
The ping command is one of the most frequently used network commands in Ethernet network basics. Generally, we only use its basic functions. Today, let’s take a detailed look at the 7 basic uses of the ping command. Master these, and you’ll become a pro!
6. Usage of ping -r count
7. How to Batch Ping Hundreds to Thousands of IP Addresses
1. Introduction to the Basic of Ping Command
In networking, ping is a powerful TCP/IP tool. Its main functions are:
1. To check network connectivity and analyze network speed.
2. To obtain the server IP from a domain name.
3. To determine the operating system used by the other party and the number of routers the data packet has passed based on the TTL value returned by ping.
We usually use it to ping an IP address directly to test network connectivity.
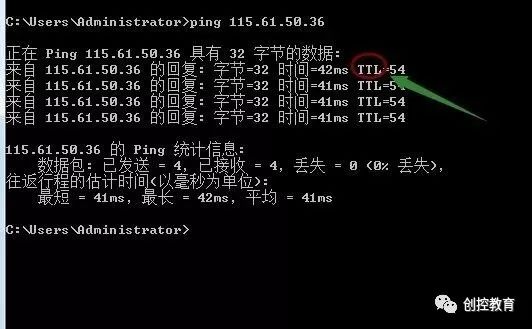
For example, directly ping an IP address or gateway, and if the ping is successful, it will show the above data. Some friends may ask what bytes=32; time<1ms; TTL=128 means.
Bytes value: The size of the data packet, which is in bytes.
Time value: Response time. The smaller this time, the faster your connection to this address.
TTL value: Time To Live, indicating how long the DNS record exists on the DNS server. It is a value in the IP protocol packet that tells the router when the data packet should be discarded.
We can roughly determine whether the target system is a Windows series or UNIX/Linux series based on the size of the TTL value returned by Ping.
Thus, the general TTL values are:
100~130ms for Windows systems;
240~255ms for UNIX/Linux systems.
Of course, today we mainly focus on the other references of ping.
Besides directly pinging the IP address to verify network connectivity and speed, the ping command has these uses.
Continuously ping a specified computer until interrupted by the administrator.
This indicates that the computer is connected to the router and the network is performing well.PressCtrl+Cto stop the continuous ping, and it will summarize the number of packets sent and whether they were successful.
Ping -a resolves the computer name and NetBIOS name. You can ping its IP address to resolve the hostname. When you encounter an IP but don’t know which device it is, you can use ping -a to find out its hostname.
By default, only four packets are sent. This command allows you to define the number of packets sent, which is very helpful for measuring network speed. For example, if I want to test the average return time of sending 10 packets, the fastest time, and the slowest time, I can find out through the following:
From the above, I can see that during the process of sending 10 packets to 47.93.187.142, all 10 were returned without loss. Among these 10 packets, the fastest return speed was 32ms, the slowest was 55ms, and the average speed was 37ms. This indicates that my network is good.
If the network is poor, such as in a monitoring system that is very laggy, the test results may show some packet loss. If the loss is significant, it indicates that the network is not good, providing a straightforward judgment on the network condition.
Ping -l size: Send a data packet of specified size to the target host.
By default, Windows sends a data packet size of 32 bytes, and the maximum size it can send is 65500 bytes. If the size of the data packet sent at once is greater than or equal to 65500 bytes, it may cause the receiving computer to crash. Therefore, Microsoft has limited this value; this parameter can be very powerful when combined with other parameters, such as an attacker can use it with the -t parameter to perform a DOS attack. (So it has risks, do not use it lightly on others’ computers).
For example: ping -l 65500 -t 211.84.7.46
This will continuously execute the ping command to the IP address until interrupted by the user with Ctrl+C.
This will continuously send data packets of 65500 bytes to the computer at 211.84.7.46. If you only have one computer, it may not have much effect, but if there are many computers, it can completely paralyze the other side, causing severe network congestion, demonstrating its significant power.
6. Usage of Ping -r count
This command records the outgoing and returning data packet routes in the “Record Route” field, probing the number of routes passed, but can only track up to 9 routes.
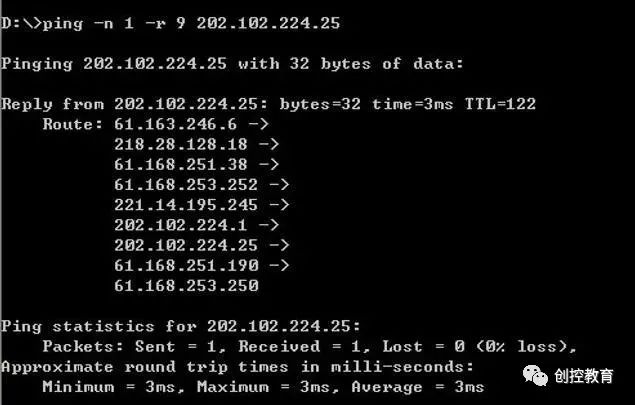
ping -n 1 -r 9 202.102.224.25 (send one data packet, record up to 9 routes)
It will display the 9 routes passed, as shown in the image. This means it can track the 9 routes that the IP address has passed, allowing for quick fault location during troubleshooting.
7. How to Batch Ping Multiple IP Addresses
For a subnet with many IP addresses, if checking each one is troublesome, we can directly batch ping the subnet to determine which IP address has a problem at a glance.
First, look at the code, just enter in the command line:
for /L %D in (1,1,255) do ping 10.168.1.%D
Modify the IP address range to the one you want to check.
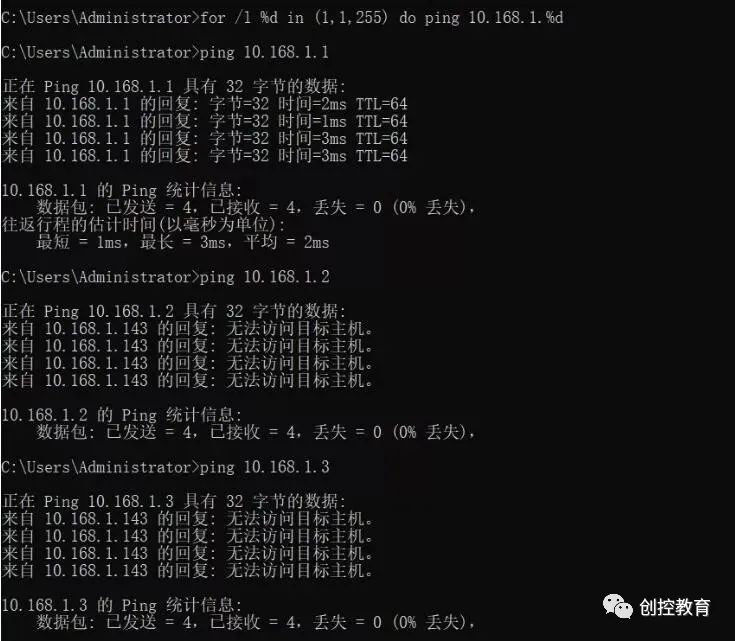
After entering the batch command, it will automatically ping all IP addresses in the subnet until completed.
Then what does this code “for /L %D in(1,1,255) do ping 10.168.1.%D” mean?
The (1,1,255) in the code indicates the start and end of the subnet, which is to check all IP addresses between 192.168.1.1 and 192.168.1.255, incrementing by 1 each time until all 255 IPs are checked.
Although the above command can batch ping addresses, it can be cumbersome to view the results when the number of displayed results is large. Let’s upgrade it with the following code.
for /L %D in (1,1,255) do ping -n 10.168.1.%D >>a.txt
Note that the IP address is variable; you can fill in the subnet you need to test, and a.txt can also be changed to any name you prefer.
This will redirect the results into the a.txt file. After all IP checks are completed, open a.txt and search for “TTL=” to find the addresses that are reachable; addresses without “TTL=” are unreachable, as shown in the image.
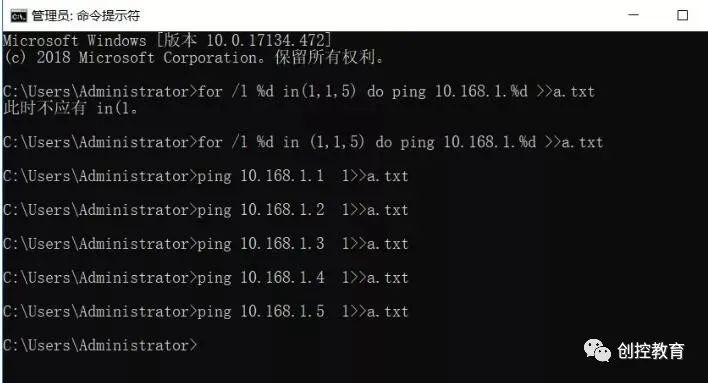
After opening, just search for addresses without TTL.
3. Further Upgrade of Ping Subnet Command
Many people might say that this still requires searching, which is not too convenient. Is there a simpler method? The answer is definitely yes; let’s look at the code.
for /l %D in (1,1,255) do (ping 192.168.1.%D -n 1 && echo 192.168.1.%D>>ok.txt || echo 192.168.1.%D >>no.txt)
This code will separate the reachable and unreachable IPs into two files, which is quite convenient, as shown in the image:
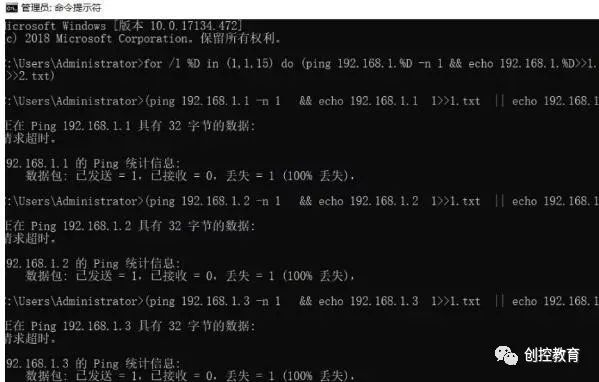
This code is very practical and can be used in large networks. Just be careful while entering it, but don’t worry; you can bookmark this article and copy the code later, changing the IP addresses as needed.
4. Ultimate Method for Ping Subnet Command
The three codes mentioned above are all for batch checking IP addresses within the same subnet. However, in actual projects, there may also be a need to check IP addresses from different subnets simultaneously. So what to do?
There is a method to batch check unplanned IP addresses simultaneously. Let’s look at the code:
for /f %D in (ip.txt) do (ping %D -n 1 && echo %i>>ok.txt || echo %D >>no.txt)
Notice that there is an additional ip.txt file. You need to prepare this file yourself, writing the addresses you want to ping into it. This way, you can ping over 1000 IP addresses, and the code will read the addresses from this file and place the results into two files. I won’t provide a screenshot here, as it’s easy to understand.
The files generated by the above code will be in your command line’s default directory. That is, if your command line state is:
“c:\windows\system32>” then the generated files will be in the system32 directory. If it is “c:\” then the files will be at the root of the C drive. You can adjust this based on your actual situation.

(Content sourced from the internet, copyright belongs to the original author)
Disclaimer:If there are copyright issues, please contact for removal!No individual or organization bears related legal responsibilities.
Recommended Reading:
Wuhan, Stay Strong [Stay Home, Learn PLC Together]











