
Recently, those following IT Home may have heard about an issue with certain models of SSDs from Samsung and Micron, where the built-in hardware encryption has vulnerabilities that could allow access to data on the drive without entering a password.
It is important to note that the BitLocker feature in Windows 10 (or Windows 8.1) relies on the built-in hardware encryption of the SSD by default rather than the encryption provided by Windows 10 itself. This means that when hardware encryption is available on the SSD, Windows 10 not only does not verify the reliability of the SSD’s hardware encryption, but also disables its own software-based encryption, potentially exposing your data to risks.
If you have extremely sensitive data on your drive, today’s IT Home Geek Academy will discuss how to disable the hardware encryption of the SSD and switch to software encryption with BitLocker.

Before we begin, we need to check the encryption status of the BitLocker drive in Windows 10 using the following method.
Run Command Prompt (CMD) as an administrator and enter the following command:
manage-bde.exe -status
The information displayed in the “Encryption Method” line of the execution result indicates the current BitLocker encryption status of your computer. If this line shows anything other than “Hardware Encryption”, it means the target drive is using BitLocker’s software encryption, and you do not need to proceed further.
If this line shows “Hardware Encryption”, please follow the steps below to disable hardware encryption and enable software encryption.
First, we need to decrypt the encrypted drive. In File Explorer, right-click on the target drive icon, select “Manage BitLocker” from the context menu, click on the “Turn Off BitLocker” link, and then click the “Turn Off BitLocker” button in the pop-up dialog.
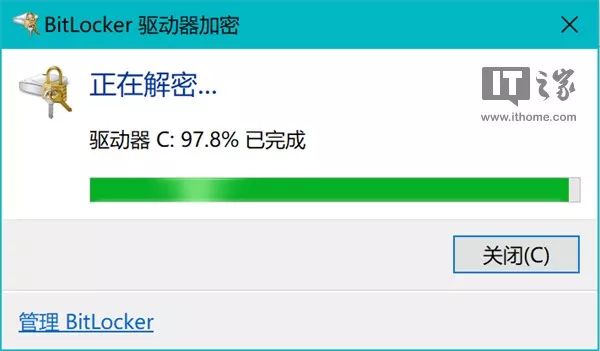
Decrypting the BitLocker drive may take some time, please be patient.
Once decryption is complete, search for and run “gpedit” in the Cortana search box, and navigate to the following location in the left pane:
Computer Configuration/Administrative Templates/Windows Components/BitLocker Drive Encryption/Operating System Drives (or Fixed Data Drives, or Removable Data Drives)
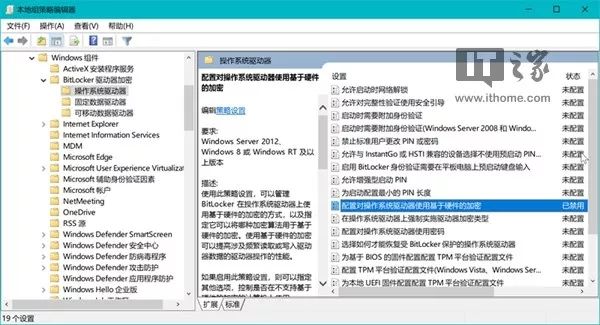
Look to the right pane and double-click the setting:
Configure use of hardware-based encryption for operating system drives (or fixed data drives, or removable data drives)
Set the policy for this item to “Disabled” and then click the “OK” button to save the changes.
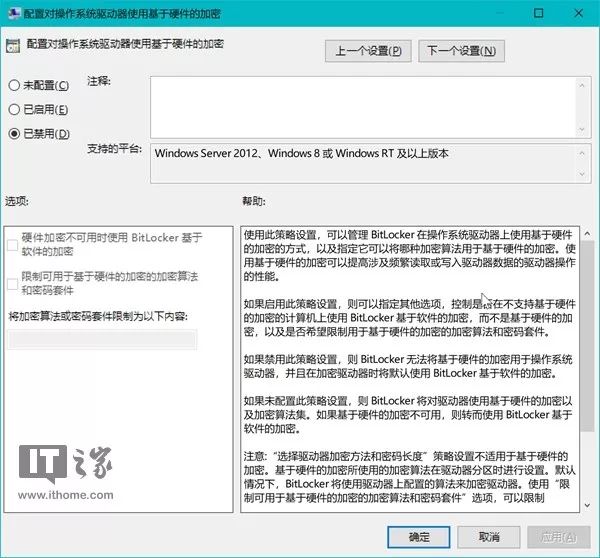
After completing the group policy settings, there is no need to restart the system. Just right-click on the target drive icon in File Explorer and click “Turn On BitLocker” to re-encrypt the drive.
Considering that Windows 10 Home Edition does not include the Group Policy Editor, to make this tutorial applicable to all Windows 10 users, we will also discuss how to modify the registry to disable BitLocker’s hardware encryption.
In the Cortana search box, search for and run “regedit”, and navigate to:
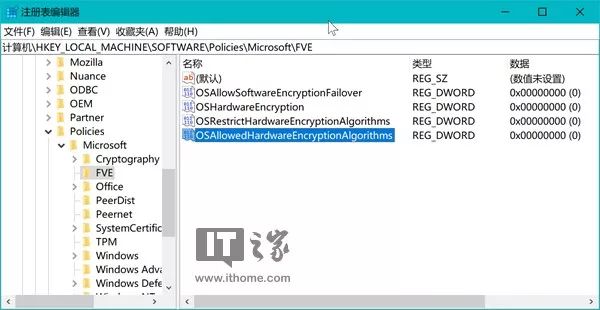
\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE\
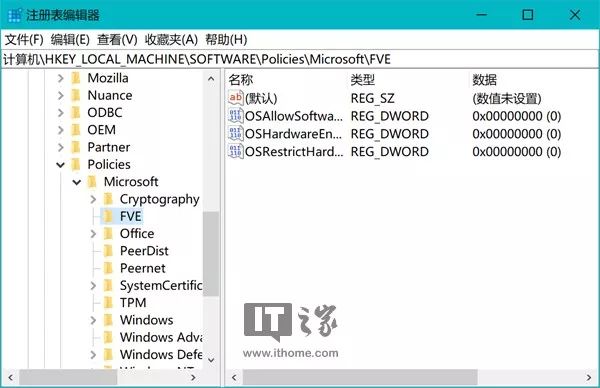
Note:
If there is no “FVE” item under “\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\”, please create it manually.
In the directory we just navigated to, create a new DWORD (32-bit) value and name it:
OSAllowedHardwareEncryptionAlgorithms
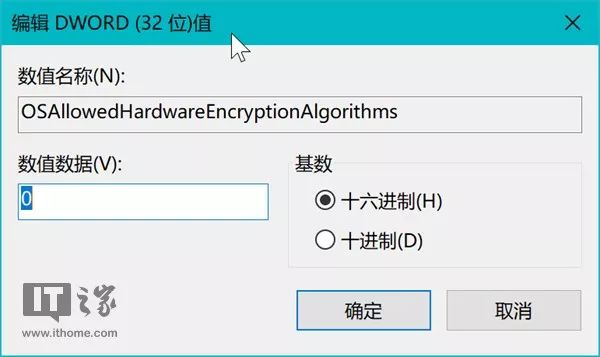
Double-click the newly created value named “OSAllowedHardwareEncryptionAlgorithms” and set its value data to 0, click the “OK” button to save the changes, and then restart the system.
After the system restarts, the changes we made in the registry will take effect, and you can re-encrypt the drive using BitLocker in File Explorer.
That concludes today’s tutorial. For more practical tutorials and informative articles, please continue to follow IT Home Geek Academy.
– END –
Featured Articles from the Academy:
Selecting the Right Computer Configuration in 10 Minutes
Graphics Card Knowledge Demystified
Flashing Android OS on Lumia Phones
Installing “Almost” Chrome OS on PC
Using Chrome Extensions on Android Phones
Understanding Files on Android Phones
What’s Inside Android APK Installation Packages?
Learn to Shut Down Windows 10 in 10 Seconds
Turning an Old Computer into a “Private Cloud”
After Complaining About Baidu for Years, Do You Really Know How to Search?


For more fresh technology news, click to read the original article on IT Home.