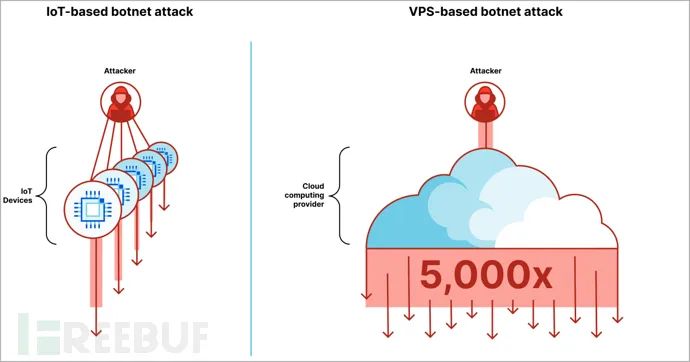
The DDoS (Distributed Denial of Service) attacks in the first quarter of 2023 have shifted from relying on compromised IoT devices to exploiting compromised Virtual Private Servers (VPS).
According to the internet security company Cloudflare, the new generation of botnets is gradually abandoning the swarm tactics of multiple individual IoT devices, instead opting to utilize leaked API credentials or known vulnerabilities to take control of misconfigured VPS servers.
This approach helps attackers to more easily and quickly establish high-performance botnets, which can be 5000 times more powerful than IoT-based botnets.
 [VPS Servers Used for DDoS Attacks]
[VPS Servers Used for DDoS Attacks]
Cloudflare explained in the report, “Although the number of devices used by the new generation of botnets is only a small fraction, each device has very powerful capabilities.” “Cloud computing providers offer virtual private servers that allow startups and businesses to create high-performance applications. The downside is that it also allows attackers to create high-performance botnets that can be up to 5000 times stronger.”
2023 Q1 DDoS Landscape
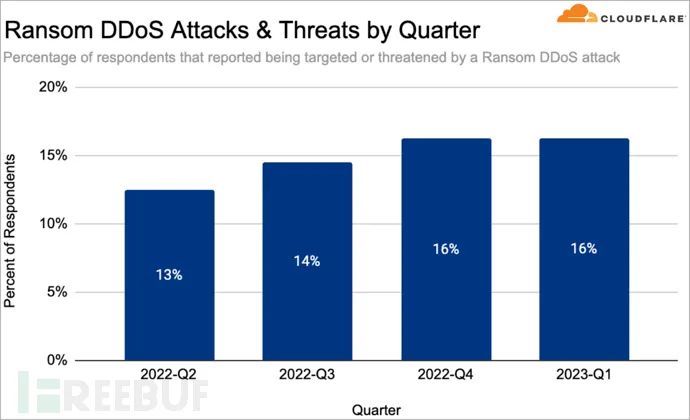
Overall, DDoS activity in the first quarter of this year remained stable, with ransom DDoS attacks showing a significant year-on-year increase of 60%, accounting for 16% of all recorded/reported DDoS attacks.
These ransom-based DDoS attacks create service disruptions by bombarding targets with junk traffic, and continue indefinitely until the victims meet the attackers’ demands.
 [Ransom DDoS Attacks]
[Ransom DDoS Attacks]
In Q1 2023, the target countries of DDoS attacks were mostly Israel, followed by the United States, Canada, and Turkey. The most attacked industries were internet services, marketing, software, and gaming/gambling.
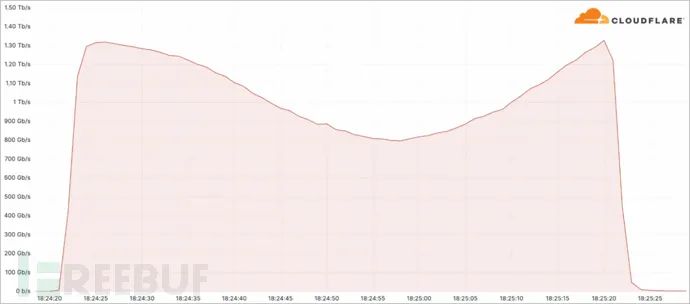
The most severe attack observed by Cloudflare this quarter peaked at over 71 million requests per second. Another notable incident was a 1.3Tbps DDoS attack targeting a telecommunications provider in South America.
 [1.3Tbps Mirai Attack]
[1.3Tbps Mirai Attack]
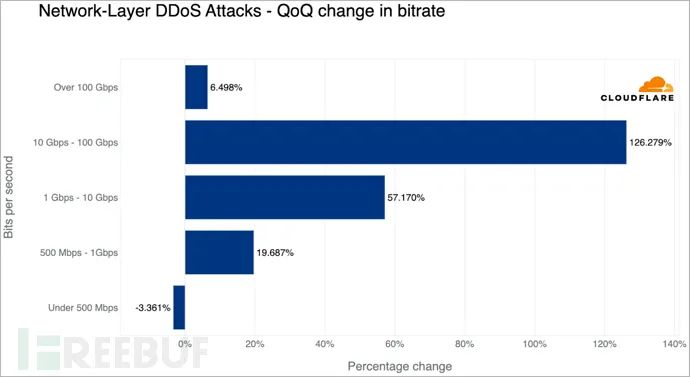
In terms of attack scale and duration, most attacks (86.6%) lasted less than 10 minutes, while 91% of attacks did not exceed 500 megabits.
However, the number of larger attacks is still increasing, with attack speeds exceeding 100Gbps, showing about a 6.5% increase compared to the previous quarter.
[DDoS Attack Scale Trends]
New Trends
DDoS attacks come in various forms, and as defense systems evolve, attackers also design new forms of attacks.
In this quarter, Cloudflare recorded the following new trends:
DDoS attacks based on SPSS (Statistical Product and Service Solutions) grew by 1565% quarter-over-quarter. This was due to two vulnerabilities (CVE-2021-22731 and CVE-2021-38153) in the Sentinel RMS license management service being exploited to launch reflective DDoS attacks.
DNS amplification DDoS attacks grew by 958% quarter-over-quarter, with attackers exploiting flaws in DNS infrastructure to generate massive amounts of traffic.
DDoS attacks based on GRE (Generic Routing Encapsulation) increased by 835% quarter-over-quarter, with attackers abusing the GRE protocol to continuously attack victims’ networks with junk requests.
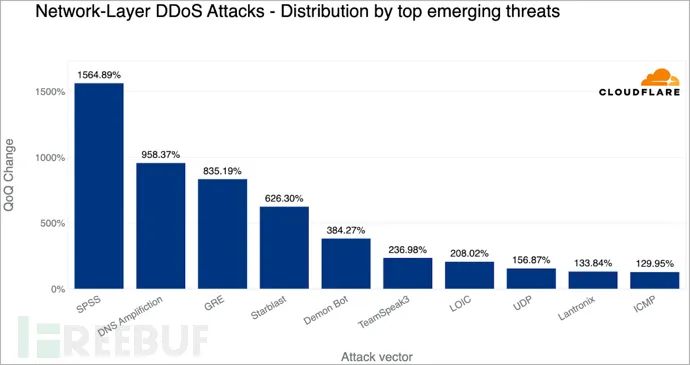 [New DDoS Attack Trends]
[New DDoS Attack Trends]
The overall trend of DDoS attacks in Q1 2023 shows an increase in scale and duration, targeting a wide range of industries. Therefore, effective defense strategies, automatic detection mechanisms, and effective solutions are particularly important.
Reference Link:
www.bleepingcomputer.com/news/security/ddos-attacks-shifting-to-vps-infrastructure-for-increased-power/