A serious vulnerability identified as CVE-2025-0072 has been discovered in the Arm Mali GPU driver, posing a significant threat to devices with newer Mali GPUs that utilize the Command Stream Frontend (CSF) architecture, including Google’s Pixel 7, Pixel 8, and 9 series.
This vulnerability was reported to Arm by security researchers on December 12, 2024, and was subsequently patched in the Mali driver version r54p0 released on May 2, 2025, as part of the Android May 2025 security update. It allows malicious Android applications to bypass Memory Tagging Extension (MTE) and achieve arbitrary kernel code execution.
The vulnerability was successfully tested on a Pixel 8 with kernel MTE enabled, highlighting the ongoing challenges in protecting low-level memory even with advanced hardware protections implemented.
New CVE-2025-0072 Vulnerability
The vulnerability exploits the handling of CSF queues in the Mali GPU driver, particularly through the interaction of objects and structures managed via ioctl, such as <span>kbase_queue</span><span>kbase_queue_group</span><span>KBASE_IOCTL_CS_QUEUE_BIND</span><span>KBASE_IOCTL_CS_QUEUE_GROUP_TERMINATE</span>
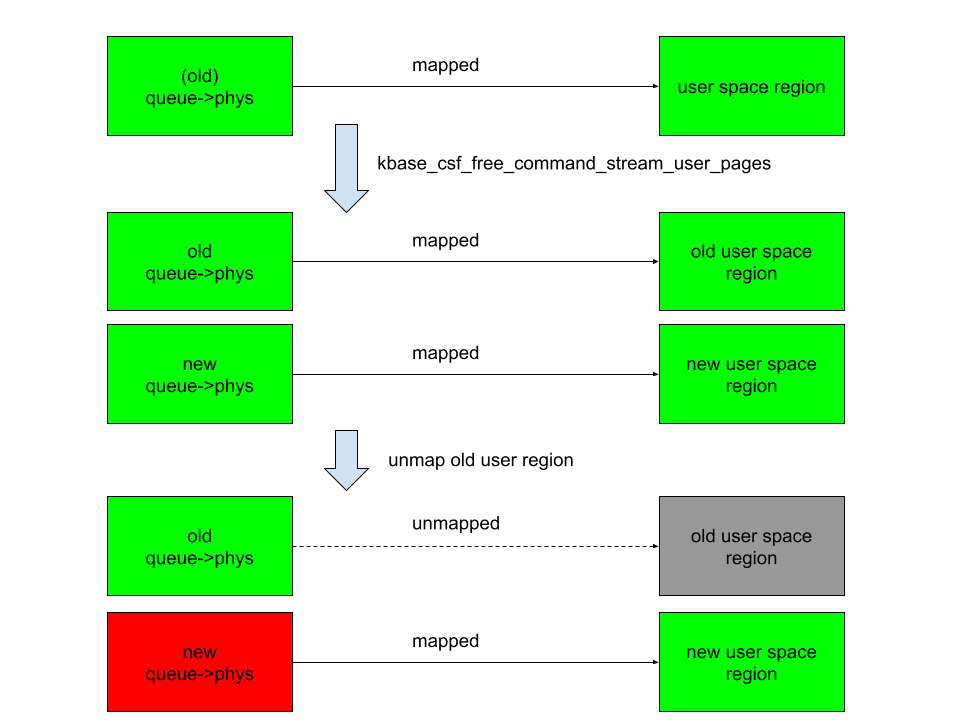
By carefully orchestrating the binding and termination of queues, an attacker can manipulate the <span>queue->phys</span> field to point to newly allocated GPU memory pages while maintaining user space mappings to previously freed pages.
This creates a use-after-free scenario where the freed memory pages can still be accessed through user space mappings.
Exploiting CSF Queues
The exploitation further takes advantage of this by reusing the freed pages as the page table global directory (PGD) for the GPU context, allowing the attacker to map and overwrite kernel memory, including kernel code, thereby gaining full control of the system.
According to reports on GitHub, this process also allows the attacker to escalate process credentials to gain root access and disable SELinux, effectively compromising the device’s security model.
What makes this vulnerability particularly concerning is its ability to bypass MTE, a hardware-based security feature in the Arm v8.5a architecture designed to detect memory corruption issues by tagging memory pointers and blocks, such as use-after-free.
Unlike previous Mali GPU vulnerabilities that accessed freed memory through GPU operations (CVE-2023-6241), CVE-2025-0072 accesses freed memory through user space mappings created by the driver using the following function:<span>mgm_vmf_insert_pfn_prot</span>
This practice of directly inserting page frames into user space page tables seems to avoid kernel-level dereferencing, thus bypassing the MTE tag checking mechanism, even when the pages return to the kernel’s buddy allocator.
This finding highlights a critical gap in MTE protection coverage, as current hardware and software protections do not check user-created mappings through drivers for access to freed memory.
CVE-2025-0072 reveals the limitations of complex memory safety mechanisms like MTE when faced with vulnerabilities in custom memory pools and driver-specific mappings.
This vulnerability not only allows attackers to gain kernel-level control over affected Android devices but also serves as a clear reminder of the need for comprehensive security audits and mitigations at all levels of system architecture.
Disclaimer:This article is either original to this public account or edited and organized based on online searches. The copyright of the article belongs to the original author and is for readers’ learning and reference only. Commercial use is prohibited. Due to numerous reprints, it is impossible to find the true source. If the source is misattributed or if there are any infringements regarding the images, text, links, or software/materials used in the article, please contact us for removal. Thank you!
