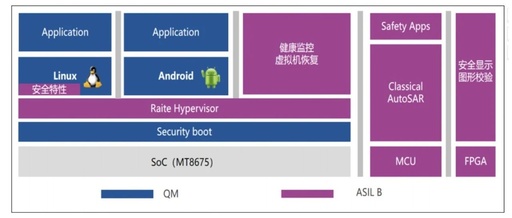
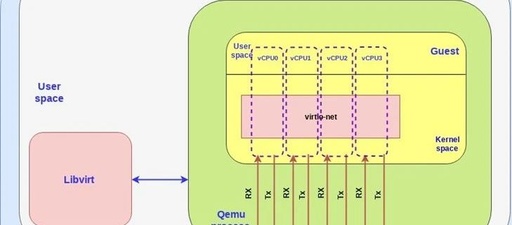
Empowering Intelligence Accelerates the Flourishing Development of Industrial IoT
The Industrial Internet of Things (IIoT), as a product of the deep integration of information and communication technology, intelligent science and technology, and industry, is a key support for the deep integration of the real economy and the digital economy, and for implementing a new round of industrial revolution. “For most countries, leveraging the IIoT … Read more