


Think Tank Highlights #GlobalDefenseDynamics #USMilitaryDynamics #RussianMilitaryDynamics #TaiwanUpdates #MicroStoreAvailable
#SouthKorea #Raytheon #Japan #ElectronicWarfare #NortheastAsiaMilitaryDynamics #Unmanned
The following content is sourced from Electric Defense, translated by Chuan’s Heart.
On September 7, 2022, the Center for Strategic and International Studies (CSIS) released a report titled “Software-Defined Warfare: The Department of Defense’s Framework for Transitioning to the Digital Age,” which clarifies that the Department of Defense must adopt new software design and architecture approaches to help the US military maintain operational advantages over global adversaries. This article compiles the main content of the report.

(This article is compiled based on the original text for communication reference only, and the views do not represent the position of this institution.)
1. Background
The US military is the most well-equipped, historically longest-standing, and largest armed force in the world, but it also faces many issues: first, the equipment level of the US military is far behind the advanced software levels in the industry; second, the US Department of Defense monopolizes national combat functions, making it unnecessary to face typical forms of industry competition; third, the rise of emerging technology startups and the narrowing of the technological capability gap with competitors compel the US military to conduct regular “technology updates.” The root of these problems lies in the fact that the Department of Defense and other US federal agencies are fundamentally hardware-centric organizations, making it very difficult to transition to software-centric organizations with higher risk tolerance. Therefore, the Department of Defense has failed to adopt new technologies, change its inherent work procedures, and design and test new operational concepts. The Department of Defense needs to make changes, with a key focus on designing a flexible, scalable, adaptive, and low-cost architecture to provide critical services, change the role of humans in the information and decision-making loop, and ultimately influence the speed, accuracy, scale, and technology of operations in the decision-making process. Thus, designing such an operational system architecture requires the following characteristics: faster decision-making and execution speed; rapid updates and optimization of systems; reduced costs for establishing and deploying systems; and improved cost and speed of delivering new functionalities. Currently, concepts such as cyber warfare, mosaic warfare, and next-generation operational networks have introduced the above concepts, but not in depth. The following diagram illustrates the Department of Defense’s integrated concept for large autonomous communication networks and weapon systems based on the above concepts.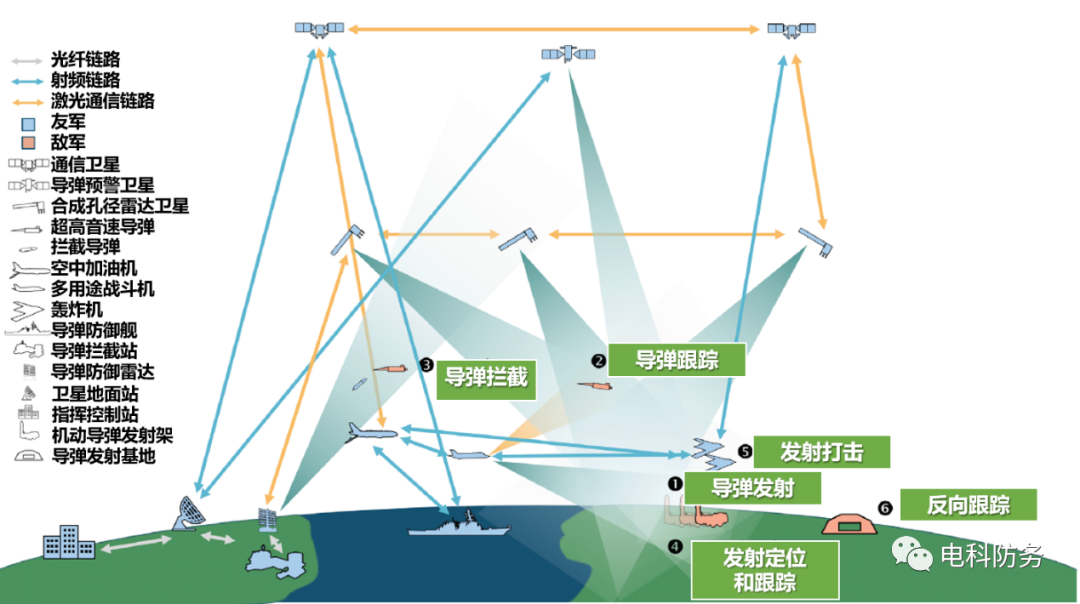 Figure 1: Integrated Concept Diagram of Large Autonomous Communication Networks and Weapon SystemsFrom a developmental perspective, the key to military equipment architecture lies in software, which is disrupting and restructuring the entire industry, especially zero-cost activities that rely on manual processes. To gain sufficient competitive advantage, software must become the core of industry models and operational modes..
Figure 1: Integrated Concept Diagram of Large Autonomous Communication Networks and Weapon SystemsFrom a developmental perspective, the key to military equipment architecture lies in software, which is disrupting and restructuring the entire industry, especially zero-cost activities that rely on manual processes. To gain sufficient competitive advantage, software must become the core of industry models and operational modes..
2. Closing the Kill Chain and Disrupting the Opponent’s OODA Loop
The kill chain is a multi-step process that includes acquiring information, analyzing intelligence, making decisions, taking action, obtaining results, and subsequently refining follow-up actions. The OODA loop refers to the process by which individuals, commanders, or teams achieve operational progress through activities such as observing, orienting, deciding, and acting. The last part of this process—initiating and closing the kill chain—is typically associated with launching and destroying tasks, but it is now equally applicable to cyber attacks. OODA is essentially a workflow supported by human cognition, and gaining an advantage in OODA manifests as a faster, tighter, and more resilient operational process. With advancements in software and computing technologies, a software-centric digital approach to the OODA loop will be necessary on future battlefields; otherwise, it may lead to a comprehensive defeat against competitors at the strategic, operational, and tactical levels. Military hardware and weapon systems remain crucial, but they will only be at the end of software network systems, and executing related decisions will still require complex operational decision-making, target localization, and resource allocation. Software will make the process of achieving effects faster, cheaper, more efficient in decision-making, more scalable in architecture, and more accurate in targeting, fundamentally changing the value of hardware.
3. Nine Key Concepts for Data Center Architecture Design in the Industry
The Department of Defense and other federal agencies can learn from the industry’s lessons based on data center architecture design, where the general design experience is to adopt large-scale software systems to achieve the highest performance at the lowest cost, and then gradually eliminate stubborn elements such as people or hardware from processes and costs where appropriate.This is the concept of “software-defined,” which integrates disparate hardware products into a single operational and management whole by driving decisions based on different core designs while also featuring distributed control.From a military terminology perspective, it can be considered an optimization of “centralized command and decentralized execution.” By borrowing from the industry’s widespread adoption of “Software-Defined Networking” (SDN) in large-scale computing systems and platforms, military equipment architecture can similarly be approached. The following will introduce the nine key concepts for data center architecture design in the industry.
1.
Concept 1: Adopt Large-Scale Architecture
This concept is characterized by investing more resources to address capacity exhaustion issues, such as expanding faster processors, more disk space, and faster network cards in computer systems, known as “vertical scaling.” The downside of this concept is that systems can easily become overwhelmed by server capacity limitations; alternatively, resources can be distributed across more small computers, known as “horizontal scaling,” but this comes with challenges including database storage, file systems, caching, data consistency, software queues, and load balancing, which may require redesigning software structures to address related issues, such as considering a cloud architecture approach.Military software architecture will integrate the advantages and disadvantages of the above methods to build low-cost, disposable, and easily manufacturable end systems that can be centralized, distributed, and scaled up or down as needed, utilizing cloud architecture for centralized computing. The US Department of Defense is already considering applying these ideas to small unmanned aerial vehicles.
2.
Concept 2: Eliminate Single Points of Failure
Currently, the design focus of the US military is hardware, people, and large scale, emphasizing scale. For example, an aircraft carrier is like a large mainframe or database system, a typical system of “vertical scaling,” which faces many single point of failure issues. Due to its expensive nature, when a single point causes system failure, there is usually no backup, leading to costly consequences.The Department of Defense and the industry are beginning to consider identifying and eliminating single points of failure, building a reliable and stable resilient architecture, where decentralized cluster systems such as drone swarms can serve as pilots to effectively deter and attack high-value military targets of competitors, ensuring that individual platform failures do not affect the overall objective while achieving high returns.
3.
Concept 3: Apply Virtualization Technology
Virtualization technology transforms computer servers into virtual machines that can be copied, cloned, snapshotted, and moved, revolutionizing data centers and sparking the cloud computing and “software as a service” revolution.Typically, virtualization creates abstraction and transformation between two different systems or operates and manages an old system as part of a large digital workflow.Once these activities are completed, virtualization enters a second dimension, setting endpoint hardware to run multiple software stacks simultaneously, achieving a distributed service-based “cloud architecture” through shared underlying hardware.For military applications, virtualization systems need to encapsulate platforms, sensors, and workflows within a set of callable application programming interfaces (APIs), with APIs serving as standardized software layer interfaces that can be invoked to demonstrate operational effects of weapon systems through the kill chain.By inputting control commands and executing system information, it can obtain status, capacity, and usage statistics to support operational planning, logistics, and resource management activities.In the Department of Defense’s Joint All-Domain Command and Control (JADC2) demonstration, API-based weapon system access was demonstrated as part of the kill chain, which can be managed by software control but has not yet been formally validated in field military exercises.
4.
Concept 4: Introduce Low-Cost Commercial Hardware and Stateless Terminals
This concept addresses the transition from “vertical scaling” to “horizontal scaling,” leading to terminals that are “stateless” but processable, using real-time software deployment and configuration to resolve issues. Its advantages include significantly reduced maintenance costs over time; the ability to change scale as needed; rapid upgrades of new systems; emergency shielding of bottleneck operations; and the introduction of new security policies. An important feature is that data is stored in the cloud, while local applications are processed through system synchronization.The Department of Defense’s approach is to introduce artificial intelligence programs and redesign new systems accordingly. For example, data training can be conducted across multiple domains using AI algorithms, but training effectiveness varies by environment, and data collected during operational phases can optimize training outcomes.Therefore, AI models need to be updated continuously. In the future, the Department of Defense will attempt to use AI on every software, and when embedded in hardware systems, it will require continuous or even wireless remote updates. To respond to this mechanism, the Department of Defense will also deploy more real-time software on local systems.Similarly, when facing issues on the battlefield, recovery will be expedited through the aforementioned methods. Thus, the ability to change software patches or “single point releases” and deploy them to field hardware systems will become critical for operational support.
5.
Concept 5: Design Measurement Instruments
Almost all products in today’s industry are equipped with measurement tools to measure various data, such as real-time terminal control systems, terminal status, and user functionality, but the Department of Defense currently cannot obtain status information from its end systems.To achieve this concept, the Department of Defense must design and build integrated measurement instrument terminal hardware systems from the outset, including remote control, sensor coordination, and components critical to system operation.Sensors should provide capabilities such as switch status and information values and should consider pairing sensors with automation components while having the ability to report status to users.However, the military currently does not support this concept. Currently, the Department of Defense’s military systems synchronize data primarily by extracting hard drives from helicopters, planes, or drones, which are then sent to secure data centers for download and processing.
6.
Concept 6: Emphasize Simulation, Testing, and Validation
Planning, drills, and exercises are essential parts of preparedness, requiring continuous assessment of results based on current situations to determine the next steps in plans and actions, often in a war game format.However, these plans and actions are rarely tested in advance, which relates to the scale of operational simulations, the number of platforms and targets, the fidelity of battlefield simulations, and the actual configuration of the simulations, with the complexity and importance of the data making transmission difficult.Currently, the Department of Defense is taking steps to integrate real, virtual, and constructive (LVC) weapon system testing methods, hoping to export or extract information from real combat systems into simulation systems in a compliant manner to support the subsequent construction of adversarial red-blue confrontation systems or digital twin systems.The above methods will allow the Department of Defense to use AI technologies and other capabilities to test different adversary strategies and technologies and explore countermeasures. However, there is currently no correct platform and API, so these plans remain on paper.
7.
Concept 7: Introduce Fault Detection Technologies
During software testing, the industry employs techniques to randomly kill certain parts of software systems to test the overall system’s recovery capabilities. The Department of Defense should also introduce such failure detection technologies, which can consider the following forms: first, introducing the aforementioned testing main functions into combat software systems; second, testing combat plans in simulated environments to identify uncontrollable factors.Subsequently, the Department of Defense needs to establish software simulation systems and conduct on-site tests under real combat conditions to achieve optimal performance of the final equipment.
8.
Concept 8: Build Edge Autonomy and Automated Processing Mechanisms
Software-defined systems typically feature separated control and data, representing a distributed control and data processing approach. To reduce system costs and complexity, some small control decisions need to be made by distributed terminals.As the Department of Defense’s systems increase, operational difficulty and costs are rising sharply, and only through more automation and autonomy, along with the adoption of AI technologies at corresponding stages, can the costs of human involvement be eliminated, granting certain systems within the framework the ability to control can significantly reduce the overall complexity of the system.
9.
Concept 9: Integrated Development and Deployment Environments
Currently, the core code development environment and terminal deployment environment of the Department of Defense are not tightly integrated. Various development environments are attempting to address this issue, but there is no straightforward solution. Deploying code to actual terminals is more challenging, requiring extensive pre-deployment testing and evaluation, but accelerating the “development-production-deployment-maintenance” cycle will be crucial for gaining competitive battlefield advantages.The industry has begun to implement this concept, encapsulating code and deploying it to terminals in a “sealed” manner, allowing new systems to process and adapt to developed code while constructing systems as acceptable targets for development, security, and operational processes.The embedding of AI is even more critical, requiring more information acquisition, re-learning, and deployment in business environments, necessitating continuous learning and updates. Therefore, only by integrating development and production environments can future software system development truly adapt.
4. Concept Integration and Architecture Design
The Department of Defense should adopt the above core concepts when designing, developing, operating, and maintaining all its weapon systems and supporting hardware. In this idealized architecture, the end-to-end software architecture connects all relevant sensors (inputs) and weapon systems (outputs), making it easier to manage all correct workflows (kill chains) as well as predictive intelligence systems, information transmission, target and firepower modeling, all integrated into a single architecture built on several large core platforms.Most importantly, everything will be integrated through complex, large-scale, highly available software controlled by either automated or manual means, while integrating development and deployment environments for faster code development, deployment, and maintenance.To achieve the above process, the following steps need to be taken:First, decentralized processing, delegating certain functions and processing authorities, determining structured interfaces and APIs for processing terminals;Second, collaborative working platforms and mechanisms, ensuring that system components can form systemic capabilities over time. This “loosely coupled, highly consistent” architecture can expand its capabilities by introducing more components and capabilities and integrating them into the system.Third, define correct interfaces and clarify the overall architecture, using industry-recognized standards and open-source best practices, with relevant scalability. The following diagram illustrates a standard software-defined architecture.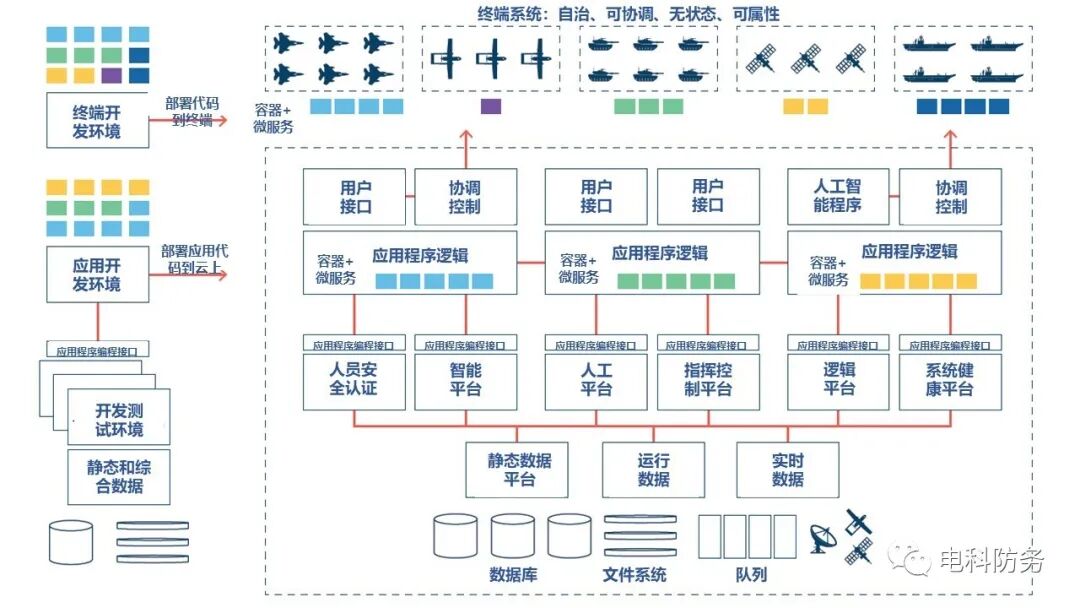 Figure 2: Ideal Core System Architecture of Software-Defined Warfare
Figure 2: Ideal Core System Architecture of Software-Defined Warfare
5. Conclusion
Software-defined warfare is the trend of the future. With the application of new technologies and the formation of data-centric concepts, adapting military weaponry to future combat and exhibiting greater flexibility will be key to winning on the battlefield. Therefore, the Department of Defense needs to change its military equipment software design concepts and architectures, incorporating virtualization, automation, real-time monitoring, and large-scale concepts into software architecture, while emphasizing the degree of AI application within, maximizing the close connection between military objectives and the organization and application of the kill chain between military equipment software and hardware, ultimately integrating into the thinking and design of the next generation of US combat systems.
Reprint Statement
This article is sourced from publicly available information on the internet or has been authorized for reprint through the original public account whitelist. The copyright belongs to the original author. The content of the article does not represent the views of this platform or its authenticity. The purpose of reprinting is to convey information and for online sharing. If there are any copyright issues, please contact us, and we will delete it immediately.


