In the context of the deep integration of the new generation of information technology and manufacturing technology, driven by the demand for industrial digitalization, networking, and intelligent transformation, the Industrial Internet, characterized by ubiquitous connectivity, comprehensive perception, intelligent optimization, and secure stability, has emerged. As a new industrial ecosystem, critical infrastructure, and new application model, the Industrial Internet realizes comprehensive connectivity of all elements and the entire value chain through the full interconnection of people, machines, and things, continuously disrupting traditional manufacturing models, production organization methods, and industrial forms globally, promoting the accelerated transformation and upgrading of traditional industries and the rapid development of emerging industries.
The Industrial Internet Identifier Resolution System, as an important network infrastructure of the Industrial Internet, is the key hub for data circulation and information exchange in industrial enterprises, supporting the interconnectivity of the Industrial Internet. With the rapid development of the Industrial Internet, the demand for talent in identifier resolution technology among related enterprises in the field is increasing.
Identifier Resolution System
Identifier Resolution System is one of the core infrastructures for the safe operation of the global Industrial Internet; through “unified coding” and “public resolution,” it assigns a unique “identity card” to physical resources such as machines and products, as well as virtual resources like algorithms and processes, enabling rapid location and information retrieval, achieving cross-enterprise, cross-industry, and cross-regional integration and sharing of information resources; it helps realize information intercommunication and sharing across all elements and links in the industrial sector, becoming a key hub for cross-regional, cross-industry, and cross-enterprise information intercommunication.
In the era of Industry 4.0, data exchange between different enterprises and different information systems is required, and identifier resolution will meet this more diverse data flow demand.
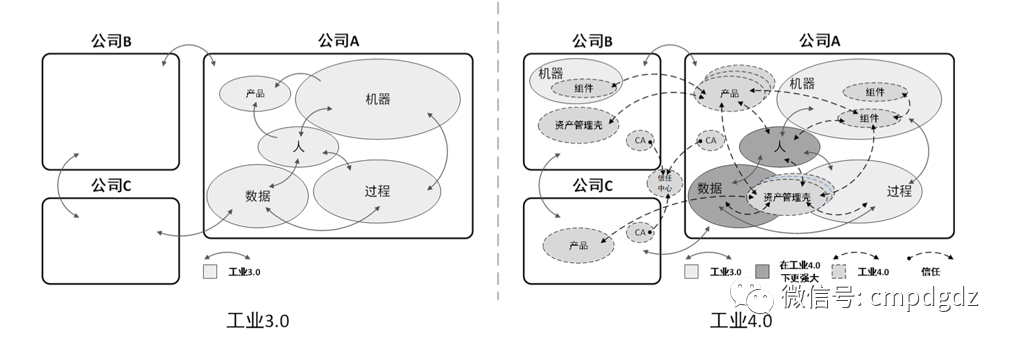
Information flow sharing of identifier resolution
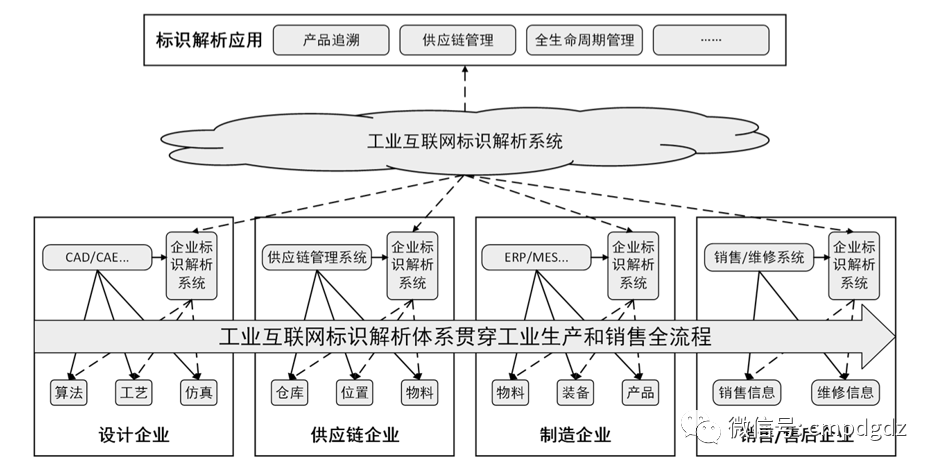
Identifier resolution becomes the key hub for information intercommunication
Four major company cases strengthen the understanding of industrial internet identifier resolution, in the future, the identifier industry ecosystem will accelerate construction.
Trusted Data Collection
Analysis of Trusted Data Collection Needs
Industrial data collection serves as a bridge from the physical world to the digital world, forming the basis for smart manufacturing and the Industrial Internet. The basic functional framework for industrial data collection is shown in Figure 1-1. Its basic functions include device access, protocol conversion, edge data processing, and central cloud.
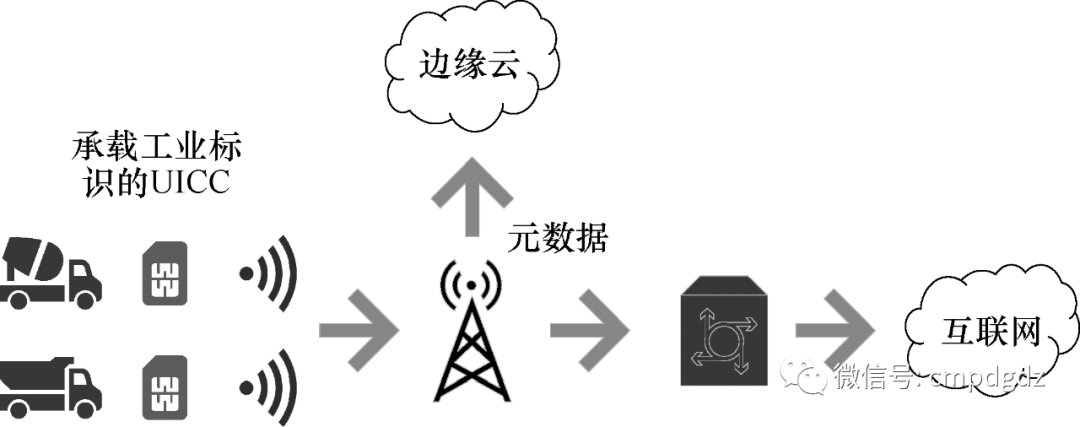
Figure 1-1 Basic functional framework of industrial data collection
-
Device access refers to connecting various industrial field devices and intelligent products through various wired and wireless communication technologies such as industrial Ethernet, industrial buses, and cellular networks (2G, 3G, 4G, NB-IOT, and 5G).
-
Protocol conversion refers to achieving unified data formats through middleware that is compatible with different industrial protocols.
-
Edge data processing involves analyzing, processing, and storing data close to the device side or data source to reduce data response latency and network congestion. The most common form of edge computing processing employs edge cloud, which is located between the base station and the core network, providing powerful cloud computing services locally to users.
-
According to application needs, the central cloud receives data from the end side and edge cloud, providing a wider range of services to users.
Application Scenarios of Trusted Data Collection
Currently, data collection scenarios in the Industrial Internet field are divided into two categories:
-
Numerical control airports/special intelligent devices, which communicate with industrial data collection systems via industrial buses, Ethernet, etc., typically using wired transmission. This method is costly and inflexible, but highly secure. -
Material identification reading devices, where material identity identification mainly uses one-dimensional barcodes/QR codes, NFC, RFID, which are low-cost methods suitable for identifying low-value individual items; trusted data collection solutions primarily apply to the first scenario.
-
Typical Case: China Unicom’s Trusted Data Collection Solution
Traditionally, the industrial data collection model includes industrial terminals and industrial platforms, as well as the networks connecting them. As shown in Figure 1-2.

Figure 1-2 Traditional industrial data collection model
In this model, data collection and interoperability between industrial terminals and platforms primarily rely on username + password for access control and permission management. The advantage of this model is its simplicity, ease of technical implementation, and low cost. However, its disadvantage is that when the number of industrial terminals is large, managing usernames and passwords becomes increasingly difficult. To facilitate practical operations, deployment personnel often use the same username and password for bulk terminals, leading to security issues and turning terminals into “zombies,” creating significant security risks for the Industrial Internet.
To address the security risks in industrial data collection, it is necessary to establish a trusted data collection system based on UICC, enabling industrial products to be connected and authenticated through multiple participants such as communication service providers, network operators, module manufacturers, and industrial enterprises, ensuring data security for industrial enterprises.
A trusted industrial data collection model based on UICC is shown in Figure 1-3.
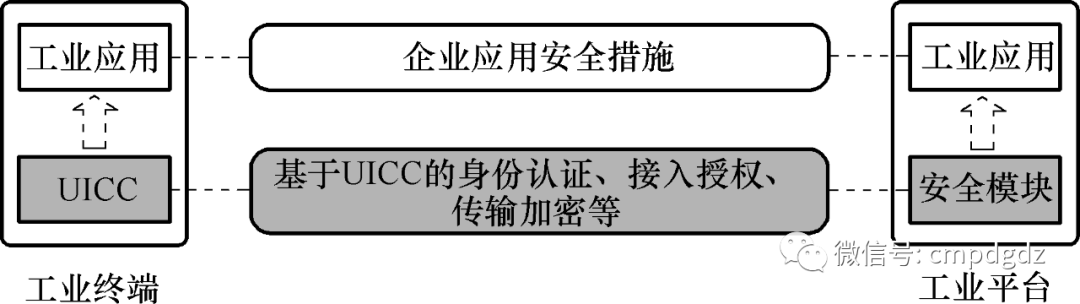
Figure 1-3 Trusted industrial data collection model based on UICC
In Figure 1-3, the UICC on the industrial terminal side stores the industrial Internet identifier and its related certificate passwords. The ICC securely protects the industrial Internet identifier and its related certificate passwords. The UICC and its business systems empower the application layer’s enterprise-related applications with capabilities for network layer terminal identity recognition, access authorization, and transmission encryption.
The industrial platform can accept or reject data writing from terminals based on the UICC’s terminal identity recognition results. To realize the model shown in Figure 1-3, it is necessary to add an industrial identifier UICC verification platform between the industrial terminals and platforms, along with building a corresponding UICC platform as shown in Figure 1-4.
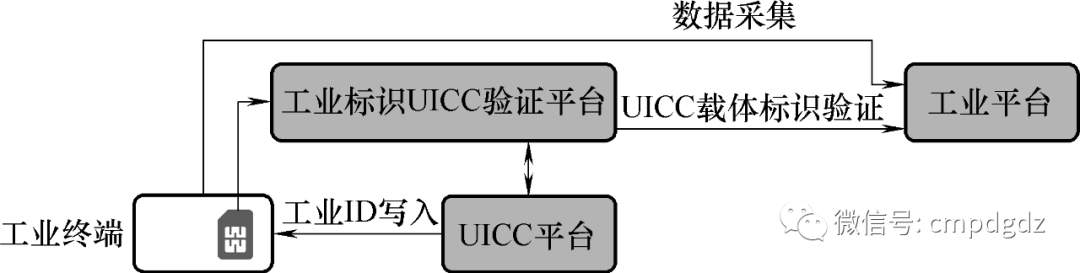
Figure 1-4 UICC empowers trusted data collection in industry
In Figure 1-4, the industrial identifier UICC verification platform verifies the UICC information in industrial terminals (i.e., carrier identifiers, including industrial identifiers, corresponding certificates, etc.), validating the legality of the UICC and, in turn, the legality of the terminal bound to the UICC.
The UICC platform is responsible for writing industrial IDs (i.e., Internet identifiers, certificates, keys, Applet data, etc.) into the UICC, and it also needs to interface with the industrial identifier UICC verification platform and other management platforms (e.g., industrial Internet identifier management platform).
In the trusted industrial data collection model based on UICC, the UICC can act as a security anchor, and the security solutions of enterprise applications can be built on top of the UICC. The security of enterprise applications can also be independent of the UICC, allowing for flexible deployment as needed.
The various modules shown in Figure 1-4 are described as follows:
-
Industrial terminals must embed UICC. The UICC is responsible for storing industrial identifiers, certificates, keys, Applet data, etc., and has the capability to remotely configure and activate the UICC through the UICC platform and write industrial identifiers via wireless over-the-air interfaces. -
The UICC platform can be transformed from the operator’s SIM card platform and must support the writing of industrial identifiers to industrial terminals, supporting profile downloads, status management, information queries, and other functions. -
The UICC verification platform, independent of the existing operator’s eSIM CA system, is specifically designed to serve industrial Internet application scenarios. As eUICC serves as the carrier for industrial identifiers, it can carry industrial Internet identifier authentication card applications and data.
In Figure 1-4, the industrial platform is an abstract concept referring to the platform responsible for collecting data from industrial terminals; the actual data collection capabilities may be integrated into different platforms. Filling the industrial Internet identifier into UICC involves complex business processes and multiple stakeholders, as shown in Figure 1-5, requiring collaborative efforts from various parties.
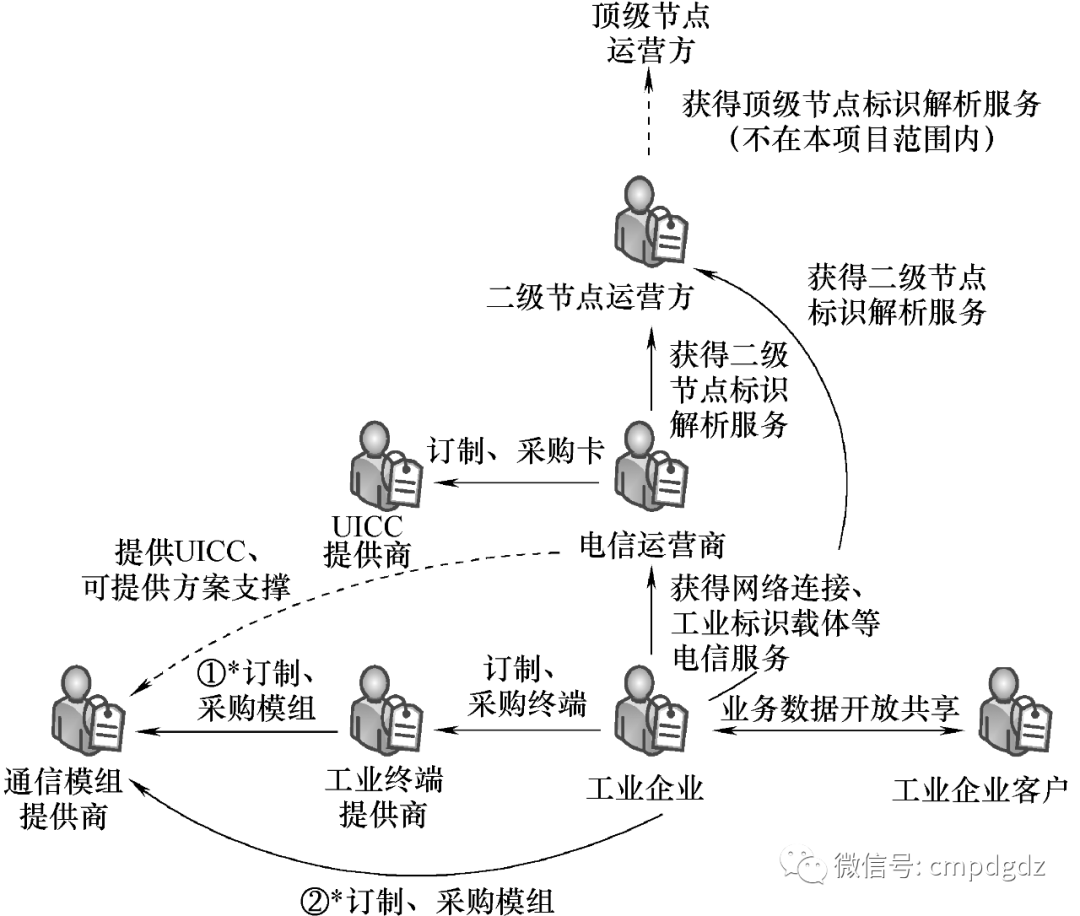
Figure 1-5 Some stakeholders in industrial data collection
Data Fusion
Analysis of Data Fusion Needs
One of the core functions of the Industrial Internet is the discovery of the value of industrial data, which is achieved through comprehensive perception, real-time exchange, and rapid processing of data at various stages of industrial products such as production, sales, and maintenance, enabling intelligent control. However, due to historical reasons, the “information silo” problem is prevalent within and between enterprises, resulting in a large amount of data not being collected or being collected but not utilized effectively, severely restricting the transformation of traditional industrial enterprises towards intelligent manufacturing based on industrial interconnectivity.
For data fusion aimed at the Industrial Internet, there are three specific implementation plans:
1) By adopting the same identifier, achieve unified data expression within enterprises and industries. Enterprises and industries adopt the same identifier resolution system to achieve intercommunication of identifier data within their fields.
2) Achieve data intercommunication between different industries and different identifier systems through cloud platforms. Different identifier data is aggregated on cloud platforms. After identifier resolution, conversions between identifiers are completed based on demand to realize data intercommunication based on identifiers.
3) Industrial data fusion based on artificial intelligence. Relevant data information is aggregated according to the physical entities and applications corresponding to various identifiers, employing artificial intelligence, machine learning, and other technologies for in-depth mining of industrial data.
This article mainly introduces the plan for achieving data fusion within the industry using the same identifier.
Application Scenarios of Data Fusion
In practical applications, data association and fusion between enterprises can generate new value. Industrial Internet identifiers can serve as media for data association between different enterprises, achieving data fusion among enterprises.
-
Typical Case: China Unicom’s Multi-dimensional Data Fusion Solution
For example, merging industrial enterprise data with operator data, the IoT card serves as the carrier for industrial Internet identifiers, enabling the fusion of industrial enterprise data with operator data. Below are specific examples.
1) The IoT card carrying industrial identifiers can associate operator information, IoT card numbers, and the URL for storing related data, as shown in Figure 1-6.
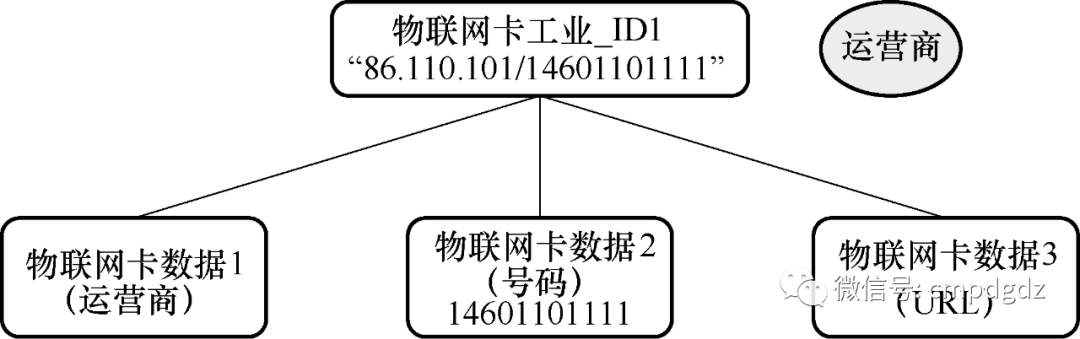
Figure 1-6 Data of IoT card carrying industrial Internet identifiers
2) The industrial identifier of the industrial Internet device can associate vendor information, IoT card number information within the device, data address URLs, etc., as shown in Figure 1-7.
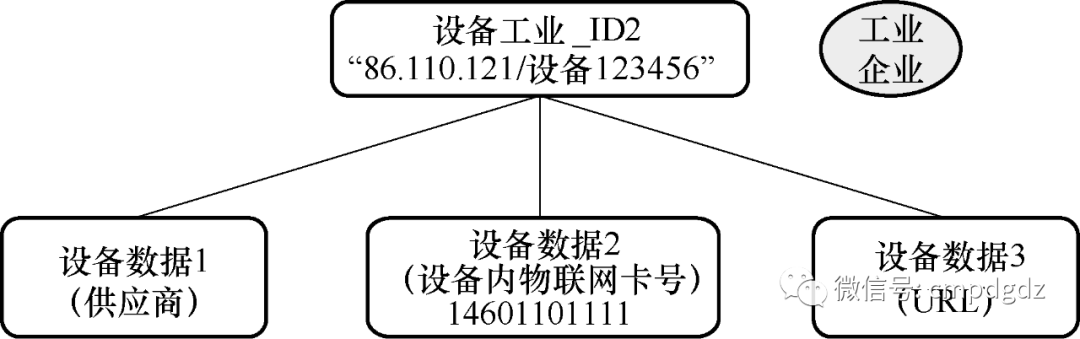
Figure 1-7 Equipment-related data associated with industrial Internet identifiers
Both the data of the IoT card carrying industrial Internet identifiers and the data associated with the industrial Internet identifiers can be resolved in the industrial Internet identifier resolution system using their industrial identifiers, allowing relevant enterprises to achieve the fusion of operator data and industrial enterprise equipment data under legitimate permissions, as shown in Figure 1-8.
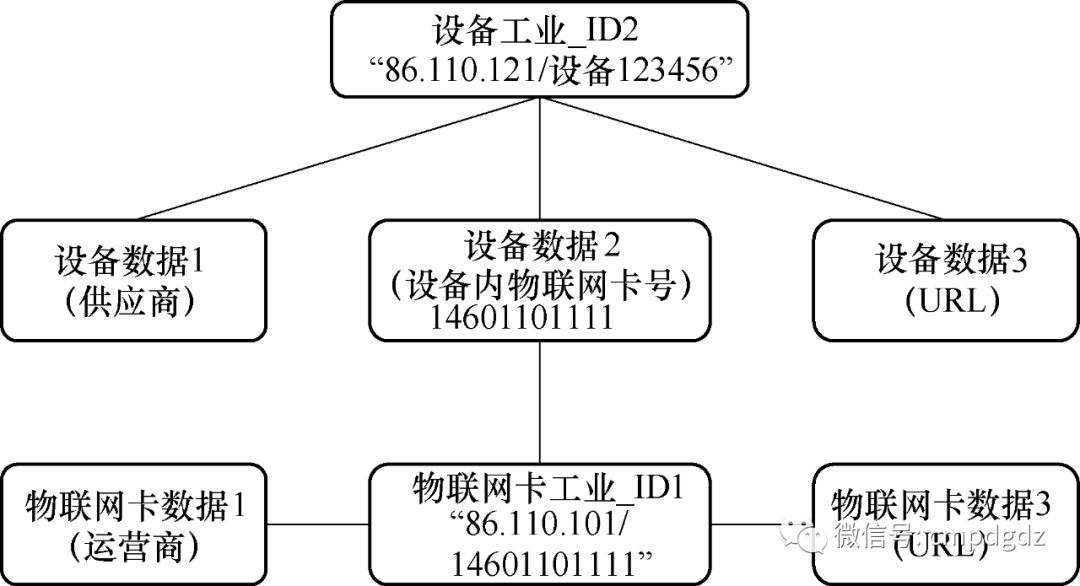
Figure 1-8 Fusion of operator data and industrial enterprise equipment data based on industrial identifiers
The supplier of “Device 123456” (an industrial enterprise) can query the industrial ID “86.110.121/Device 123456” through the service platform. In addition to obtaining the relevant open data of the device, “Device Data 1” and “Device Data 3,” it can also obtain more information about the IoT industrial ID “86.110.101/14601101111” through the IoT card number, thus completing the fusion of industrial data across industries.
3) eSIM applications involve data exchange and fusion across operators, where eUICC can carry industrial Internet identifiers and EID identifier information. Industrial identifiers can associate supplier information, IoT card number information within devices, data address URLs, etc., while EID identifiers can associate with the corresponding profiles (IMSI, MSISDN, ICCID) and corresponding card list service information. The cross-operator device data fusion achieved through industrial Internet identifiers of eSIM devices is shown in Figure 1-9.
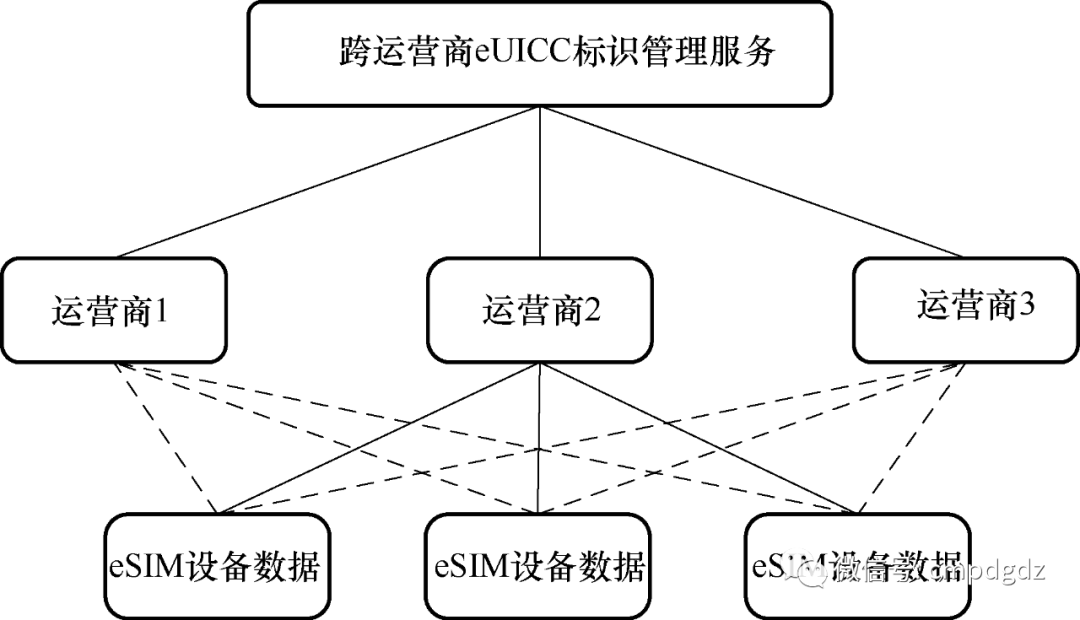
Figure 1-9 Cross-operator device data fusion achieved through industrial Internet identifiers of eSIM devices
Unified Identity Authentication
Analysis of Unified Identity Authentication Needs
The network world has gone through three stages: the internet, mobile internet, and industrial internet, but the method of password input has not changed. In today’s transition from mobile internet to industrial internet, password input faces significant security challenges. In the era of interconnectivity, the industrial internet permeates many aspects of life, with the development of smart cities already taking shape. Different scenarios, such as door locks, public transportation, and hospital consultations, require different identity authentication entities, meaning that each facility needs to carry a “key.” As the implementation of the industrial internet deepens, people may need to carry hundreds of “keys” daily. This situation arises because the identity authentication protocols for different facilities do not have a unified national standard. In the future, if technology could achieve unified identity authentication between different industrial internet facilities, allowing all smart devices to be authenticated with a single “key,” it would greatly facilitate people’s production and daily life.
Application Scenarios of Unified Identity Authentication
In a future world surrounded by smart devices, unified identity authentication solutions can meet users’ authentication needs across different life scenarios, with applications spanning manufacturing, education, transportation, healthcare, community, public services, and more.
In daily life, entering different buildings requires different identity recognition devices, which brings certain inconveniences to people’s lives and community management. By combining biometric recognition and connected devices, a unified identity authentication solution can address identity cross-trust issues, assisting property management in more conveniently, efficiently, and accurately managing entrants.
In the transportation sector, different communities and parking lots use different vehicle identity information (cards, license plates, public ETC tags, etc.) to recognize vehicles, causing significant difficulties in management and usage. Based on a unified identity authentication solution, a nationwide unified electronic vehicle identifier (such as RFID) can be adopted to scientifically and efficiently manage vehicles.
-
Typical Case: Tencent’s Tencent User Security Infrastructure (TUSI) Solution
Identity authentication is an essential aspect of industrial internet applications. The usual approach is for each application to independently manage its issued identity certificates and perform identity authentication separately. Since identities and their authentication methods cannot interconnect, this approach creates certain barriers to data openness and sharing.
The basic idea of internet unified identity authentication is to allow different application entities to use different CA centers to issue identifiers and their certificates within a unified technical framework, and to use blockchain to verify the issued identifiers and their certificates.
This solution balances flexibility and reliability, providing a unified identity authentication enabling for data sharing. Tencent’s Tencent User Security Infrastructure (TUSI) is an example of internet unified identity authentication.
The unified identity authentication framework of Tencent’s TUSI solution is shown in Figure 1-10.
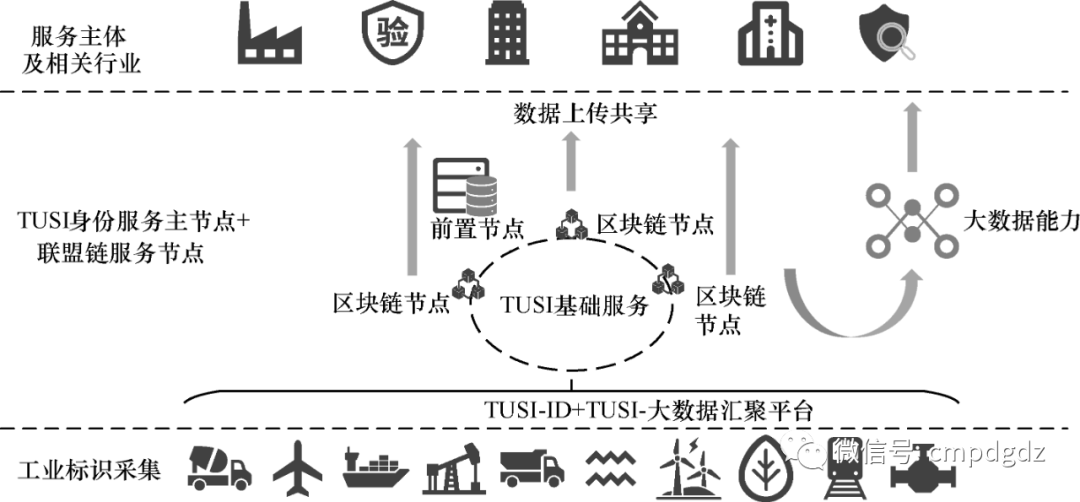
Figure 1-10 Unified identity authentication framework of Tencent’s TUSI solution
-
IoT nodes and devices equipped with TUSI-issued trusted TUSI-IDs can trace and authenticate device identities, collecting multi-dimensional data through existing IoT entry points to the TUSI front end.
-
Using the TUSI identity blockchain system, data is encrypted and stored on the blockchain, with various industries and related management departments having TUSI front-end nodes for decryption and data upload/synchronization.
-
Through the TUSI big data aggregation platform, multi-dimensional information can be filtered, aggregated, classified, cleaned, modeled, and outputted as interfaces and capabilities for third-party use.
-
Relevant management departments can access identity data and sensitive data of corresponding objects and devices in real-time, such as device status, information, historical records, operation permissions, lifecycle, etc.
The TUSI trusted identity blockchain leverages the characteristics of blockchain to achieve privacy protection, trust transmission, identity indexing, and cross-authentication security features.
Unified identity authentication involves four types of stakeholders, as shown in Figure 1-11.
-
CA centers issue identifiers and their certificate keys.
-
Industrial internet manufacturers authenticate the industrial internet devices connected through the blockchain identity verification platform.
-
The blockchain identity verification platform encrypts and stores the identifiers and certificates issued by CA centers, providing identity verification services for industrial internet manufacturers.
-
Industrial internet devices, as carriers of identifiers, load the security modules certified by CA centers.
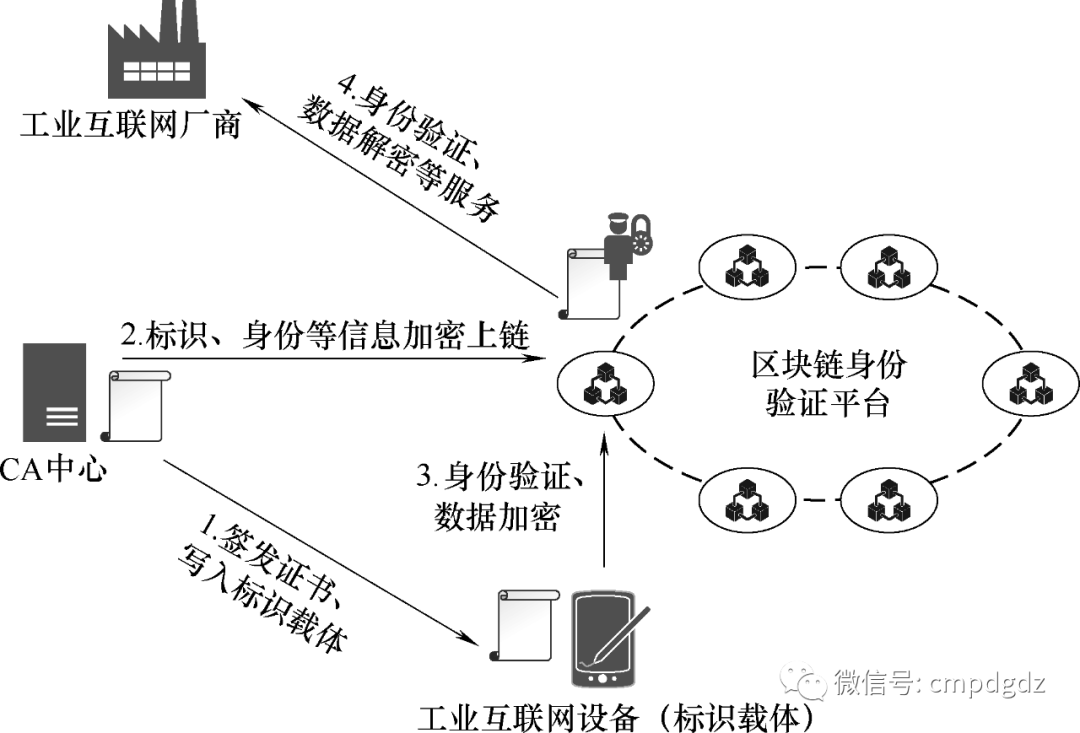
Figure 1-11 Basic process of internet unified identity authentication
Due to the need for networking and computational capabilities, the identity carriers for internet unified identity authentication adopt UICC, modules, or MCU chips.
The TUSI identity blockchain completes the secure closed loop from IoT devices to the cloud, with advantages including that the TUSI identity blockchain is a consortium blockchain, making it more efficient and controllable compared to public chains; the TUSI identity blockchain forms a secure closed loop from the device side to the cloud based on the TUSI protocol; the TUSI identity blockchain is flexibly deployable, capable of being encapsulated in hardware carriers or serving as cloud services; the TUSI identity blockchain places a high emphasis on user privacy, retaining only desensitized identity indexes; and the TUSI identity blockchain provides cross-authentication services for the same user across different scenarios.
Access Security Authentication
Analysis of Access Security Authentication Needs
In today’s era, information communication technology is developing rapidly. The Internet of Things, as a typical representative of information communication technology, is experiencing rapid development globally. IoT applications involve numerous fields including city management, smart homes, logistics management, intelligent manufacturing, retail, healthcare, and security, pushing the world into a new era of interconnectivity, where hundreds of billions of new devices such as wearable devices and smart homes will connect to the network.
The scale of IoT terminal devices is continuously increasing, and the accompanying threats are also growing, such as software vulnerabilities, insecure communications, data leaks, and malware infections. IoT devices have become the main carriers of botnets and can form ultra-high-capacity DDoS attack sources. The scale, frequency, complexity, impact, and losses of IoT DDoS attacks are rapidly increasing.
While terminal intelligence brings convenience, it also exposes more security issues, threatening users’ privacy, property, and even life safety. Security issues have become a significant factor hindering the development of the IoT and the improvement of user acceptance.
At the same time, security solutions targeting IoT terminals are rapidly developing worldwide. These security solutions include hardware security solutions (e.g., secure chips), software solutions (e.g., software sandboxes), and combined hardware-software solutions (e.g., trusted execution environments), some of which have emerged from security demands in finance, mobile communications, etc. When adapting to IoT terminals and scaling up, there are challenges in matching security costs with application scenarios. The lack of measurement indicators for security solutions from terminal manufacturers and poor consumer perception and differentiation create significant challenges when deploying security solutions to IoT devices.
The Link ID² (Internet Device ID) authentication solution for IoT devices is launched by Alibaba Cloud, providing end-to-end trusted access capabilities for IoT systems through trusted computing and cryptographic technologies.
ID² is a trusted identity identifier for IoT devices, possessing unalterable, unforgeable, and globally unique security attributes, serving as a key infrastructure for achieving interconnectivity and service flow. ID² supports multiple security level carriers, reasonably balancing the various demands of IoT in terms of security, cost, and power consumption, providing customers with affordable, easy-to-use, and guaranteed security solutions that adapt to the fragmented market needs of the IoT.
Application Scenarios of Access Security Authentication
Link ID² has covered nearly 30 application scenarios, including smart locks, security products, wearable devices, gateways, three meters, and unmanned vending machines. As of now, Alibaba Cloud IoT security products have provided security services for over 40 million devices, with more than 60 carriers integrated into the ID² hardware ecosystem and over 100 ecological partners.
-
Typical Case: Alibaba Cloud’s Link ID² Solution
Alibaba Cloud’s Link ID² solution provides two services: an ID distribution center and an ID authentication center, as shown in Figure 1-12.
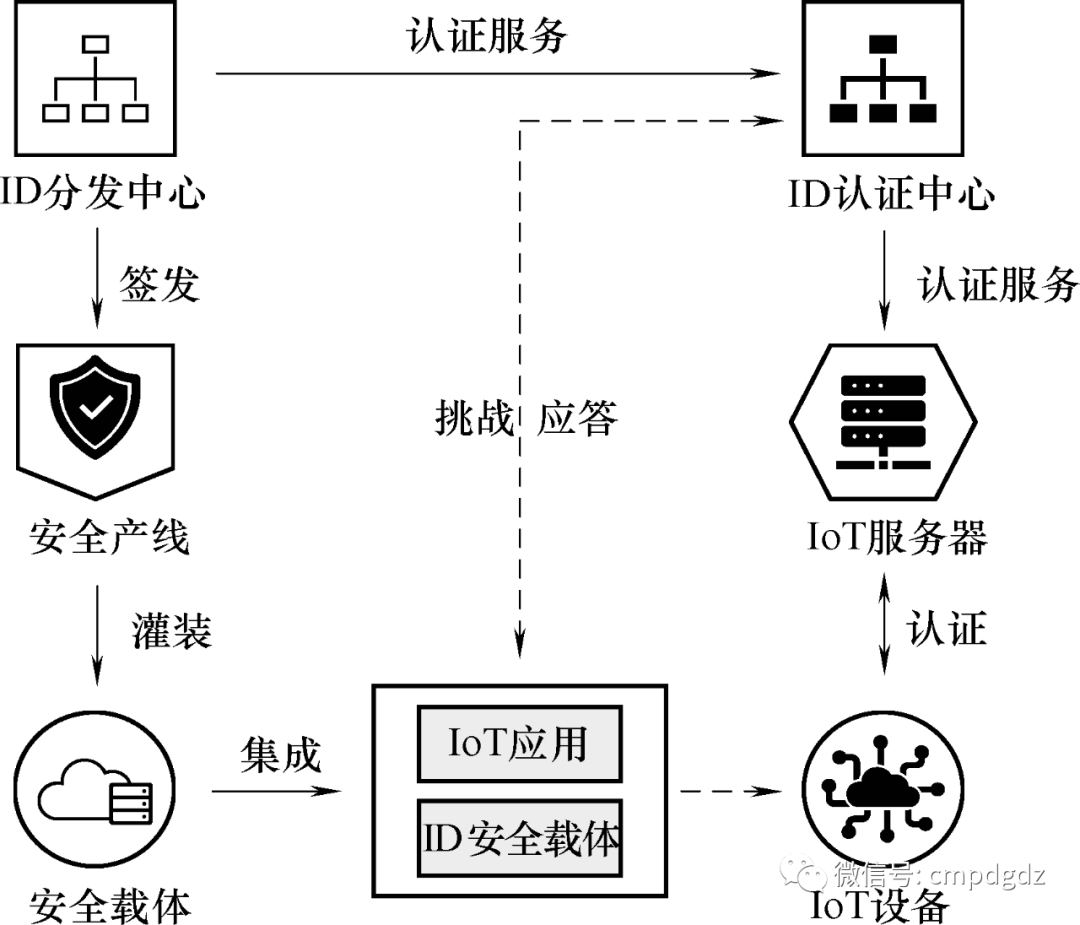
Figure 1-12 ID² principle diagram
The distribution center adopts hardware encryption machines and secure storage technologies to ensure the security of key generation and storage in the cloud, interfacing with partners’ secure production lines to ensure secure burning of keys onto various security level carriers.
Customers integrate secure carriers (e.g., SE, SIM cards, Secure MCU, TEE, and software sandboxes) into IoT devices (i.e., terminals) and, based on the SDKs on the device side and cloud, call the device authentication, information encryption, and other interfaces provided by the ID² authentication center to establish secure channels, ensuring the non-repudiation, integrity, and confidentiality of business data.
The core functions are as follows:
-
Device identity authentication provides each IoT device with a unique identity identifier, offering two-way identity authentication services based on ID² to prevent device tampering or counterfeiting.
-
Secure connection provides a lightweight security protocol compatible with TLS and DTLS—iTLS/iDTLS, which is more suitable for IoT devices, significantly reducing resource consumption while ensuring security.
-
Business data protection, based on keys derived from the device’s trusted root, supports various encryption algorithms to provide security protection for sensitive data such as device firmware, business data, and application authorization.
-
Key management: provides centralized management for keys used by devices, applications, and businesses in the IoT system, including key generation, destruction, and end-to-end secure distribution.
The core features are as follows:
-
Lightweight, using ID² instead of CA certificates, saving storage space and reducing network resource consumption; the connection handshake phase can save 70% of network resource consumption.
-
High security provides a trusted root from the cloud for IoT devices, ensuring the legitimacy of IoT devices and the security of data from the source.
-
Wide coverage, applicable to various security level IoT application scenarios, supporting carriers of different security levels (SE, SIM cards, TEE, Secure MCU, software sandboxes).
Accelerating Development of Identifier Application Promotion
Secondary Node Layout
Secondary nodes are important facilities that meet industry needs, expand identifier resolution service capabilities, service range, and service depth, serving as a crucial foundation and support for constructing a secure, stable, efficient, and upgradable industrial internet identifier resolution system. Depending on the service range, secondary nodes can be divided into industry-specific secondary nodes and comprehensive secondary nodes; multiple industry-specific secondary nodes can be established within the same industry. Currently, nodes have covered 30 industries, including shipping, containers, petrochemicals, food, and medical devices, providing identifier services directly to industry enterprises, initially forming an identifier application system, continually advancing applications to deeper levels, broader ranges, and larger scales.
Industry Application Models
Node enterprises are conducting forward-looking explorations of identifier applications, resulting in a batch of replicable typical application cases. Based on existing application achievements, five typical identifier application models have been distilled: intelligent production management and control, networked production collaboration, full lifecycle management, digital product delivery, and automated equipment management. Jiangsu Zhongtian has achieved not only the information correlation of product lifecycles by assigning industrial internet identifiers to prefabricated rods, optical cables, optical fibers, and production equipment, but also the integration of product data with equipment operation data, aiding intelligent production management and increasing production efficiency by over 15%. Inspur and Kingdee have connected industrial software data exchange devices with the identifier resolution system, achieving automated data registration, heterogeneous identifier transformation, flexible setting of data management permissions, and on-demand querying, enabling networked production collaboration between upstream and downstream enterprises. The statistics of identifier resolution application industries are shown in Figure 1-13.
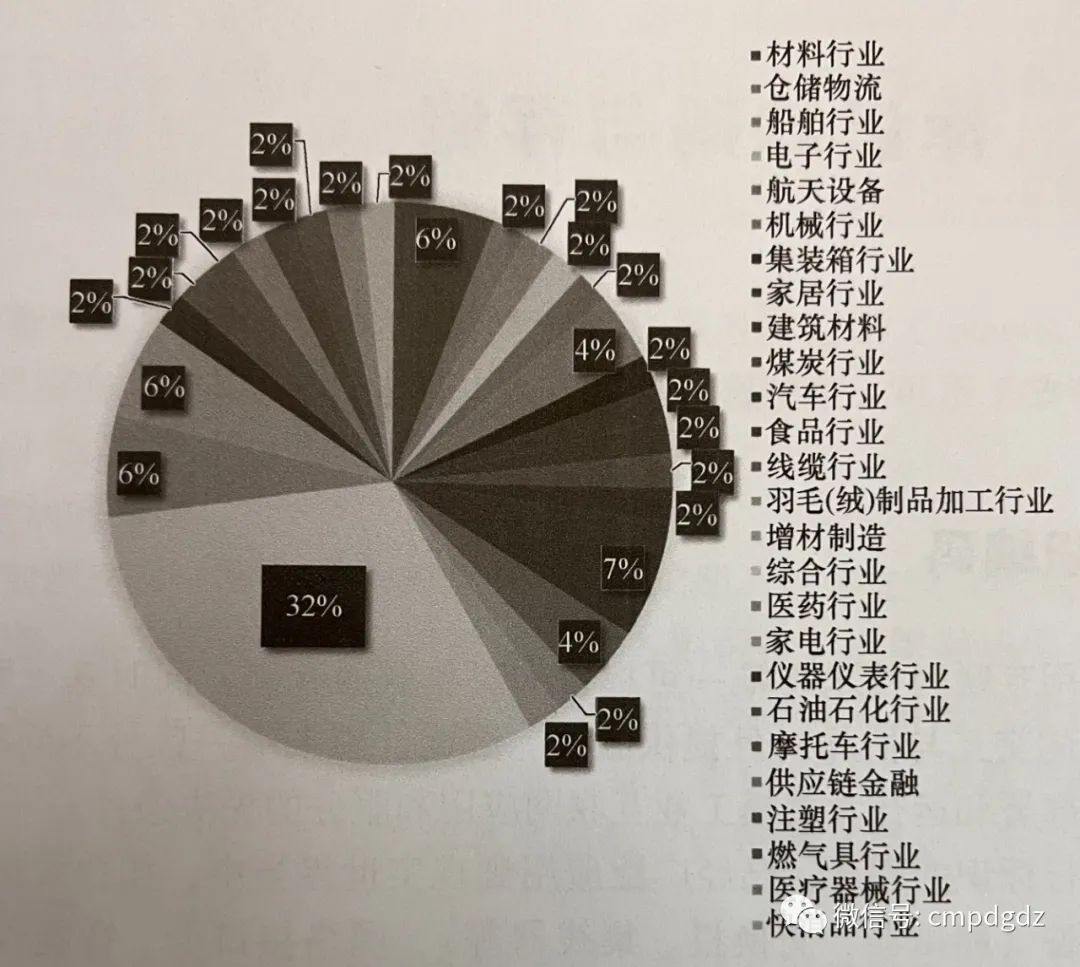
Figure 1-13 Statistics of identifier resolution applications by industry
Public Service Capabilities
Connecting various “end” service entry points, including public clients, IoT device ends, payment terminals, and identifier reading and writing devices, further expands the application scenarios of identifiers, gradually forming public service capabilities and providing comprehensive application services to the general public. By connecting the national top-level node with Alipay, “Scan to Pay” has become a service entry point that simultaneously connects internet domain names and identifier resolution systems, creating a series of public service platforms and promoting the identifier resolution system’s coverage to a broader range.
Accelerating Construction of the Identifier Industry Ecosystem
Under the mechanism of government guidance and market leadership, the roles of identifier ecosystem participants are continuously enriching and expanding in scale. In the areas of identifier resolution technology standards, identifier software and hardware research and development, security protection, testing and verification, secondary node construction, public application support, international cooperation, and end-to-end ecosystem, a broad coalition of identifier resolution service agencies, system integrators, application enterprises, open-source organizations, and other stakeholders in industry, academia, and research has initially formed a pattern of open sharing and mutual benefit in the identifier industry.
Encouraging security vendors to enter the identifier security market, covering solution providers, certification service providers, national cryptography algorithm research institutions, encryption chip providers, etc., collaboratively constructing security guarantees for identifier resolution; pragmatically advancing international cooperation, participating in the formulation of international standards, and joining international coding organizations, further enhancing international influence; constructing a testing and verification system for identifier resolution, fully supporting the research and verification of identifier technologies, products, and systems; and the Ministry of Industry and Information Technology has led the formulation of the “Industrial Internet Identifier Management Measures” and its supporting systems, promoting the formation of a unified management and coordinated development system for identifier resolution, effectively gathering consensus from various parties and forming a joint force for advancement, guiding the construction and operation of nodes at all levels.