Linux System Programming: Basic Concepts
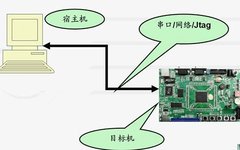
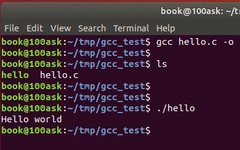
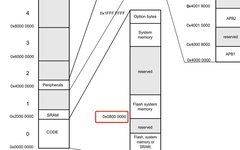
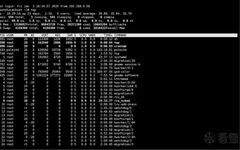
Click the above“Mechanical and Electronic Engineering Technology”to follow us Host Machine The host machine (Host Machine) usually refers to the computer used for developing and compiling embedded software. The host machine is typically a high-performance desktop or laptop that runs standard operating systems such as Windows, Linux, or macOS. The main functions of the host … Read more