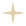UART has parity check, and CAN communication has CRC check. Communication protocols such as Modbus, MAVlink, and USB also have checksum information.
When customizing data storage, experienced engineers will always add some checksum information.
In your daily communication or data storage, do you use checksum information? Below are several common checksum algorithms.
Checksum is the most basic and commonly used checksum algorithm by embedded software engineers. Its implementation method is very simple, so simple that it only takes a few lines of code.
There are many ways to implement it, and it varies by programming language and application. Below is an example of an 8-bit checksum in C language:
uint8_t CheckSum(uint8_t *Buf, uint8_t Len){ uint8_t i = 0; uint8_t sum = 0; uint8_t checksum = 0;
for(i=0; i<len; &="" +="*Buf++;" 0xff;="" checksum="sum" checksum;}<="" code="" i++)="" return="" sum="" {="" }=""></len;>
XOR Check is similar to Checksum; it performs an “XOR” operation on the data, ultimately obtaining an “XOR value”.
uint8_t CheckXOR(uint8_t *Buf, uint8_t Len){ uint8_t i = 0; uint8_t x = 0;
for(i=0; i<len; code="" i++)="" return="" x="x^(*(Buf+i));" x;}<="" {="" }=""></len;>
There are many ways to implement checksum and XOR checks; for example, some may also pass a parameter as the XOR check value.
Of course, the above code is for learning reference only; the actual application should modify the code according to the project situation.
CRC: Cyclic Redundancy Check.
CRC is the most commonly used error-checking code in data communication. Its characteristic is that the length of the information field and the checksum field can be arbitrarily selected. Cyclic Redundancy Check (CRC) is a data transmission error-checking function that performs polynomial calculations on the data and appends the result to the end of the frame. The receiving device also executes a similar algorithm to ensure the correctness and integrity of data transmission. (Source: Internet)
CRC checks are a type of redundancy check, and students majoring in computer-related fields in college should have learned about CRC checks (though not many may have understood it during their studies).
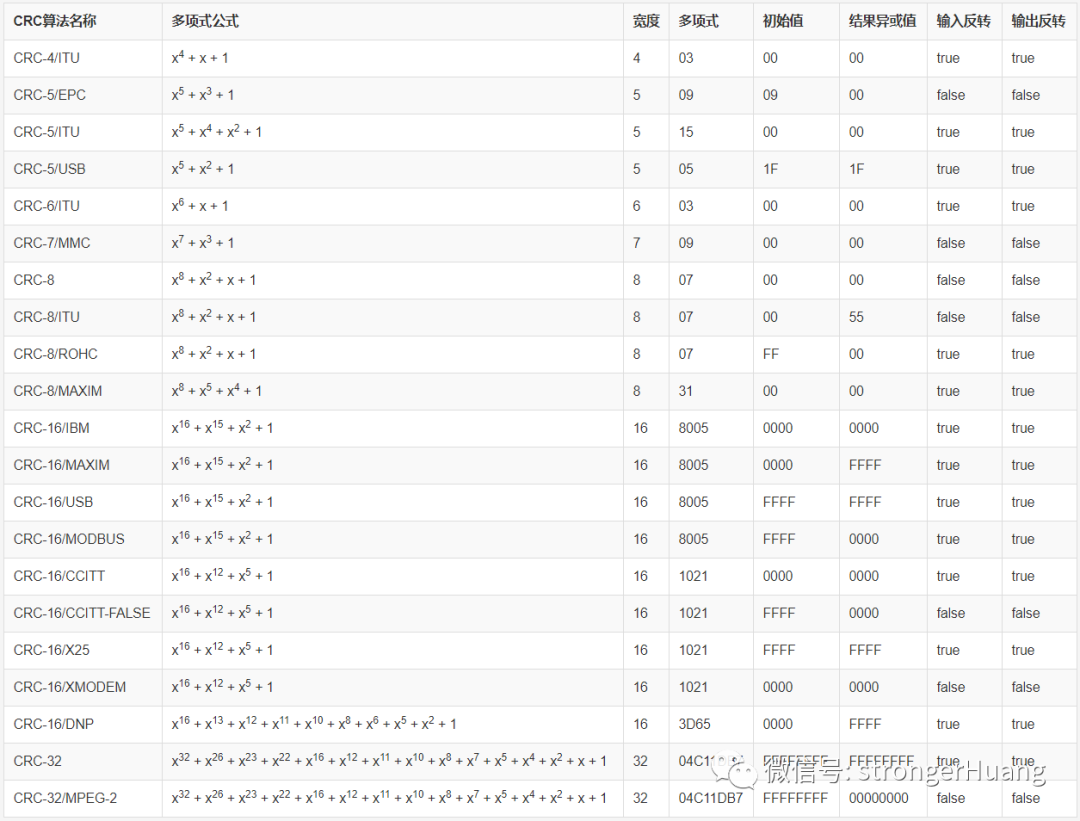
There are various variants of CRC, such as: CRC-1, CRC-5-USB, CRC-8, CRC-16, CRC-32, CRC-64, etc. Among these, CRC-16 is widely used in the embedded field.
Common CRC parameter models:
For example, here is the source code for implementing CRC16 on a microcontroller:
uint8_t CRCTAB_H[256] = {/*Table omitted*/};uint8_t CRCTAB_L[256] = {/*Table omitted*/};void CRC16(uint8_t *pData, uint8_t Len, uint8_t *CRC_H, uint8_t *CRC_L){ uint8_t i; uint8_t index; uint8_t crc_h = 0xFF; uint8_t crc_l = 0xFF;
for(i=0; i<len; *crc_h="crc_h;" *crc_l="crc_l;}</code" +="" crc_h="crc_l^CRCTAB_H[index];" crc_l="CRCTAB_L[index];" i);="" i++)="" index="crc_h^*(pData" {="" }=""></len;>
CRC checks are implemented differently in different scenarios, and there are many publicly available libraries and source codes online, such as:
LibCRC – An open-source CRC library in C:
https://github.com/lammertb/libcrc
There are also online tools for calculating CRC checks and generating code; interested readers can learn more about them.
MD5: Message-Digest Algorithm 5.
From the name, it is clear that it is a cryptographic algorithm developed from MD3 and MD4. It primarily collects the information summary of the file for calculation and encryption.
By using the MD5 algorithm for encryption, a file can obtain a unique MD5 value, which is unique, just like our fingerprints. Therefore, we can determine whether a file is correct by its MD5 value. Passwords encrypted will also generate MD5 values, and forums use MD5 values to verify whether users’ passwords are correct.
MD5 is an algorithm that takes variable-length input and produces a fixed-length output of 128 bits. Through the program flow, it generates four 32-bit data, which are combined into a 128-bit hash. The basic process involves modulo operations, length adjustments, and cyclical calculations with linking variables to produce the result.
MD5 source code is readily available online, with versions in various programming languages (C, C++, JAVA).
For example, here is a C version shared by a user named talent518:
https://github.com/talent518/md5
As programming technology continues to advance, checksum algorithms are becoming more numerous, with both general algorithms and specific algorithms for special fields.
For example, I previously worked on password-related development, using the SM3 cryptographic hash algorithm published by the Cryptography Administration.
Additionally, there is the SHA-1 algorithm (Secure Hash Algorithm 1), which is an improvement on the MD4 algorithm.
This article concludes here. There are many checksum algorithms available on the market; if needed, you can search online for more information.
Copyright belongs to the original author. If there is any infringement, please contact for deletion.
From STM32 to Embedded Linux Driver Development
Foreign chip companies are laying off: no R&D left!
ChatGPT implements various lighting programs for 51, STM32, Raspberry Pi, etc.
→ Follow to stay updated ←