Understanding the SPI Mechanism in Dubbo Extensions
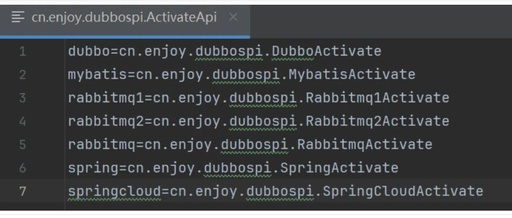
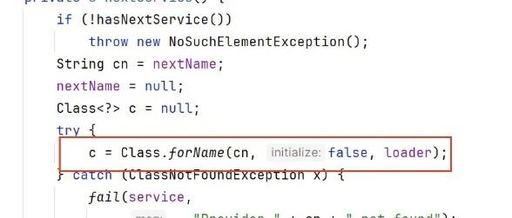
1. What is SPI 1.1 Introduction to SPI SPI, which stands for Service Provider Interface, is a service discovery mechanism. It automatically loads the classes defined in files located in the META-INF/services directory on the ClassPath. This mechanism enables extensibility for many frameworks, such as Dubbo and JDBC. Let’s start with a simple example to … Read more