Executive SummaryIn recent years, an increasing number of protocols capable of causing UDP reflection attacks have come to the forefront, such as CoAP[1], Ubiquiti[2], WS-Discovery[3], OpenVPN[4], and a certain DVR protocol[5]. These attack methods differ from the well-known reflection attack types like DNS, SSDP, NTP, and Memcached, posing certain challenges for DDoS attack protection. In June of this year, Israeli cybersecurity company JSOF disclosed several 0-day vulnerabilities in the Treck TCP/IP stack, potentially affecting hundreds of millions of devices worldwide. After analyzing the published white papers, we found that one of the affected manufacturers, Digi, uses ADDP (Advanced Digi Discovery Protocol) for device discovery. The multicast address used by ADDP is 224.0.5.128, port 2362, but the protocol also supports unicast in its implementation, combined with the ability of UDP to spoof source IPs, thus posing a risk of being used for reflection attacks. To understand the potential scale of ADDP reflection attacks, we conducted a survey of ADDP services exposed on the internet through the Green Alliance Threat Intelligence Center (NTI). Over 5,000 IPs globally have opened ADDP services, which are at risk of being exploited for DDoS attacks. These devices involve multiple products from Digi, such as Connect WAN 3G, ConnectPort WAN VPN, ConnectPort X4, Connect ME4 9210, etc. The five countries with the highest number of devices exposing ADDP services are the United States, Italy, Poland, Chile, and Spain, with the United States accounting for 43% of the total. The length of ADDP discovery messages is 14 bytes, while the response messages are mostly over 100 bytes, with an average length of 126 bytes, resulting in an average bandwidth amplification factor of 9. As a new type of reflection attack, ADDP has not yet attracted the attention of attackers, but its potential risks are mainly twofold: it can be used for DDoS attacks and can be used to discover devices from the Digi manufacturer, which may later be used for Ripple20-related attacks.
1. Introduction to ADDP
Ripple20[7] is a series of zero-day vulnerabilities discovered by JSOF[8] in the widely used low-level TCP/IP software library developed by Treck Inc. In June 2020, JSOF published a technical white paper on CVE-2020-11896 and CVE-2020-11898 in Ripple20[9], where CVE-2020-11896 includes a PoC for the Digi Connect ME 9210. After the publication of the technical white paper, we analyzed the affected Digi Connect ME 9210 and found that, in addition to the RCE described in the white paper, the ADDP protocol used by Digi’s Ethernet module also poses a risk of being used for reflection attacks.Digi International Inc.[10] (hereinafter referred to as Digi) is an IoT solutions provider established in 1985, with a product line ranging from RF modems to gateways. Digi Connect ME is a series of Ethernet modules designed by Digi, pre-installed with Digi’s plug-and-play firmware. To achieve plug-and-play functionality, Digi designed the ADDP (Advanced Digi Discovery Protocol), similar to SSDP (Simple Service Discovery Protocol), which is based on UDP for discovering Digi ConnectPort X series products within a local area network. Such discovery protocols typically support both multicast and unicast, and due to the ability of UDP to spoof source IPs, services exposed on the internet are extremely susceptible to being used for reflection attacks. ADDP uses the multicast address 224.0.5.128, port 2362, and the ADDP data frame[11] can be divided into four parts: protocol header, packet type, total length of payload, and payload. A typical ADDP device discovery packet is shown below:
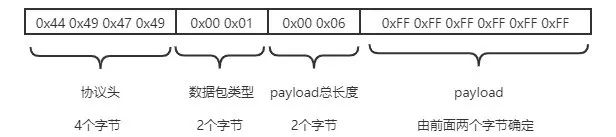
Figure 1.1 Example of ADDP Discovery Packet
The protocol header is the header of this protocol, and ADDP uses fixed characters as the protocol header. In the UDP scanning plugin of zmap[12], there are three types of protocol headers: DIGI (“0x44 0x49 0x47 0x49”), DVKT, and DGDP.
The packet type is used to distinguish the function of the packet and occupies two bytes:-0x0001: Device discovery request-0x0002: Device discovery response-0x0003: Static network design request-0x0004: Static network setting response-0x0005: Reboot request-0x0006: Reboot response-0x0007: DHCP network setting request-0x0008: DHCP network setting responseThe total length of the payload occupies two bytes.The payload is the effective load of the data frame, and typically, the payload length of ADDP device discovery packets is 6 bytes, fixed content being: “0xFF 0xFF 0xFF 0xFF 0xFF 0xFF”, as shown in Figure 1.1. Unlike the device discovery packet, the response to the device discovery packet has a payload format of field type + payload length + payload content, where the possible field types are as follows:-0x01: MAC address-0x02: IP address-0x03: Subnet mask-0x04: Network name-0x05: Domain name-0x06: Hardware type-0x07: Hardware version-0x08: Firmware-0x09: Result content-0x0a: Result flag-0x0b: IP gateway-0x0c: Setting error code-0x0d: Product model-0x0e: Real Port number-0x0f: DNS IP address-0x10: Unknown field-0x11: Error code-0x12: Number of serial ports-0x13: Encrypted Real Port number-0x1a: Device IDAn example of an ADDP protocol response message is shown below, and based on the above introduction, it is easy to understand the meaning of each field. For the IP and MAC address-related fields, we have anonymized the data.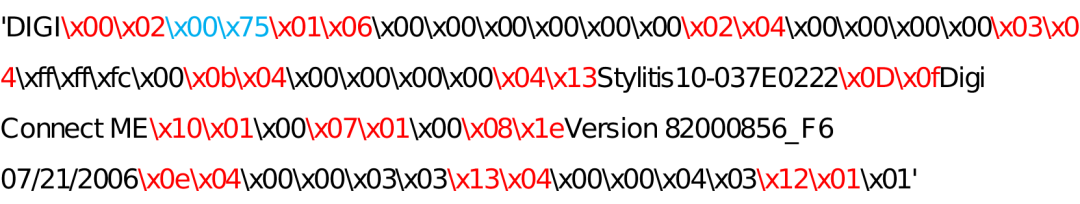
2. Analysis of ADDP Exposure
To accurately characterize the potential scale of ADDP reflection attacks, we conducted a survey of ADDP services exposed on the internet through the Green Alliance Threat Intelligence Center (NTI). Unless otherwise specified, the data mentioned in this chapter is based on global single-round survey data (June 2020).Over 5,000 IPs globally have opened ADDP services, which are at risk of being exploited for DDoS attacks.
To avoid omissions, we used three types of device discovery messages in zmap for the survey, resulting in the global exposure situation of ADDP services, as shown in Table 2.1. When the protocol header is “DGDP”, no live devices were detected.
Table 2.1 Global Exposure of ADDP Services
| Device Discovery Message Protocol Header | zmap Plugin Name | Number of Services Exposed |
| DIGI | digi1_2362.pkt | 4868 |
| DVKT | digi2_2362.pkt | 896 |
| DGDP | digi3_2362.pkt | 0 |
We analyzed the product model field in the banner of ADDP services, as shown in Figure 2.1. Interested readers can search the official website for specific products corresponding to the devices; we will not elaborate further here.
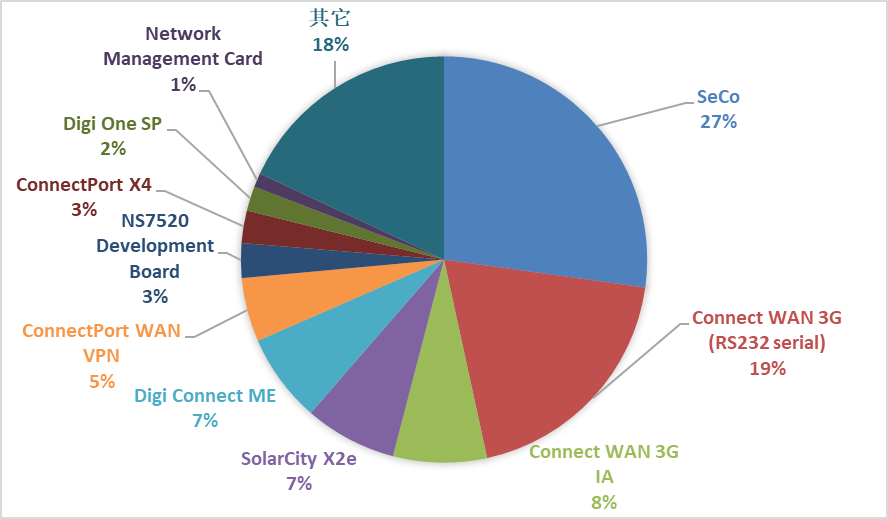
Figure 2.1 Distribution of Product Models with Open ADDP Services
The five countries with the highest number of devices exposing ADDP services are the United States, Italy, Poland, Chile, and Spain, with the United States accounting for 43%, while only 39 devices are exposed in our country.
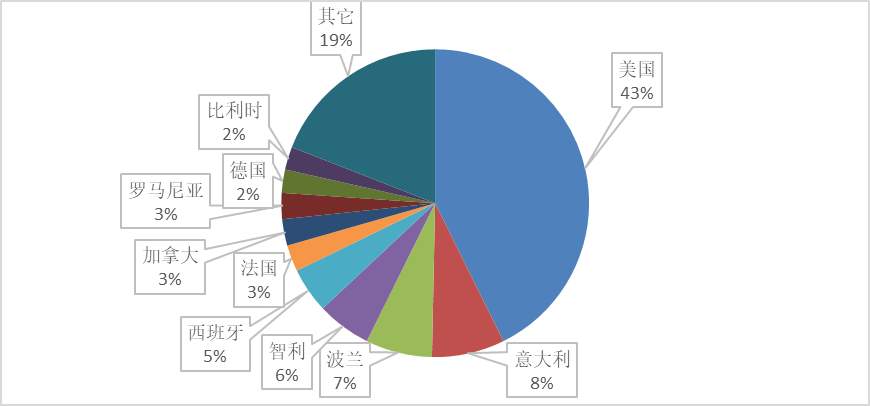
Figure 2.2 Distribution of Countries with Open ADDP Services
We analyzed the length of response messages, which are mostly over 100 bytes, with an average length of 126 bytes. Thus, the average bandwidth amplification factor (BAF)[6] is 9.
3. Conclusion
This article first introduced ADDP and then analyzed its exposure situation on the internet. As a new type of reflection attack, ADDP has not yet attracted the attention of attackers, but its potential risks are mainly twofold: it can be used for DDoS attacks and can be used to discover devices from the Digi manufacturer, which may later be used for Ripple20-related attacks.Protection Recommendations:As a security vendor:(1) ADDP scanning capabilities can be added to scanning products to timely discover security vulnerabilities in customer networks.(2) Traffic detection capabilities for ADDP can be added to protection products to timely identify security threats in customer networks. Threat intelligence related to IPs with open ADDP services can also be associated to block connections from the identified source IPs.As a device developer, when responding to ADDP service discovery messages, check whether the source IP of the message is a multicast address; if it is not a multicast address, do not respond. This will significantly increase the difficulty of using ADDP services to launch reflection attacks.As a telecom operator, BCP38 network ingress filtering should be followed.As a regulatory body:(1) Monitor ADDP threats in the network and report issues found.(2) Promote security assessments of ADDP functionality in devices; if devices do not meet relevant requirements, prohibit them from being marketed.As a device user:(1) If not needed, disable the ADDP discovery function of the device.(2) Try to deploy devices with open ADDP services within a local area network to increase the difficulty of exploitation.(3) If it is necessary to deploy devices with open ADDP services on the public internet, deploy a router (using NAT capabilities) or protective security devices (such as firewalls) in front of the devices to control external IP access to the devices.As a user with DDoS protection needs, purchase DDoS protection products from security vendors that have ADDP reflection attack protection capabilities. If already purchased and the product supports custom application layer features, corresponding feature rules can be added.
References
[1] CoAP Attacks In The Wild, https://www.netscout.com/blog/asert/coap-attacks-wild
[2] Over 485,000 Ubiquiti devices vulnerable to new attack, https://www.zdnet.com/article/over-485000-ubiquiti-devices-vulnerable-to-new-attack/
[3] IoT Devices Based on ONVIF Protocol Participating in DDoS Reflection Attacks,
https://anquan.baidu.com/article/623
[4] OpenVPN Services Used for UDP Reflection Amplification DDoS Attacks
https://www.freebuf.com/vuls/215171.html
[5] New Type of DVR UDP Reflection Attack Method Discovered in the Live Network
https://mp.weixin.qq.com/s/mCF3HiDDK1QdjvgOBGlaDA
[6] Amplification Hell: Revisiting Network Protocols for DDoS Abuse, https://www.ndss-symposium.org/ndss2014/programme/amplification-hell-revisiting-network-protocols-ddos-abuse/
[7] Ripple20, https://www.jsof-tech.com/ripple20/
[8] JSOF, https://www.jsof-tech.com/
[9] JSOF_Ripple20_Technical_Whitepaper_June20, https://www.jsof-tech.com/wp-content/uploads/2020/06/JSOF_Ripple20_Technical_Whitepaper_June20.pdf
[10] Digi International Inc., https://www.digi.com/about-digi
[11] addp, https://github.com/zdavkeos/addp/blob/master/addp.py
[12] digi pkt, https://github.com/zmap/zmap/blob/master/examples/udp-probes/digi1_2362.pkt
Original Source: Green Alliance Technology Research Communication
