IntroductionAfter the “N Room” incident in South Korea, public concern over privacy breaches from surveillance devices has resurfaced. With the rapid development of the Internet of Things (IoT), smart cameras and appliances are increasingly favored. However, some of these convenient IoT devices can also become the “eyes and ears” for criminals, forming a networked, chain-like black market.Through investigative research, it was found that criminals can easily hack into certain smart surveillance devices and sell hacking software and IDs online, exposing countless users’ privacy to others’ surveillance.Video Author: Zhao XuSome Bedrooms No Longer Have SecretsConsidering security and prevention factors, many users have installed cameras in various locations at home and in the office, allowing real-time viewing through mobile apps. These cameras are often left on continuously, with some owners stating, “I can’t be bothered to restart; I never turn them off.”What users believed to be private surveillance footage has, in fact, become “live public broadcasts.”As a reporter posing as a netizen, I joined a social media group named “Surveillance”. Within ten minutes, a group member inquired if anyone wanted to purchase camera IDs, subsequently sending over ten screenshots of surveillance videos, most of which were captured by home cameras, with the most recent timestamp being March 24. These images were set to “self-destruct” after five seconds. The member claimed that camera IDs were “ordinary ones for 85 yuan for 10, and better ones for 175 yuan for 25,” with operational guidance included. After payment, the member sent a list of 24 device names, marked with labels like “living room” and “bedroom”. Following the “instructions”, I downloaded a mobile app and was able to log in to view live surveillance footage.Even more shocking, for just 320 yuan, one could purchase a “hacking software” that would allow users to bypass the need to buy individual camera IDs, enabling quick access to 999 out of 1,000 online camera IDs, essentially a “monthly subscription”.So, how do criminals hack into home cameras and achieve remote control? On one hand, some camera brands use weak passwords for account registration, and some can connect to camera devices without registration, making them easy to hack; on the other hand, hackers use “database dumping” and “credential stuffing” techniques to crack camera IDs.If a user’s network device uses the same login account and password, it can be compromised by “credential stuffing” techniques, turning it into public content. For example, if a large amount of personal user login information is illegally obtained from an email website, these account passwords could very well become the “keys” to hack into that user’s home devices. If a major social media platform or software is hacked, tens of millions or even billions of personal information could be leaked.Cameras, Door Locks, Cars… All Can Be Hacked“The rapid development of IoT has outpaced the security measures for personal privacy protection,” admitted an internet security professional. Compared to the IoT security devices used by enterprises, personal smart cameras, smart door locks, and IoT-enabled private vehicles are all susceptible to remote hacking or physical interference. For instance, if a home’s smart temperature control device is hacked, it could turn “summer” into “winter”, and if a self-driving car is compromised, it could easily lead to traffic accidents.Recently, the National Internet Emergency Center’s Critical Infrastructure Security Emergency Response Center reported that within a span of over half a month, the number of IoT malware attacks targeting specific vulnerabilities reached 67 million, with a single organization attempting attacks on hundreds of thousands of IP addresses. It can be concluded that as long as IoT devices are exposed to the internet, they are at risk of being attacked at any time, and may be repeatedly targeted by different organizations.
The member claimed that camera IDs were “ordinary ones for 85 yuan for 10, and better ones for 175 yuan for 25,” with operational guidance included. After payment, the member sent a list of 24 device names, marked with labels like “living room” and “bedroom”. Following the “instructions”, I downloaded a mobile app and was able to log in to view live surveillance footage.Even more shocking, for just 320 yuan, one could purchase a “hacking software” that would allow users to bypass the need to buy individual camera IDs, enabling quick access to 999 out of 1,000 online camera IDs, essentially a “monthly subscription”.So, how do criminals hack into home cameras and achieve remote control? On one hand, some camera brands use weak passwords for account registration, and some can connect to camera devices without registration, making them easy to hack; on the other hand, hackers use “database dumping” and “credential stuffing” techniques to crack camera IDs.If a user’s network device uses the same login account and password, it can be compromised by “credential stuffing” techniques, turning it into public content. For example, if a large amount of personal user login information is illegally obtained from an email website, these account passwords could very well become the “keys” to hack into that user’s home devices. If a major social media platform or software is hacked, tens of millions or even billions of personal information could be leaked.Cameras, Door Locks, Cars… All Can Be Hacked“The rapid development of IoT has outpaced the security measures for personal privacy protection,” admitted an internet security professional. Compared to the IoT security devices used by enterprises, personal smart cameras, smart door locks, and IoT-enabled private vehicles are all susceptible to remote hacking or physical interference. For instance, if a home’s smart temperature control device is hacked, it could turn “summer” into “winter”, and if a self-driving car is compromised, it could easily lead to traffic accidents.Recently, the National Internet Emergency Center’s Critical Infrastructure Security Emergency Response Center reported that within a span of over half a month, the number of IoT malware attacks targeting specific vulnerabilities reached 67 million, with a single organization attempting attacks on hundreds of thousands of IP addresses. It can be concluded that as long as IoT devices are exposed to the internet, they are at risk of being attacked at any time, and may be repeatedly targeted by different organizations. Industry insiders believe that weak security awareness is a significant vulnerability. “Many people lack awareness of network security or have a false sense of security, thinking that hacking incidents are far removed from them,” said a security expert and senior architect at Qihoo 360. Criminals also purchase the same model products to conduct research and analysis, finding targeted attack methods, which poses greater challenges for security management.Many also use other IoT devices as “spies”: robot vacuums with built-in cameras constantly surveil rooms; smart speakers suddenly emit “mysterious laughter” at night; Apple’s Siri has been reported to upload user recordings to servers without user consent…
Industry insiders believe that weak security awareness is a significant vulnerability. “Many people lack awareness of network security or have a false sense of security, thinking that hacking incidents are far removed from them,” said a security expert and senior architect at Qihoo 360. Criminals also purchase the same model products to conduct research and analysis, finding targeted attack methods, which poses greater challenges for security management.Many also use other IoT devices as “spies”: robot vacuums with built-in cameras constantly surveil rooms; smart speakers suddenly emit “mysterious laughter” at night; Apple’s Siri has been reported to upload user recordings to servers without user consent…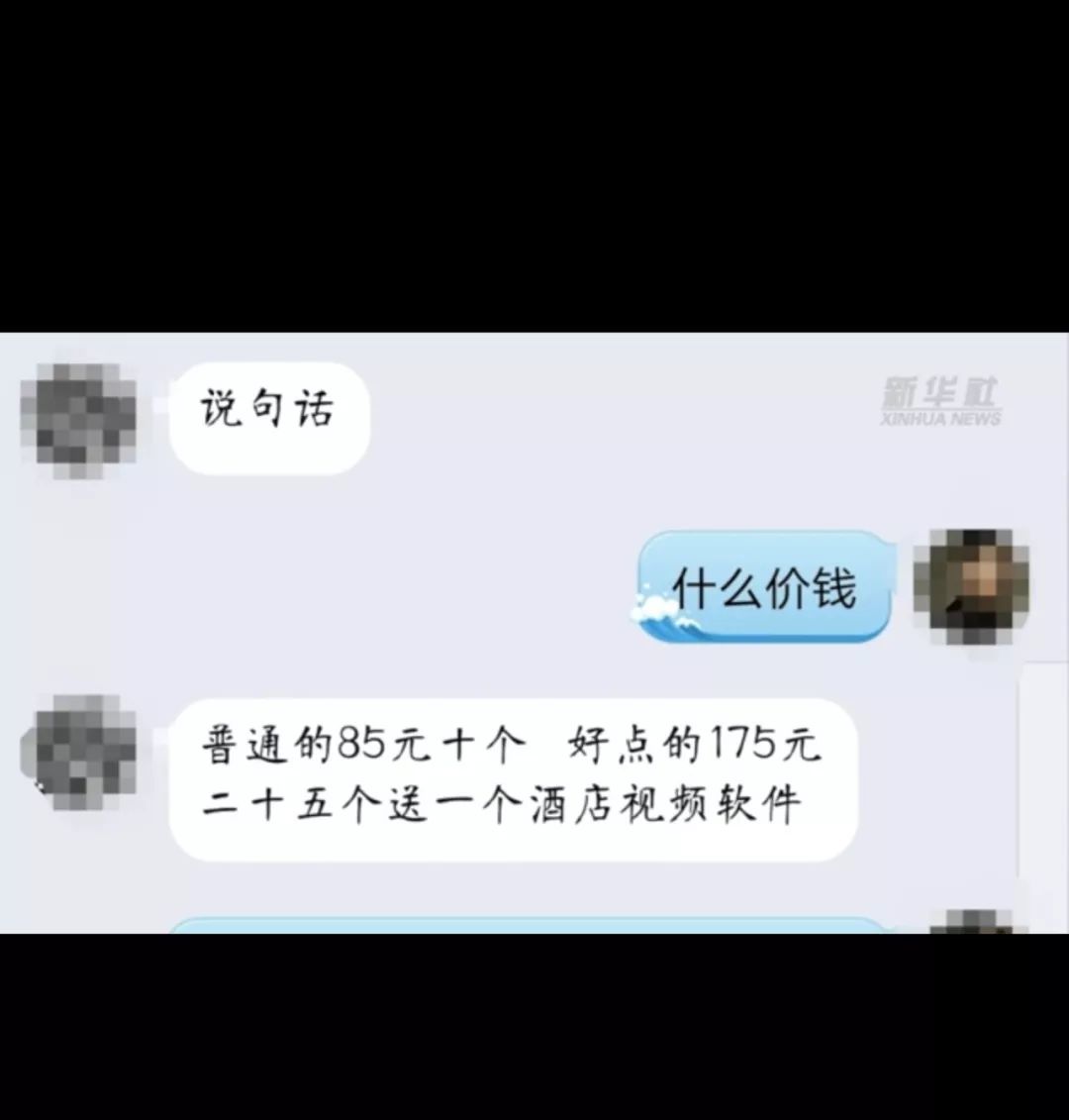 During an undercover investigation, screenshots of conversations with criminals were recorded.The vulnerabilities present in IoT have become a breeding ground for illegal activities. For instance, in the case of privacy cameras, a complete industrial chain has formed behind them, typically consisting of three stages: developing and selling camera hacking tools, attacking network cameras, and proxy selling of camera videos. Each stage has clear divisions of labor and covert methods. Some groups use virtual currencies for transactions to evade regulation, ultimately using camera videos for extortion.Hacking IoT devices to invade privacy is far simpler than the public imagines; some hacking software can be operated with “zero threshold” and “foolproof operation”, allowing installation in just one minute.Armoring IoT PrivacyIllegal activities in the IoT sector pose threats to social order and national security. As related technologies continue to enter practical applications, the scope of attacks by criminals will also increase, making it a long road to combat such illegal activities. Closing the privacy loopholes in IoT requires multi-party joint prevention and control, close collaboration, and the establishment of a multi-layered defense system.Relevant law enforcement officials stated that hacker crime cases remain at a high incidence rate, and efforts should focus on building a coordination and communication mechanism among internet, industry, and public security departments to comprehensively address internet hacker crime issues.Hu Gang, Secretary-General of the Research Center of the China Internet Association, believes that the legislative work on network security should adhere to “rapid establishment and frequent amendments” for efficient and swift legislation to address new types of cybercrime. “Judicial authorities must promptly handle urgent and changing cases involving IoT-related illegal activities,” Hu Gang said.Peng Xinlin, Deputy Director of the Criminal Law Research Institute at Beijing Normal University, suggested that various departments should take joint action to strengthen the crackdown on crimes using IoT devices, while encouraging innovation and development alongside enhanced industry supervision and guidance. Internet users should also enhance their security awareness, strengthen protective measures, and report any clues of hacker illegal activities in a timely manner.Companies should prioritize network security in their office environments, regularly check cameras and other devices, establish a network security protection system, and emphasize employee training on network security, while ensuring software and system vulnerabilities are patched and security updates are maintained throughout the device lifecycle.Experts recommend that internet users manage their accounts and passwords on social media platforms categorically, using different passwords for each platform and opting for high-strength passwords, while regularly updating important network platform passwords. When purchasing IoT devices, it is advisable to buy from reputable manufacturers and legitimate channels, and to choose devices that have undergone security testing.
During an undercover investigation, screenshots of conversations with criminals were recorded.The vulnerabilities present in IoT have become a breeding ground for illegal activities. For instance, in the case of privacy cameras, a complete industrial chain has formed behind them, typically consisting of three stages: developing and selling camera hacking tools, attacking network cameras, and proxy selling of camera videos. Each stage has clear divisions of labor and covert methods. Some groups use virtual currencies for transactions to evade regulation, ultimately using camera videos for extortion.Hacking IoT devices to invade privacy is far simpler than the public imagines; some hacking software can be operated with “zero threshold” and “foolproof operation”, allowing installation in just one minute.Armoring IoT PrivacyIllegal activities in the IoT sector pose threats to social order and national security. As related technologies continue to enter practical applications, the scope of attacks by criminals will also increase, making it a long road to combat such illegal activities. Closing the privacy loopholes in IoT requires multi-party joint prevention and control, close collaboration, and the establishment of a multi-layered defense system.Relevant law enforcement officials stated that hacker crime cases remain at a high incidence rate, and efforts should focus on building a coordination and communication mechanism among internet, industry, and public security departments to comprehensively address internet hacker crime issues.Hu Gang, Secretary-General of the Research Center of the China Internet Association, believes that the legislative work on network security should adhere to “rapid establishment and frequent amendments” for efficient and swift legislation to address new types of cybercrime. “Judicial authorities must promptly handle urgent and changing cases involving IoT-related illegal activities,” Hu Gang said.Peng Xinlin, Deputy Director of the Criminal Law Research Institute at Beijing Normal University, suggested that various departments should take joint action to strengthen the crackdown on crimes using IoT devices, while encouraging innovation and development alongside enhanced industry supervision and guidance. Internet users should also enhance their security awareness, strengthen protective measures, and report any clues of hacker illegal activities in a timely manner.Companies should prioritize network security in their office environments, regularly check cameras and other devices, establish a network security protection system, and emphasize employee training on network security, while ensuring software and system vulnerabilities are patched and security updates are maintained throughout the device lifecycle.Experts recommend that internet users manage their accounts and passwords on social media platforms categorically, using different passwords for each platform and opting for high-strength passwords, while regularly updating important network platform passwords. When purchasing IoT devices, it is advisable to buy from reputable manufacturers and legitimate channels, and to choose devices that have undergone security testing.
Recommended Reading
-
11 new local confirmed cases in one day! Shulan City, Jilin, adjusted to high-risk level
-
Multiple express delivery companies announce price adjustments! The reason is…
-
Today, please keep this guide to confessing your feelings!
-
“Hello, someone has already paid for you!”
-
[Warning] Do you always smell a foul odor while wearing a mask? It could indicate issues with these parts of your body!
Source: Half-Month Talk WeChat Official AccountEditor: Xie PengReviewed by: Xing Ying, Qin Chenyu
