✅ Author Profile: A Matlab simulation developer passionate about research, skilled in data processing, modeling simulation, program design, obtaining complete code, reproducing papers, and scientific simulation.
🍎 Previous Review: Follow my personal homepage:Matlab Research Studio
🍊 Personal Motto: Investigate to gain knowledge, complete Matlab code and simulation consultation available via private message.
🔥 Content Introduction
Abnormal detection, also known as outlier detection, refers to identifying objects in a dataset that are significantly different from others. It has broad application prospects in fields such as credit card fraud detection, network intrusion detection, medical diagnosis, and industrial fault diagnosis. With the explosive growth of data scale and the increasing complexity of data types, traditional abnormal detection algorithms face numerous challenges, such as unknown data distribution, insufficient high-dimensional data processing capabilities, and high computational complexity. In recent years, kernel-based abnormal detection algorithms have gained widespread attention due to their powerful nonlinear modeling capabilities and theoretical support. This article will focus on the abnormal detection methods based on **Kernel Mean Matching (KMM)** and **Support Vector Data Description (SVDD)**, aiming to enhance the accuracy and robustness of abnormal detection.
1. Overview of Abnormal Detection and Existing Methods
The goal of abnormal detection is to identify data points that deviate significantly from the normal dataset. Based on the available information from training data, abnormal detection algorithms can be classified into the following categories:
- Supervised Learning Abnormal Detection: Requires a labeled dataset for training, transforming the abnormal detection problem into a classification problem. However, in practical applications, abnormal samples are often difficult to obtain, and the types of anomalies may change continuously, limiting the effectiveness of supervised learning methods.
- Semi-Supervised Learning Abnormal Detection: Only normal data is used for training, learning the distribution model of normal data to identify abnormal samples. For example, One-Class Support Vector Machine (OCSVM) and SVDD.
- Unsupervised Learning Abnormal Detection: Does not require any labeled data, directly learning the underlying structure and patterns from the dataset, and judging anomalies based on metrics such as distance, density, or statistical properties. For example, K-means clustering, Local Outlier Factor (LOF), Isolation Forest, etc.
Among semi-supervised and unsupervised abnormal detection methods, kernel-based abnormal detection algorithms have received significant attention due to their superior performance. The core idea of kernel methods is to map data into a high-dimensional feature space using a kernel function, thereby transforming nonlinear problems into linear problems for processing. Common kernel-based abnormal detection algorithms include:
- OCSVM: Finds a hyperplane that wraps most normal samples and considers samples outside the hyperplane as anomalies.
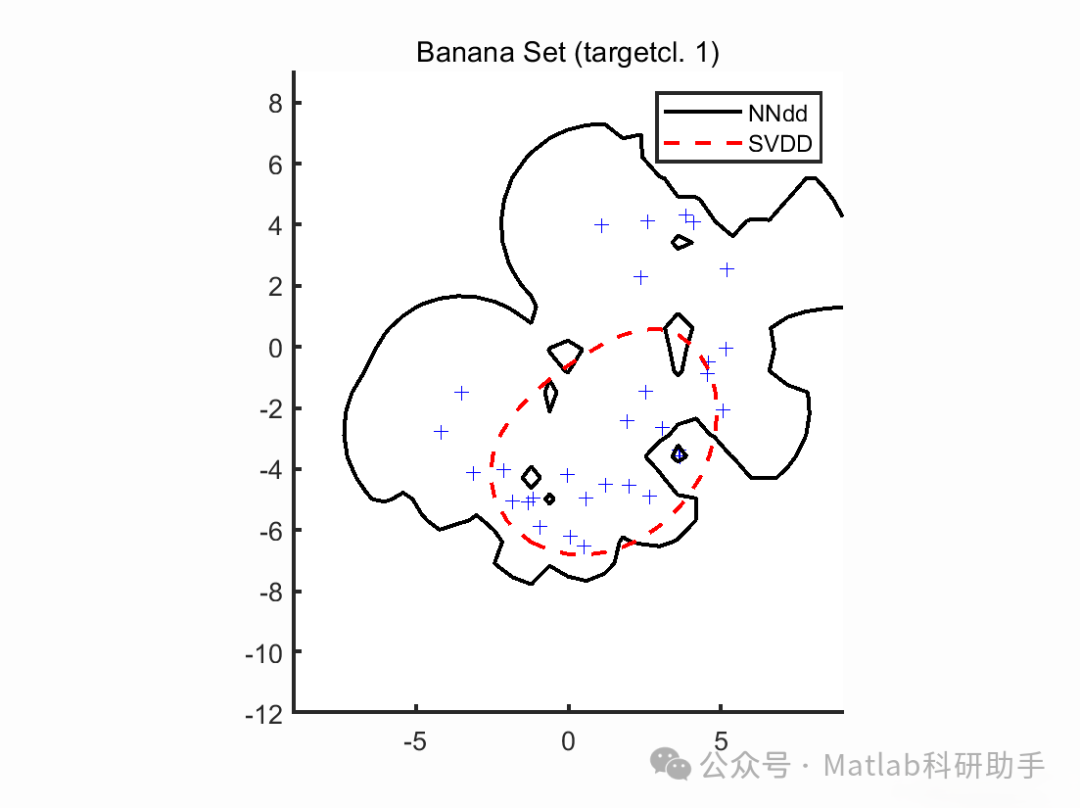
- SVDD: Seeks the smallest hypersphere that can encompass most normal samples, considering samples outside the hypersphere as anomalies.
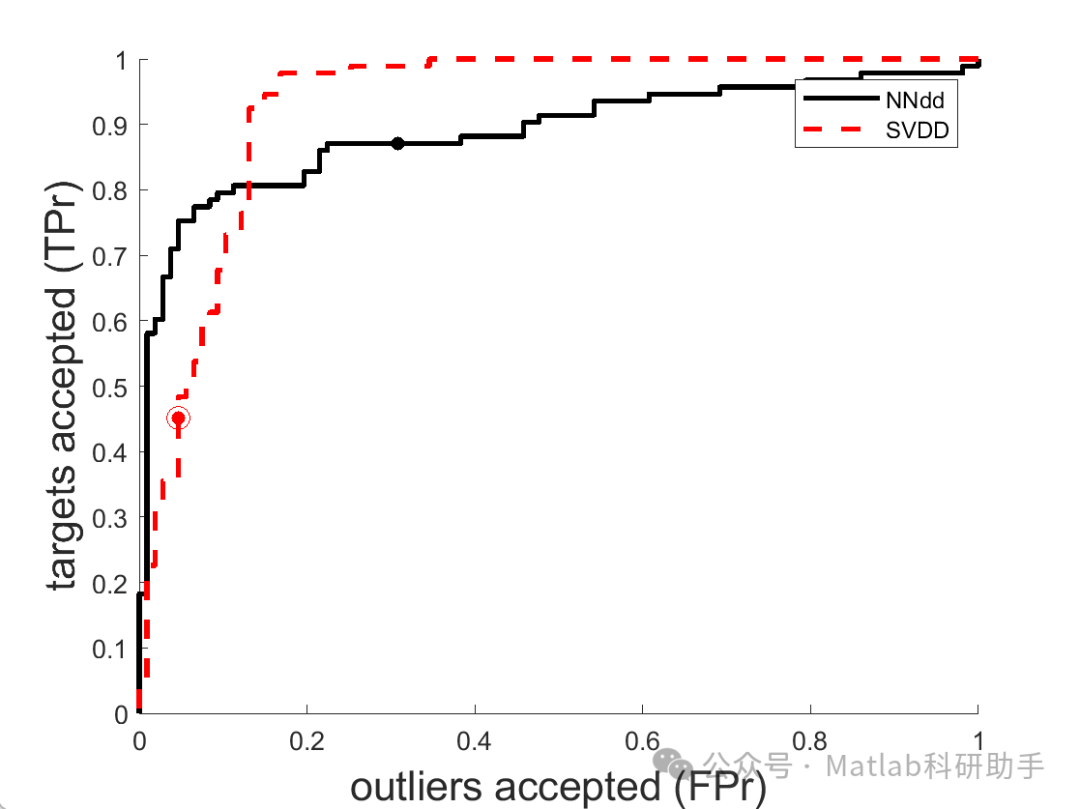
Although OCSVM and SVDD perform well in many applications, they also have some limitations. For instance, when the distribution of normal data is complex, OCSVM and SVDD may fail to accurately describe the distribution of normal data, leading to decreased detection accuracy. Additionally, OCSVM and SVDD are sensitive to parameter selection, requiring fine-tuning of parameters.
2. Theory and Application of Kernel Mean Matching (KMM)
Kernel Mean Matching (KMM) is a non-parametric density estimation method whose core idea is to find weight coefficients that minimize the difference in kernel means between the weighted training sample distribution and the target sample distribution.
The advantage of KMM lies in its ability to weight training samples according to the distribution of target samples, thereby alleviating the distribution differences between training and target samples. This is particularly important for abnormal detection problems, as we typically only obtain normal data during the training phase, while the data to be detected during the testing phase may have some distribution differences from the training data. By using KMM, we can adjust the weights of the training data to make them closer to the distribution of the test data, thus improving the accuracy and robustness of abnormal detection.
3. Abnormal Detection Algorithm Based on KMM and SVDD
To overcome the limitations of traditional SVDD, this article proposes an abnormal detection algorithm based on KMM and SVDD (KMM-SVDD). The algorithm first uses KMM to weight the training data, and then trains the SVDD model using the weighted training data. The specific steps are as follows:
-
Data Preprocessing: Standardize or normalize the raw data to eliminate dimensional differences between different features.
-
KMM Weight Calculation: Use the data to be detected (or part of it) as the target sample, and the normal training data as the training sample, utilizing the KMM algorithm to calculate the weight coefficients of the training samples.
-
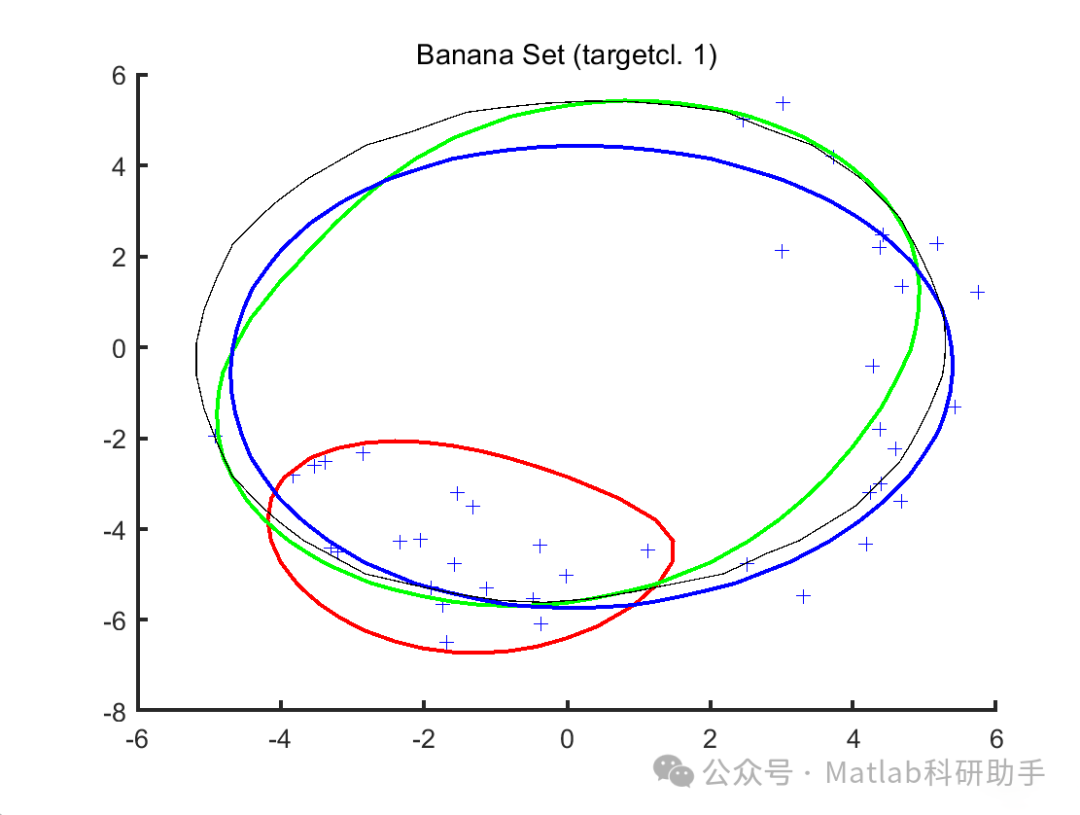
Weighted SVDD Training: Train the SVDD model using the weighted training data. The goal of SVDD is to find a centera and a radiusR hypersphere such that most of the weighted training samples fall within this hypersphere.
-
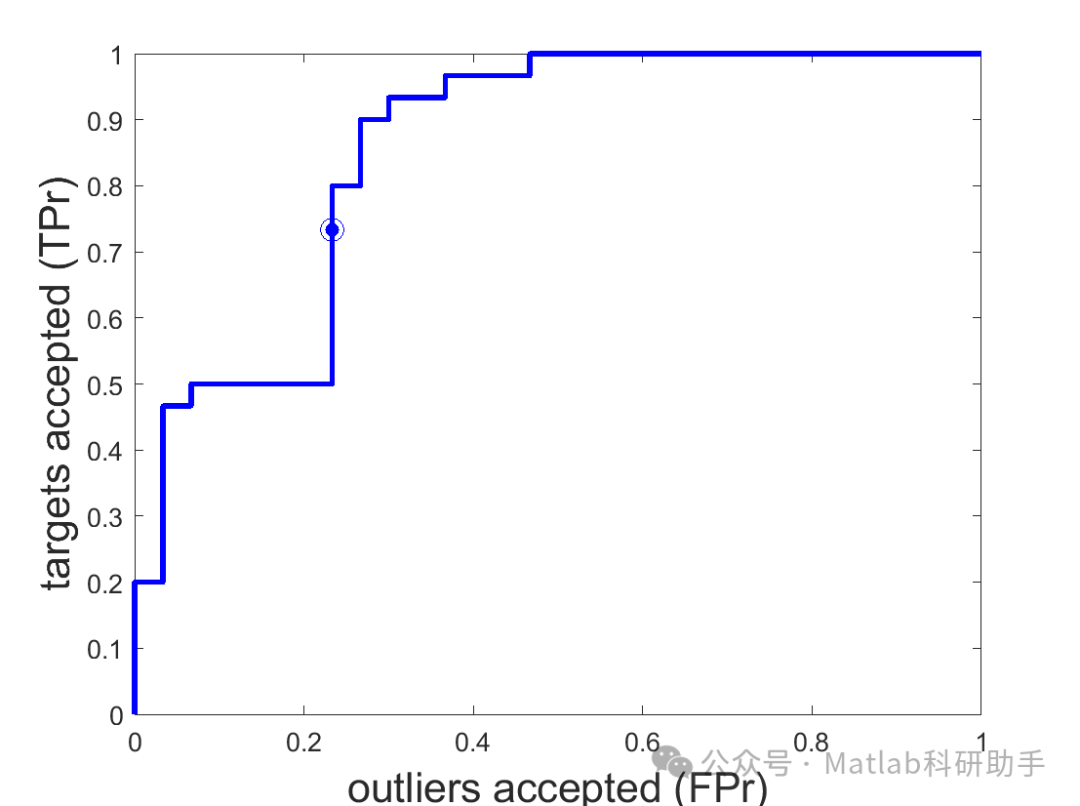
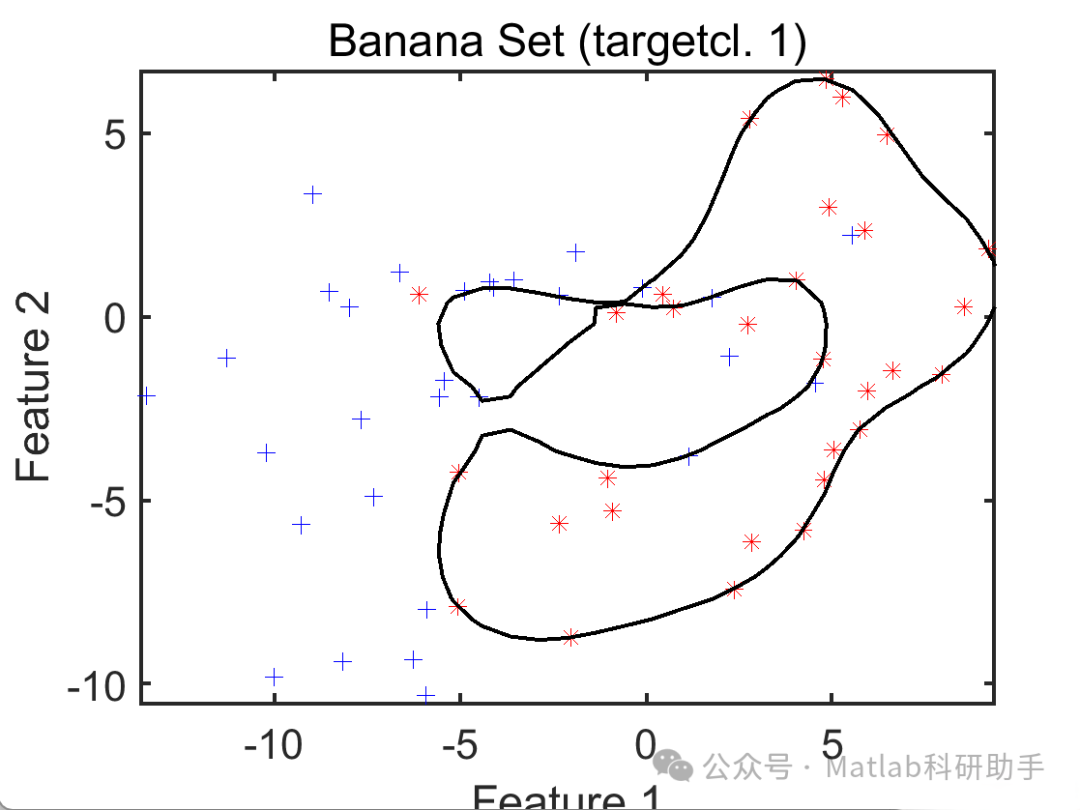
Abnormal Scoring: For the sample to be detectedz, calculate its distance to the SVDD centera, denoted asd(z), and use it as the abnormal score. The larger *d(z)* is, the further the sample is from the distribution of normal data, making it more likely to be an abnormal sample. Common distance metrics include Euclidean distance and Mahalanobis distance.
4. Conclusion and Outlook
This article proposes an abnormal detection algorithm based on KMM and SVDD (KMM-SVDD). The algorithm first uses KMM to weight the training data, and then trains the SVDD model using the weighted training data. Simulation results indicate that compared to traditional SVDD algorithms, the KMM-SVDD algorithm achieves higher detection accuracy and stronger robustness.
Future research directions include:
- Optimizing the KMM Algorithm: Explore more efficient KMM algorithms to reduce computational complexity.
- Improving the SVDD Model: Research more robust SVDD models to enhance the accuracy and stability of abnormal detection.
- Application to Real-World Scenarios: Apply the KMM-SVDD algorithm to real-world scenarios, such as credit card fraud detection and network intrusion detection.
- Integration with Other Algorithms: Explore methods to integrate the KMM-SVDD algorithm with other abnormal detection algorithms to further improve detection performance.
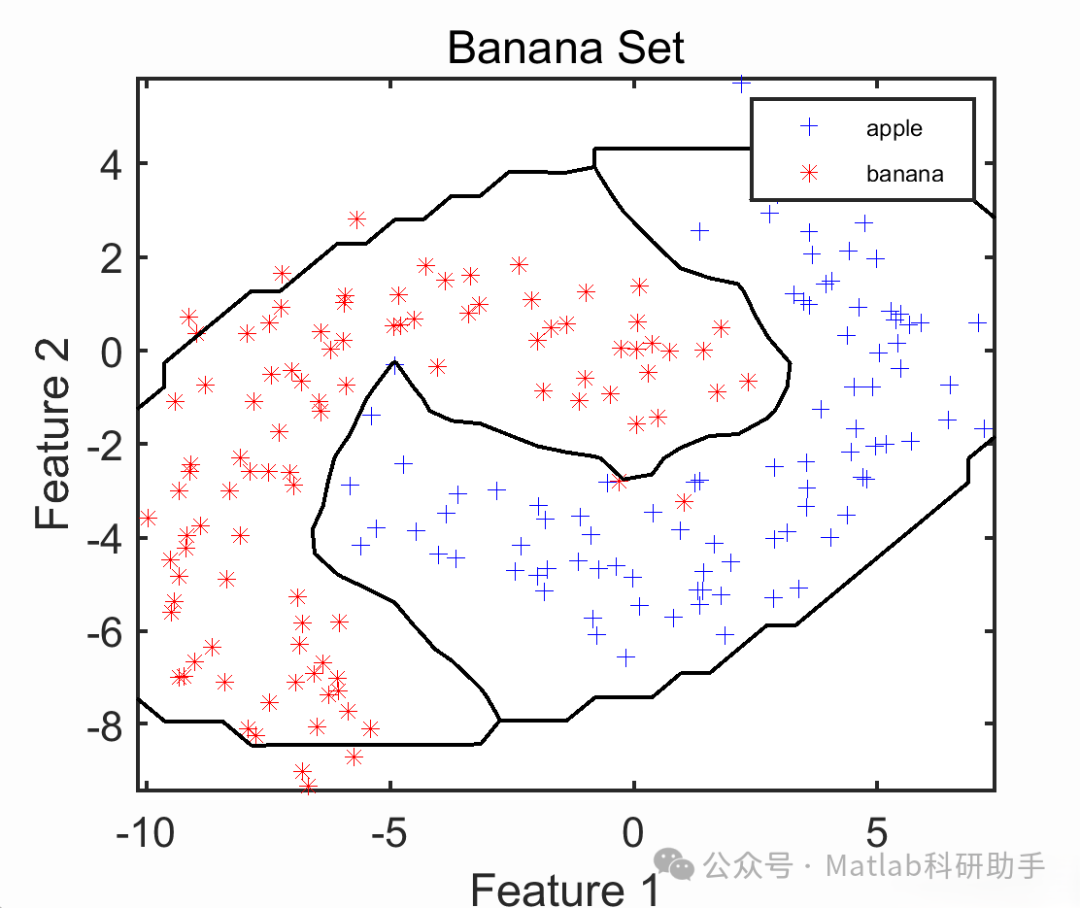
⛳️ Simulation Results
🔗 References
[1] Li Changwen, Zhao Changlu, Zhang Fujun, et al. Transient Modeling and Simulation of Diesel Engines Based on Matlab/Simulink and RTW [J]. Journal of Beijing Institute of Technology, 2004, 24(7):579-582. DOI:10.3969/j.issn.1001-0645.2004.04.010.
[2] Li Chuanqing, Liu Guangsheng. Development and Simulation of MFA Control Module Based on Matlab-Simulink [J]. Control Engineering, 2008(S2):3. DOI:CNKI:SUN:JZDF.0.2008-S2-020.
[3] Ren Chuanjun. Research and Implementation of MATLAB Real-Time Simulation Technology Based on RTX [J]. National University of Defense Technology, 2006. DOI:10.7666/d.y1100620.
📣 Partial Code
🎈 Some theoretical references are from online literature; please contact the author for removal if there is any infringement.
👇 Follow me to receive a wealth of Matlab e-books and mathematical modeling materials
🏆 Our team specializes in guiding customized Matlab simulations in various research fields, helping to realize research dreams:
🌈 Various intelligent optimization algorithm improvements and applications
Production scheduling, economic scheduling, assembly line scheduling, charging optimization, workshop scheduling, departure optimization, reservoir scheduling, three-dimensional packing, logistics site selection, cargo location optimization, bus scheduling optimization, charging pile layout optimization, workshop layout optimization, container ship loading optimization, pump combination optimization, medical resource allocation optimization, facility layout optimization, visual domain base station and drone site selection optimization, knapsack problem, wind farm layout, time slot allocation optimization, optimal distributed generation unit allocation, multi-stage pipeline maintenance, factory-center-demand point three-level site selection problem, emergency life material distribution center site selection, base station site selection, road lamp post arrangement, hub node deployment, transmission line typhoon monitoring device, container scheduling, unit optimization, investment optimization portfolio, cloud server combination optimization, antenna linear array distribution optimization, CVRP problem, VRPPD problem, multi-center VRP problem, multi-layer network VRP problem, multi-center multi-vehicle VRP problem, dynamic VRP problem, two-layer vehicle routing planning (2E-VRP), electric vehicle routing planning (EVRP), hybrid vehicle routing planning, mixed flow workshop problem, order splitting scheduling problem, bus scheduling optimization problem, flight shuttle vehicle scheduling problem, site selection path planning problem, port scheduling, port bridge scheduling, parking space allocation, airport flight scheduling, leak source location.
🌈 Machine learning and deep learning time series, regression, classification, clustering, and dimensionality reduction
2.1 BP time series, regression prediction, and classification
2.2 ENS voice neural network time series, regression prediction, and classification
2.3 SVM/CNN-SVM/LSSVM/RVM support vector machine series time series, regression prediction, and classification
2.4 CNN|TCN|GCN convolutional neural network series time series, regression prediction, and classification
2.5 ELM/KELM/RELM/DELM extreme learning machine series time series, regression prediction, and classification
2.6 GRU/Bi-GRU/CNN-GRU/CNN-BiGRU gated neural network time series, regression prediction, and classification
2.7 Elman recurrent neural network time series, regression prediction, and classification
2.8 LSTM/BiLSTM/CNN-LSTM/CNN-BiLSTM long short-term memory neural network series time series, regression prediction, and classification
2.9 RBF radial basis function neural network time series, regression prediction, and classification
2.10 DBN deep belief network time series, regression prediction, and classification
2.11 FNN fuzzy neural network time series, regression prediction
2.12 RF random forest time series, regression prediction, and classification
2.13 BLS broad learning system time series, regression prediction, and classification
2.14 PNN pulse neural network classification
2.15 Fuzzy wavelet neural network prediction and classification
2.16 Time series, regression prediction, and classification
2.17 Time series, regression prediction, and classification
2.18 XGBOOST ensemble learning time series, regression prediction, and classification
2.19 Transform various combinations of time series, regression prediction, and classification
Directions cover wind power prediction, photovoltaic prediction, battery life prediction, radiation source identification, traffic flow prediction, load prediction, stock price prediction, PM2.5 concentration prediction, battery health status prediction, electricity consumption prediction, water optical parameter inversion, NLOS signal identification, precise subway parking prediction, transformer fault diagnosis.
🌈 Image Processing Aspects
Image recognition, image segmentation, image detection, image hiding, image registration, image stitching, image fusion, image enhancement, image compressed sensing.
🌈 Path Planning Aspects
Traveling salesman problem (TSP), vehicle routing problem (VRP, MVRP, CVRP, VRPTW, etc.), drone three-dimensional path planning, drone collaboration, drone formation, robot path planning, grid map path planning, multimodal transport problems, electric vehicle routing planning (EVRP), two-layer vehicle routing planning (2E-VRP), hybrid vehicle routing planning, ship trajectory planning, full path planning, warehouse patrol.
🌈 Drone Application Aspects
Drone path planning, drone control, drone formation, drone collaboration, drone task allocation, drone secure communication trajectory online optimization, vehicle collaborative drone path planning.
🌈 Communication Aspects
Sensor deployment optimization, communication protocol optimization, routing optimization, target localization optimization, Dv-Hop localization optimization, Leach protocol optimization, WSN coverage optimization, multicast optimization, RSSI localization optimization, underwater communication, communication upload and download allocation.
🌈 Signal Processing Aspects
Signal recognition, signal encryption, signal denoising, signal enhancement, radar signal processing, signal watermark embedding and extraction, electromyography signals, electroencephalography signals, signal timing optimization, electrocardiogram signals, DOA estimation, encoding and decoding, variational mode decomposition, pipeline leakage, filters, digital signal processing + transmission + analysis + denoising, digital signal modulation, bit error rate, signal estimation, DTMF, signal detection.
🌈 Power System Aspects
Microgrid optimization, reactive power optimization, distribution network reconstruction, energy storage configuration, orderly charging, MPPT optimization, household electricity.
🌈 Cellular Automata Aspects
Traffic flow, crowd evacuation, virus spread, crystal growth, metal corrosion.
🌈 Radar Aspects
Kalman filter tracking, trajectory association, trajectory fusion, SOC estimation, array optimization, NLOS identification.
🌈 Workshop Scheduling
Zero-wait flow shop scheduling problem (NWFSP), permutation flow shop scheduling problem (PFSP), hybrid flow shop scheduling problem (HFSP), zero idle flow shop scheduling problem (NIFSP), distributed permutation flow shop scheduling problem (DPFSP), blocking flow shop scheduling problem (BFSP).
👇