Click the blue words to follow us

In today’s cybersecurity field, SDP is a hot topic. SDP (Software Defined Perimeter) is a security framework developed by the Cloud Security Alliance, based on the concept of zero trust. Every terminal connecting to the server must undergo authentication and authorization before connection, ensuring the trustworthiness of all access. As all access must occur in a trusted environment, it ensures that the core network assets of enterprises are hidden under security protection and not directly exposed to the public network, thereby avoiding security threats to core data assets.
In other words, in the face of the SDP architecture, every visitor is untrusted, and only after verification will they be given the “key” to access the corresponding server. If we compare the server to a “door,” then for the visitor, without a key, they cannot find the corresponding door; even with a key, they can only open the door corresponding to that key. SDP isolates services from insecure networks, effectively improving the security risks faced by enterprises, such as being easily hacked through phishing software or Trojan horses, mobile office scenarios, and threats faced during the gradual migration of traditional data to the cloud, assisting enterprises in achieving a secure transition and enabling them to face the many challenges posed by comprehensive digital construction.
SDP Architecture
In SDP, traditional enterprise boundaries are broken; firewalls are no longer the only boundary of enterprises, and internal networks are logically segmented; similarly, new boundaries need to be established between public clouds and private clouds. SDP adapts to software-defined network architecture, born for the cloud, especially suitable for hybrid networking environments, combining with SD-WAN (Software Defined Wide Area Network) to provide deeper security protection capabilities for enterprise networking.
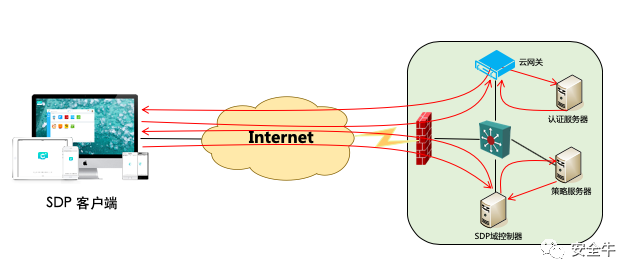
Based on the self-developed SD-WAN cloud network service platform, integrating the capabilities of the SDP controller and SDP host, combining SD-WAN virtual cloud gateways, central nodes, and multi-terminal client network construction and control capabilities, the SDP controller’s capabilities are combined with the central cloud gateway, which provides application protection based on the zero trust model, authorizing specific users accordingly. At the same time, the SDP client adapts to multiple terminal operating systems, allowing all applications authorized for user access to be uniformly displayed across different terminals.
The SDP architecture system includes:
SDP Client
As a C/S type client application and B/S type web application, it provides a unified application access entry, supports application-level access control, supports cross-kernel control calls, and secure management of plugins, achieving a simplified, rapid, and secure integration.
Security Gateway
As the entry point for user authorized access to internal applications, the security gateway isolates external users from internal resources, filtering illegal access.
SDP Domain Controller and Policy Server
Provides registration for gateway devices, hides gateway addresses, avoiding scanning and illegal actions from malicious threat sources.
Authentication Server
Realizes user identity pre-verification and pre-authorization, connects with the internal third-party authentication system of the enterprise, and the client’s request first goes through the authentication server, obtaining authenticated authorization before returning the result to the SDP domain controller.
SDP and Networking Combined Solutions
In the application scenarios of SDP, the most common situation is that an enterprise has a headquarters and one or more geographically dispersed branches, and the physical network (internal network) owned by the enterprise cannot connect these institutions. Employees in external areas need to access enterprise resources when performing work tasks, which may be remote office scenarios or accessing enterprise-owned or personally owned devices in other areas outside the enterprise. Since the SDP architecture naturally adapts to the SD-WAN network architecture, leveraging its own technical advantages, the solution combining SDP with SD-WAN networking provides a zero trust secure network architecture for more enterprises, gaining increasing favor from customers.
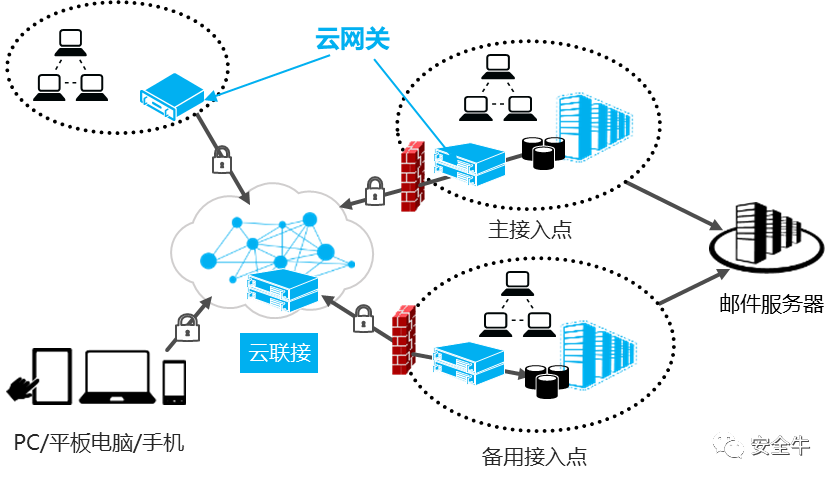
Users can send pre-authorization requests to the SDP controller through different terminals, and the policy controller judges based on preset policies, returning the authentication results to the SDP controller, which then sends the access control list to the client; thereafter, only the cloud gateway within the access rights receives the authentication request. After confirming that the authentication information is correct, the client connects and establishes the access connection.
In the process of organically integrating SDP with networking, the SDP controller still plays the role of the “brain” in the solution, dynamically authenticating the identities of the initiators and assisting in establishing a trusted secure access tunnel between the initiating terminal and the target server. It is worth mentioning that this tunnel is not fixed; rather, it is dynamically constructed and changes with requests, effectively shielding various potential threats in the network and building a more secure network boundary.
SDP Practical Cases and Results
In a financial industry unit’s practice, users completed smooth upgrades of business systems and IT infrastructure to meet the rapidly developing business needs.
The user’s data centers are set in two different provinces, and virtualization technology is used, making it difficult to protect the network boundary through a single firewall; at the same time, many internal servers are in different network segments, and employees urgently need a solution to smoothly use applications across network segments; users hope to effectively achieve boundary protection, ensure the security of data centers in different locations, and implement application-based access authorization to guarantee security during user access to applications.
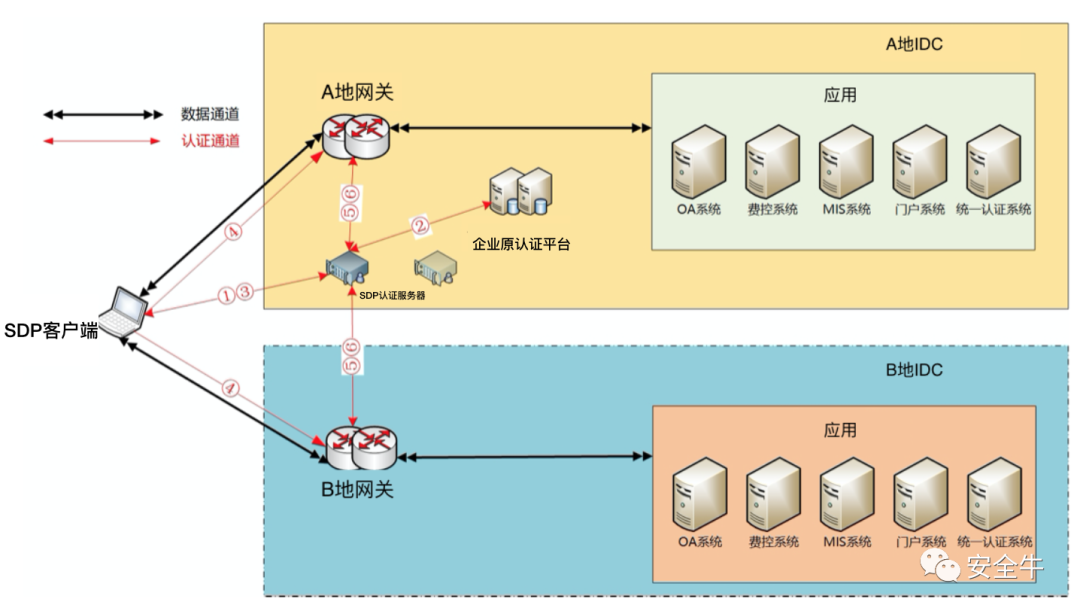
Based on customer needs, an SDP controller is provided, reusing the enterprise’s internal original authentication system to authenticate user identities and establish connections between trusted terminals and security gateways. After a user initiates an access request, the authorized applications in the two different provincial data centers are displayed on the same screen, achieving “what you see is what you use.” The SDP host is placed close to the server, hiding the enterprise’s application servers, and only access that has been authenticated by the SDP authentication server can exchange data with servers in the trusted area.
The following diagram shows the architecture of the SDP deployed in the customer’s environment. The authentication channel and data channel are effectively isolated, allowing access to different segment applications through a single client, fulfilling the customer’s needs.
Results of SDP Case Practice
1. The combination of SDP and networking has helped the financial unit’s internal employees broaden their office model. From traditional internal office access through PCs to secure office access anytime and anywhere via multiple mobile terminals—this transition only requires establishing a secure access tunnel without any other operations, and the tunnel can be securely established with one click, reducing operational complexity and improving efficiency;
2. IT managers within the financial unit do not need to perform complex configurations and management. Compared to the traditional security hardware + VPN deployment model, the combination of SDP and networking can significantly enhance the efficiency of internal IT managers and help enterprises control IT management costs;
3. Different financial enterprises or different departments within the same enterprise have varying security needs. The SDP concept is user-centric; this solution ensures that resources can be flexibly allocated according to user needs and ensures that all security-related operations are executed in the cloud, ensuring that network access is easier to control and more flexible while requiring minimal additional maintenance, perfectly aligning with the needs of medium and large enterprises undergoing digital transformation.
Conclusion
The transformation combining SDP and networking allows enterprise end customers to access applications within the authorized range simply by using the client for verification, without needing to worry about their permission ownership. Enterprise IT managers are no longer burdened by complex authentication rules, improving usability and maintainability while ensuring security.

This article is authored by Chen Ju, a master’s degree holder with over 10 years of industry technical experience and over 8 years of product experience. He joined Di’an Technology in 2008, mainly responsible for product technical direction, currently serving as a director and deputy general manager of Shanghai Di’an Technology Co., Ltd. For many years, he has been dedicated to promoting the development of Di’an Technology’s SD-WAN products, managing the product lifecycle, and maintaining the product line.
Related Reading
In the era of “zero trust”, VPN will inevitably be replaced by SDP
How Software Defined Perimeter (SDP) Mitigates Common Security Threats
CSA GCR Release | “SDP Implementation Compliance Technical Guide for Level 2 Protection”

