
Click the blue text above to follow me

Hacker Techniques

With the advancement of technologies such as the Internet of Things (IoT) devices, wearables, and smart home kits, embedded systems continue to evolve rapidly. Choosing the right programming language for embedded architecture development is crucial for efficient, reliable, and scalable solutions.
The public account “Computer Program Bar” will introduce the top 5 embedded architecture programming languages dominating the industry in 2024.
C Language
Despite being around for nearly a century, C language remains the standard format for embedded systems programming in 2024 due to its unique features. Its low-level capabilities, efficient memory management, and direct hardware manipulation make it an ideal choice for resource-constrained environments.
The simplicity and widespread use of C language ensure a large developer community and extensive documentation, which are invaluable for troubleshooting and optimization. The public account “Computer Program Bar” focuses on sharing knowledge of cutting-edge technology and technical expertise.

The main advantages of C language include its portability across dedicated microcontrollers, minimal runtime overhead, and potential for writing optimized code. These factors allow C language to continue to dominate in embedded firmware development, real-time operating systems, and embedded device drivers.
C++
C++ language, based on C, introduces object-oriented programming to embedded systems. In 2024, C++ is becoming increasingly popular in more complex embedded systems, especially those requiring advanced user interfaces or complex data structures. Its support for instructions, templates, and the Standard Template Library (STL) allows for higher modularity and reusable code.

While C++ has a higher overhead compared to C, modern compilers have significantly improved the optimization of C++ code for embedded systems. This makes C++ the preferred choice for projects requiring stability, performance, and a higher level of abstraction.
Python
The rise of Python in embedded systems programming is remarkable. In 2024, it is widely used for rapid prototyping, testing, and even production of certain embedded applications. MicroPython, a lightweight implementation of Python 3, has made it possible to run Python on resource-constrained microcontrollers, further enhancing its versatility and adaptability. Follow the public account “Computer Program Bar” for real-time updates on cutting-edge technology trends.

Python’s simplicity, readability, and vast library ecosystem make it an excellent choice for IoT devices and edge computing applications. Although it may not be suitable for mission-critical tasks, Python excels in statistical processing, connectivity, and advanced control logic in embedded systems.
Rust
Rust has gained significant attention in global embedded systems in 2024 due to its focus on memory safety and zero-cost abstractions. It provides the performance of low-level languages like C and C++, while ensuring safety against common programming errors, including buffer overflows and data races.

The main advantage of Rust lies in its memory management, which is handled statically and dynamically through various tools. Additionally, with Rust, embedded developers can write for a range of embedded systems, from small microcontrollers to multi-faceted systems.
Java
Finally, Java is the most widely used language among embedded developers. Due to its WORA (Write Once, Run Anywhere) capabilities, this programming language can be applied across various platforms. Furthermore, thanks to its DevOps tools, Java is well-known in the field.
With Java embedded programs, developers can write portable, downloadable, and scalable embedded applications. Java programs offer a wealth of libraries and DevOps tools.

Additionally, through the Java Virtual Machine, developers can ensure that embedded systems developed in Java are easy to port and applicable to various IoT platforms. To learn more about IoT technology, you can follow “Computer Program Bar” for search queries.
The panoramic advantages of programming languages for embedded systems in 2024 explain the stability of traditional and modern programming languages in terms of efficiency and productivity. Languages like C and C++ demonstrate control over hardware and real-time performance, while Python, Rust, and Java are expanding the possibilities for improvements in embedded systems.

Choosing the right programming language depends on the challenges’ requirements, hardware constraints, the development team’s knowledge, and long-term maintainability. As embedded architectures become increasingly complex and interconnected, choose the embedded software development services from “Computer Program Bar”, as our expertise and insights make us a reliable partner in this evolving field.
Popular Career Directions in Computer Science
Currently, the job prospects in cybersecurity are quite promising. According to statistics from 2022, the gap in cybersecurity professionals has grown to 1.4 million.
1. Numerous job positions and broad development directions
① Employment Environment: Cybersecurity can involve related work in fields such as computer science and technology, information communication, e-commerce, internet finance, and e-government. It can also be conducted in government agencies, banks, insurance, securities, and other financial institutions, as well as in telecommunications and media industries.
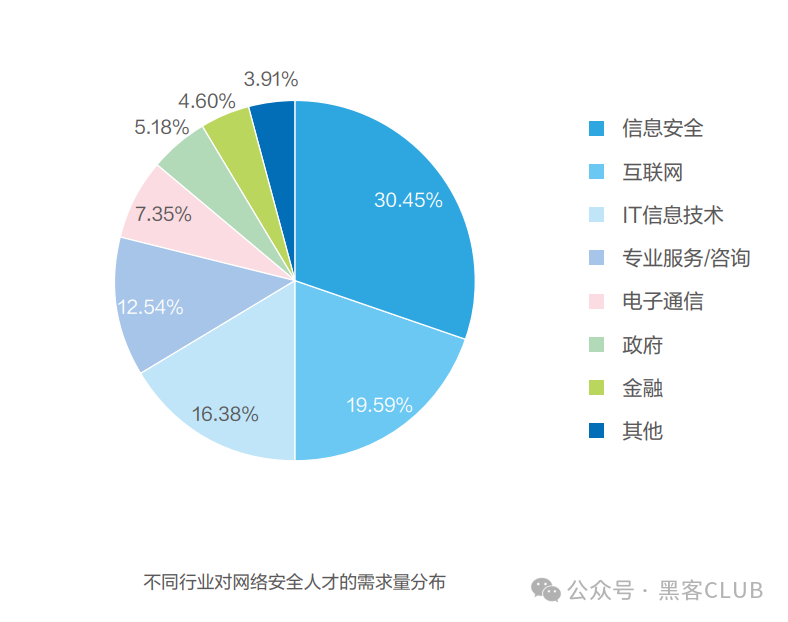
② Job Positions: Cybersecurity Engineer, Penetration Testing Engineer, Code Audit Engineer, Level Protection Engineer, Security Operations Engineer, Security Operations Engineer, Security Service Engineer, etc.
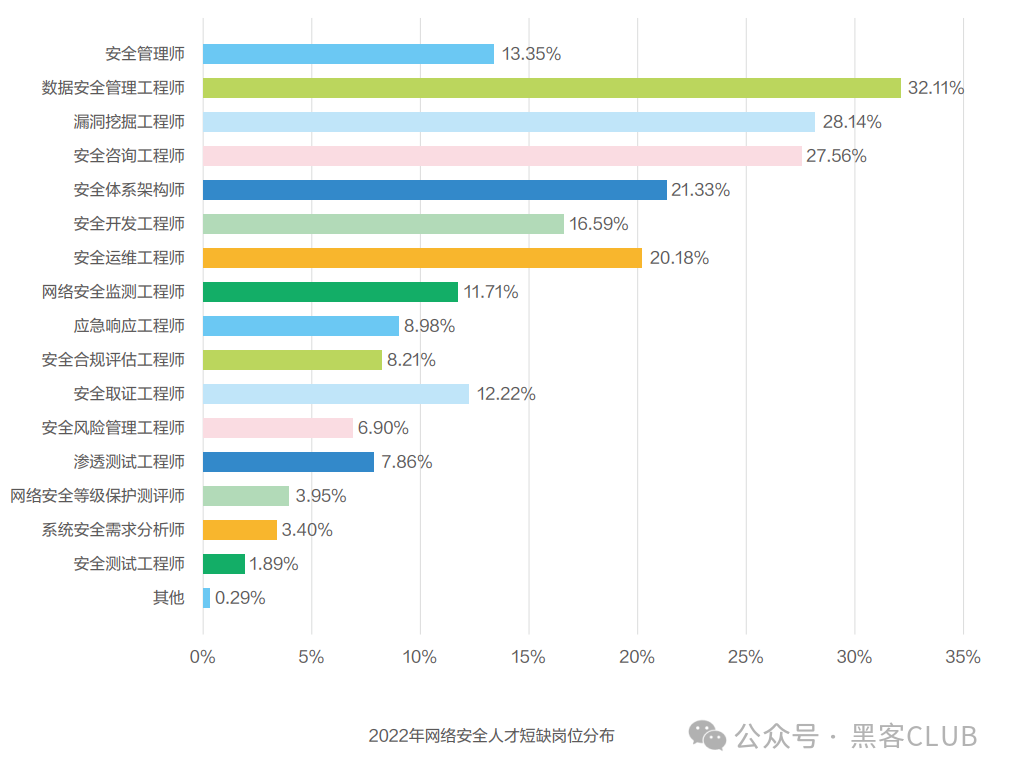
2. Attractive salary and rapid improvement
As an emerging industry, the market demand for cybersecurity talent far exceeds supply. For companies to truly recruit talent, they must have sufficient competitive advantages in salary and benefits. Therefore, salaries in the cybersecurity field have shown steady growth in recent years.
According to the “Cybersecurity Industry Talent Development Report” released by the Ministry of Industry and Information Technology, the average annual salary of cybersecurity professionals is 212,800 yuan, indicating a high overall salary level. Data shows that the annual salary of cybersecurity professionals is mainly concentrated in the range of 100,000 to 200,000 yuan, accounting for 40.62%, which is consistent with previous years; followed by the range of 200,000 to 300,000 yuan, accounting for 38.43%, showing a significant increase from 19.48% in 2020; while the proportion of those earning below 100,000 yuan dropped from 19.74% in 2020 to 9.08% in 2022. This indicates that the cybersecurity industry, as an emerging track, is still in a rapid development stage, with the salary levels of practitioners rising quickly, reflecting a greater emphasis on talent retention in the cybersecurity field.

3. Great career development space
From the main content of learning cybersecurity, including Linux operations, Python development, penetration testing, code auditing, level protection, emergency response, and risk assessment, it is evident that this cybersecurity major is highly technical and has distinct professional characteristics, making it one of the engineering majors where one can learn real technology.
Therefore, in terms of career development, the cybersecurity major not only offers numerous job positions but also places graduates in a core technical position within their workplaces due to its strong technical nature, providing significant career development opportunities.
Summary of Cybersecurity Positions
01
Position One: Penetration Testing Engineer
**Position Definition:** Simulating hacker attacks, utilizing hacking techniques, discovering vulnerabilities, and proposing remediation suggestions. Some large companies, such as Qihoo 360, even divide the penetration position into red and blue teams, requiring high technical demands from candidates, making penetration testing a common goal for many newcomers.
Job Responsibilities:
Responsible for penetration testing, security assessment, and security hardening of client networks, systems, and applications.
Provide emergency response services when network attacks or security incidents occur, assisting users in system recovery and investigation.
Recommend reasonable network security solutions based on the client’s network architecture.
Difficulty Level: 5 stars
Salary Status:

02
Position Two: Security Operations Engineer
Position Definition: Maintaining the normal and secure operation of network systems; if subjected to hacker attacks, emergency response and intrusion investigation security hardening are required. Many newcomers typically start their careers in operations.
Job Responsibilities:
Daily terminal maintenance, operating system installation and hardening.
Complete troubleshooting and handling of network security equipment failures.
Complete the writing and submission of relevant management system documents.
Difficulty Level: 3 stars
Salary Status:
03
Position Three: Security Operations Engineer
Position Definition: Based on operations, efficiently and sustainably enhance the enterprise’s security defense capabilities.
Job Responsibilities:
Responsible for the formulation and optimization of various security policies, including monitoring and scanning.
Responsible for emergency response to information security incidents.
Participate in network security assessment work, security hardening work, and monitoring, etc.
Difficulty Level: 3 stars
Salary Status:

04
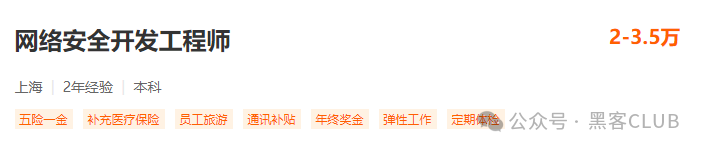
Position Four: Security Development Engineer
Position Definition: As the name suggests, responsible for the development of security products, platforms, and policies.
Job Responsibilities:
Responsible for the system technical design, code development and implementation, unit testing, static checks, and local builds of network security products.
Participate in the system technical design and research and development of other company products.
Difficulty Level: 5 stars
Salary Status:
05
Position Five: Level Protection Assessment Engineer
Position Definition: Also known as level protection assessment, primarily responsible for conducting information security level protection assessments, information security risk assessments, emergency responses, and information security consulting.
Job Responsibilities:
Implementation of network security level protection assessment projects.
Implementation cooperation for security projects such as web penetration testing and operating system security hardening.
Difficulty Level: 3 stars
Salary Status:

06
Position Six: Security Research Engineer
Position Definition: Research talent in the field of cybersecurity.
Job Responsibilities:
Track and analyze domestic and international security events, development trends, and solutions.
Undertake or participate in innovative research topics.
Participate in project proposal design, organize and promote project implementation, and complete research content.
Responsible for tackling key technologies in cybersecurity and developing security tools.
Difficulty Level: 5 stars
Salary Status:

07
Position Seven: Vulnerability Discovery Engineer
Position Definition: Mainly engaged in reverse engineering, software analysis, and vulnerability discovery work.
Job Responsibilities:
Assess the security status of computer network systems through simulated specific methods.
Identify network security vulnerabilities through specific techniques, discovering but not exploiting vulnerabilities.
Difficulty Level: 5 stars
Salary Status:

08
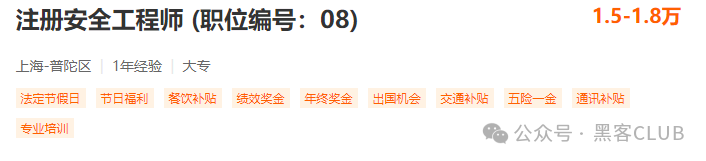
Position Eight: Security Management Engineer
Position Definition: Responsible for the formulation and review of processes, specifications, and standards related to information security, and for the construction of the overall security system of the company.
Job Responsibilities:
Planning and constructing the technical system for network security across all business systems, optimizing the network security architecture.
Responsible for formulating and reviewing processes, specifications, and standards related to network security, efficiently handling emergencies.
Responsible for building network security protection systems, enhancing network security assurance levels.
Difficulty Level: 4 stars
09
Position Nine: Emergency Response Engineer
Position Definition: Mainly responsible for emergency response to information security incidents, attack tracing, and forensic analysis, participating in the research of emergency response, attack tracing, and forensic analysis techniques to enhance overall capabilities for handling major information security incidents.
Job Responsibilities:
Responsible for emergency response to information security incidents, attack tracing, and forensic analysis work.
Summarize experience in emergency response to security incidents and conduct training.
Responsible for security testing (black box and white box) and penetration testing for all business systems before going live.
Participate in the research of emergency response, attack tracing, and forensic analysis techniques to enhance overall capabilities for handling major information security incidents.
Track domestic and international security hot events, mainstream security vulnerabilities, threat intelligence, and black and gray market dynamics, conducting analysis and research to form response plans.
Difficulty Level: 4 stars
Salary Status:

10
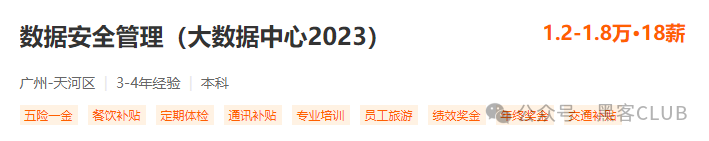
Position Ten: Data Security Engineer
Position Definition: Mainly responsible for the daily maintenance and management of the company’s data security, ensuring data security.
Job Responsibilities:
Responsible for daily maintenance and management of data security, including data security audits, monitoring and response to data security incidents, and audits and investigations for security compliance.
Responsible for the formulation and management of data security standards and specifications, including data security requirement identification, risk analysis, data classification, data desensitization, data flow, leak protection, permission control, etc.; promote the implementation and execution of related security control strategies on the platform.
Responsible for carrying out various data security work related to the entire data lifecycle.
Responsible for formulating and implementing data security solutions for cross-platform and cross-region data transmission and interaction.
Regularly organize and conduct self-assessment of data security, identify potential data security risks, formulate corresponding control measures, and promote the implementation of rectification.
Difficulty Level: 4 stars
Salary Status:
——
Introduction to Cybersecurity
If you are genuinely interested in 【cybersecurity/hacker techniques】 and have ample time to learn, I can share over 90 video tutorials that I have collected for free, whether you are a beginner or looking to advance your skills:
【Scan the card below to claim】
-
Growth roadmap & learning plan
-
Supporting video tutorials
-
SRC & hacker literature
-
Network protection action materials
-
Must-read hacker book list
-
Interview question collection

After one to two months of consistent learning, you can start discovering vulnerabilities for rewards. After three to four months, you can reach the technical level needed for CTF competitions (as shown in the resource screenshots below).
1. Video Tutorials
Many friends do not like obscure texts, so I have prepared video tutorials for everyone, which include a total of 21 chapters and 190 lessons, each chapter condensed with the essence of the current section.

Send “hacker” to the public account to get the complete video tutorial and toolkit for free



Complete network offense and defense video courses + interview questions, scan the card to take it!
I wish everyone can advance and become a technical expert!