
Authors: Xu Ning, Zhao Hui
Source: China Military Network
We do not comment on whether animals can be used for sports event predictions. However, from a scientific perspective, octopuses are indeed very intelligent creatures. They can perform activities that seem complex for other animals, such as unscrewing bottle caps and using tools. An octopus has 500 million neurons, one main brain, and eight secondary brains (located in its eight arms). The secondary brains handle simpler information, while more complex situations are sent to the main brain.
This information processing model of octopuses, which does not overload the main brain by delegating tasks to secondary brains, is akin to a certain internet technology. In academia and industry, it is referred to as: edge computing.

From Distributed Computing
On the night of the Qatar World Cup final, a short video live stream reached a historical peak of over 37 million simultaneous viewers. With Argentina’s victory, comments and likes in the live stream flooded the screen. But have you ever wondered how short video platforms maintain stable and smooth live broadcasts while supporting so many users in real-time interaction?
As early as 1995, Professor Tim Berners-Lee of MIT, the inventor of the World Wide Web, foresaw future internet traffic congestion issues. He proposed to his colleagues the invention of a way to better interact with internet content. Professor Layton found a solution from applied mathematics and algorithms. This led to the birth of Akamai, the world’s largest distributed computing service provider.
To solve congestion issues, Akamai deployed tens of thousands of servers worldwide. It “packages” internet resource data and caches it in servers across more than 100 countries and regions, providing fast services. When a user requests to download a video, the request is directed to the nearest server for download. This greatly reduces user access time. This is the concept of distributed data processing, which involves breaking down large resource data into smaller, more manageable parts and distributing them to edge nodes for caching, effectively reducing information latency and speeding up data transmission.
The concept of distributed data processing has caught the attention of network security personnel. They centralized data and applications in edge devices, proposing to preprocess data at the edge before quickly and securely transmitting the processed data to the cloud. This effectively blocks hacker intrusions. Since the edge possesses some functions of cloud data processing, this computing paradigm, which extends from cloud computing, is called fog computing.
The idea of processing data at the network edge has also sparked interest among internet service providers. In commercial operations, there has been a phenomenon where network expansion occurs without an increase in revenue. To avoid becoming mere “pipeline” providers, operations researchers have added computing, storage, and processing capabilities near wireless networks, integrating them into the network to provide IT and partial cloud computing services locally. This emphasizes application, service, and content localization, proximity, and distributed deployment, known as mobile edge computing.
Distributed caching, fog computing, and mobile edge computing all collect and analyze data close to the source and provide services nearby. Thus, the concept of edge computing was born. Edge computing is a new computing model that executes computations at the network edge. The objects of edge computing include downlink data from the cloud and uplink data from the Internet of Things, where the edge refers to any computational and network resources along the path from the data source to the cloud.
For example, for telecommunications companies, the edge is the cellular network base station closest to the customer; for Akamai, the edge consists of globally distributed content delivery devices; for military bases, the edge includes high-definition cameras covering the entire base, and so on. In summary, the edge refers to the computing infrastructure close to the data source, typically located in positions with latencies ranging from tens to hundreds of milliseconds.
Edge computing has transformed traditional data processing models. With the rapid development of the Internet of Things, massive data puts immense pressure on network transmission and cloud computing. To meet the demand for timely data processing, edge computing has been introduced, forming a collaborative computing model of “cloud + edge + end.” Using a familiar analogy from the healthcare system, the end = “patient,” edge = “community hospital,” and cloud = “top-tier hospital.” Patients first visit community hospitals for treatment; after addressing minor ailments, they can return home, while “complex cases” are transferred to top-tier hospitals for treatment. This improves service efficiency.
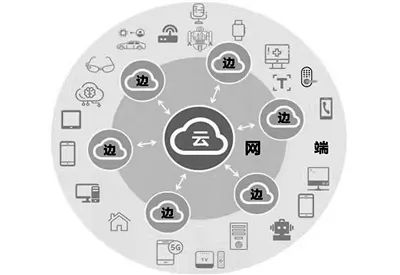
Conceptual diagram of edge computing. Source image
Growing Amid Massive Data
According to a research report by Machina Research, a global leader in IoT market research, the total number of connected devices worldwide is expected to exceed 27 billion by 2025. As of 2021, connected terminals generated data amounting to 847ZB (1ZB=270B, i.e., 100 trillion bytes) annually, with data being decentralized and fragmented. Over 50% of data needs to be analyzed, processed, and stored at the network edge. The massive data processing and network bandwidth limitations have fostered the growth of edge computing. So, what are the main characteristics of edge computing?
Edge computing bridges the “last mile” of network connectivity.From this perspective, edge computing is somewhat similar to the gateway (like a router) in a home network. However, the functionality of edge computing is broader; it considers how various network communication protocols can coexist and interconnect, as well as technical challenges related to network deployment, configuration, management, and maintenance, offering diverse connectivity features.
Edge computing enhances the ability to process time-sensitive information.Take surveillance as an example; the traditional processing method involves transmitting video data from cameras located at the network edge directly to cloud servers via the internet. The cloud stores, infers, and analyzes a large amount of video data before forwarding the analysis results to users. Due to limitations in remote data transmission speed, users cannot obtain real-time analysis results. The video processing model based on edge computing deploys the cloud’s video analysis program close to the cameras, significantly reducing network and system latency through proximity computing services, thus enhancing the real-time nature of video processing.
Edge computing can survive in harsh environments.Edge computing differs from the dense pre-coverage distribution model of communication base stations, as it is generally deployed for specific areas and scenarios. It occupies a small space and is suitable for relatively harsh working conditions and operating environments, providing protection against electromagnetic interference, dust, explosions, vibrations, and fluctuations in current/voltage, greatly enhancing deployment convenience.
Edge computing ensures privacy protection.Data at the network edge often involves personal privacy; uploading edge data to the cloud increases the risk of leakage. By storing user privacy data in edge devices without uploading it to the cloud, the possibility of cloud leakage is completely eliminated, ensuring better security for privacy data.
Building a Bridge Between Military and Intelligence
Edge computing, when integrated with emerging technologies such as artificial intelligence, big data, the Internet of Things, and 5G, fully demonstrates its role in the new modes of warfare, becoming a bridge to promote military intelligence.
The introduction of edge computing will make intelligence processing timelier.In modern warfare, a large number of unmanned equipment is used for intelligence reconnaissance, with their imaging or video recording devices transmitting captured images and videos to backend control centers through data links, shortwave, ultra-shortwave, and other wireless communication means for filtering, interpreting, analyzing, and annotating to extract valuable information. Currently, this processing model has certain “time lags” in meeting the real-time requirements of intelligence and timely reflecting battlefield situations. If devices that integrate edge computing and video surveillance technology are installed on unmanned equipment, utilizing edge computing to extract and analyze behavior features in images in real-time can effectively eliminate redundant information, significantly improving the accuracy and timeliness of intelligence reconnaissance.
Edge computing can enhance threat awareness on the battlefield.In the future, intelligent recommendation algorithms can be used to provide personalized battlefield information push, developing intelligent edge computing to form a cognitive toolbox for operational elements, units, and forces. This can help soldiers quickly interpret information from battlefield data, identify danger zones and potential threats, and swiftly deploy solutions, greatly enhancing awareness of threats on the battlefield.
Edge computing can support information support and assurance.In the rapidly changing battlefield, when frontline combat forces interact with rear command posts, communication is often prone to interference and interruption due to limited battlefield resources, insufficient connection bandwidth, and various intertwined communication methods. If military smartphones are equipped with software developed based on edge computing, combined with military radios to form an edge cloud, each mobile terminal can send data to other mobile devices through Wi-Fi, cellular communication, and RF means, achieving synchronization and updating of information across various edge terminals.
Edge computing can support human-machine collaboration.In future air combat, there may be scenarios where onboard radar alarms that an enemy is launching missiles at friendly forces; airborne warning aircraft inform that enemy aircraft are approaching from behind, preparing to attack; aircraft responsible for suppressing air-to-air and surface-to-air missiles are sending information to friendly forces at the same frequency or different frequencies; pilots may also hear the roar of air-to-air missiles and all the noise from radar warning equipment, etc. In such a complex environment with multiple sources of information, if edge computing devices with augmented reality and intelligent analysis functions are installed on the aircraft to perceive and analyze air combat situations in real-time, they can provide effective information to pilots in rapidly evolving tactical environments, supporting human-machine collaboration, helping pilots make accurate decisions quickly, and better “saving themselves and eliminating enemies” in air combat.
Edge computing can assist in battlefield map generation.Whether combat troops can quickly generate accurate maps of operational target areas is one of the key factors for the success of military operations. In the future, advanced computer vision, artificial intelligence, mapping software, and edge computing can be integrated into a handheld platform that controls drone swarms for real-time and continuous 360° monitoring of target areas, using video data collected by drones to perform calculations on-site and generate realistic 3D maps in real-time. Since it does not require network connections or additional processing capabilities, real-world maps can be created globally, providing decision support for combat troops entering the battlefield.

Follow our public account for more information
Membership application, please reply “individual member” or “unit member” in the public account
Welcome to follow the media matrix of the China Command and Control Society

CICC Official Website

CICC Official WeChat Account

Journal of Command and Control Official Website

International Unmanned Systems Conference Official Website

China Command and Control Conference Official Website

National Military Simulation Competition

National Aerial Intelligent Game Competition

Sohu Account

Yidian Account