
Author: Lan Lan
Source: Warm Blue Notes
This article mainly reviews common attacks on TCP/IP, providing at least a basic understanding.
Introduction
1. IP Spoofing
What is IP?
In a network, every device is assigned an address. This address is like the home address of Xiao Lan, “number room“, where the “number” corresponds to the entire subnet, and the “room” corresponds to the number assigned to the computers within the subnet. This is the address in the network. The “number” corresponds to the network number, and the “room” corresponds to the host number, making the overall address a IP address.
What can we know from an IP address?
With an IP address, we can determine the location of the server being accessed. This allows us to send messages to the server. Generally, the message sent by the sender first passes through the hub of the subnet, is forwarded to the nearest router, and then accesses the next router based on the routing location until it reaches the destination.
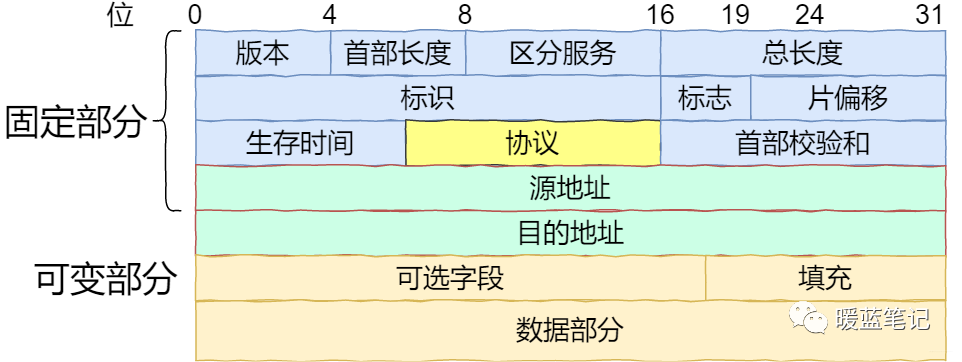
IP Header Format
IP Spoofing Technology
Deception, trickery, entrapment!
IP spoofing technology is the technique of forging the IP address of a certain host. By disguising the IP address, a host can impersonate another host, which often has certain privileges or is trusted by other hosts.
Assuming there is a legitimate user (1.1.1.1) who has established a normal connection with the server, the attacker constructs TCP data for the attack, disguising their IP as 1.1.1.1, and sends a TCP segment with the RST flag to the server. When the server receives such data, it considers the connection from 1.1.1.1 to be erroneous and clears the established connection from the buffer.
At this point, if the legitimate user 1.1.1.1 sends legitimate data again, the server no longer has such a connection, and the user must re-establish the connection. During the attack, a large number of forged IP addresses are sent to the target with RST data, preventing the server from servicing legitimate users. Although IP address spoofing attacks are quite difficult, we should be aware that such attacks are very widespread, and intrusions often start with this type of attack.
2. SYN Flooding
Introduction to SYN Flooding
Denial of Service attacks (DDoS) have been a threat since the 1970s and continue to cause immeasurable losses to organizations worldwide. SYN Flood is one of the most classic DDoS attack methods on the internet, first appearing around 1999, with Yahoo being one of the most famous victims at that time. SYN Flood attacks exploit the vulnerabilities of the TCP three-way handshake, allowing attackers to incapacitate the target server at a low cost, making it difficult to trace.
SYN Flood is a common DOS (Denial of Service) and DDOS (Distributed Denial of Service) attack method. It exploits the flaws in the TCP protocol by sending a large number of forged TCP connection requests, exhausting the CPU or memory resources of the attacked party, ultimately leading to the inability to provide normal services.
Principle of TCP SYN Flood Attack
TCP SYN Flood attacks utilize the TCP three-way handshake (SYN -> SYN/ACK -> ACK). Assuming the connection initiator is A and the connection acceptor is B, where B is listening on a certain port (Port) for connection requests from A, the process is illustrated in the following diagram, with A on the left and B on the right.
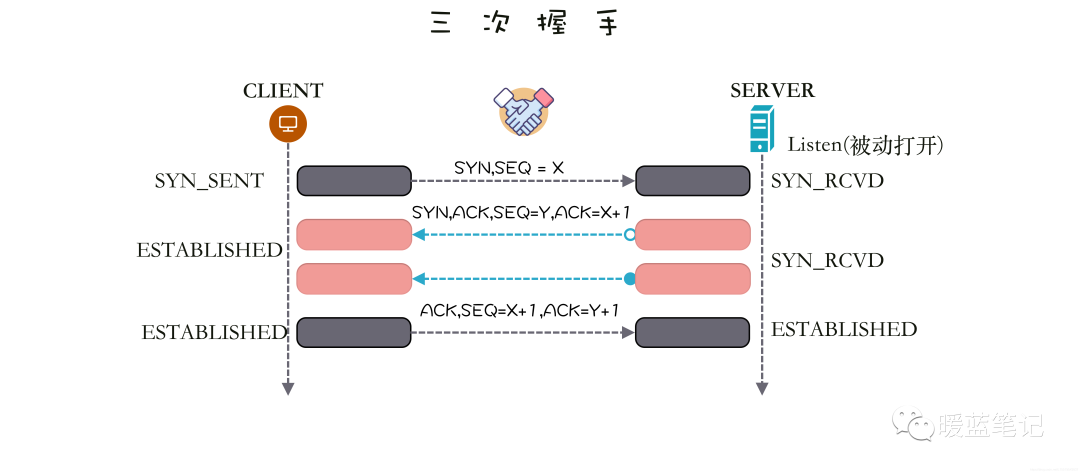
A first sends a SYN (Synchronization) message to B, requesting B to prepare to receive data; B responds with a SYN-ACK (Synchronization-Acknowledgement) message to A, which serves two purposes:
-
To confirm to A that it is ready to receive data,
-
And to request A to also prepare to receive data. At this point, B has confirmed its readiness to A and is waiting for A’s confirmation, putting the connection in a half-open state; A then sends an ACK (Acknowledgement) message back to B, confirming that it is also ready to receive data, thus completing the three-way handshake and establishing the connection.
Have you noticed that the key point is whether both parties have entered the ready to receive messages state as per each other’s request? This confirmation mainly relies on the sequence number that both parties will use. TCP ensures that messages arrive at the receiving application in the order they were sent by using the sequence number to mark the order of message transmission.
TCP is a duplex connection, supporting bidirectional communication, meaning both parties can send messages to each other simultaneously. The SYN and SYN-ACK messages open a one-way communication channel from A to B (B learns A’s sequence number); the SYN-ACK and ACK messages open a one-way communication channel from B to A (A learns B’s sequence number).
The above discussion assumes both parties are honest and communication is normal.
However, in reality, the network may be unstable, leading to packet loss, causing handshake messages not to reach the other party, or the other party may deliberately not follow the rules, delaying or not sending handshake confirmation messages.
Assuming B provides services through a certain TCP port, when B receives A’s SYN message, it actively responds with a SYN-ACK message, putting the connection into a half-open state. Since B is unsure whether the SYN-ACK message sent to A or A’s ACK message will be lost in transit, it sets a Timer for each pending half-open connection. If the time exceeds and A’s ACK message is not received, B will resend the SYN-ACK message to A until the retry exceeds a certain number of times, at which point it will give up.
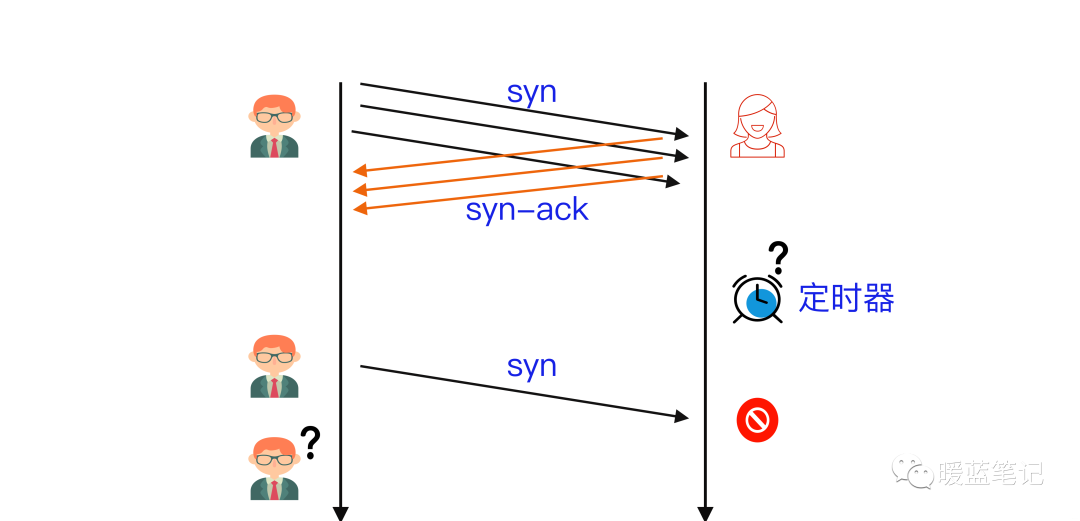
To help A connect smoothly, B needs to allocate kernel resources to maintain half-open connections. When B faces a massive number of connections from A, as shown in the diagram, a SYN Flood attack is formed. The attacking party A can control bots to send a large number of SYN messages to B without responding to ACK messages, or simply forge the Source IP in the SYN messages, causing B’s SYN-ACK messages to be lost, leading to B being occupied by a large number of half-open connections that cannot be completed, until resources are exhausted and it stops responding to normal connection requests.
3. UDP Flooding
UDP flooding is also a type of denial of service attack, sending a large number of User Datagram Protocol (UDP) packets to the target server, aiming to overwhelm the device’s processing and response capabilities. Firewalls protecting the target server may also be exhausted due to UDP flooding, leading to denial of service for legitimate traffic.
How does UDP Flood attack work?
UDP Flood primarily exploits the steps taken by the server to respond to UDP packets sent to one of its ports. Normally, when a server receives a UDP packet on a specific port, it goes through two steps:
-
The server first checks if there is a program running that is listening for requests on the specified port.
-
If no program is receiving packets on that port, the server responds with an ICMP (ping) packet to notify the sender that the destination is unreachable.
For example, suppose today Xiao Lan wants to contact a hotel, and when the hotel customer service receives the call, they first check the list of rooms to ensure Xiao Lan is in a guest room, then transfer the call to Xiao Lan.
First, the receptionist receives a call from the caller requesting to connect to a specific room. The receptionist then needs to check the list of all rooms to ensure the guest is available and willing to answer the call. Coincidentally, if suddenly all the phone lines light up at once, they will quickly become overwhelmed.
When the server receives each new UDP packet, it processes the request through these steps, utilizing server resources in the process. Each UDP message sent will contain the IP address of the source device. During this type of DDoS attack, the attacker typically does not use their real IP address but instead forges the source IP address of the UDP packets, preventing the attacker’s true location from being exposed and potentially saturating the response data packets from the target server.
As the target server utilizes resources to check and respond to each received UDP packet, when it receives a large number of UDP packets, the target’s resources may quickly be exhausted, leading to denial of service for normal traffic.
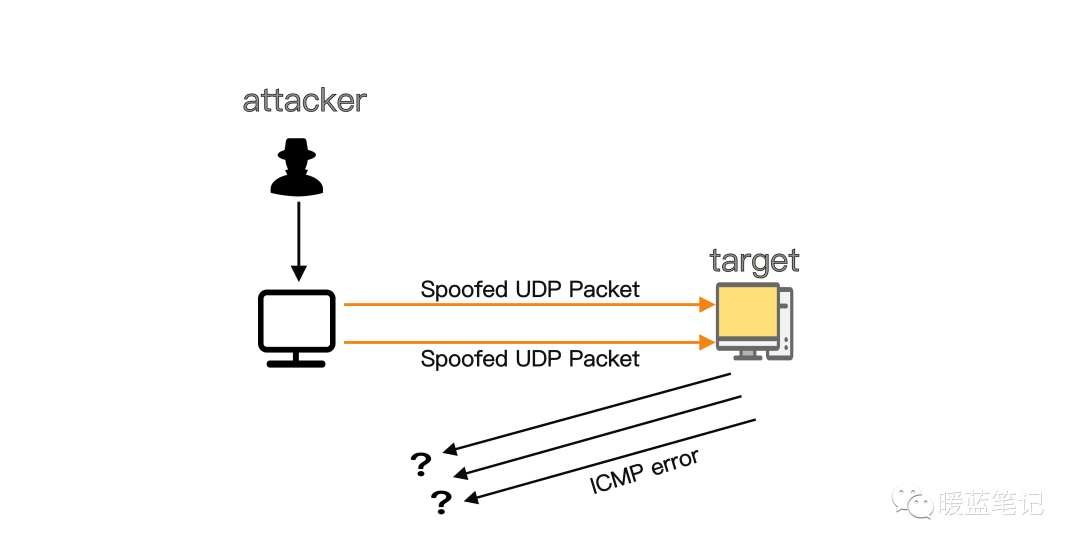
How to mitigate UDP flood attacks?
Most operating systems partially limit the response rate of ICMP packets to interrupt DDoS attacks that require ICMP responses. One downside of this mitigation is that during an attack, legitimate packets may also be filtered. If the capacity of the UDP Flood is high enough to saturate the state table of the target server’s firewall, any mitigation occurring at the server level will be insufficient to handle upstream bottlenecks on the target device.
4. TCP Reset Attack
In a TCP reset attack, the attacker sends forged messages to one or both parties in the communication, instructing them to immediately disconnect, thereby interrupting the connection between the two parties. Normally, if a client detects that the arriving segment is incorrect for the relevant connection, TCP will send a reset segment, leading to a rapid teardown of the TCP connection.
TCP reset attacks exploit this mechanism by sending forged reset segments to the communicating parties, tricking them into prematurely closing the TCP connection. If the forged reset segment is completely realistic, the receiver will consider it valid and close the TCP connection, preventing the connection from being used for further information exchange. The server can create a new TCP connection to restore communication, but it may still be reset by the attacker. Fortunately, the attacker requires some time to assemble and send the forged segments, so generally, this attack is only lethal for long connections; for short connections, the information exchange is often completed before the attack can take effect.
In a sense, forging TCP segments is relatively easy because TCP/IP does not have any built-in methods to verify the identity of the server. Some special IP extension protocols (such as IPSec) can indeed verify identity, but they are not widely used. Clients can only receive segments and, if possible, use higher-level protocols (such as TLS) to verify the identity of the server. However, this method does not apply to TCP reset packets because TCP reset packets are part of the TCP protocol itself and cannot be verified using higher-level protocols.
5. Simulation Attack
The following experiment was conducted on the
OSXsystem; please test on other systems as needed.
Now let’s summarize what needs to be done to forge a TCP reset packet:
-
Sniff the exchanged information between the two communicating parties.
-
Intercept a packet with the
ACKflag set to 1 and read itsACKnumber. -
Forge a TCP reset packet (with the
RSTflag set to 1) whose sequence number equals theACKnumber of the intercepted packet. This is the ideal scenario, assuming the speed of information exchange is not very fast. In most cases, to increase the success rate, multiple reset packets with different sequence numbers can be sent continuously. -
Send the forged reset packet to one or both parties to interrupt the connection.
For simplicity, we can use the local computer to communicate with itself via localhost and then perform a TCP reset attack on itself. The following steps are needed:
-
Establish a TCP connection between two terminals.
-
Write an attack program that can sniff the data exchanged between the two terminal windows.
-
Modify the attack program to forge and send reset packets.
Now let’s officially start the experiment.
Establishing a TCP Connection
You can use the netcat tool to establish a TCP connection, which is pre-installed on many operating systems. Open the first terminal window and run the following command:
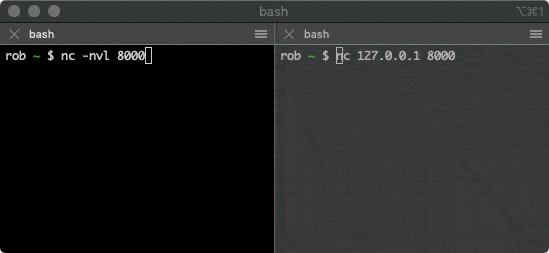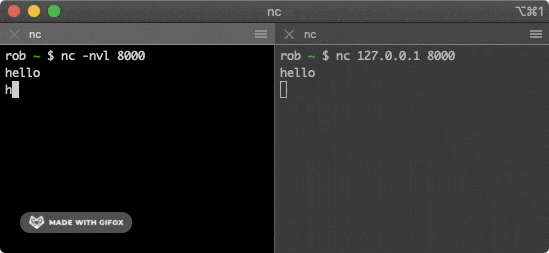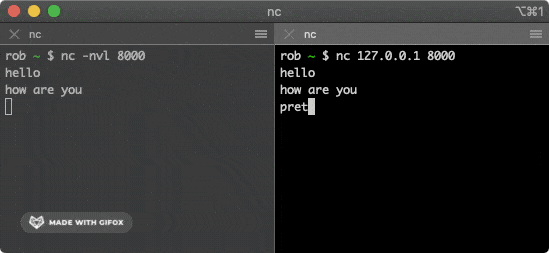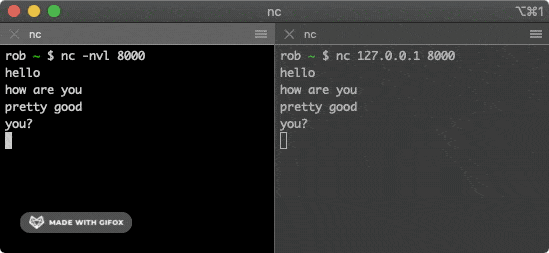
$ nc -nvl 8000
This command will start a TCP service listening on port 8000. Then open the second terminal window and run the following command:
$ nc 127.0.0.1 8000
This command will attempt to establish a connection with the service above. Typing some characters in one of the windows will send them through the TCP connection to the other window and print them out.
Sniffing Traffic
Write an attack program using the Python networking library scapy to read the data exchanged between the two terminal windows and print it to the terminal. The code is relatively long; below is a part of it, with the core of the code calling scapy‘s sniffing method:
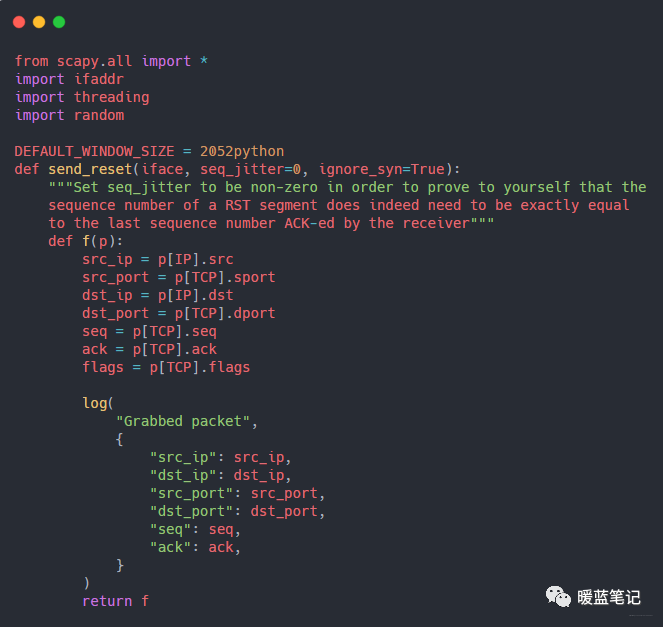
This code tells scapy to sniff packets on the lo0 network interface and record detailed information about all TCP connections.
-
iface: Tells
scapyto listen on thelo0(localhost) network interface. -
lfilter: This is a filter that tells
scapyto ignore all packets that do not belong to the specified TCP connection (both parties arelocalhostand the port number is8000). -
prn:
scapyuses this function to operate on all packets that meet thelfilterrules. The above example simply prints the packets to the terminal; the function will be modified later to forge reset packets. -
count: The number of packets
scapyneeds to sniff before returning.
Sending Forged Reset Packets
Next, we will modify the program to send forged TCP reset packets to conduct a TCP reset attack. Based on the previous analysis, we only need to modify the prn function to check the packets, extract the necessary parameters, and use these parameters to forge and send TCP reset packets.
For example, suppose the program intercepts a packet from (src_ip, src_port) to (dst_ip, dst_port) with the ACK flag set to 1 and an ACK number of 100,000. The attack program should:
-
Since the forged packet is a response to the intercepted packet, the source
IP/Portof the forged packet should be the destinationIP/Portof the intercepted packet, and vice versa. -
Set the
RSTflag of the forged packet to 1 to indicate that this is a reset packet. -
Set the sequence number of the forged packet to the
ACKnumber of the intercepted packet, as this is the next sequence number the sender expects to receive. -
Call
scapy‘ssendmethod to send the forged packet to the sender of the intercepted packet.
For my program, I just need to uncomment this line and comment out the line above it to launch a full attack. After setting up the TCP connection as in step 1, open a third window to run the attack program, and then type some strings in one of the TCP connection terminals; you will find that the TCP connection is interrupted!
Further Experiments
-
You can continue to use the attack program to experiment by adjusting the sequence number of the forged packets to see what happens, whether it indeed needs to be exactly the same as the
ACKnumber of the intercepted packet. -
Open
Wiresharkto listen on thelo0network interface and use the filterip.src == 127.0.0.1 && ip.dst == 127.0.0.1 && tcp.port == 8000to filter out irrelevant data. You can see all the details of the TCP connection. -
Send data streams more quickly over the connection to make the attack harder to execute.
6. Man-in-the-Middle Attack
In a scenario where Zhu Bajie wants to confess to Xiao Lan, he writes a letter to her, but a third party, Xiao Hei, intercepts the letter and alters it, causing disruption between them. This meddler is the man-in-the-middle, executing a man-in-the-middle attack. Now let’s continue discussing what a man-in-the-middle attack is.
What is a Man-in-the-Middle?
The man-in-the-middle attack, abbreviated as MITM attack, refers to an attacker creating independent connections with both ends of the communication and exchanging the data received, making both ends believe they are directly conversing through a private connection, while in fact, the entire session is fully controlled by the attacker. Let’s illustrate this with a diagram:
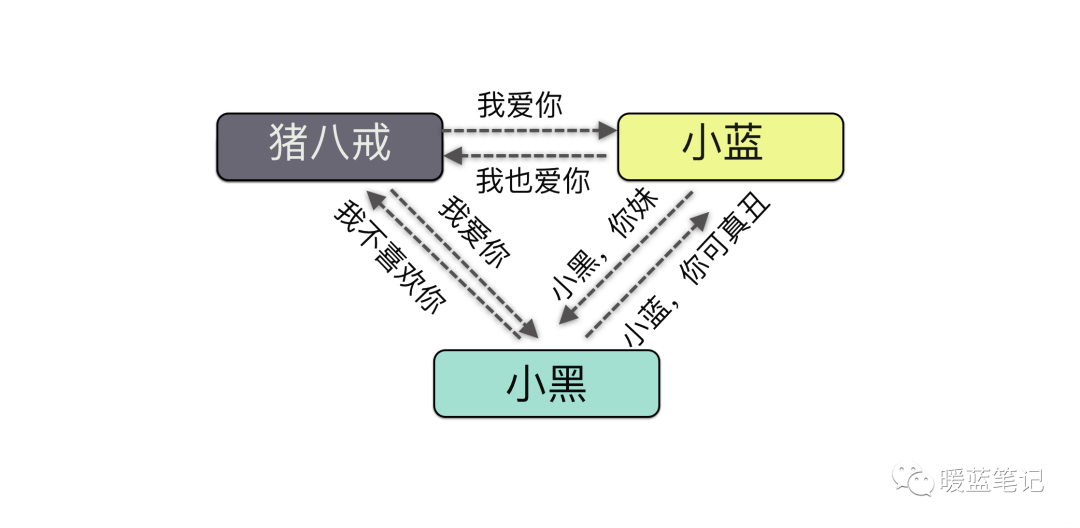
From this diagram, we can see that the man-in-the-middle is actually the attacker. Through this principle, there are many practical applications, for example, when you browse unhealthy websites on your phone, it may prompt you that the site may contain viruses, asking whether to continue visiting or take other actions.
Principle of Man-in-the-Middle Attack
For example, I signed a labor contract with the company, and each person has a copy of the contract. If someone alters the contract content, how can I verify its authenticity? I would have to find a professional institution for authentication, which naturally incurs costs.
In the security field, there is a saying: We cannot eliminate cybercrime; we can only find ways to increase the cost of committing cybercrime. Since we cannot eliminate such situations, we should find ways to increase the cost of committing crimes. Today, we will briefly understand basic network security knowledge, which is also a frequent interview topic.
To avoid situations where both parties do not trust each other’s words, a third-party institution is introduced, which holds the original contract. As long as this institution does not engage in insider theft, the contract remains relatively secure.
What if the third-party institution is lax or prone to errors?
Even though we have given the original contract to a third-party institution, to prevent internal personnel from altering it, what measures should be taken?
One feasible method is to introduce a hash algorithm. The contract and its hash are provided together. To simplify the understanding of the hash, you can think of it as a function that encrypts the original text, producing a unique hash value. If the original text changes even slightly, the hash value will change.
What are some common hash algorithms?
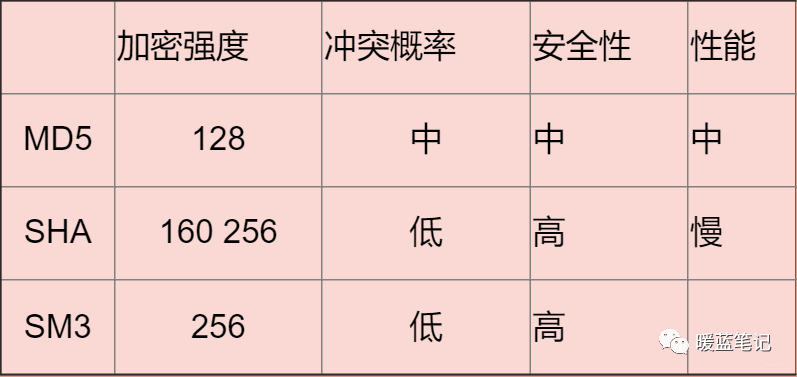
Currently, commonly used encryption algorithms include message digest algorithms and secure hash algorithms (SHA). MD5 converts any length of text into a 128-bit hash value, but in 2004, MD5 was proven to be prone to collisions, meaning two different original texts can produce the same hash. This effectively gives hackers a backdoor to easily forge hashes.
Therefore, in most cases, the SHA algorithm is chosen.
What if there is an insider?
It seems that the situation is secure in theory, as it prevents contract tampering. However, if an employee has the authority to modify both the contract and the hash, it becomes a matter of time before they cause trouble, as no system can completely prevent employees from accessing sensitive information unless such information does not exist. So, can we consider storing the contract and the hash separately?
How to ensure that employees do not modify the contract?
This is indeed quite difficult, but there are always more solutions than difficulties. We can keep the contract in the hands of both parties and the hash with a third-party institution, making tampering more difficult.
What if an employee colludes with a user?
It seems that relying on a third-party institution is still not effective, as there is still a significant risk. Therefore, we need to find new solutions, leading to the emergence of digital signatures and certificates.
Digital Certificates and Signatures
For example, Sum and Mike sign a contract. Sum first calculates the hash of the contract using the SHA algorithm, then encrypts the hash with his private key, obtaining a digital signature. Sum provides Mike with the original contract, the signature, and the public key.
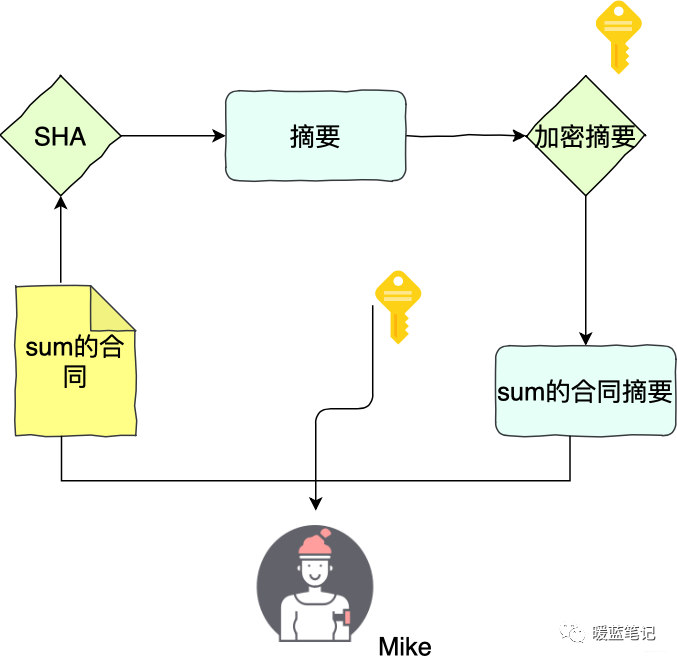
If Sum wants to prove that the contract belongs to Mike, he must use Mike’s public key to decrypt the signature and obtain the hash x, then Mike calculates the SHA hash of the original text Y, and compares x and Y. If they are equal, it is considered that the data has not been tampered with.
In this process, Mike cannot modify Sum’s contract because modifying the contract requires not only changing the original text but also altering the hash, which requires Mike’s private key, a password unique to Sum, while the public key is the password Sum shares with others.
In summary, data encrypted with a public key can only be decrypted with a private key, and data encrypted with a private key can only be decrypted with a public key. This is asymmetric encryption.
Symmetric and Asymmetric Encryption
Privacy protection? It’s not to scare everyone; information is transparent, but we should try to maintain personal privacy. Today, we will learn about symmetric and asymmetric encryption.
First, read this character “key”; it is pronounced “yao”. I used to think so too, but it is actually pronounced “yue”.
Symmetric Encryption
As the name suggests, symmetric encryption uses the same key (secret key) for both the encryption and decryption parties. Specifically, the sender encrypts the information to be sent using the corresponding encryption algorithm and secret key; for the receiver, they use the decryption algorithm and the same secret key to unlock the information, thus being able to read it.
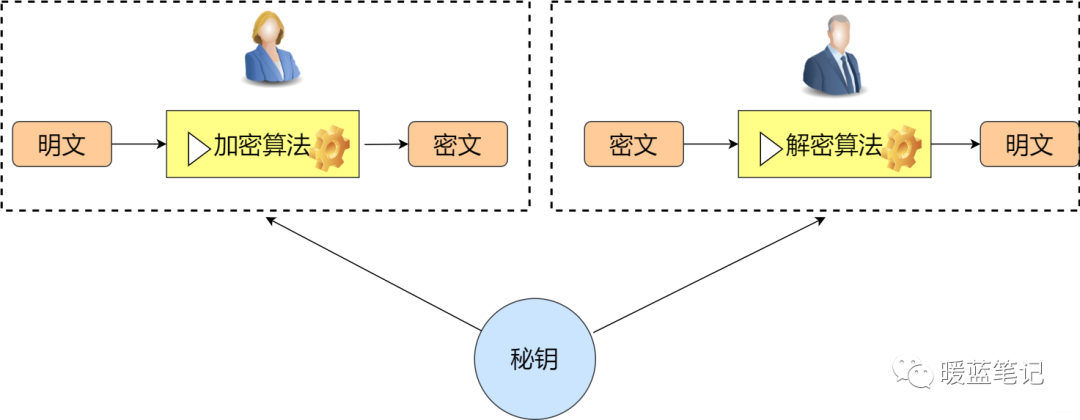
Common Symmetric Encryption Algorithms
-
DES
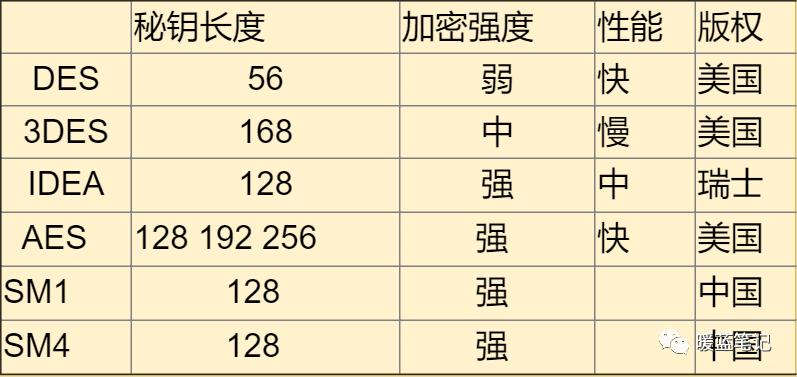
DES uses a key that is superficially 64 bits, but only 56 bits are actually used in the algorithm; the remaining 8 bits can be used for parity and are discarded in the algorithm. Therefore, the effective key length of DES is 56 bits, commonly referred to as a 56-bit key length. Assuming the key is 56 bits, using a brute-force attack, the number of keys is 2 to the power of 56, which would take about a year to decrypt if executed once per nanosecond. Of course, no one does this. DES is no longer considered a secure encryption method mainly because its 56-bit key is too short.
-
IDEA
International Data Encryption Algorithm. The key length is 128 bits, and the advantage is that there are no patent restrictions.
-
AES
After DES was cracked, AES was introduced shortly after, offering three lengths: 128 bits, 192 bits, and 256 bits. To ensure performance is not significantly affected, 128 bits is usually chosen.
-
SM1 and SM4
The previous algorithms are foreign; we have independently researched the national secret algorithms SM1 and SM4. Both are national standards, and the algorithms are public. The advantage is strong support and recognition from the state.
Let’s summarize a few:
Asymmetric Algorithms
In symmetric encryption, the sender and receiver use the same secret key. In asymmetric encryption, the sender and receiver use different keys. The main problem it addresses is preventing leaks during the key negotiation process. For example, in symmetric encryption, Xiao Lan sends a message and tells you the password is 123balala. It is easy for others to intercept the password. In asymmetric encryption, Xiao Lan tells everyone the password is 123balala, but for the man-in-the-middle, it is useless because they do not have the private key. Therefore, asymmetric keys mainly solve the problem of key distribution. See the diagram below:

In fact, we often use asymmetric encryption, such as when setting up a big data platform with multiple servers like Hadoop, which involves key distribution. Similarly, when setting up a Docker cluster, related asymmetric encryption algorithms are also used.
Common Asymmetric Encryption
-
RSA (RSA Encryption Algorithm)
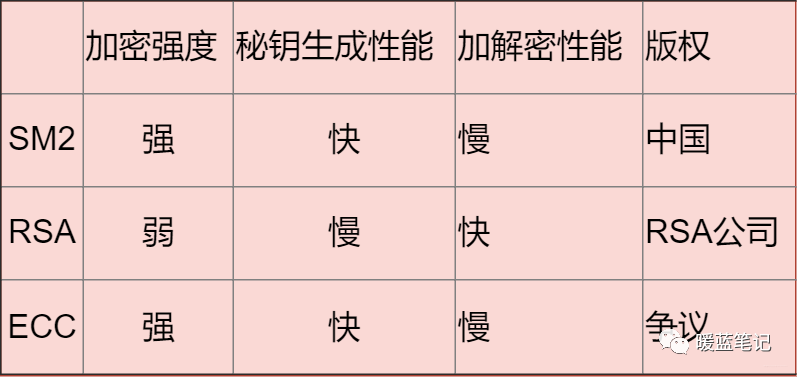
The advantage is that it is relatively fast; if a higher encryption difficulty is desired, a long key is needed.
-
ECC
Based on elliptic curves, it is currently the strongest asymmetric encryption algorithm.
-
SM2
Also designed based on elliptic curve problems. Its greatest advantage is state recognition and strong support.
Comparison of the three:
Hash Algorithms
This should be more familiar to everyone. For example, we often use MD5 checksums; in many cases, I do not use it for encryption but to obtain a unique ID. In system development, storing various password information for users is usually done through hash algorithms, ultimately storing their hash values.
Common Hashes
-
MD5
MD5 can generate a 128-bit message digest and is currently the most widely used hash algorithm. You can refer to various application scenarios. Although its uniqueness has been compromised due to algorithm flaws, in most scenarios, this does not pose a security issue. However, if the length is not limited (32 characters), I still do not recommend continuing to use MD5.
-
SHA
Secure Hash Algorithm. SHA is divided into SHA1 and SHA2 versions. The algorithm’s idea is to receive a plaintext segment and convert it into a ciphertext in an irreversible manner, which can be simply understood as taking a string of input (called pre-image or information) and transforming it into a shorter, fixed-length output sequence, known as the hash value (also called message digest or message authentication code).
-
SM3
National secret algorithm SM3. Its encryption strength is comparable to SHA-256. It mainly receives strong support from the state.
Summary:
In conclusion, in most cases, symmetric encryption is used, which provides good security. If distributed key distribution is needed, consider asymmetric encryption. If reversible computation is not required, then hash algorithms should be used. Recently, I have been looking into this area due to demand, diving into information security, and hoping I won’t have to buy shampoo in the future. Thank you all for reading!
There is still a question: if Sum denies having given Mike the public key and the contract, it would be a problem.
Therefore, it is necessary for Sum to have sufficient credibility for what he has done, which introduces the need for third-party institutions and certificate mechanisms.
The reason certificates have credibility is that the issuer of the certificate has credibility. So if Sum wants Mike to acknowledge his public key, Sum will not directly give the public key to Mike but will provide a certificate containing the public key issued by a third-party institution. If Mike also trusts this institution, and it is legally recognized, then the trust relationship is established.
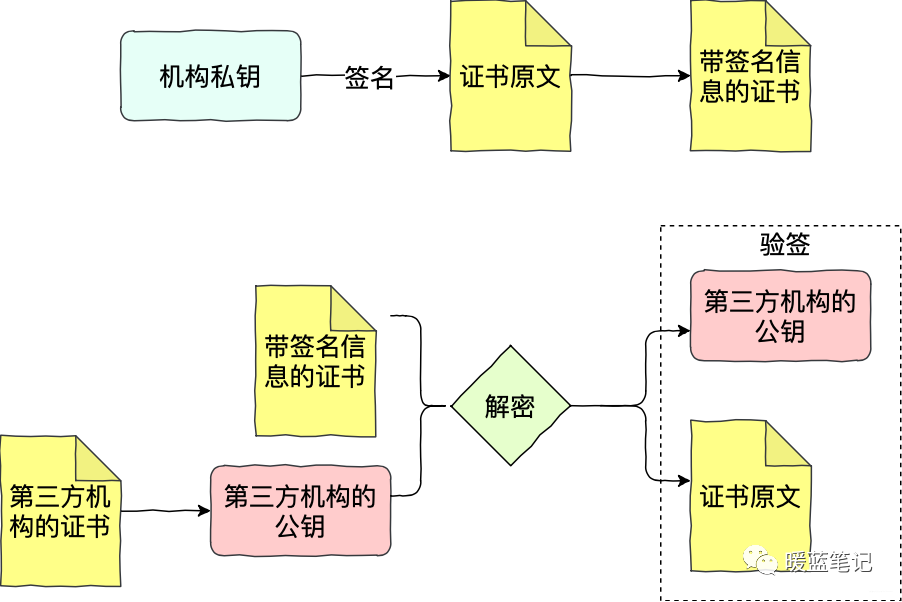
As shown in the diagram above, Sum submits his application to the institution, generating the original text of the certificate. The institution signs Sum’s application original (first calculating the hash of the original text and then encrypting it with its private key), obtaining a certificate with signature information. Mike receives the certificate with signature information and decrypts it using the public key of the third-party institution to obtain the hash of Sum’s certificate and the original text of the certificate. With the hash and original text of Sum’s certificate, Mike can perform signature verification. If the verification passes, Mike can confirm that Sum’s certificate was indeed issued by the third-party institution.
Using this mechanism, neither party can deny the contract. The core of this solution is the need for a third-party credit service institution to provide credit endorsement. This creates a fundamental trust chain; if the trust in the third-party institution collapses, such as being hacked, the entire trust chain will also break.
To make this trust chain more robust, it is necessary to create a longer trust chain, avoiding single-point trust risks.
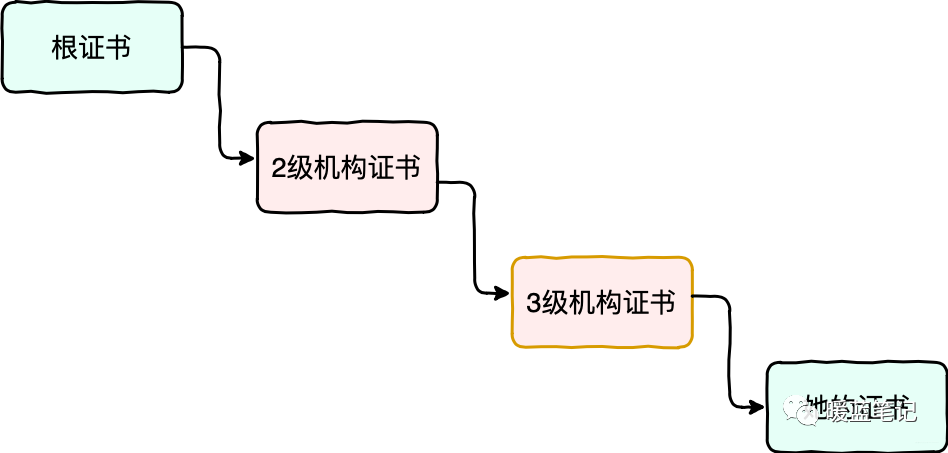
In the diagram, the root certificate authority with the best reputation provides the root certificate, then the root certificate authority issues certificates to secondary institutions; the secondary institution issues certificates to tertiary institutions; and finally, the tertiary institution issues Sum’s certificate.
To verify the legality of Sum’s certificate, the public key in the tertiary institution’s certificate must be used to decrypt the digital signature of Sum’s certificate.
To verify the legality of the tertiary institution’s certificate, the secondary institution’s certificate must be used to decrypt the digital signature of the tertiary institution’s certificate.
To verify the legality of the secondary institution’s certificate, the root certificate must be used to decrypt it.
This forms a relatively longer trust chain. If one party wants to cheat, it is very difficult unless all institutions in the chain collude to commit fraud.
How to avoid Man-in-the-Middle Attacks?
Now that we understand the principle of man-in-the-middle attacks and their dangers, let’s look at how to avoid them. We have all encountered situations like the one below:
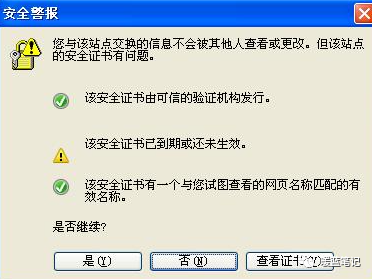
In many cases, encountering this interface indicates a man-in-the-middle attack, requiring timely monitoring of security certificates. The famous GitHub website has also suffered from man-in-the-middle attacks:
To avoid man-in-the-middle attacks, the main methods currently are:
-
Clients should not easily trust certificates: because these certificates are likely to be from a man-in-the-middle.
-
Apps can pre-embed certificates locally: meaning we have some certificates locally in advance, so other certificates cannot take effect.
7. DDoS
In summary, many of the attacks described above are DDoS attacks, so let’s briefly summarize the content related to this attack.
In fact, major global internet companies have all suffered from numerous DDoS attacks.
In 2018, GitHub was attacked with bandwidth reaching up to 1.35Tbps in an instant. This DDoS attack can be considered one of the largest and most powerful DDoS attacks in internet history. After GitHub was attacked, just a week later, DDoS attacks began targeting Google, Amazon, and even Pornhub, with subsequent DDoS attacks reaching bandwidths of up to 1Tbps.
So what exactly is a DDoS attack?
DDoS stands for Distributed Denial of Service, which translates to 分布式拒绝服务. It refers to multiple attackers from different locations simultaneously attacking one or several targets, representing a distributed, coordinated large-scale attack. A single DoS attack generally uses a one-to-one approach, exploiting flaws in network protocols and operating systems, employing deception and disguise strategies to conduct network attacks, flooding the website server with a large number of requests for replies, consuming network bandwidth or system resources, leading to network or system overload and ultimately paralyzing normal network services.
For example:
I opened a hotpot restaurant with fifty seats in Chongqing, and due to high-quality ingredients and honest service, it is usually bustling with customers, while the hotpot restaurant across the street has no customers. To deal with me, the owner of the other restaurant called fifty people to sit in my restaurant without ordering, preventing other customers from eating.
The above example illustrates a typical DDoS attack, generally referring to attackers using “zombie” computers to launch a large number of requests against the target website in a short time, massively consuming the target website’s host resources, rendering it unable to provide normal services. Online gaming and internet finance are high-risk industries for DDoS attacks.
There are many attack methods, such as ICMP Flood, UDP Flood, NTP Flood, SYN Flood, CC Attack, DNS Query Flood, etc.
Implementation Principle of DDoS Attack Using SYN Flood
SYN Flood is an attack method that exploits the flaws in the TCP protocol by sending a large number of forged TCP connection requests, causing the attacked party’s resources to be exhausted (CPU overload or insufficient memory).
Establishing a TCP connection normally requires three-way handshake: the client sends a SYN packet, the server receives the request and returns a packet indicating acceptance, and the client also returns a confirmation, completing the connection.
SYN Flood occurs when a user sends a packet to the server and suddenly crashes or disconnects, causing the server to send a response packet but not receive the client’s confirmation packet (the third handshake cannot be completed). In this case, the server generally retries and waits for a while before discarding the incomplete connection.
If one user experiences an anomaly, causing a thread on the server to wait for a while is not a big issue, but if a malicious attacker simulates this situation on a large scale, the server will consume a lot of resources to maintain tens of thousands of half-open connections, often resulting in it being unable to respond to normal requests, or even crashing. From the perspective of normal customers, the website appears unresponsive and inaccessible.
How to Respond to DDoS Attacks?
-
High-Defense Servers
Using the hotpot restaurant example, a high-defense server is like adding two security guards to my hotpot restaurant, who can protect the restaurant from harassment and regularly patrol the area to prevent disturbances.
A high-defense server is primarily one that can independently defend against over 50Gbps of attacks, helping websites resist denial of service attacks, regularly scanning the main network nodes, etc. This is a good solution, but it is expensive~
-
Blacklists
Facing the troublemakers in the hotpot restaurant, I angrily take their pictures and ban them from entering the restaurant. However, sometimes people who look similar may also be banned. This is the principle of setting up a blacklist, which adheres to the principle of “killing a thousand innocents to catch one guilty” and may block normal traffic, affecting regular business.
-
DDoS Cleaning
DDoS cleaning is like noticing a customer who has been in the restaurant for a few minutes but has not ordered, so I kick them out.
DDoS cleaning monitors user request data in real-time, promptly detecting abnormal traffic such as DOS attacks, and cleaning up this abnormal traffic without affecting normal business operations.
-
CDN Acceleration
CDN acceleration can be understood as moving the hotpot restaurant online to offer takeout services, making it difficult for troublemakers to find the restaurant and harass it.
In reality, CDN services distribute website access traffic across various nodes, thus hiding the true IP of the website. Even when facing DDoS attacks, traffic can be distributed across various nodes, preventing the origin server from crashing.
Conclusion
Computer networks involve many knowledge points, and this article has only touched on them. A deeper understanding requires everyone to read relevant books. After reading this article, when the interviewer asks about DDoS or TCP-related attack techniques, I hope you can answer correctly. See you in the next article!
-End-


Daily self-portrait of a programmer, see if you recognize yourself?

Gossip: A middle school boy scams 12 girls out of 50 million!

A programmer from a state-owned enterprise: after-tax income of 60+, working 9 to 5, received an offer from Ant Group P7, is it necessary to pursue further education?
 Remember to add ice to the cola, if you love me, you should pin it
Remember to add ice to the cola, if you love me, you should pin it 

 Quality three consecutive biubiubiu~
Quality three consecutive biubiubiu~
