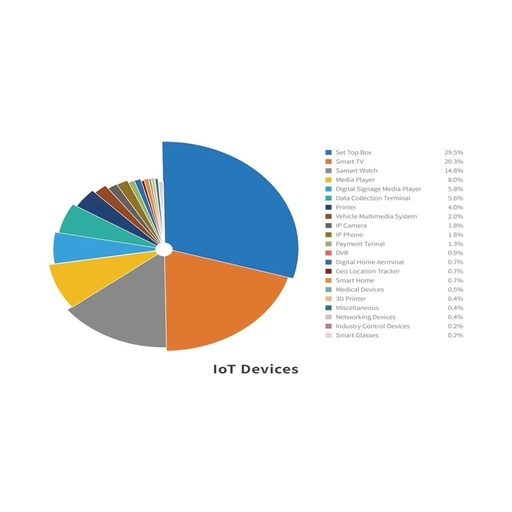
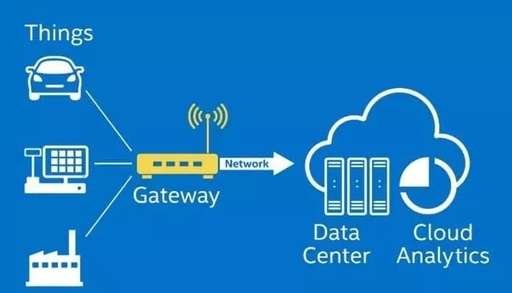
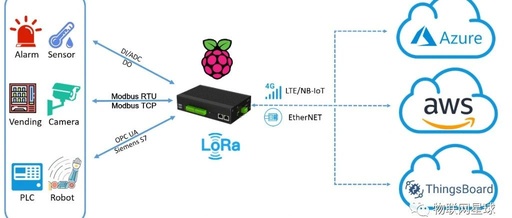
IoT Devices: Vulnerabilities and Security Risks
Recently, two American internet service providers suffered a network attack, causing many well-known websites to be inaccessible, claiming that half of America’s internet was paralyzed. Subsequent investigations revealed that hackers exploited viruses to infect IoT devices, which were then used to launch network attacks. Internet security experts stated that the number of infected IoT devices … Read more