

Since the birth of MCUs in the 1970s, the technology for breaking chips and the solutions to prevent chip cracking have been in a constant chase of “the higher the road, the higher the magic,” with each side trying to outdo the other. This article shares the development history of microcontrollers in terms of security protection. At the end of the article, it summarizes the advantages and disadvantages of the currently highest security-level smart card chips.
1. The Era of Single Board Computers
In the early 1970s, embedded systems were composed of separate components such as: CPU, ROM, RAM, I/O cache, serial ports, and other communication and control interfaces. During this period, there were almost no protective measures to prevent intruders from copying the data in the ROM area of single board computers, except for legal restrictions.
2. The Era of Microcontrollers
With the development of large-scale integrated circuit technology, the CPU, data memory (RAM), program memory (ROM), and other I/O communication ports were integrated into a single microcontroller chip, replacing single board computers. As shown:
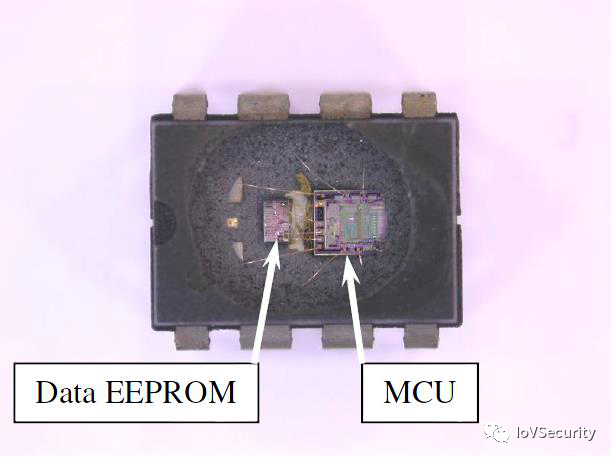
During this period, the internal memory EEPROM and the MCU were separately sealed within the same package. Intruders could use microprobes to obtain data.
3. Security Fuses
As the number of intruders increased, MCUs added security fuses to prohibit data access for their own safety. As shown:
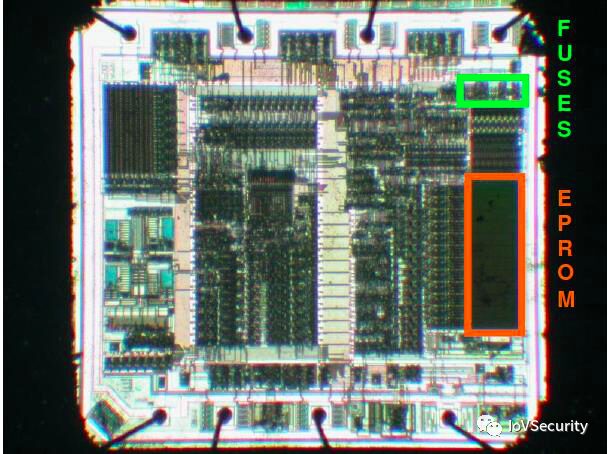
Advantages: It is easy to implement without completely redesigning the MCU architecture, only using fuses to control data access.
Disadvantages: Fuses are easy to locate and attack. For example, the state of the fuse can be modified by directly connecting the bit output to the power supply or ground. Some can be cut off with a laser or focused ion beam to sever the fuse’s sensing circuit. Non-invasive attacks can also succeed because a separate fuse layout differs from the normal storage array, allowing external signals to force the bits into an unreadable state, thus accessing information on the internal chip. Semi-invasive attacks can enable attackers to succeed quickly but require opening the chip package to access the die. A well-known method is to use ultraviolet light to erase the security fuse.
4. Security Fuses Integrated into Memory Arrays
Later, MCU manufacturers made the security fuses a part of the memory array, as shown:
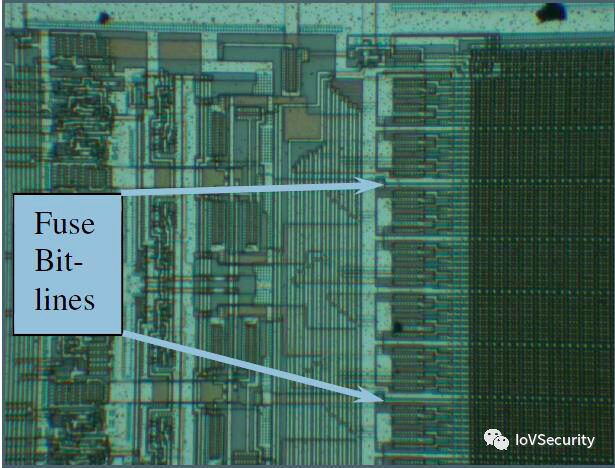
Generally, the fuses are located very close to the main memory or share some control lines, and are manufactured using the same process as the main memory, making it difficult to locate the fuses. Non-invasive attacks can still be conducted, and combinations of external signals can force the fuse bits into an unreadable state. Similarly, semi-invasive attacks are also possible. Of course, attackers need more time to locate the security fuses or the control circuitry responsible for security monitoring, but this can be automated. Conducting invasive attacks will be very difficult and require manual operations, which will cost more to crack.
5. Using a Portion of Main Memory to Control External Data Access
By locking specific address information at power-up, it can be used as security fuses. Alternatively, passwords can be used to control access to the memory. For example, Texas Instruments’ MSP430F112 requires the correct 32-byte password to perform read-back operations. If the password is not entered, the memory can only be read back after erasing the byte password. Although this protection method seems more effective than previous ones, it has some drawbacks that can be exploited with low-cost non-invasive attacks, such as timing analysis and power consumption. If the security fuse state is part of the memory after power-up or reset, it gives attackers the opportunity to exploit power noise to force the state in the memory into an erroneous condition.
6. Using Top-Level Metal Networks
Designing with top-level metal networks increases the difficulty of intrusion. All grids are used to monitor short circuits and open circuits, and once triggered, will reset or clear the memory. As shown:
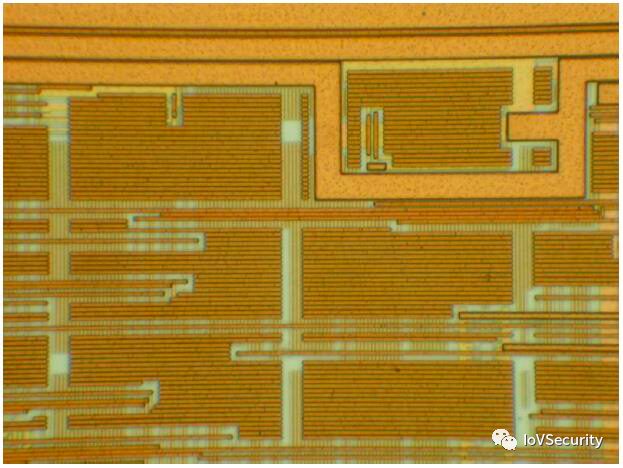
Ordinary MCUs do not use this protection method because the design is difficult, and it can also be triggered under abnormal operating conditions, such as: high-intensity electromagnetic field noise, low or high temperatures, abnormal clock signals, or poor power supply. Therefore, some ordinary MCUs use cheaper pseudo-top-level metal grids, which can be attacked through highly efficient optical analysis and micro-probing. Moreover, these grids cannot prevent non-invasive attacks. They also cannot effectively prevent semi-invasive attacks because capacitance exists between wires, and light can reach the effective area of the circuit through the wires. In smart cards, some grid lines are laid between power and ground. Some programmable smart cards go further by completely eliminating standard programming interfaces, or even removing EEPROM read interfaces, replacing them with a boot module that can erase or shield itself after loading code, and only respond to functions supported by the user’s embedded software. This effectively prevents non-invasive attacks.
7. Smart Card Chip Security Design
In recent years, some smart cards have used Bus Encryption technology to prevent probing attacks. As shown:
Data is stored in encrypted form in the memory. Even if intruders obtain data from the data bus, they cannot know the key or other sensitive information (such as data recovery methods). This protective measure effectively prevents both invasive and semi-invasive attacks. Some smart cards can even ensure that each card has a different bus encryption key, so that even if intruders completely crack it, they cannot produce chips with the same functionality because each smart card chip has a unique ID number, and it is impossible to obtain a smart card with the same ID number. Additionally, it is worth mentioning that some smart cards design standard module structures, such as decoders, register files, ALUs, and I/O circuits using similar ASIC logic. These designs become Gle Logic designs. Gle Logic significantly increases the performance and security of the CPU core. It is nearly impossible to know the physical location of the bus, effectively preventing reverse engineering and micro-probing attacks.
Advantages and Disadvantages of Smart Card Chip Encryption Solutions
For developers, choosing a more secure designed microcontroller can provide better protection. Compared to most microcontrollers, even smart cards designed ten years ago can offer better protection. Modern smart cards provide more anti-attack protections, with internal voltage sensors protecting against power glitch attacks, overvoltage, and undervoltage protections. Clock frequency sensors prevent attacks that lower clock frequency during static analysis. They can also prevent clock noise attacks that increase clock frequency. Top-level metal grids and internal bus hardware encryption can prevent micro-probing attacks. However, compared to microcontrollers, smart card chips also have disadvantages, such as: high chip prices, and difficulty in purchasing small quantities. Development tools are expensive, and confidentiality agreements are required with manufacturers, even for manuals. Many manufacturers only sell large quantities of smart cards to specific customers. Another drawback is the limited functionality of I/O; ordinary smart card chips usually only have ISO7816 interfaces, with very few having separate I/O ports. This means that most applications cannot replace microcontrollers and can only be used in industries with very high security requirements, such as: pay-TV set-top boxes, bank cards, SIM cards, second-generation ID cards, and high-end encryption chips. The application of smart card chips in the encryption chip field will be a promising direction. Because smart card chips have high security levels and fewer IO resources, while ordinary MCUs have abundant hardware resources but low security levels, key algorithms and operating parameters can be stored in special forms in smart card chips to achieve powerful functionality with high security strength.
Postscript
The ongoing struggle between groups attempting to break protective mechanisms and manufacturers continuously introducing new security measures is endless. “The higher the road, the higher the magic,” or “evil cannot suppress justice,” will continue to unfold between the two factions!
Author: Wu Zhe
Source: IoVSecurity

