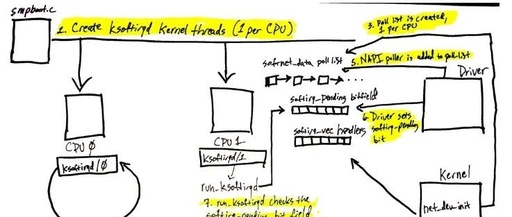
Summary of Shell Programming Knowledge, Including Common Linux Command Usage Tips
The following article is a summary of common knowledge in Shell programming, covering syntax and techniques. 1. Basic Concepts of Shell 1. Introduction The Shell is a command-line interpreter, an interface for users to interact with the kernel, receiving user-input commands and invoking system functions for execution. The Shell is loaded into memory when logging … Read more