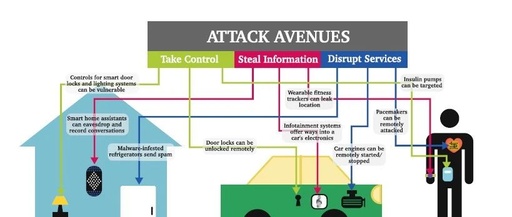
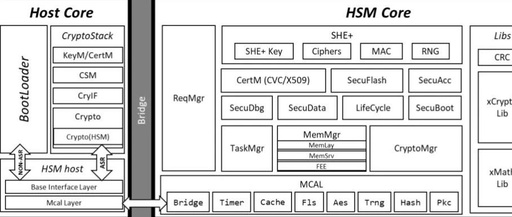
How to Achieve Data Security Encryption Transmission in Power Quality Monitoring Devices
With the development of social economy and technology, the quality of electric energy has increasingly attracted more attention. The advancement of technology has deteriorated the quality of electric energy while also raising higher requirements for it, with harmonics being one of the important technical indicators of electric energy quality. Good electric energy quality is the … Read more