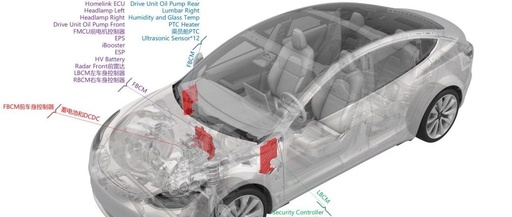
Tesla Major Security Vulnerability: Keyless Car Unlocking via BLE Relay Attack
In a recent cybersecurity study, Tesla’s keyless entry system revealed a major security vulnerability, allowing attackers to unlock a Tesla Model 3 or Model Y within 10 seconds through a BLE (Bluetooth Low Energy) relay attack. The method to execute this attack is not complicated. It merely requires placing a decoding sensing device near the … Read more