 Introduction:
Introduction:
In the fields of web applications and API interface testing, the dynamic nature and complexity of testing scenarios impose high demands on the flexible management of test data. Traditional static test data is often insufficient to meet the needs of multi-user concurrency, parameterized requests, and response content validation. For example, in performance testing of e-commerce systems, if user IDs, order numbers, or real-time tokens cannot be dynamically generated, the coverage and authenticity of the tests will be significantly compromised. The variable functionality in HTTP testing has emerged to address this, combined with existing expression generation capabilities, providing an “intelligent channel” for the flexible execution of test cases and result validation, effectively enhancing testing efficiency and accuracy.
The Core Principles of Variable Functionality
XINERTEL
The variable functionality in HTTP testing supports flexible expansion of testing scenarios through dynamic data injection and extraction, with its core mechanism comprising the following three parts:
1. Variable Import:
By uploading files (such as CSV) for batch import or setting predefined variables, parameterized input can be achieved. For instance, in simulating a user login scenario, username and password combinations can be pre-stored for the testing tool to call as needed.
2. Variable Extraction:
Dynamic content can be extracted from key fields in response messages (such as JSON return values and HTTP header information) and saved as global variables for reuse in subsequent requests. For example, extracting a user token from a login response and using it for authentication in subsequent order interface requests.
3. Assertion and Termination Control:
Based on variable matching results, an assertion mechanism can be triggered to verify in real-time whether the response content meets expectations, and to terminate testing in case of anomalies to prevent error propagation. For instance, checking if the “status code” returned by the interface is 200, and if consecutive failures reach a threshold, the test will be terminated. Coupled with packet capture functionality, it can also save the erroneous message for subsequent analysis.
The above functionalities, through deep integration with testing tools, support cross-request data sharing and logical control, achieving an upgrade from “static scripts” to “dynamic links” in testing.
Types and Usage of Variables
XINERTEL
The types of variables currently supported by the instrument include:String (string), Number (number), IPv4 (IPv4 address), IPv6 (IPv6 address), MAC (MAC address), Form (form).
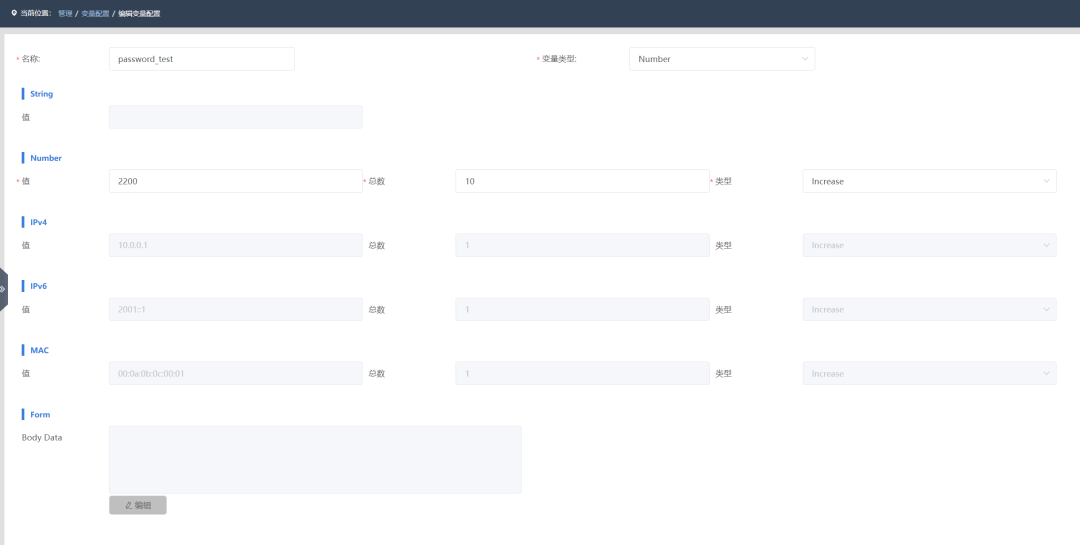
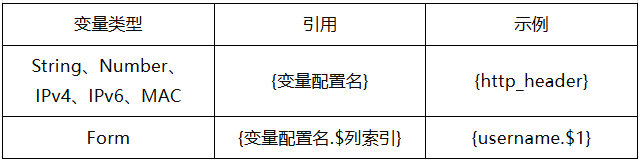
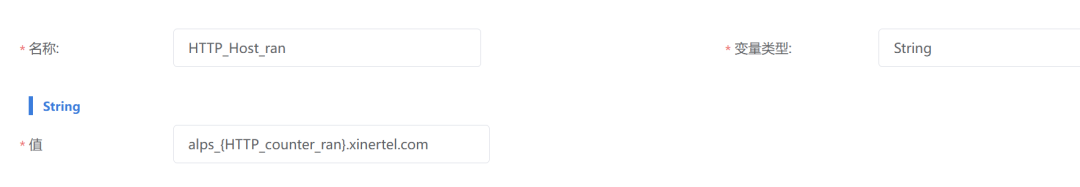
In String variables, other variables can also be referenced to generate new variables. For example, referencing HTTP_Host_ran variable in HTTP_counter_ran to generate new variable parameters.
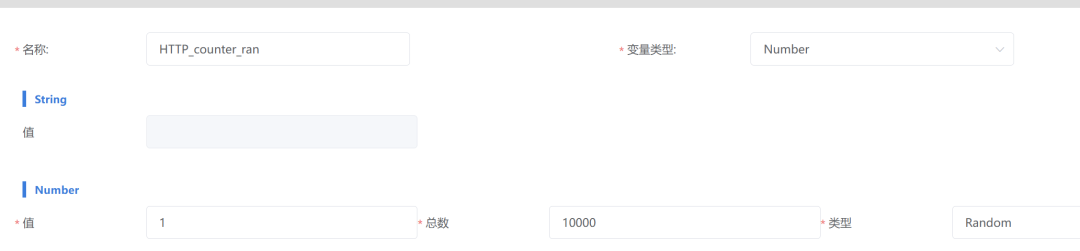 The Necessity of Variable Functionality Testing
The Necessity of Variable Functionality Testing
XINERTEL
1. Validate the Accuracy of Dynamic Scenarios:
Ensure that the generation, transmission, and extraction logic of variables is correct under concurrent requests, parameterized inputs, and dependency chain scenarios (e.g., session tokens passed across interfaces).
2. Improve Testing Efficiency and Coverage:
Replace manual data input with automation, quickly covering test cases for multiple users, roles, and data combinations.
3. Ensure Reliability of Anomaly Handling:
By injecting invalid data or simulating extraction failures, verify whether the tool can correctly handle missing or incorrectly formatted variables, preventing system crashes due to data anomalies.
Testing Methods for Variable Functionality
XINERTEL
On the XINERTEL ALPS testing platform, we can easily test variable-related functionalities. Below, we will look at the actual configuration methods for variable import, response variable extraction, and assertion functionality.
Variable Import Configuration TEST METHODS
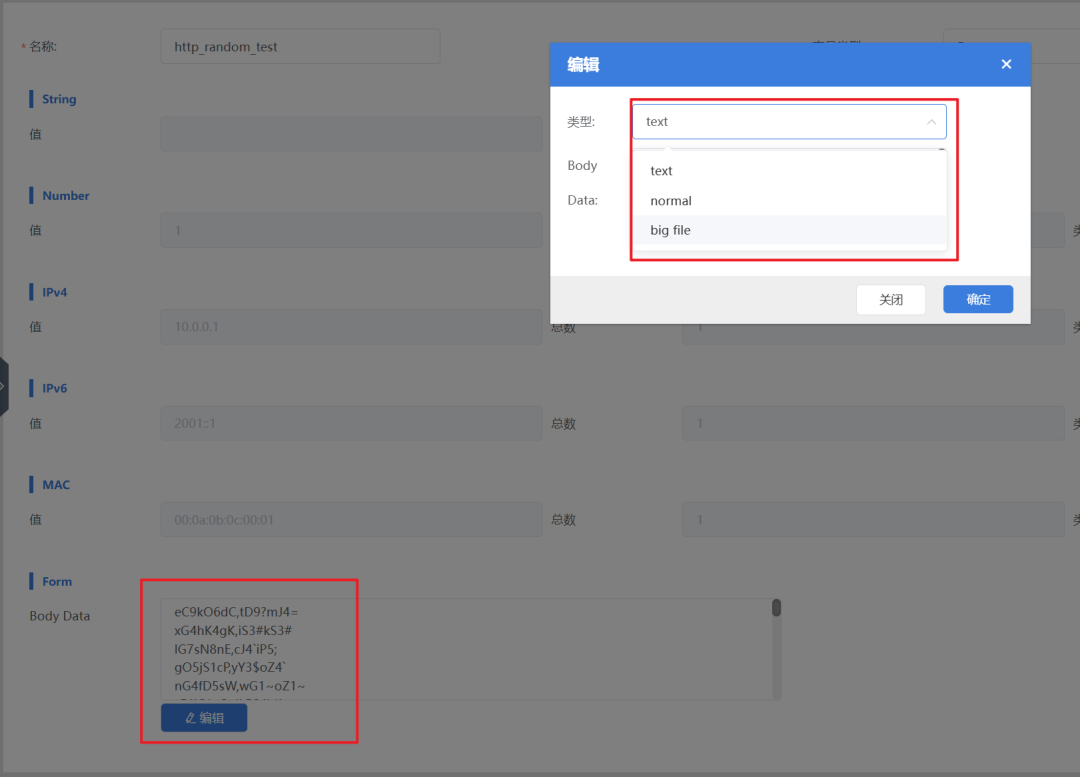
1. CreateForm Variable: Go to [Management → Variable Configuration], select the variable type as Form, click “Import” to upload an Excel/CSV file, mapping the data to the variables.
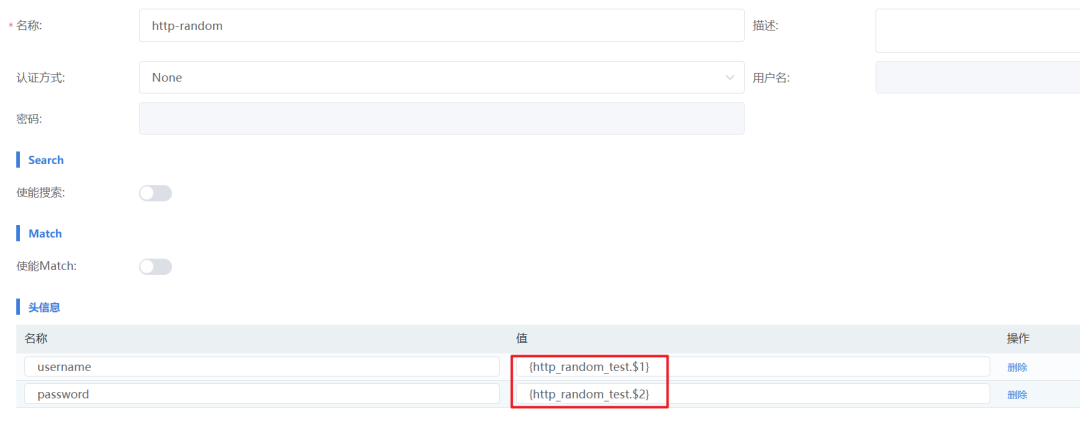
 2. Bind Request Parameters: In [Request Configuration], add headers or parameters using the format {Variable Configuration Name.$Column Number} to reference variables (for example, {http_random_test.$2} to take the second column).
2. Bind Request Parameters: In [Request Configuration], add headers or parameters using the format {Variable Configuration Name.$Column Number} to reference variables (for example, {http_random_test.$2} to take the second column).
 3. Loop Call Data: After adding a GET request, each execution will automatically poll by row in the Body data, without the need to write loop code manually!!
3. Loop Call Data: After adding a GET request, each execution will automatically poll by row in the Body data, without the need to write loop code manually!!
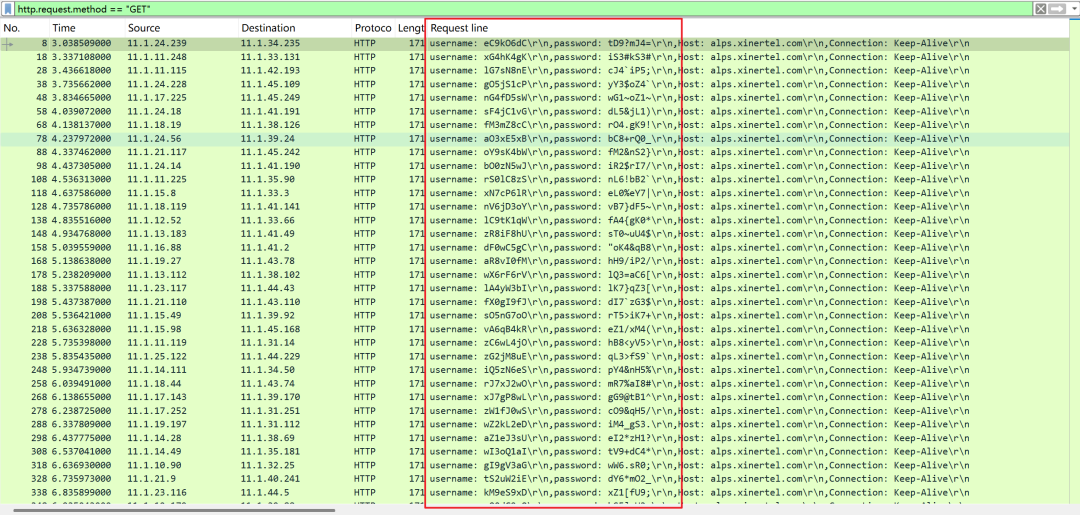
Value Point: When the polled data changes irregularly, it can be simulated more closely to the actual environment through the combination of imported data and variable configuration.
Response Variable Extraction TEST METHODS
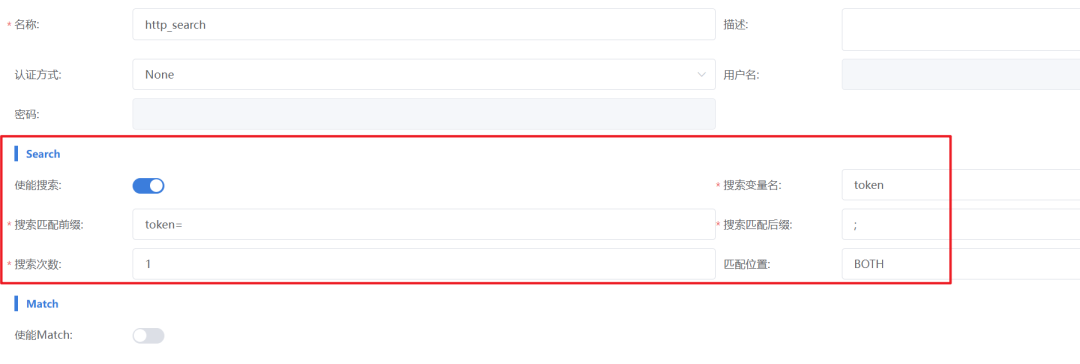
1. Configure Search Rules: Add a client/server simulation component, enable search in the request configuration of the HTTP command, and set it as follows:
–Variable Name: token (this name will also correspond to the variable name in subsequent searches in new requests)
–Prefix/Suffix: For example, prefix “token=, suffix “;“
–Search Count: For the first match, set the count to 1
–Match Location: Select BOTH to cover both HTTP headers and payloads.
2. Automatic Capture and Transmission: After executing the request, the Token in the response will be extracted as a variable and directly called in subsequent requests using {token}!
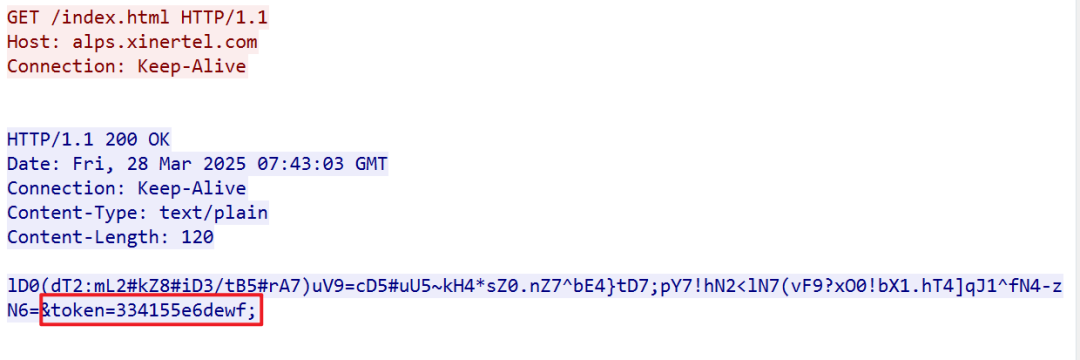 Subsequent requests will carry the token returned by the server.
Subsequent requests will carry the token returned by the server.
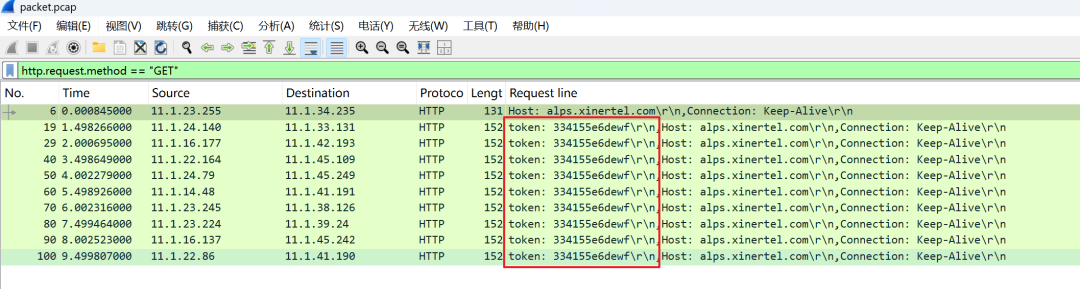 Value Point: Say goodbye to regular expressions; dynamic parameters can be passed across interfaces without hard coding!
Value Point: Say goodbye to regular expressions; dynamic parameters can be passed across interfaces without hard coding!
Assertion and Termination Control Testing TEST METHODS
-
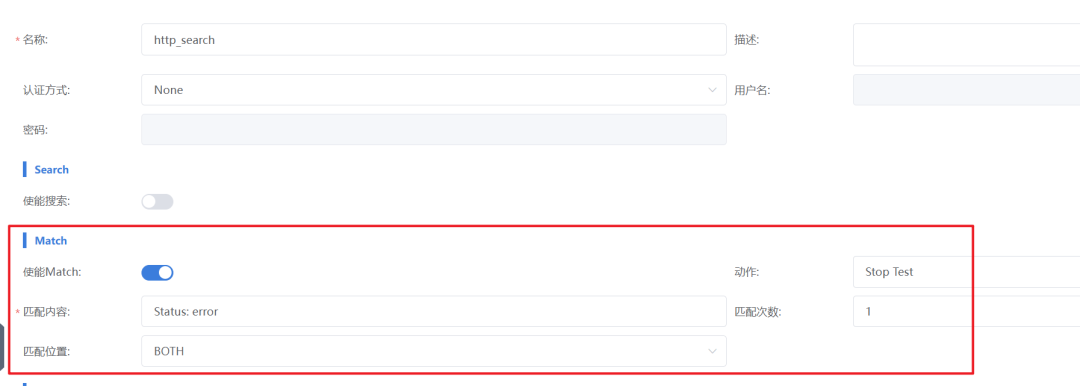
Configure Assertion Rules: Add a client/server simulation component, enable Match in the request configuration of the HTTP command, and set:
– Matching Content: “status”:”error”
– Matching Count: For example, 1 time to trigger.
– Matching Location: Select BOTH to ensure coverage of both HTTP headers and payloads.
2. Configure Packet Capture: To ensure capturing messages when faults occur, we can set the number of captured packets to 9 to avoid too many mixed packets that are difficult to analyze and locate faults (the instrument supports a maximum of 1G of packet capture cache), and enable Enable Overwrite.
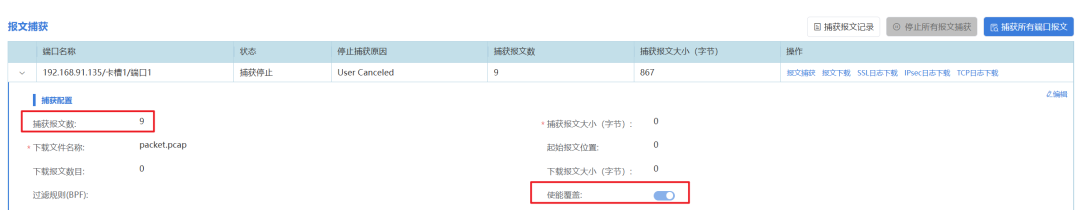
3. Automatic Circuit Breaker for Anomalies: When the response hits the matching rules, the test will immediately terminate and be marked as failed, accurately locating the problem node!
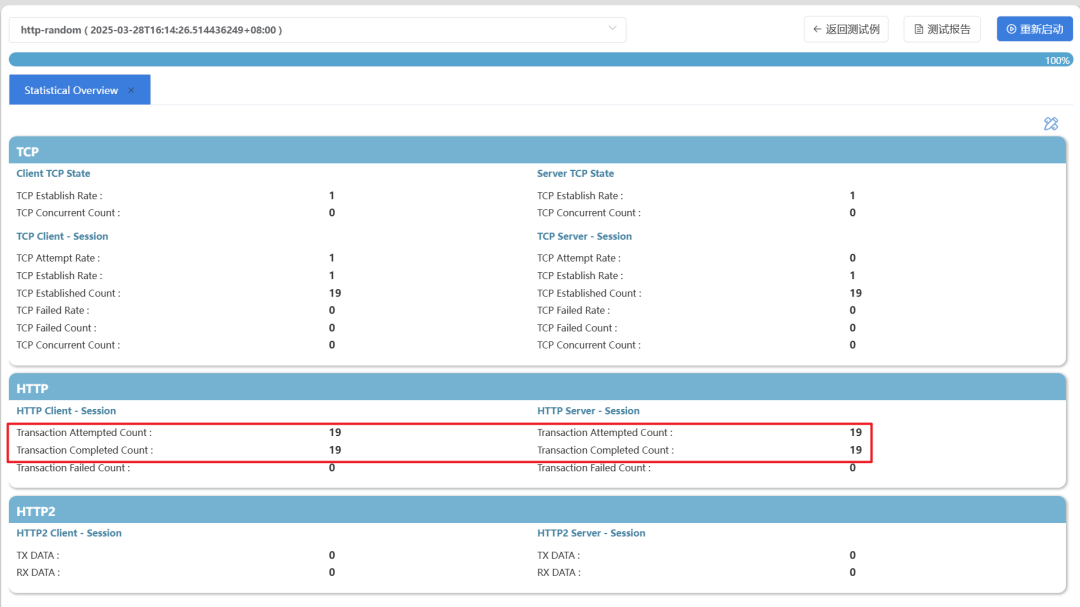
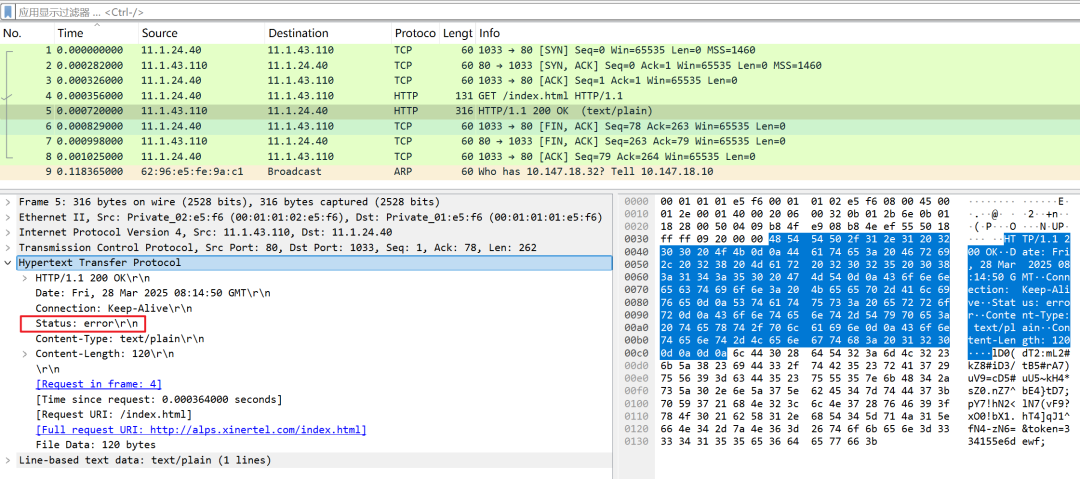
The following is a comparison of messages with and without response assertions set. It can be seen that without setting assertions, even if an error occurs, the instrument will continue executing, making it difficult to accurately locate the error scene.
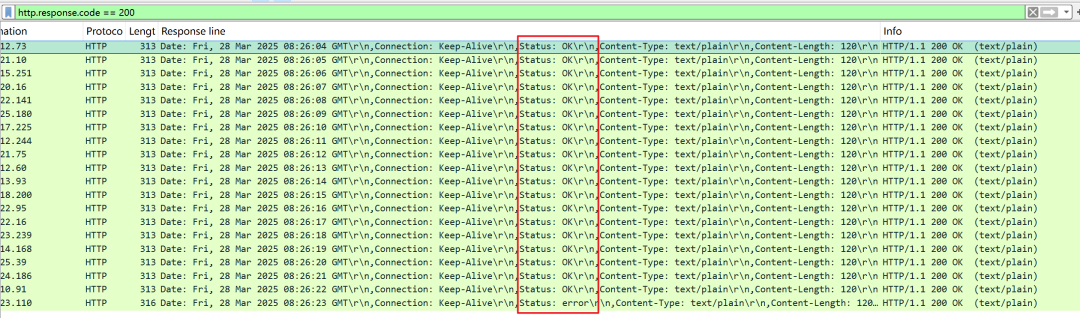
Response assertion set
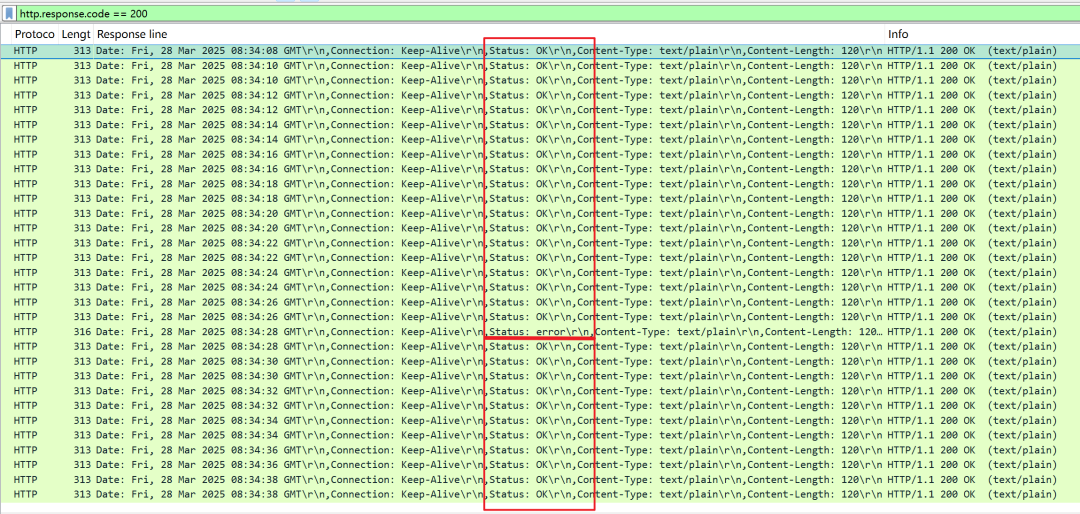
Response assertion not set
Value Point: Self-checking ability of tests, troubleshooting faster!
DarPeng Series Testing Platform
XINERTEL
The DarPeng series high-performance network application security testing instrument is launched by XINERTEL, aimed at voice, video, data applications, and network security. It accurately simulates the network access behavior of millions of real terminal users to perform stress and performance testing on individual application-layer perceptive devices (such as Firewall/IPS/IDS/WAF/DPI etc.) or entire systems; by simulating a large amount of real attack traffic and malicious software, it verifies the detection, defense, and virus capabilities of network security devices or systems, while also confirming the control and identification capabilities of the tested devices through replaying real environment traffic.
XINERTELDarPeng2000E is a security testing instrument built on the new generation x86 architecture, featuring high performance, high bandwidth, high integration, and high efficiency.

Combined with XINERTEL’s new generation of B/S architecture-based testing software ALPS (Application Layer Protocol Simulator), it provides powerful application layer traffic simulation capabilities.ALPS software can simulate the following application layer protocols and scenarios:
-
Application Layer Protocol Simulation: Including HTTP, FTP, TCP, DNS and other common network protocols, ensuring compatibility and functionality testing of network applications;
-
Voice Communication Simulation: Supports VoIP SIP and RTP protocols, simulating voice communication traffic, assessing network support for voice services;
-
Video Streaming Media Simulation: Covers RTSP, RTP, IPTV and other protocols, simulating video streaming media services, testing the efficiency of network transmission for video content.
ALPS software performs excellently, capable of handling millions of HTTP/TCP new connection requests and supporting up to hundreds of millions of concurrent connections, meeting the testing needs of large-scale network environments. In addition, ALPS also has the following advanced simulation capabilities:
-
Attack Traffic Simulation: Simulates DDoS attacks, botnets, and custom attacks, testing the defensive capabilities of network security devices;
-
Malicious and Virus Traffic Simulation: Generates malicious and virus traffic, assessing the detection and response mechanisms of network security solutions;
-
Encryption Protocol Support: Integrates national secret algorithms in IPsec, SSL and other encryption and decryption protocols, ensuring compliance with national security standards;
-
Audio and Video Quality Testing: Integrates audio and video quality testing in application layer protocol simulation, assessing network support for multimedia services.
END
Written by: Jiang Bangquan
Typeset by: Marketing Department
If you need more information, please feel free to contact us
Product Consultation Hotline:010-82349338
