Recently, researchers discovered a new type of information-stealing malware written inRust that can extract sensitive data fromChromium-based andGecko-based web browsers.
Part01
Overview of the Malware Situation
This malware, namedMyth Stealer, represents a significant evolution in cybercriminal strategies, combining modern programming techniques with traditional social engineering methods to steal user credentials and financial information.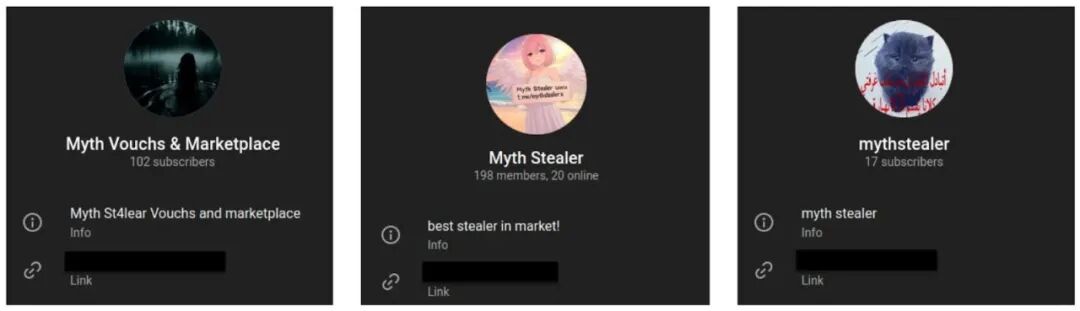
Sincelate December 2024, this malware has been distributed through a well-organized fraudulent website andTelegram channels. Initially, the malware attracted users with a free trial, then shifted to a subscription model, allowing cybercriminals to purchase weekly or monthly access using cryptocurrency andRazer Gold.
The threat actors maintain multiple Telegram channels for distribution, updates, and even posting “customer” reviews, showcasing the professionalism of their cybercriminal infrastructure.
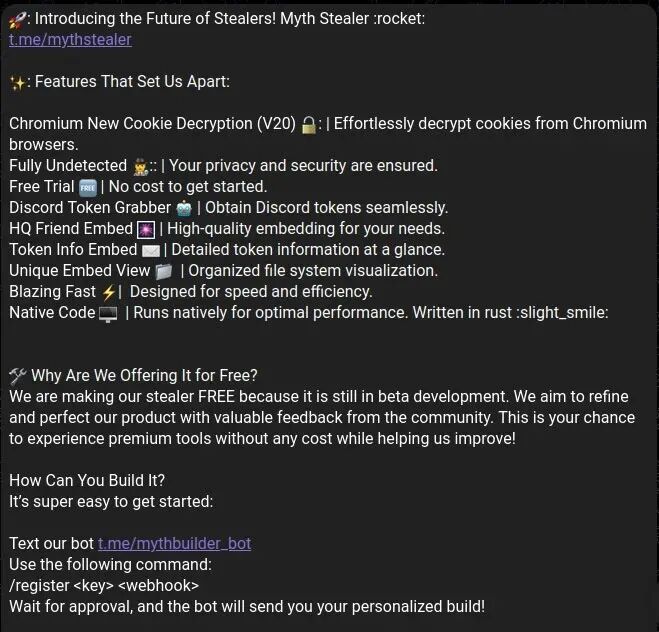
Trellix researchers discovered this previously undetected malware sample during routine proactive threat hunting activities, revealing its complex architecture and evasion capabilities. The research team found that the malware targets communication platforms and various globally used professional browsers such asChrome, Firefox, Edge, Opera, Brave, andDiscord.
Its distribution mechanism relies on social engineering, with attackers disguising the malware as legitimate game software, cheat tools, or beta versions of popular games. Victims typically encounter the malware throughpassword-protected RAR archives, with passwords often following predictable patterns, such as the game name followed by “beta” or “alpha”.
In some cases, threat actors post malicious links in online forums and even provide reports showingzero detections fromVirusTotal to establish credibility within gaming communities.
Part02
Advanced Infection and Evasion Mechanisms
The technical complexity of Myth Stealer is evident through its multi-layered infection process and comprehensive evasion strategies. Upon execution, Myth Stealer uses a loader component to display a realistic fake window to the victim while decrypting and executing the actual stealer payload in the background.
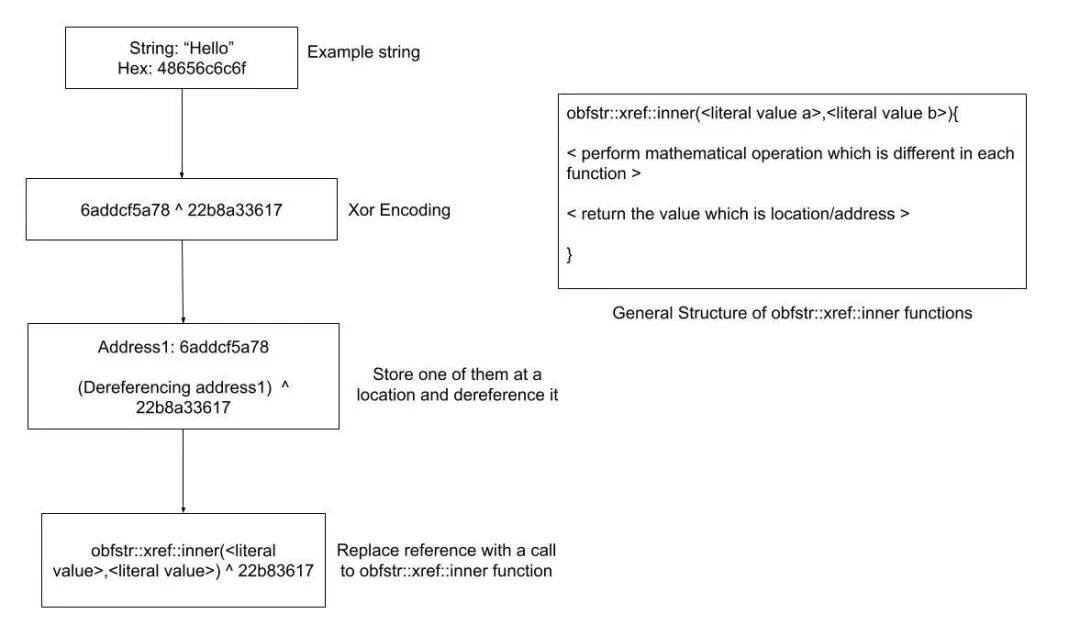
These deceptive interfaces utilize Rust libraries such as<span><span>native-windows-gui</span></span>, <span><span>egui</span></span>, or<span><span>native_dialog</span></span> to create visually convincing application windows that mask the malicious activities occurring behind the scenes. The stealer component itself is a 64-bit DLL file with complex anti-analysis features. Notably, it employs the Rust library<span><span>obfstr</span></span> for string obfuscation, converting readable strings into complex XOR operations, significantly increasing the difficulty of reverse engineering.
The malware also evades sandbox detection by checking for specific usernames and system files typically associated with analysis environments; upon detection of such events, it immediately terminates execution.
For Chromium-based browsers, Myth Stealer employs a particularly clever remote debugging feature to evade detection. The malware launches the browser process with specific parameters, including<span><span>--remote-debugging-port=9222</span></span>, <span><span>--remote-allow-origins=*=</span></span>, and<span><span>--headless</span></span>, to establish a debugging session. This allows it to access browser data directly without using file-based extraction methods. In recent versions, the malware attempts to use Windows’s<span><span>ShellExecuteW</span></span> API in conjunction with<span><span>runas</span></span><code><span><span> parameter to</span></span><strong><span><span> elevate privileges</span></span></strong><span><span>, thereby enhancing its ability to access protected browser databases.</span></span>
Its persistence mechanism is equally complex: it creates a file named<span><span>winlnk.exe</span></span> in the user’s<span><span>AppData\Roaming</span></span> directory while establishing a custom registry entry that associates a forged<span><span>.lnkk</span></span> file extension with the malware executable. This method ensures that the malware remains active after system reboots while keeping a low profile, evading standard security monitoring focused on traditional persistence techniques.
References:
New Rust Based InfoStealer Extracts Sensitive Data from Chromium-based Browsershttps://cybersecuritynews.com/new-rust-based-infostealer-extracts-sensitive-data/
Recommended Reading

Radio Discussion