Linux | Red Hat Certified | IT Technology | Operations Engineer
👇 Join the tech exchange QQ group with 1000 members, note 【Public Account】 for faster access

1. User Types in Linux
Before we dive into Linux permission management, let’s first understand a key concept: user types in Linux.
In Linux, there are actually two types of users: the superuser and the regular user. The superuser is the default user type after we set up the environment, also known as the root user, while the regular user is created under the superuser. For convenience in learning and working, we may need multiple user identities, similar to multiple executable files in Visual Studio. Regular users have permission constraints compared to superusers, meaning that some files may not be accessible under a regular user, while a superuser can access them freely.
We can use the following command to check our current identity: whoami
Superuser:
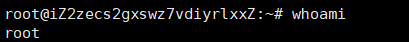
Regular user:
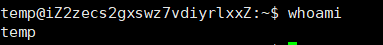
Here, temp is the username of the regular user, created by ourselves. A superuser can create multiple regular users. We will explain how to create regular users in detail in the next article.
2. Basic Concepts of Permissions
In Linux, the permissions for files and directories are controlled by the following three operations:
Read (r): View the contents of a file or list the contents of a directory. Write (w): Modify the content of a file or add/delete files in a directory. Execute (x): Execute a file (such as a script or program) or enter a directory.These permissions can be assigned to three types of users:
File Owner (User): The creator or owner of the file. User Group (Group): Users who belong to the same group as the file owner. Others: All other users who do not belong to the file owner or user group.3. Representation of Permissions
Now let’s address a question: what exactly are the permissions we’ve been discussing?
Here, permissions refer to the execution capabilities of different users on the files we create.
When we check the detailed information of the files we created:
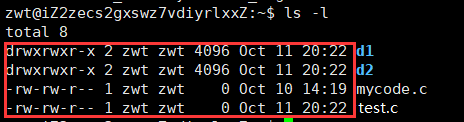
We can see that each file’s information consists of a similar string. What do these pieces of information mean?
As shown in the following image:
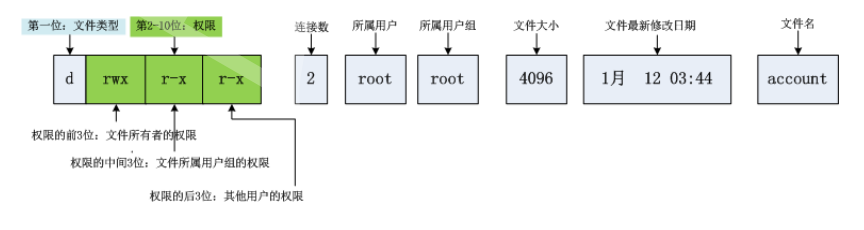
In Linux, file permissions are typically represented as strings, such as in the image above:
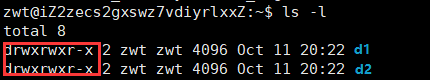
Here, the first character of the string indicates the file type:
- indicates a regular file d indicates a directory l indicates a symbolic link p: pipe file c: character device file (e.g., screen or serial device) s: socket file b: block device file (e.g., hard disk, CD-ROM)The following nine characters are divided into three groups, each representing the permissions for the owner, user group, and others:
First group (rwx): Permissions for the file owner Second group (r-x): Permissions for the user group Third group (r--): Permissions for othersThe meaning of each character is as follows:
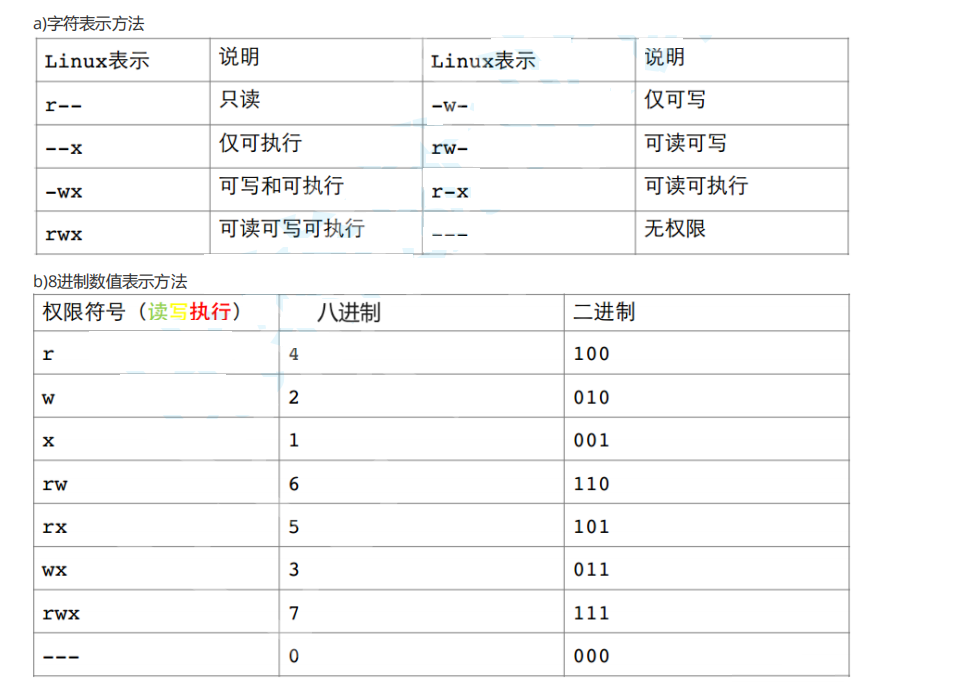
r: readable w: writable x: executable -: no permissionBecause permissions have a binary nature, we can represent them using binary 0/1 (readable, writable, executable as 1, no permission as 0). For example, the permissions for a file owner are:rwx, which is represented in binary as 111 and in octal as 7.
4. Methods for Setting File Access Permissions
1. chmod Command
Function: Set file access permissions
Note: Only the file owner and root user have the right to modify file permissions.
The chmod command permission value format has two forms:
① User Symbol +/-= Permission Character
+ : Adds the permission indicated by the permission code - : Removes the permission indicated by the permission code = : Assigns the permission indicated by the permission code User Symbols: u: owner g: group o: other users a: all usersExample:
# chmod u+w /home/abc.txt # chmod o-x /home/abc.txtAs shown:
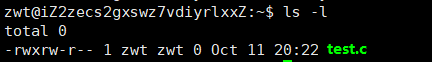
In this test.c file, the group permissions are rw-, with no execute permission, and the file owner is zwt. Therefore, we can operate under the identity of zwt or root to grant execute permission to the group.
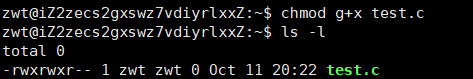
After the operation, we can see that the group has also been granted x execute permission.
② Three Octal Digits
In addition to the above representation using letters, we can also use octal numbers:
Example:
# chmod 664 /home/abc.txt # chmod 640 /home/abc.txt2. chown Command
Function: Change file owner Format: chown [options] username filename Note: Only the root user has the right to change the file owner Options: -R Recursively change file ownerExample:
# chown user1 f1 # chown -R user1 filegroup13. chgrp Command
Function: Change file group Format: chown [options] groupname filename Note: Only the root user has the right to change the file group Options: -R Recursively change file groupExample:
# chgrp users /abc/f24. umask Command
Function: View or modify file maskBefore explaining this command, we need to understand what a mask is.
When we create files in Linux:
As shown, we created a regular file and a directory file.
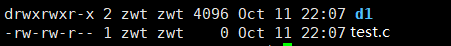
When we check their permissions, we can see that the directory file has permissions of 775 (octal representation), while the regular file has permissions of 664.
However, the default permissions differ from what we see. The default permissions for a directory file are 777, and for a regular file, they are 666. The reason we see the above is due to the existence of the mask.
We can check the mask using umask:
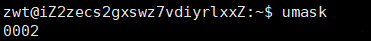
We can see that the mask is 0002, which when added to 775 and 664 corresponds exactly to the default permission values. This means that the files we actually obtain lack certain permissions compared to the default permissions, and these missing permissions are those defined in the umask.
Final Permissions = Default Permissions & (~umask)Therefore, we can change the umask value to modify the starting default permissions for the directories or files we create, achieving the desired result.
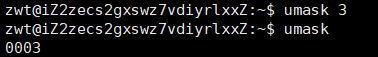
5. Directory Permissions
The permissions for directories differ from those discussed above for files.
The results of the three types of permissions for directory files are as follows:
Executable Permission: If a directory does not have executable permissions, you cannot cd into the directory. Readable Permission: If a directory does not have readable permissions, you cannot use commands like ls to view the contents of the directory. Writable Permission: If a directory does not have writable permissions, you cannot create or delete files in the directory.This means that when a user has write permissions on a directory file, they can delete files inside it, even if they may not have any permissions on those files.
However, this leads to a problem. When we use an open-source directory file from the internet in our work, and we are all members of that directory file’s group with write permissions, does that mean that if we create a file in that directory, others can delete it at will?
To solve this problem, we introduce the concept of the sticky bit.
Sticky Bit
When the sticky bit is set on a directory, only the file owner can delete or rename files within that directory. The flag is represented by t in the permissions for others.Example:
chmod +t dir # Set sticky bitPoints to Note:
1. The executable permission for a directory indicates whether you can execute commands in the directory. 2. If a directory does not have -x permission, you cannot execute any commands on it, not even cd into it, even if the directory still has -r read permission (this is a common mistake, thinking that having read permission allows you to enter the directory to read files). 3. If a directory has -x permission but no -r permission, the user can execute commands and cd into the directory. However, due to the lack of read permission for the directory, even if they can execute ls commands in the directory, they still do not have permission to read the documents within the directory.6. Special Permissions
In Linux, in addition to basic permissions, there are three types of special permissions, one of which is the sticky bit mentioned above.
As follows:
Set UID (SUID): When an executable file with SUID permission is run, the program runs with the permissions of the file owner. The flag is represented by s in the owner permissions. Set GID (SGID): Similar to SUID, but the program runs with the permissions of the user group. The flag is represented by s in the group permissions. Sticky Bit: When the sticky bit is set on a directory, only the file owner can delete or rename files within that directory. The flag is represented by t in the permissions for others.To set these special permissions, you can use the chmod command:
chmod u+s file.txt # Set SUID chmod g+s dir # Set SGID chmod +t dir # Set Sticky Bit7. Summary
Linux permission management is a key component in ensuring system security. Understanding the relationships between users, groups, and permissions, as well as how to view and modify permissions, is essential for managing and protecting Linux systems. By properly setting permissions, unauthorized access and data leaks can be effectively prevented.
For course inquiries, add: HCIE666CCIE
↑ Or scan the QR code above ↑
What technical points and content would you like to see?
You can leave a message below to let Xiao Meng know!