Although the 60 software has many advertisements, it is possible to turn off the ads in its settings with a little effort. I particularly appreciate the 60’s Crystal Protection Engine, which utilizes hardware virtualization and is said to have posed challenges for script kiddies. First, let’s talk about the location: 1. 60 Security Guard 2. Top right corner
2. Top right corner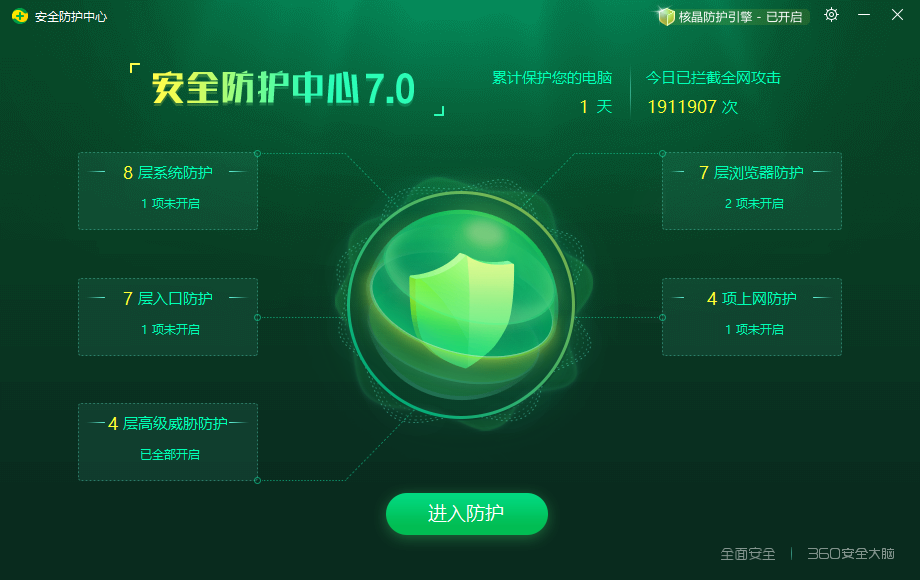 3. Official introduction: Intel-VT Crystal Protection Engine, an innovative international leading protection technology that enhances your computer’s security using the CPU’s hardware virtualization mechanism, specifically designed for 64-bit systems.
3. Official introduction: Intel-VT Crystal Protection Engine, an innovative international leading protection technology that enhances your computer’s security using the CPU’s hardware virtualization mechanism, specifically designed for 64-bit systems.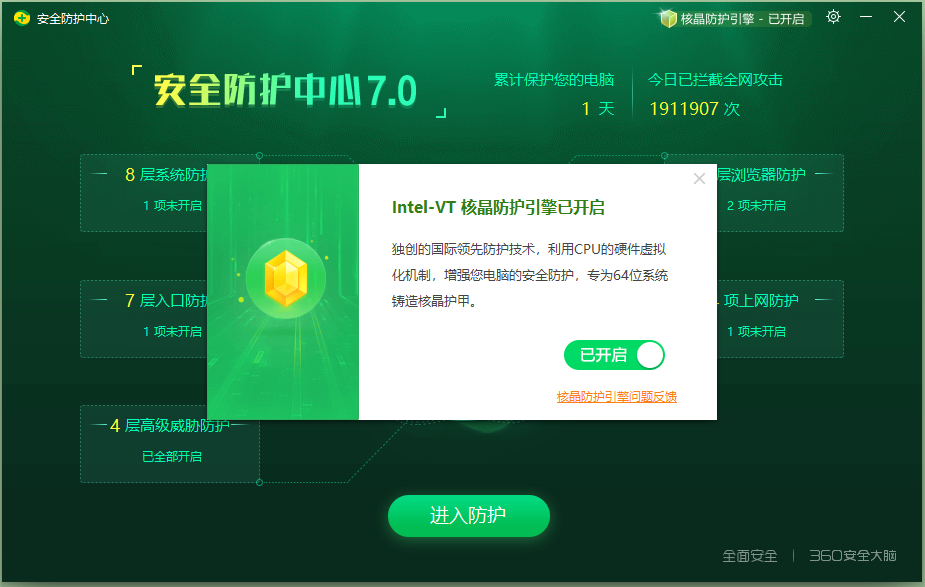 Excerpt from the official introduction: The Crystal Engine utilizes Intel/AMD CPU hardware virtualization technology (Vanderpool Technology, referred to as VT technology) to create a client protection engine. Currently, it is only used for active defense functions. It can be used for other client security functions in the future. I specifically visited the 60’s technical forum.
Excerpt from the official introduction: The Crystal Engine utilizes Intel/AMD CPU hardware virtualization technology (Vanderpool Technology, referred to as VT technology) to create a client protection engine. Currently, it is only used for active defense functions. It can be used for other client security functions in the future. I specifically visited the 60’s technical forum. By the way: This 60 forum looks like it is built on PHP? Discuz?bbs.360.cn/forum.php?mod=viewthread&tid=3011884
By the way: This 60 forum looks like it is built on PHP? Discuz?bbs.360.cn/forum.php?mod=viewthread&tid=3011884
The principle of the 60 Crystal Protection Engine is based on CPU hardware virtualization technology (Intel VT-x/AMD-V), which creates an independent high-privilege virtualization layer to isolate the operating system kernel from the security protection mechanism, achieving efficient and stable security protection.
1. Core Principle: Hardware Virtualization Isolation Technology
- Virtualization Layer Isolation: The Crystal Protection Engine utilizes CPU hardware virtualization technology (such as Intel VT-x or AMD-V) to create an independent virtualization layer (Hypervisor) beneath the operating system kernel. This virtualization layer runs at the highest privilege level (Ring -1), while the operating system kernel runs at a lower privilege level (Ring 0).
- Kernel-Level Protection: Through this isolation, the Crystal Engine can directly monitor and intercept illegal operations on the kernel without modifying the operating system kernel, effectively preventing kernel-level malware (such as Rootkits) attacks.
2. Key Technology: PatchGuard Compatibility and Bypass
- Bypassing PatchGuard Restrictions: The PatchGuard mechanism in Windows 64-bit systems prevents third-party software from modifying kernel code, making it difficult for traditional security software to achieve kernel-level protection. The Crystal Engine bypasses the PatchGuard restrictions through hardware virtualization technology, enabling real-time monitoring and protection of the kernel.
- Conflict-Free Design: The design of the Crystal Engine avoids direct conflicts with PatchGuard, thus preventing system blue screens or crashes, ensuring system stability and security.
3. Function Implementation: Real-Time Monitoring and Active Defense
- Kernel Behavior Monitoring: The Crystal Engine can monitor all operations within the kernel in real-time, including system calls, memory access, process creation, etc., promptly detecting and intercepting abnormal behavior.
- Active Defense Mechanism: Through the isolation of the virtualization layer, the Crystal Engine can intercept before malware attempts to modify the kernel, preventing it from executing malicious operations. This active defense mechanism significantly enhances system security.
4. Performance Optimization: Low Resource Usage
- Hardware Acceleration: The Crystal Engine utilizes the CPU’s hardware virtualization capabilities to separate protection tasks from the operating system kernel, reducing the kernel’s burden and minimizing the impact on system performance.
- Efficient Protection: Due to the isolation of the virtualization layer and hardware acceleration, the Crystal Engine can provide efficient security protection without significantly degrading system performance.
5. Application Scenarios: Kernel-Level Security Protection
- Preventing Rootkits: Rootkits are a type of malware that hides within the operating system kernel, making it difficult for traditional security software to detect and remove. The Crystal Engine can directly monitor and intercept Rootkit behavior through hardware virtualization technology, effectively preventing its attacks.
- Protecting System Integrity: The Crystal Engine can prevent malware from tampering with system files, injecting malicious code, or performing other operations that compromise system integrity, ensuring system stability and security.
6. Technical Advantages: Compatibility and Stability
- Compatibility: The Crystal Engine is compatible with mainstream operating systems (such as Windows) and does not affect the normal functionality of the system.
- Stability: Since the Crystal Engine runs in an independent virtualization layer, it does not conflict with the operating system kernel, thus providing high stability.
7. Relationship with Virtual Machines
- Coexistence with Virtual Machines: The Crystal Engine can coexist with virtual machines (such as VMware, VirtualBox), but it is necessary to ensure that the VT-x/AMD-V features of the virtual machines do not conflict with the virtualization layer of the Crystal Engine.
- Resource Allocation: In some cases, enabling the Crystal Engine may affect the performance of virtual machines, and users can adjust settings according to their needs.
Click to follow, your support is my motivation for continuous creation.