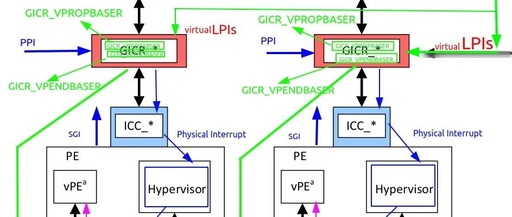
CPU Virtualization Series: VM Entry and Exit
Wang Baisheng, Xie Guangjun Reading time: 8 minutes Quick read: 3 minutes This article is excerpted from the book “In-Depth Exploration of Linux System Virtualization: Principles and Implementation” written by Wang Baisheng and Xie Guangjun, focusing on how the virtual CPU switches between Host mode and Guest mode, and how KVM and the physical CPU … Read more