In recent years, incidents of supply chain constraints have become frequent. Although the two recent incidents are not directly related to our country, they inevitably evoke a sense of loss and concern.
First, ARM’s cancellation of the instruction set architecture license to Qualcomm indicates that commercial reputation is worthless in the face of economic interests. Second, the removal of 11 Russian developers from the Linux kernel contribution list shows that the spirit of open source is difficult to maintain in the face of political disputes.
Both incidents occurred abroad, but domestic ARM CPU manufacturers should also be vigilant and learn from history, using past experiences as a guide for future actions.

ARM Architecture is Insecure
Security is a system engineering issue. The so-called security classification levels of L1, L2, L3, and L4 are essentially self-deception. True security can only be achieved when the CPU instruction set, IP core design, chip production, and packaging are completely independent, and when the operating system and application software are fully controllable.
Currently, domestic ARM chips based on ARM instruction set architecture or IP core licensing find it difficult to achieve true security. For example, domestic ARM mobile chips have purchased ARM Cortex A9, A7, A15, A53, A57, A72, A73, A76, A77 CPU cores over the past decade, which can be described as introducing one generation while falling behind another, repeatedly relying on purchasing better CPU cores from ARM and adopting better processes from TSMC for performance improvements. This model of design and manufacturing being outsourced carries significant risks; any change in the international environment could lead to a shock.
Moreover, the inability to freely extend the purchased instruction set architecture or IP core results in numerous inherent vulnerabilities and backdoors that cannot be repaired, making the CPU a lamb to the slaughter. From the vulnerabilities that have already emerged, domestic ARM chips struggle to cope with critical vulnerabilities such as Spectre and memory vulnerabilities, which can lead to serious issues like confidential information leaks and attacks on cloud computing systems.
Currently, security researchers have discovered several serious security vulnerabilities in ARM architecture CPUs. For example:
1. CVE-2024-5660 Memory Access Error Vulnerability.This vulnerability exists in ARM V8.2 architecture processors. It allows modified, untrusted customer operating systems to jeopardize the security of the host system and can be exploited by attackers for system attacks in cloud computing scenarios.
2. UnTrustZone Vulnerability.Attackers can copy secret data to SRAM within TrustZone through secure calls and exploit this vulnerability to recover secret data from SRAM, thereby breaching the security isolation of TrustZone.
3. TIKTAG Vulnerability.This vulnerability reveals defects in memory protection on ARM processors. For ARM v8.2 architecture, the lack of implementation of MTE results in missing memory protection functions, or even if MTE is implemented, this vulnerability prevents ARM v8.2 architecture from fully defending against memory attacks. This vulnerability targets Arm’s Memory Tagging Extension (MTE) and uses speculative execution to leak MTE memory tags, bypassing critical protection mechanisms against memory corruption. Using the TIKTAG vulnerability gadget, attackers can accurately leak MTE tags in real applications such as Google Chrome and the Linux kernel within seconds, thereby undermining memory protection mechanisms.
4. CVE-2024-10929 SPECTRE-BSE Ghost Vulnerability.A ghost vulnerability known as Spectre-BSE (Spectre Branch Status Eviction) exists in ARM architecture CPUs. This vulnerability allows attackers to control the victim’s branch history, thereby controlling the victim’s branch prediction path, indicating that the defenses against ghost vulnerabilities in ARM v8.2 architecture may not be thorough.
5. Leaky MDU Side Channel Vulnerability.This vulnerability exploits the MDU side channel to speculate on victim address information, thereby breaking security features such as KASLR. Attackers can obtain victim address information by leveraging changes in the state of the disambiguation unit, further accessing secret data dependent on that address information.
ARM Licensing is Unreliable
Over the past decade, domestic companies have introduced a large number of CPUs from abroad, establishing MIPS, SPARC, Power, ARM, and X86 CPUs in mainland China. In practice, after the onset of the tech war in the United States, there have been instances of supply shortages and “discontinued” ARM chips.
When American politicians make threats, ARM has stated that it will comply with U.S. sanctions, severing all cooperation and communication with companies in mainland China. When the international situation eases, ARM promotes “compliance” and expresses willingness to do business with China. Practice has proven that ARM lacks the ability to counter U.S. sanctions and has no immunity against international political risks.
In the past, domestic ARM manufacturers liked to boast about their so-called ARM instruction set licensing, but in reality, this licensing cannot withstand international political risks and is also difficult to avoid commercial risks.
Take ARM’s lawsuit against Qualcomm as an example. ARM issued a “60-day mandatory notice to terminate the architecture license agreement” to Qualcomm in the lawsuit, proving that ARM’s licensing can be revoked, and ARM can sell licenses externally, which naturally means it can also cancel licenses.
Indeed, the final judgment of the U.S. court favored Qualcomm, but that does not mean that Chinese companies will receive the same protection from U.S. courts. After all, Qualcomm’s lobbying groups, legal resources, and political-business relationships in the U.S. are not something any Chinese company can easily match, and ARM is still a publicly traded company in the U.S. Once a Chinese company gets involved in a similar lawsuit, the outcome will not be much better than that of the previously shocked JinHua.
ARM’s cancellation of the instruction set architecture license to Qualcomm and the removal of 11 Russian developers from the Linux kernel contribution list share a common point: the sanctioned parties are all building on someone else’s land.
It seems free, but regardless of how much your construction increases the value of the land, it does not prevent the landlord from expelling you and swallowing your construction results, then bringing in someone else to continue the construction. Therefore, the only way to avoid being constrained is to build on your own land.
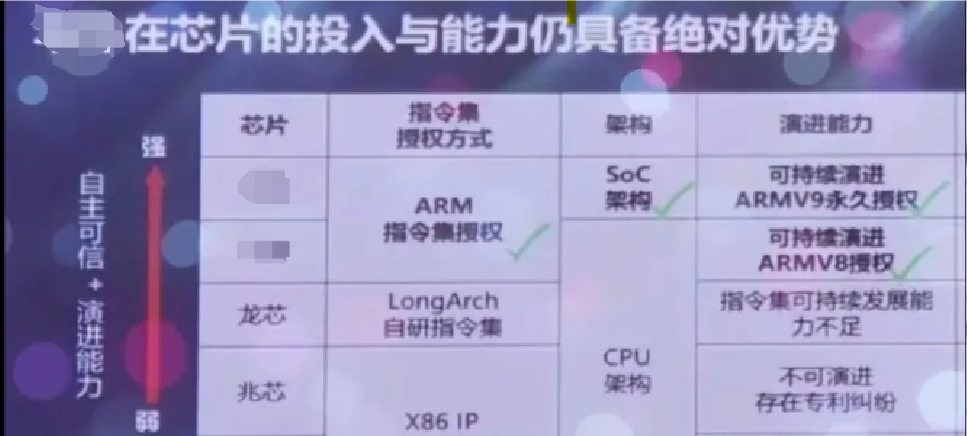
ARM Development is Not Autonomous
Although ARM CPU manufacturers claim in presentations that the Loongson instruction set lacks sustainable development capabilities, they can continue to evolve based on ARM V9 licensing. In reality, Loongson is the truly independent instruction set with autonomous development capabilities, while domestic ARM CPU manufacturers can only follow ARM closely.
Specifically, the issue with the ARM route is the endless purchasing problem. The ARM instruction set has been updated to V9, and it will certainly be updated to V10, V11 in the future. Previously, domestic ARM purchased V8 licensing, now they have purchased V9 licensing; when ARM updates to V10, will domestic ARM manufacturers have to purchase again? If this endless purchasing continues, then where does the so-called autonomy of domestic ARM lie?
In terms of autonomy, Loongson’s independent instruction set, with all core IP designed independently and a self-built software ecosystem, has the strongest autonomy. If Loongson can succeed, it can achieve a tripartite balance among X86, ARM, and LoongArch, realizing a division of the world.
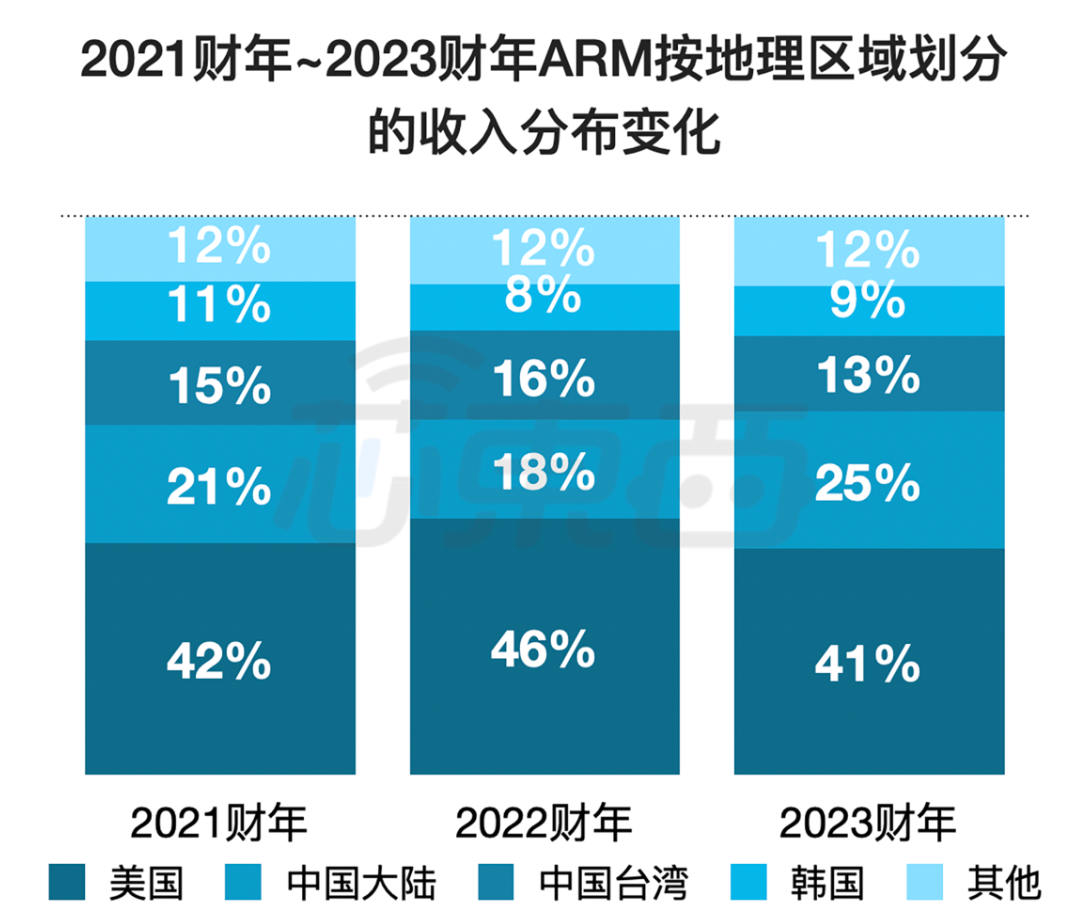
In contrast, domestic ARM is actually a vassal within the ARM system, technically and profit-wise constrained by ARM, needing to continuously pay royalties to ARM. Last year, ARM went public in the U.S., with the Chinese market accounting for 38% of its revenue, making the Chinese market an important source of ARM’s revenue and profits.
Here, I must criticize the so-called self-developed domestic ARM CPUs. If everything is self-developed, why do they still have to pay high licensing fees to ARM every year?
The value of self-development is fundamentally determined by the amount of patent fees paid to foreign companies. If no patent fees are paid, it is undoubtedly true self-development; otherwise, it is pseudo self-development.
With the annual payment of huge licensing fees to ARM, and with nearly 40% of ARM’s revenue coming from the Chinese market, how can domestic ARM CPUs have the audacity to claim autonomy?
Conclusion
In fact, the appropriate positioning of domestic ARM chips should be as commercial chips, integrating Western technology systems, purchasing ARM licenses and TSMC processes, benefiting from the Android software ecosystem, and expanding in the commercial market, providing domestic mobile manufacturers with more affordable ARM chips, thereby enhancing their bargaining power against Qualcomm and MediaTek.
In practice, to ensure information security, it is essential to have a CPU that is completely independent from the instruction set, IP core design, chip production, and packaging. Domestic ARM chips are not suitable as the foundation for autonomous information systems. Especially in scenarios with high requirements for security and autonomy, ARM should not be forcibly promoted.