Author: Ananya Tungaturthi, Product Marketing Manager at Silicon Labs Any device connected to the internet may face attacks at some point. Attackers may attempt to remotely compromise IoT (Internet of Things) devices to steal data, conduct DDoS attacks (Distributed Denial of Service attacks), or try to disrupt the rest of the network. Securing IoT requires an integrated approach that ensures protection throughout the device lifecycle, from design and development to deployment and maintenance.The security of IoT devices is a major concern for customers and device manufacturers. To ensure secure communication between two devices, two critical areas need protection. The first is the channel between the two devices and the data transmitted within these channels, which are handled by communication protocols such as Thread and Bluetooth. The second is the security of the device itself, which is the responsibility of the developers.Currently, multiple organizations, standards, and frameworks aim to provide guidelines and best practices for IoT security, such as the IoT Security Foundation, NIST Cybersecurity Framework, ISO/IEC 27000 series standards, and the OWASP Top Ten IoT Security Vulnerabilities. However, no universal standard applies to all IoT devices, as different devices have different security requirements and challenges, depending on their application scenarios, functionalities, and environments.Therefore, IoT device manufacturers and developers need to adopt and implement the standards and frameworks that are most relevant and suitable for their specific devices while keeping up with emerging trends and technologies in the field of IoT security.The Most Common IoT Security ThreatsWhile the dangers posed by security threats in IoT devices may be low, the impacts in other areas can be significant and cause considerable damage. Let’s delve into the most common IoT security threats.Unauthorized AccessOne of the most common security threats is unauthorized access. Hackers can access IoT devices through weak passwords and other vulnerabilities, allowing them to control the device or steal personal information. This may include accessing the device’s camera or microphone or using the device to launch a DDoS attack.Data BreachesAnother common security threat for IoT devices is data breaches, which occur when attackers obtain sensitive or confidential data from a device or the network the device is on. This can compromise the privacy and integrity of the data and expose the device or user to threats such as identity theft, fraud, or extortion.Malware AttacksThe third common security threat for IoT devices is malware attacks, where malware executes unauthorized actions on the victim’s system, potentially compromising the device’s functionality and reliability, causing damage, disruption, or destruction to the device or its network.Distributed Denial of Service AttacksAnother threat to IoT device security is denial of service attacks, where DDoS attacks target the availability of network resources and servers, utilizing various IoT devices from different locations to launch attacks on communication media, making detection more challenging. Therefore, analyzing and defending against DDoS is an important research area.Physical TamperingThis is another threat that occurs when an attacker physically accesses, alters, or damages a device or its components. Such attacks can compromise the integrity, functionality, and confidentiality of IoT devices. This can affect the security and functionality of the device and allow attackers to access, manipulate, or destroy the device or its data.How Silicon Labs Addresses IoT Security ChallengesWhen it comes to security issues, people often mention data breaches, malware attacks, denial of service attacks, and so on. However, IoT devices are more susceptible to some other types of attacks. These may be simple attacks where attackers attempt to run unauthorized code on your device or execute product counterfeiting, or complex attacks such as differential power analysis attacks.Silicon Labs addresses these issues through its Secure Vault™ IoT security technology. Secure Vault is a suite of advanced security features designed to protect IoT devices from these evolving threats.Silicon Labs is a leading provider of chips, software, and solutions for IoT devices, focusing on delivering secure and reliable connectivity for a smarter, more connected world. Silicon Labs offers a comprehensive suite of powerful IoT security products and services, including secure boot, secure debugging, secure key management, and secure identity authentication.Let’s take a look at common security countermeasures (see below) that can help protect the keys and private keys of endpoint devices and ensure a fully secure ecosystem.
Any device connected to the internet may face attacks at some point. Attackers may attempt to remotely compromise IoT (Internet of Things) devices to steal data, conduct DDoS attacks (Distributed Denial of Service attacks), or try to disrupt the rest of the network. Securing IoT requires an integrated approach that ensures protection throughout the device lifecycle, from design and development to deployment and maintenance.The security of IoT devices is a major concern for customers and device manufacturers. To ensure secure communication between two devices, two critical areas need protection. The first is the channel between the two devices and the data transmitted within these channels, which are handled by communication protocols such as Thread and Bluetooth. The second is the security of the device itself, which is the responsibility of the developers.Currently, multiple organizations, standards, and frameworks aim to provide guidelines and best practices for IoT security, such as the IoT Security Foundation, NIST Cybersecurity Framework, ISO/IEC 27000 series standards, and the OWASP Top Ten IoT Security Vulnerabilities. However, no universal standard applies to all IoT devices, as different devices have different security requirements and challenges, depending on their application scenarios, functionalities, and environments.Therefore, IoT device manufacturers and developers need to adopt and implement the standards and frameworks that are most relevant and suitable for their specific devices while keeping up with emerging trends and technologies in the field of IoT security.The Most Common IoT Security ThreatsWhile the dangers posed by security threats in IoT devices may be low, the impacts in other areas can be significant and cause considerable damage. Let’s delve into the most common IoT security threats.Unauthorized AccessOne of the most common security threats is unauthorized access. Hackers can access IoT devices through weak passwords and other vulnerabilities, allowing them to control the device or steal personal information. This may include accessing the device’s camera or microphone or using the device to launch a DDoS attack.Data BreachesAnother common security threat for IoT devices is data breaches, which occur when attackers obtain sensitive or confidential data from a device or the network the device is on. This can compromise the privacy and integrity of the data and expose the device or user to threats such as identity theft, fraud, or extortion.Malware AttacksThe third common security threat for IoT devices is malware attacks, where malware executes unauthorized actions on the victim’s system, potentially compromising the device’s functionality and reliability, causing damage, disruption, or destruction to the device or its network.Distributed Denial of Service AttacksAnother threat to IoT device security is denial of service attacks, where DDoS attacks target the availability of network resources and servers, utilizing various IoT devices from different locations to launch attacks on communication media, making detection more challenging. Therefore, analyzing and defending against DDoS is an important research area.Physical TamperingThis is another threat that occurs when an attacker physically accesses, alters, or damages a device or its components. Such attacks can compromise the integrity, functionality, and confidentiality of IoT devices. This can affect the security and functionality of the device and allow attackers to access, manipulate, or destroy the device or its data.How Silicon Labs Addresses IoT Security ChallengesWhen it comes to security issues, people often mention data breaches, malware attacks, denial of service attacks, and so on. However, IoT devices are more susceptible to some other types of attacks. These may be simple attacks where attackers attempt to run unauthorized code on your device or execute product counterfeiting, or complex attacks such as differential power analysis attacks.Silicon Labs addresses these issues through its Secure Vault™ IoT security technology. Secure Vault is a suite of advanced security features designed to protect IoT devices from these evolving threats.Silicon Labs is a leading provider of chips, software, and solutions for IoT devices, focusing on delivering secure and reliable connectivity for a smarter, more connected world. Silicon Labs offers a comprehensive suite of powerful IoT security products and services, including secure boot, secure debugging, secure key management, and secure identity authentication.Let’s take a look at common security countermeasures (see below) that can help protect the keys and private keys of endpoint devices and ensure a fully secure ecosystem.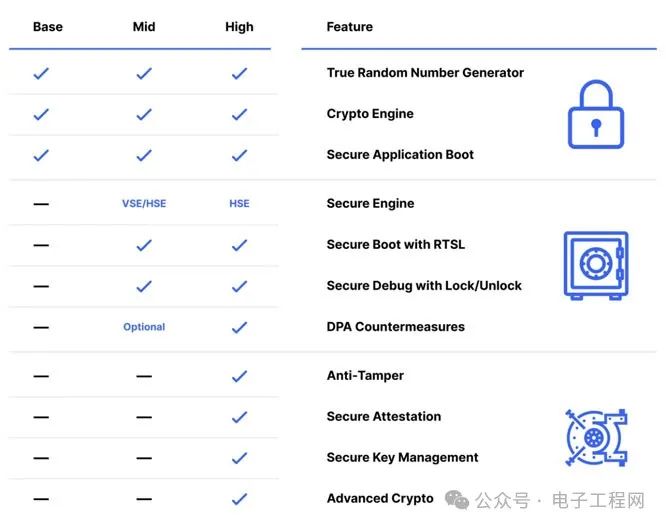 Secure Vault’s intermediate functions will protect endpoint devices from logical attack vectors. Some applications also need to guard against physical attack vectors, which require Secure Vault’s advanced features such as secure key management and tamper protection. Device manufacturers looking to protect their devices from product counterfeiting and device cloning should consider investing in secure identity authentication features, which support the validation of a device’s identity before allowing it to join the smart IoT network.Secure Key ManagementThere are various methods to securely store keys. One method is to create very expensive storage units that will be embedded in the secure subsystem. From the perspective of the silicon die area, these storage units are costly, always raising concerns for decision-makers: how many storage units do we want to put in the chip? Ultimately, the situation is that the storage units are still insufficient, and some key materials end up being stored in standard storage in unencrypted plaintext form. Another method for secure key storage is to use Physical Unclonable Functions (PUFs) to create device-specific Key Encryption Keys and store all key materials in the form of encrypted key binary large objects (BLOBs) in standard storage. The additional benefit of this approach is that it provides nearly unlimited secure key storage.Physical Unclonable Functions (PUFs)PUFs are physical structures embedded in integrated circuits (ICs) that are difficult to clone due to their unique micro or nano characteristics arising from inherent sub-micron manufacturing process variations. Static Random Access Memory (SRAM) PUFs are the most well-known PUFs based on available standard components.Other Attack VectorsThe threat of attackers trying to run their unauthorized code on our devices is always present, and secure boot functionality can address this issue by verifying the signatures on the code before allowing application code to run on the device. This function is based on a ROM-based root of trust, which is used as a secure anchor for the verification sequence. We can also prevent unauthorized access to devices by locking debug ports and enabling DPA countermeasures to prevent devices from being unlocked due to side-channel attacks.Security is a very interesting area in IoT devices because one can never ensure 100% protection for devices. Just as the more layers an onion has, the harder it is to peel, the more layers we create in devices, the more difficult and costly it becomes for attackers to access information. At Silicon Labs, we adhere to the principle of achieving security through design, meaning that security is embedded and integrated into every stage of the device lifecycle, from design and development to deployment and maintenance.
Secure Vault’s intermediate functions will protect endpoint devices from logical attack vectors. Some applications also need to guard against physical attack vectors, which require Secure Vault’s advanced features such as secure key management and tamper protection. Device manufacturers looking to protect their devices from product counterfeiting and device cloning should consider investing in secure identity authentication features, which support the validation of a device’s identity before allowing it to join the smart IoT network.Secure Key ManagementThere are various methods to securely store keys. One method is to create very expensive storage units that will be embedded in the secure subsystem. From the perspective of the silicon die area, these storage units are costly, always raising concerns for decision-makers: how many storage units do we want to put in the chip? Ultimately, the situation is that the storage units are still insufficient, and some key materials end up being stored in standard storage in unencrypted plaintext form. Another method for secure key storage is to use Physical Unclonable Functions (PUFs) to create device-specific Key Encryption Keys and store all key materials in the form of encrypted key binary large objects (BLOBs) in standard storage. The additional benefit of this approach is that it provides nearly unlimited secure key storage.Physical Unclonable Functions (PUFs)PUFs are physical structures embedded in integrated circuits (ICs) that are difficult to clone due to their unique micro or nano characteristics arising from inherent sub-micron manufacturing process variations. Static Random Access Memory (SRAM) PUFs are the most well-known PUFs based on available standard components.Other Attack VectorsThe threat of attackers trying to run their unauthorized code on our devices is always present, and secure boot functionality can address this issue by verifying the signatures on the code before allowing application code to run on the device. This function is based on a ROM-based root of trust, which is used as a secure anchor for the verification sequence. We can also prevent unauthorized access to devices by locking debug ports and enabling DPA countermeasures to prevent devices from being unlocked due to side-channel attacks.Security is a very interesting area in IoT devices because one can never ensure 100% protection for devices. Just as the more layers an onion has, the harder it is to peel, the more layers we create in devices, the more difficult and costly it becomes for attackers to access information. At Silicon Labs, we adhere to the principle of achieving security through design, meaning that security is embedded and integrated into every stage of the device lifecycle, from design and development to deployment and maintenance.
Follow 【Electronic Engineering Network】 for more electronic industry news



