 109.134 represents the combination of the subnet number and host number. Since the subnet mask has only the last eight bits as 0, the host number corresponds to the last eight bits of the IP address, which is 134, while the remaining part is the subnet number—109.
ARP Protocol
Do you remember that every data packet in the Ethernet protocol at the data link layer has a MAC address header? We know that every Ethernet card has a unique MAC address, so how does an IP packet know this MAC address? This is the job of the ARP protocol.
The ARP (Address Resolution Protocol) is a resolution protocol. The host does not initially know which interface corresponds to the IP address. When a host wants to send an IP packet, it first checks its ARP cache (an IP-MAC address corresponding table). If the queried IP-MAC pair does not exist, the host sends an ARP broadcast packet to the network, which contains the IP address to be queried. All hosts that receive this broadcast will check their own IP address. If a host finds it matches, it prepares an ARP packet containing its MAC address to send back to the host that sent the ARP broadcast. The broadcasting host will update its ARP cache with the new information (the IP-MAC mapping). The broadcasting host will then use the updated ARP cache data to prepare the data link layer packet for transmission.
A typical ARP cache information can be obtained by using the command “arp -a” on any system:
Interface: 192.168.11.3 --- 0x2
Internet Address Physical Address Type
192.168.11.1 00-0d-0b-43-a0-2e dynamic
192.168.11.2 00-01-4a-03-5b-ed dynamic
This will yield results like this.
This cache is time-limited, generally lasting 20 minutes (in Berkeley-derived systems).
RARP Protocol
When systems with local disks boot, they generally read the IP address from a configuration file on the disk. However, diskless machines, such as diskless workstations, need to use other methods to obtain an IP address.
Every system on the network has a unique hardware address, configured by the network interface manufacturer. The RARP implementation process for diskless systems involves reading the unique hardware address from the interface card and sending a RARP request (a frame of data on the network) to request the IP address for the diskless system from a certain host.
The complexity of the RARP server lies in the fact that it generally has to provide hardware address to IP address mapping for multiple hosts. More complex is the fact that RARP requests are transmitted as a special type of Ethernet data frame. This means the RARP server must be able to send and receive this type of Ethernet data frame.
RARP is used by many diskless systems to obtain an IP address during boot. Implementing RARP is more complex than ARP because RARP requests are broadcast at the hardware level. This means they are not forwarded through routers. In order for diskless systems to boot even when RARP is turned off, multiple RARP servers are typically provided on a single network (a single cable).
“Learning Linux This Way” is a technical book based on the latest Linux system, aimed at readers with no background. It starts with basic Linux knowledge and gradually increases the difficulty, detailing the working principles and configuration methods of various services in the Linux system to meet the requirements of the real production environment for operations personnel, highlighting the practicality of the content. Readers who want to learn the Linux system can click the “Read Original” button to learn more about this book. This book is also suitable for professional operations personnel as a highly valuable reference tool!