

 The smart vacuum cleaner in your home works right under your nose, while the ‘invisible guest’ watches you through its built-in camera… Recently, a smart vacuum cleaner from a South Korean brand was reported to have security vulnerabilities, allowing hackers to remotely control it and invade personal privacy.
The smart vacuum cleaner in your home works right under your nose, while the ‘invisible guest’ watches you through its built-in camera… Recently, a smart vacuum cleaner from a South Korean brand was reported to have security vulnerabilities, allowing hackers to remotely control it and invade personal privacy. Click the audio to learn more!
Click the audio to learn more!
Originally intended to enhance quality of life, ‘smart homes’ have become ‘spies’ in our lives, which is indeed shocking. The fact that ‘home privacy’ is leaked by ‘smart home’ devices is even more chilling. While smart homes provide us with a more comfortable living experience, their security is increasingly concerning.
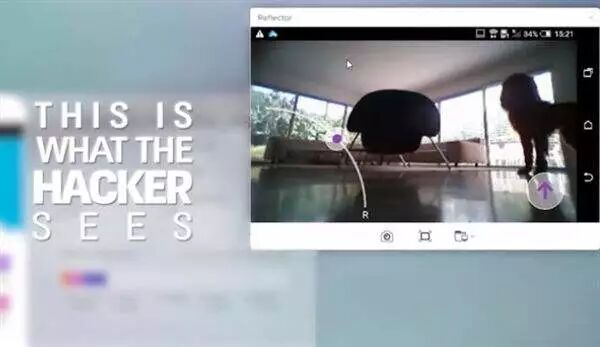
In an experiment, engineers from the 360 Security Team demonstrated how easily a remote camera can be hacked.
“Here is a common household smart camera, currently in working mode, showing real-time footage on the phone. Now I will demonstrate how to exploit vulnerabilities and weak passwords to hack into the camera and display its footage on a computer.”
In less than a minute, he successfully hacked the camera and transmitted the footage to a laptop.

“Let’s check the local folder, where these three files are the recorded video data that was transmitted.”
Subsequently, the engineer demonstrated the process of cracking a smart door lock.
“This smart door lock from a certain manufacturer supports unlocking with an access card. When we open the door, our malicious attacker attempts to authenticate using a spoofed card, which fails. However, when the phone is brought close to the access card in our wallet, the malicious attacker can successfully copy the information from the card after being in close proximity, and then use that information to unlock the door.”
When the reporter searched for ‘camera hacking’ in QQ, numerous related chat groups appeared. After randomly adding a few, it was found that the content involved privacy in smart homes, occasionally sharing what was claimed to be footage from others’ cameras. Some netizens even proactively added the reporter as a friend, asking if they needed scanning software, claiming that these software could hack cameras.
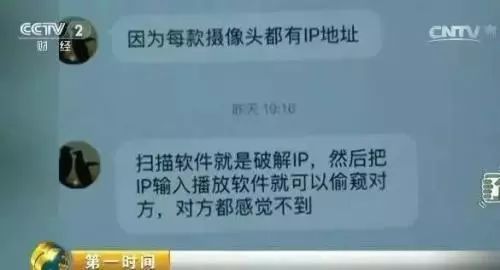
A network seller even sent the reporter a video teaching how to use software to hack into someone else’s camera.
“If I know the serial number and password, and if the password hasn’t been changed, I can log in.”
In some QQ groups, a large number of IP addresses are shared by group owners as ‘gifts’ to attract users. In these groups, new files are added daily, containing three hundred to five hundred IP addresses, each downloaded hundreds of times.
What principle does this software use to scan relevant data and obtain IP addresses?
Gao Sheng, Senior Engineer at the National Internet Emergency Center: This is actually a scanner that uses pre-set accounts or weak passwords to scan the internet, thereby discovering the IP addresses of cameras with vulnerabilities. The weak passwords used are generally common weak passwords provided by manufacturers or short consecutive numbers and letters.
In fact, not only household cameras but also public cameras used for urban management and traffic monitoring have issues that can be accessed using weak passwords. The National Quality Inspection Bureau has conducted quality and safety risk monitoring of smart cameras. Risk assessment experts have determined that the risk level of these smart products is high.
“A high-risk level means that the information security of the entire product is very serious. Currently used cameras have considerable information security risks.”
The National Quality Inspection Bureau collected samples from the market, and the results showed that 32 out of 40 batches had quality and safety hazards. It is these technical vulnerabilities that allow smart home devices to be frequently hacked, and behind this is a gradually forming black market for selling personal privacy.
Wang Yangdong, Head of the Cloud Security Team at 360 Information Security Departmentsuggests: There should be prompt establishment of security standards for smart home products, further strengthening the security testing of products on the market, and exploring the establishment of a credit mechanism for corporate privacy protection.

The trend of smart appliances becoming intelligent and networked has become inevitable. Companies should focus on researching how to protect users’ personal privacy on the path to intelligence, rather than merely emphasizing or exaggerating functionality. Cybersecurity experts also remind users that when purchasing smart home devices, they should choose products from reputable brands and manufacturers.
“For consumers, what can be done is to ensure high password strength. The passwords for daily accounts should be strong. Avoid using common passwords, such as using the same password for a small website account and for Taobao, QQ, etc. Such common passwords can lead to significant risks if the security of that small website is weak and the account password is leaked, potentially affecting all your critical accounts, such as Taobao, WeChat, Alipay, QQ, and bank passwords.”
“Smart homes” are the trend of future social development. As a new industry and emerging phenomenon, ensuring their security is evidently more important than convenience. Since vulnerabilities in ‘smart home’ devices have already been discovered in practical life, they should be promptly addressed. Companies developing and producing ‘smart home’ devices should enhance their security design, and relevant government departments should quickly issue safety standards for ‘smart home’ devices. Devices that do not meet safety standards should be banned from the market. At the same time, relevant authorities should severely crack down on new types of crimes that use ‘smart home’ devices for illegal activities, preventing them from forming a climate and gray market.
Reporter: Guan Xin
Source: China Voice “News Overview”
