1
Introduction
Bluetooth technology has been widely applied in various scenarios such as personal electronics, automotive electronics, smart homes, smart cities, and industrial IoT, gaining support from over 30,000 manufacturers. The number of Bluetooth-enabled devices has reached 3.6 billion, and it is expected to rise to 5.2 billion by 2020. Bluetooth is currently one of the most widely used communication technologies in near-field communication environments. If serious security vulnerabilities arise in this technology, the impact will be extensive and far-reaching.
The Bluetooth Special Interest Group has fully considered Bluetooth’s security during the standard formulation process, with designs in areas such as device pairing, authentication, authorization, confidentiality, and integrity. However, during the implementation of the Bluetooth protocol by various manufacturers, inconsistencies in understanding the Bluetooth protocol or limitations in device resources have exposed numerous security incidents. Products including mobile phones, automotive entertainment systems, smart bracelets, smart locks, Bluetooth light bulbs, and Bluetooth safes have all been found to have Bluetooth vulnerabilities, raising concerns among users.
Addressing the security issues of Bluetooth technology requires manufacturers to improve their security R&D processes, enhance security designs, and introduce necessary steps such as third-party security testing; it also requires security researchers to continuously study and discover vulnerabilities in Bluetooth device protocols, develop specialized Bluetooth vulnerability detection and monitoring tools, and promote the safe and orderly development of the entire Bluetooth industry.
This article first briefly describes Bluetooth technology and the Bluetooth industry, then analyzes the Bluetooth security mechanisms and current status, elucidates the security threats faced by Bluetooth technology through an analysis of public and original Bluetooth vulnerabilities, and finally presents a specific Bluetooth attack case.
2
Introduction to Bluetooth Technology
Bluetooth is a development standard for short-range radio frequency (RF) communication, primarily used to establish wireless personal area networks. Bluetooth has been integrated into many types of commercial and consumer devices, including mobile phones, laptops, cars, printers, keyboards, mice, headphones, and more recently, medical devices and personal devices (such as smartwatches, music speakers, home appliances, fitness equipment, and trackers). This allows users to form self-organizing networks to transmit voice and data between various devices.
Bluetooth is a low-cost, low-power technology that provides a mechanism for creating small wireless networks in a special way, known as a piconet. A piconet consists of two or more physically proximate Bluetooth devices operating on the same channel using the same frequency hopping sequence. Bluetooth piconets are typically established on a temporary and changing basis, providing flexibility and scalability for communication between mobile devices.
3
The Bluetooth Industry
3.1 Current Status of the Bluetooth Market
Bluetooth is currently managed by the Bluetooth Special Interest Group (Bluetooth SIG). The Bluetooth SIG has over 33,000 member companies worldwide, distributed across multiple fields including telecommunications, computing, networking, and consumer electronics. The Bluetooth SIG is responsible for overseeing the development of Bluetooth specifications, managing certification programs, and maintaining trademark rights. Manufacturers’ devices must comply with the Bluetooth SIG’s standards to enter the market as “Bluetooth devices.”
According to data released by the Bluetooth SIG in 2018, the shipment of Bluetooth devices reached 3.6 billion in 2017, and it is expected that by 2022, there will be 5.2 billion Bluetooth devices deployed across various industries.
3.2 Bluetooth Application Market
With the continuous growth in IoT demand, Bluetooth applications are also evolving, expanding from initially focusing on point-to-point connectivity issues to broadcast communication for indoor positioning and location-based services. Currently, driven by Bluetooth mesh networks, Bluetooth has created an emerging market that requires reliable wireless solutions to establish large-scale device networks. The table below shows the Bluetooth application market.
|
Function |
Audio Transmission |
Data Transmission |
Location Services |
Device Layer Network |
|
Application Scenarios |
Wireless Headphones Wireless Speakers In-Car Infotainment Systems |
Sports and Fitness Devices Medical and Health Devices Peripheral Devices and Accessories |
Landmark Information Navigation Maps and Related Services Item and Asset Tracking |
Control Systems Monitoring Systems Automation Systems |
|
Bluetooth Version |
Bluetooth Basic Rate/Enhanced Data Rate (BR/EDR) |
Low Energy Bluetooth |
3.3 Bluetooth Application Scenarios
3.3.1 Mobile Phones, Tablets, and Personal Computers
Bluetooth technology has become an inherent part of mobile phones, tablets, and personal computers, with over 2 billion Bluetooth devices shipped in this sector in 2018.
3.3.2 Audio and Entertainment
Bluetooth has become synonymous with the wireless audio and entertainment market, with extensive use of Bluetooth technology in wireless speakers, headphones, game controllers, hearing aids, and other devices.
3.3.3 Automotive
Bluetooth is the leading technology behind in-car infotainment systems, enabling hands-free calling and audio transmission functions. In addition, Bluetooth is also applicable to emerging automotive use cases such as keyless entry, in-vehicle wearable devices, and connected maintenance.
3.3.4 Connected Devices
Bluetooth is also applied to connected devices ranging from everyday household items to smart medical devices, such as smartwatches, wearable devices in healthcare, enterprise-grade wearables (like smart glasses and scanners), and consumer-grade Bluetooth robots.
3.3.5 Smart Buildings
Bluetooth has expanded the definition of smart buildings by enabling indoor positioning and location-based services. Bluetooth technology provides a building-wide Beacon network, enabling indoor positioning and location-based services, including landmark information, indoor navigation, and asset tracking. Additionally, Bluetooth-connected lighting is becoming a major use case in automation, and healthcare institutions are adopting Bluetooth technology to monitor patients, track assets, and advance emergency services.
3.3.6 Smart Industry
Bluetooth technology applied in wireless sensor networks can achieve predictive maintenance and detect issues before machine failures occur.
3.3.7 Smart Home
The first batch of Bluetooth home automation systems was launched in 2018, and the Bluetooth network continues to provide a reliable wireless connection platform for automating control of lighting, temperature control, smoke detectors, cameras, doorbells, locks, and more.
4
Current Status of Bluetooth Security
4.1 Bluetooth Security Mechanisms
Since its inception, Bluetooth has gone through versions 1.0 to 5.0 and Bluetooth mesh, each with different features. Generally, Bluetooth 4.0 and above is referred to as Low Energy Bluetooth (LE), while versions prior to 4.0 are referred to as Bluetooth BR/EDR/HS (Bluetooth 1.0, 2.0, 3.0). The Bluetooth standard specifies five fundamental security services:
(1) Authentication: Verifying the identity of the communicating devices based on their Bluetooth addresses. Bluetooth does not provide a native user authentication mechanism;
(2) Confidentiality: Ensuring that only authorized devices can access and view the transmitted data to prevent information leakage due to eavesdropping;
(3) Authorization: Allowing control over resources by ensuring that devices are authorized before being permitted to use a service;
(4) Message Integrity: Verifying that messages sent between two Bluetooth devices have not been altered during transmission;
(5) Pairing/Binding: Creating one or more shared keys and storing these keys for subsequent connections to form a trusted device pair.
The key to the authentication and encryption mechanisms provided by Bluetooth lies in generating a secret symmetric key. In Bluetooth BR/EDR, this key is called the link key, while in Low Energy Bluetooth, it is referred to as the long-term key. Key generation is primarily accomplished through pairing, and the following two pairing methods will be introduced: PIN (Traditional Pairing) and SSP (Secure Simple Pairing).
4.1.1 PIN (Traditional Pairing)
PIN (Traditional Pairing) is completed when the user enters the same PIN code on one or both devices. The PIN code used in Bluetooth pairing can be a binary number of 1 to 16 bytes or more commonly alphanumeric characters. For low-risk application scenarios, a 4-digit PIN code is generally used; for higher-risk application scenarios, a longer PIN code (such as an 8-character alphanumeric code) is typically used.
4.1.2 SSP (Secure Simple Pairing)
SSP was first introduced in Bluetooth 2.1. Compared to PIN, SSP simplifies the pairing process and enhances security by adding ECDH public key encryption to prevent passive eavesdropping and man-in-the-middle (MITM) attacks during pairing. SSP provides the following four association models:
(1) Numeric Comparison
During pairing, a six-digit number is displayed on each device. If the numbers match, a “Yes” response is provided on each device. Otherwise, the user responds “No,” and the pairing fails. The main difference from traditional pairing using a PIN is that the displayed numbers are not used for generating the link key.
(2) Passkey Entry
In this model, only one device displays a six-digit number, and the user enters it on the device with input capability. Like the numeric comparison model, this six-digit number does not participate in link key generation.
(3) Just Works
This mode applies when at least one of the pairing devices has neither display nor input capability. The user does not need to perform any actions during the connection process, which makes this mode vulnerable to man-in-the-middle attacks.
(4) Out of Band
This mode is designed to support external communication methods, such as NFC, to exchange some information used during pairing. Pairing is completed through Bluetooth radio frequency, but it still requires non-Bluetooth transmission mechanisms to provide information.
4.2 Analysis of Typical Bluetooth Security Vulnerabilities
4.2.1 Smartphones
In September 2017, IoT security company Armis discovered nine 0-day vulnerabilities in the Bluetooth protocol, known as BlueBorne. BlueBorne could exploit these vulnerabilities to attack devices running Android, iOS, and other operating systems, posing significant risks.
For example, in Android smartphones, if the user has Bluetooth enabled and has not patched the system, hackers can exploit this vulnerability to attack the phone. Once successful, hackers can gain very high privileges, such as controlling the camera, taking photos, capturing screenshots, launching applications, waking up the phone; accessing contacts, photos, documents; and controlling the phone’s keyboard.

Figure 4-1 BlueBorne
4.2.2 Automotive Entertainment Systems
Bosch’s Drivelog Connect is a service that provides information about vehicle status, offering drivers a wealth of convenient features and vehicle health status information, such as potential issues, service deadlines, fuel consumption data, and driving conditions. Users can connect to the Drivelog Connector adapter via a mobile app, which has a Bluetooth certification vulnerability that exposes information leakage. Attackers can quickly brute-force the paired PIN code offline through this vulnerability, allowing them to connect to the Drivelog Connect adapter via Bluetooth. Once connected, they can inject malicious commands to control the vehicle, even shutting down a running car engine within Bluetooth range.
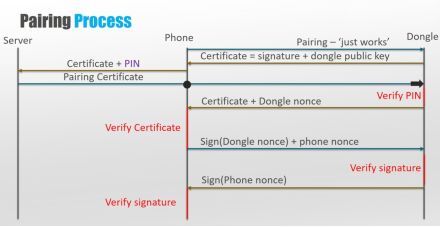
Figure 4-2 Pairing Process Between Mobile Bluetooth and Drivelog Adapter
Figure 4-2 describes the pairing process between the mobile Bluetooth and the adapter, where the adapter sends its certificate, which contains the public key and a signed binary string. The signature uses the SHA-256 hash algorithm, with parameters calculated from the adapter’s MAC address, adapter PIN code, and adapter public key.
If an attacker can connect to the adapter, they can obtain enough information to brute-force the PIN code. Given that the Drivelog adapter’s PIN code consists of 8 digits, there are a total of 100 million possible combinations. Generally, an ordinary laptop can complete 100 million SHA-256 hash calculations in 30 minutes; if multiple servers are used for computation, this time can be reduced. This means that attackers can crack the PIN code in a short time and successfully connect to the adapter.
4.2.3 Smart Wearables
Smart wearables mainly include Bluetooth bracelets, Bluetooth watches, etc. These devices often use Low Energy Bluetooth technology and communicate with mobile apps via Bluetooth. These devices typically use the Just Works pairing mode and do not authenticate the source of Bluetooth commands. Attackers can often control the device by obtaining Bluetooth commands through other means.
For example, in a certain brand of bracelet, as long as the attacker writes a specially formatted data segment after the Bluetooth connection, they can send arbitrary Bluetooth commands to the bracelet (such as private protocol vibrations, LED color changes, enabling real-time step monitoring, etc.).

Figure 4-3 A Certain Brand of Bracelet
4.2.4 Bluetooth Locks
Low Energy Bluetooth technology is widely used in smart locks, allowing users to unlock with just a tap on a mobile app or WeChat mini-program. However, the security of Bluetooth locks as security products is not optimistic. At DEFCON 24, security researchers had already exposed security vulnerabilities in several Bluetooth smart locks, with a variety of vulnerabilities ranging from plaintext passwords to replay attacks. In fact, one smart lock completely failed under fuzzing attacks, leaving the door wide open.

Figure 4-4 Bluetooth Lock
4.2.5 Bluetooth Light Bulbs
Bluetooth light bulbs are a very common type of Bluetooth smart home device, typically using Low Energy Bluetooth technology and controlled via mobile apps. Since the bulbs themselves do not have input/output capabilities, the connection between the bulb and the mobile app generally uses the Just Works pairing mode. If the bulb does not have any authentication mechanism for the source of Bluetooth commands, attackers can often control the bulb by replaying the Bluetooth commands sent from the mobile app.
For example, in a certain brand of Bluetooth light bulb, the bulb can be controlled via a mobile app to change its on/off state and color.
Figure 4-5 Bluetooth Light Bulb App
Figure 4-6 shows the captured Bluetooth communication data packet, where the attacker sends the command “0800c430d239cc260000” to change the color of the bulb. By replaying different commands, the attacker can control the bulb.
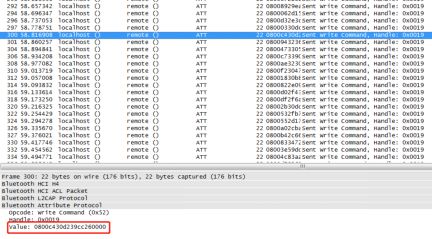
Figure 4-6 Low Energy Bluetooth Data Packet Between App and Bulb
4.2.6 Bluetooth Safes
Some safes also feature Bluetooth functionality, and the VT20i safe is a popular product on Amazon that uses a mobile app to unlock the safe via Bluetooth.

Figure 4-7 VT20i Safe
This safe has multiple vulnerabilities. According to the official website and promotional materials from the manufacturer, the Bluetooth communication between the app and the safe is encrypted. However, in reality, the manufacturer did not use encryption, allowing attackers to eavesdrop on the communication data between the safe and the application to obtain the unlocking password.
Additionally, the app does not employ any hardening measures. Through analysis of the decompiled source code, attackers can access the logic for unlocking the app. Attackers can remotely unlock this safe by sending specially constructed Bluetooth commands.
4.3 Analysis of Bluetooth Vulnerability Attack Cases
The Android Bluetooth Remote Code Execution Vulnerability (CVE-2017-0781) is a heap overflow vulnerability in the Bluetooth BNEP protocol. BNEP (Bluetooth Network Encapsulation Protocol) encapsulates data packets from different networks and transmits them via the Bluetooth L2CAP protocol.
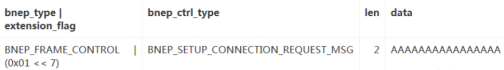
Figure 4-8 Bluetooth Stack Overview
In existing Android systems, Bluetooth uses the BlueDroid architecture. In BlueDroid, the BNEP service processes received data packets as follows:
(1) Parse BNEP_TYPE to obtain the extension bit;
(2) Check the connection status; if already connected, it can process non-BNEP_FRAME_CONTROL packets. If not connected, it only processes BNEP_FRAME_CONTROL packets;
(3) Call the handling function corresponding to BNEP_TYPE;
(4) For BNEP_TYPE that is not BNEP_FRAME_CONTROL and has an extension bit, the extension data must also be processed;
(5) Call the PAN layer callback function.
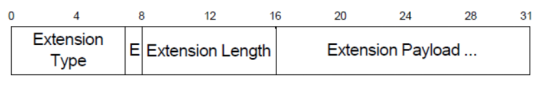
Figure 4-9 BNEP Control Message Format
Figure 4-10 BNEP Extension Header Format
Before the BNEP connection is truly established, a valid BNEP_FRAME_CONTROL data packet must be processed first. This vulnerability occurs during the processing of BNEP_FRAME_CONTROL before the connection is established, resulting in a heap overflow.
By sending a BNEP_TYPE of BNEP_FRAME_CONTROL, with an extension field of 1 and CTRL_TYPE of BNEP_SETUP_CONNECTION_REQUEST_MSG, an erroneous BNEP packet can trigger the vulnerability.
Figure 4-11 BNEP Heap Overflow Data Packet
When the user has Bluetooth enabled and has not patched the system, hackers can exploit this vulnerability to attack the phone. Once successful, hackers can gain the same system permissions as the Bluetooth process, allowing them to execute arbitrary code on Android phones using a reverse shell.
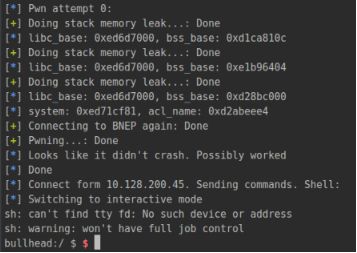
Figure 4-12 Attacking the Nexus 5X Phone and Reversing the Shell