Collected and organized all Linux kernel vulnerabilities from January 1, 2022, to February 18, 2023, with data sourced from NVD, totaling 314 vulnerabilities. The analysis of the Linux kernel attack surface is based on CWE types and the subsystems where the vulnerabilities are located.- CWE Statistics
According to publicly available CVE information, a total of 314 vulnerabilities can be categorized into 31 types based on CWE names. The statistics are as follows: 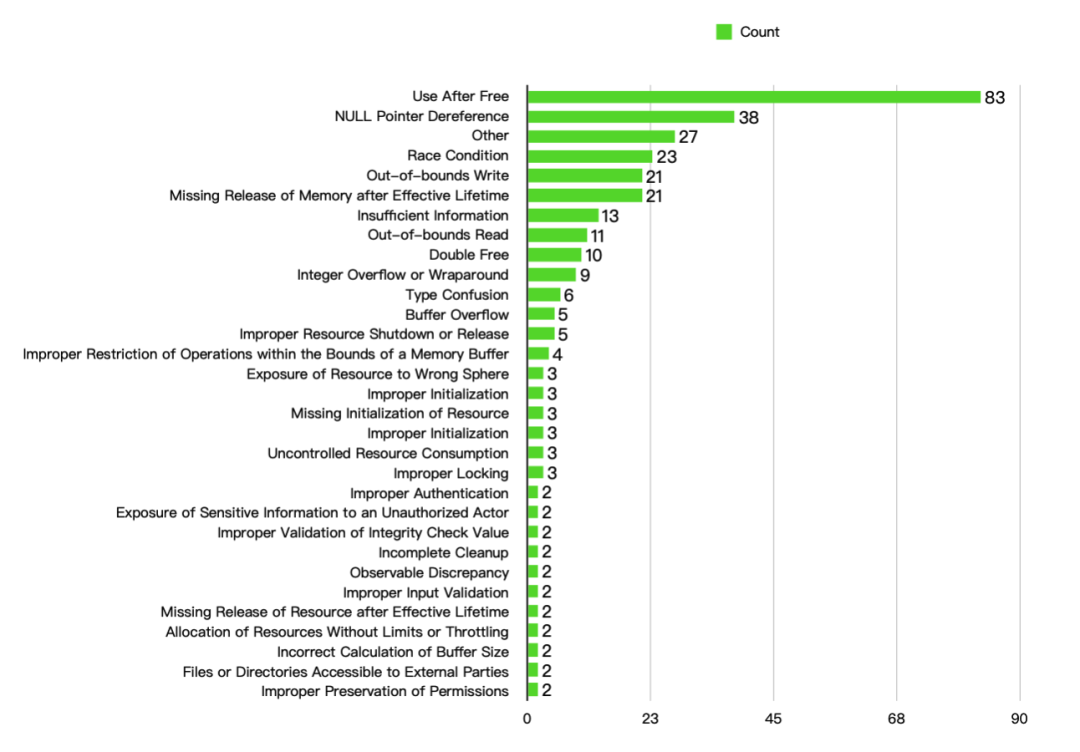 From the above image, it can be seen that the number of Use After Free vulnerabilities is very high, more than double that of the second most common, Null Pointer Dereference. Additionally, for the convenience of drawing statistical graphs, many individual CWE statistics are included in the Other category, totaling 18 vulnerability types, listed in no particular order: 1. Missing Authorization 2. Use of a Broken or Risky Cryptographic Algorithm 3. Improper Privilege Management 4. Use of Insufficiently Random Values 5. Improper Control of Dynamically-Managed Code Resources 6. Release of Invalid Pointer or Reference 7. Improper Handling of Exceptional Conditions 8. Time-of-check Time-of-use (TOCTOU) Race Condition 9. Insecure Default Initialization of Resource 10. Non-exit on Failed Initialization 11. Unchecked Return Value 12. Deadlock 13. Access of Uninitialized Pointer 14. Loop with Unreachable Exit Condition (‘Infinite Loop’) 15. Divide By Zero 16. Incorrect Authorization 17. Incorrect Type Conversion or Cast 18. Improper Validation of Array Index
From the above image, it can be seen that the number of Use After Free vulnerabilities is very high, more than double that of the second most common, Null Pointer Dereference. Additionally, for the convenience of drawing statistical graphs, many individual CWE statistics are included in the Other category, totaling 18 vulnerability types, listed in no particular order: 1. Missing Authorization 2. Use of a Broken or Risky Cryptographic Algorithm 3. Improper Privilege Management 4. Use of Insufficiently Random Values 5. Improper Control of Dynamically-Managed Code Resources 6. Release of Invalid Pointer or Reference 7. Improper Handling of Exceptional Conditions 8. Time-of-check Time-of-use (TOCTOU) Race Condition 9. Insecure Default Initialization of Resource 10. Non-exit on Failed Initialization 11. Unchecked Return Value 12. Deadlock 13. Access of Uninitialized Pointer 14. Loop with Unreachable Exit Condition (‘Infinite Loop’) 15. Divide By Zero 16. Incorrect Authorization 17. Incorrect Type Conversion or Cast 18. Improper Validation of Array Index
Top 10 Vulnerability Count Statistics are as follows:
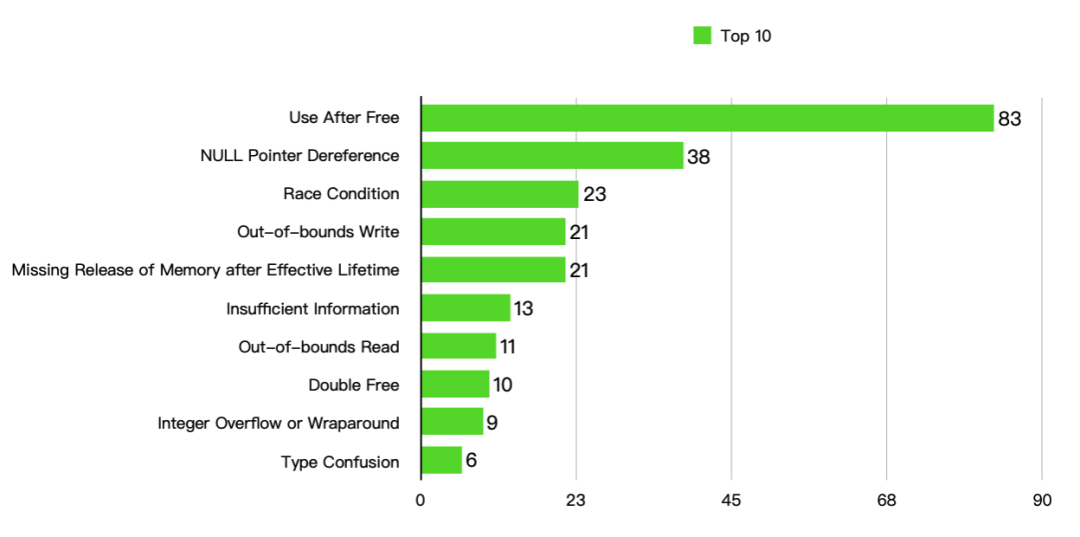
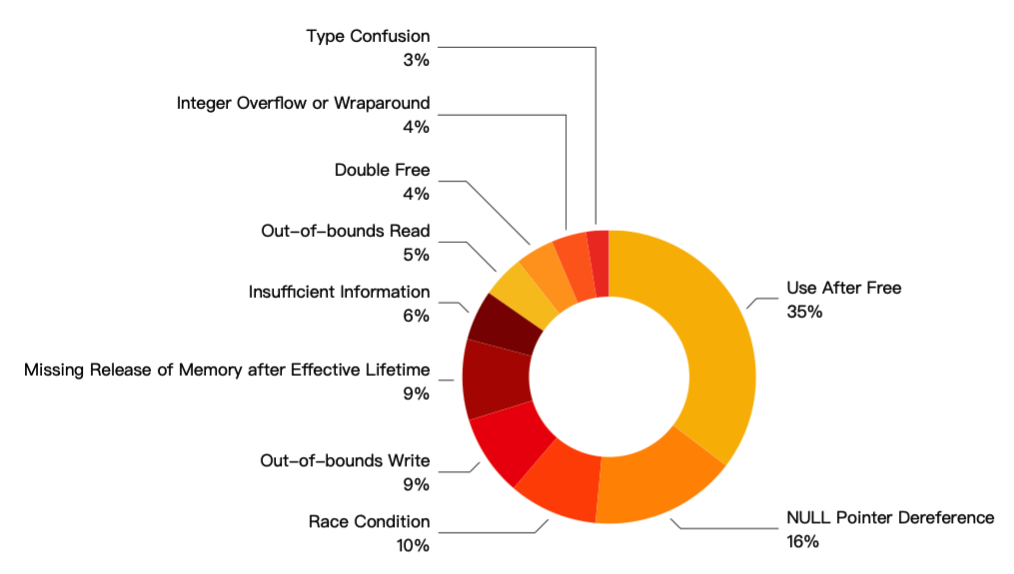
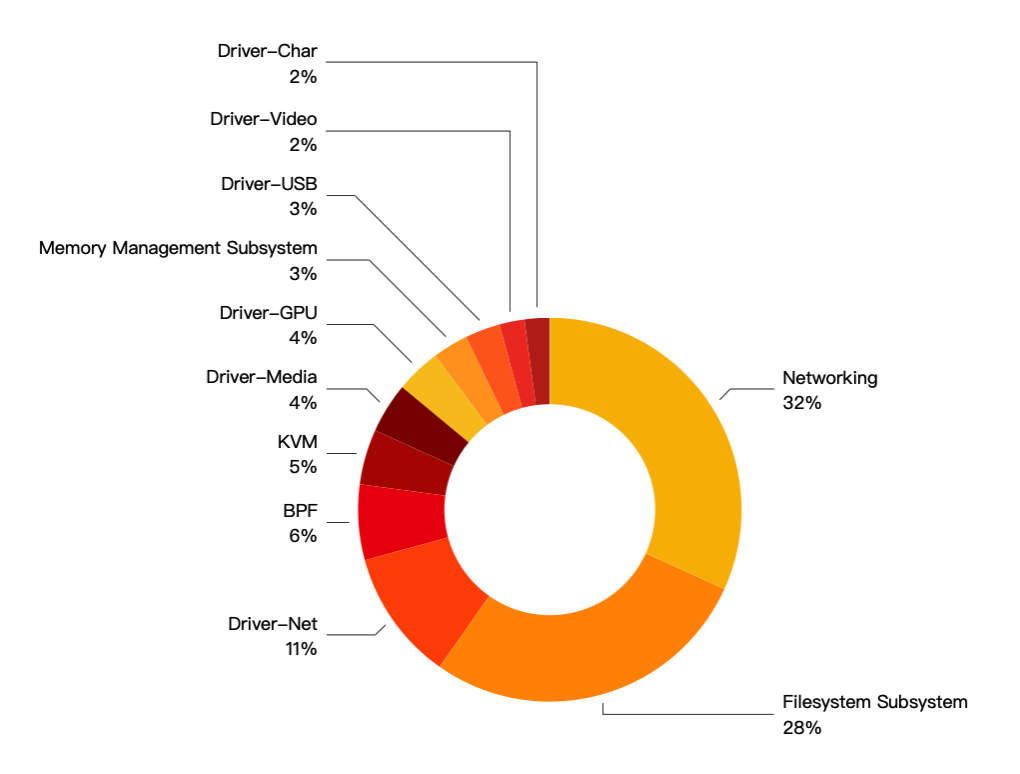
The Top 10 vulnerabilities total 235, accounting for 74.84% of the total number of vulnerabilities. The proportion of each type in the Top 10 is as follows:
- Subsystem Vulnerability Statistics
Analyzing 314 CVE records, excluding those with incomplete descriptions that cannot be located, leaves 297 vulnerabilities. For the convenience of drawing statistical graphs, 267 vulnerabilities belonging to specific subsystems were counted:
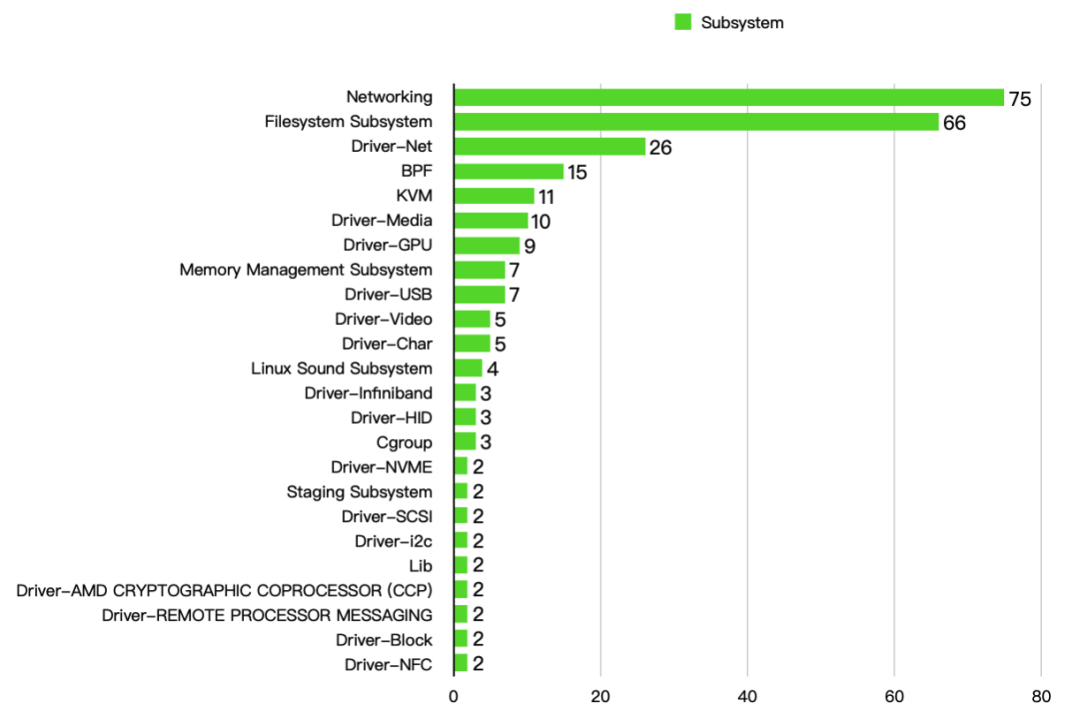
Additionally, 30 vulnerabilities are in separate subsystems or kernel modules, listed in no particular order:
1. HID 2. KPTI 3. SYSCTL Subsystem 4. USB Subsystem 5. Power Supply 6. Driver-Misc 7. Monitor 8. Driver-ATM 9. Driver-Isdn 10. Mgmt-Tester 11. Virtual Devices 12. Driver-Firmware 13. MMU and TLB 14. Events Subsystem 15. Driver-lightnvm 16. Scheduler 17. IPC 18. Driver-VFIO MEDIATED 19. Memory deduplication mechanism 20. X86 ARCHITECTURE 21. Driver-Virt 22. LINUX FOR POWERPC 23. Driver-Vhost 24. DMA 25. Block Subsystem 26. Driver-Bluetooth 27. Workqueue 28. BPF JIT for S390 29. Networking-Bluetooth 30. Driver-SONY MEMORYSTICK
Top 10 kernel subsystem vulnerability statistics are as follows, with Driver-Video and Driver-Char tied for tenth place:
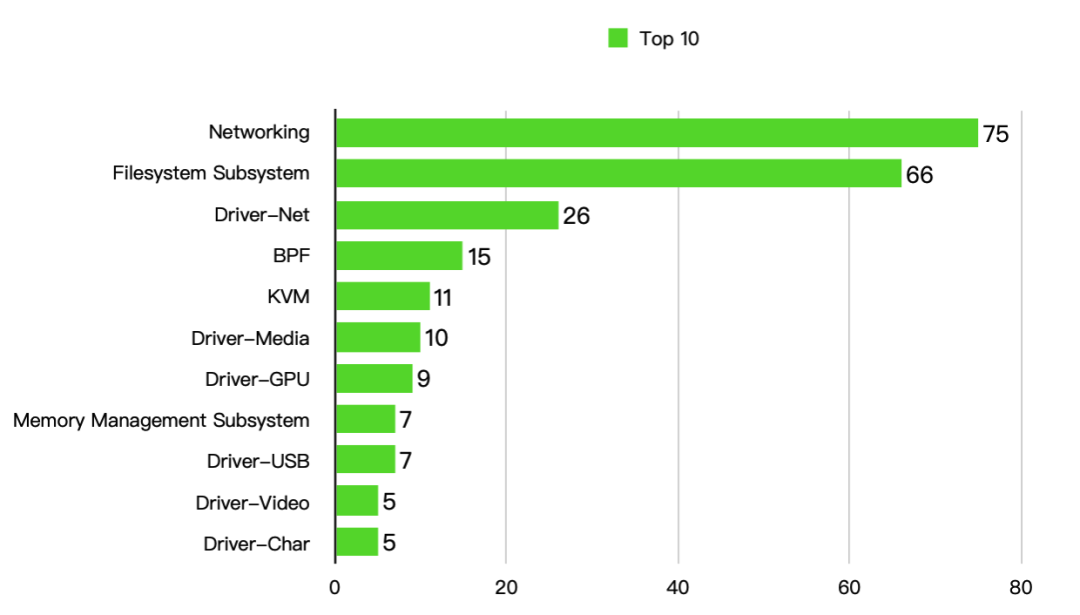
From the above image, it can be seen that the Networking and Filesystem Subsystems have a large number of vulnerabilities, indicating a significant attack surface. The remaining vulnerabilities are mostly also related to kernel drivers:
- Typical Attack Surface Cases
During the analysis of CVE information, several representative vulnerabilities and attack surfaces were summarized, most of which can be easily discovered and exploited. The following list includes:
Uninitialized values of struct members leading to subsequent operations causing vulnerabilities. For example, CVE-2022-29968, CVE-2022-0847
Missing macro definitions or missing permission flags leading to memory permission errors or information leaks. For example, CVE-2022-1353, CVE-2022-0500, CVE-2022-0494
Calling unload class functions and then reusing release class functions, leading to double free. For example, CVE-2022-29156, CVE-2022-28390
Not checking if the returned pointer is null or if the return value has failed. For example, CVE-2022-28356
Integer overflow caused by confusion between unsigned and signed types. For example, CVE-2022-0998
Missing release after valid lifecycle. For example, CVE-2022-27950
Race conditions caused by lack of locking. For example, CVE-2021-4149
Writing beyond the allocated buffer size, leading to heap overflow. For example, CVE-2022-27666
Unchecked array index. For example, CVE-2022-27223
Missing validation of structures before use. For example, CVE-2022-0516
Missing validation of values, not checking if they are zero. For example, CVE-2021-3743
Not zeroing memory after use, leading to kernel information leaks. For example, CVE-2022-0382
Incorrect release order leading to Use After Free, for example, CVE-2022-0487
Preceding functions can return null, but subsequent functions do not check if the return value is null, leading to null pointer dereference. For example, CVE-2022-0286
- Conclusion
From the above analysis, the attack surface of the kernel can be summarized as follows:
The main types of vulnerabilities are UAF, null pointer dereference, OOB Write, OOB Read, race conditions, and missing release after valid lifecycle.
The subsystems with the highest number of vulnerabilities are the networking subsystem, filesystem subsystem, BPF, KVM, and various kernel drivers.
Overall, the Linux kernel places a high emphasis on security. Although some vulnerabilities cannot be used for privilege escalation attacks, they can lead to denial of service and are assigned CVE numbers. However, due to the large scale of the project and varying levels of developer expertise, many low-level security vulnerabilities have emerged, thus providing opportunities for vulnerability discovery in the Linux kernel.