Introduction to Trusted Platform Module (TPM)
1
RPMB (Replay Protected Memory Block) Partition is a secure partition in eMMC.
When writing data to RPMB, eMMC verifies the legality of the data; only designated Hosts can write to it. During data reading, it also provides a signature mechanism to ensure that the data read by the Host is from within RPMB and not forged by an attacker.
In practical applications, RPMB is typically used to store data that requires protection against unauthorized tampering, such as public keys and serial numbers related to fingerprint payments on mobile phones. RPMB can authenticate write operations, but reading does not require authentication, allowing anyone to read. Therefore, data stored in RPMB is usually encrypted before storage.
Capacity Size
2
The size of two RPMB Partitions is determined by the BOOT_SIZE_MULT Field of the Extended CSD register, with the following calculation formula:
Size = 128Kbytes x BOOT_SIZE_MULT
Generally, the size of the Boot Area Partition is a multiple of 128KB, with a default in eMMC of 4 MB, meaning RPMB_SIZE_MULT is 32. Some chip manufacturers provide the ability to rewrite RPMB_SIZE_MULT to change the size of the RPMB Partition. The maximum RPMB_SIZE_MULT can be 128, meaning the maximum capacity of the Boot Area Partition can be 128 x 128 KB = 16384 KB = 16 MB.
Replay Protect Principle
3
Products using eMMC, during production, generate a unique 256 bits Secure Key for each product, which is burned into the OTP area of the eMMC (a one-time programmable area). Meanwhile, the Host retains this Secure Key in a secure area (e.g., TEE).
Internally, eMMC also has an RPMB Write Counter. Each time a legitimate write operation is performed to RPMB, the Write Counter automatically increments.
By applying the Secure Key and Write Counter, RPMB can achieve Replay Protect for data reading and writing.
RPMB Data Reading
4
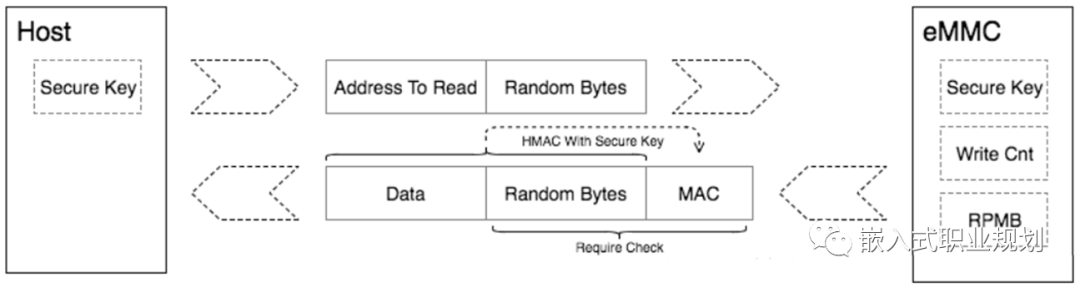
1. The Host initiates a request to read RPMB from eMMC, generating a 16 bytes random number to send to eMMC.
2. eMMC reads the requested data from RPMB and uses the Secure Key to calculate a signature by combining the read data with the received random number using the HMAC SHA-256 algorithm. Then, eMMC sends the read data, the random number, and the calculated signature back to the Host.
3. Upon receiving the RPMB data, random number, and signature, the Host first checks if the random number matches the one it sent. If they match, it uses the same Secure Key to sign the combination of data and random number using the HMAC SHA-256 algorithm. If the signature matches the one sent by eMMC, it confirms that the data read is correct and not forged by an attacker.
This reading process ensures that the Host accurately reads the data from RPMB.
RPMB Data Writing
5
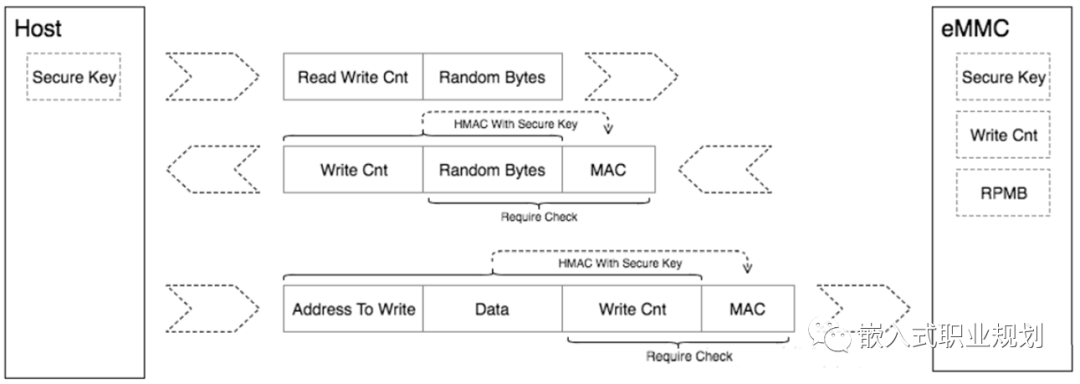
1. The Host follows the above reading process to read the RPMB Write Counter (to verify the validity of the data).
2. The Host combines the data to be written with the Write Counter and calculates a signature, then sends the data, Write Counter, and signature to eMMC.
3. Upon receiving the data, eMMC first checks if the Write Counter matches the current value. If they match, it then signs the combination of data and Write Counter and compares it with the signature sent by the Host. If the signatures match, authentication is successful, and the data is written to RPMB.
This writing process ensures that RPMB cannot be tampered with illegally.
Note: RPMB in UFS also uses the same principles as in eMMC.