
Click the top left corner to follow us
Gift to Readers
In the wonderful world of coding research, we can gain many unique insights. From the perspective of algorithm optimization, it is like carefully polishing a piece of art; each refinement of the code and improvement of the algorithm is akin to removing impurities, making it more efficient. This inspires us to continuously examine our ways of working in life and at work, seeking optimization opportunities to enhance efficiency. For example, when dealing with complex data, skillfully using data structures and algorithms can transform originally chaotic information into an orderly format, reminding us to be adept at finding patterns and summarizing methods when facing complex problems.

01/Overview
Introduction:
The Wireless Sensor Network (WSN), as a monitoring system composed of numerous distributed sensor nodes, is widely used in various fields such as environmental monitoring, military reconnaissance, and industrial control. In the actual operation of WSNs, the distribution state of nodes has a crucial impact on network performance. Among them, the existence of holes and boundary nodes is two key issues, and accurately detecting them is significant for maintaining network connectivity, coverage, and data transmission efficiency.
Concepts and Impacts of Holes and Boundary Nodes
1. Hole Nodes:A hole refers to a phenomenon within the coverage area of a WSN where, due to node failures, energy depletion, physical damage, or irregular node deployment, a local area experiences a lack of sensor nodes or nodes that cannot function properly. The nodes in this area are termed hole nodes. The emergence of holes can create monitoring blind spots, leading to a lack of environmental information collection in these areas, severely affecting the comprehensiveness and accuracy of monitoring. For example, in a WSN for forest fire monitoring, if a critical forest area forms a hole, it will be unable to detect a fire in time, delaying the response.2. Boundary Nodes:Boundary nodes are located at the edge of the WSN coverage area. Compared to internal nodes, they have relatively fewer connections to neighboring nodes and face issues such as signal attenuation when transmitting data outward and susceptibility to external interference. The characteristics of boundary nodes determine their energy consumption patterns, which differ from internal nodes, as they often undertake more cross-regional data forwarding tasks. If not managed properly, they can deplete energy prematurely, affecting network connectivity and overall stability. For instance, in a soil moisture monitoring WSN in smart agriculture, boundary nodes located at the edge of farmland are responsible for collecting local soil information while also aggregating and forwarding data from scattered surrounding nodes, resulting in a heavier workload.
The Importance of Detecting Holes and Boundary Nodes
1. Ensuring Monitoring Quality:Timely detection of hole nodes can prompt the network to quickly take remedial measures, such as waking up backup nodes, redeploying mobile nodes, or adjusting the monitoring range of existing nodes to fill monitoring blind spots, ensuring continuous and complete monitoring of the target area. Only by obtaining comprehensive and accurate monitoring data can reliable evidence be provided for subsequent decision analysis. For example, in the context of industrial pollution emission monitoring, precise monitoring data is a key support for regulatory enforcement by environmental protection departments.
2. Optimizing Network Performance:Accurately identifying boundary nodes helps to formulate specific energy management strategies for them, such as reducing data transmission frequency, adopting more efficient encoding methods, or enhancing signal transmission power, balancing energy consumption between boundary and internal nodes, and extending the overall lifespan of the network. Additionally, precise control of the connection status of boundary nodes is beneficial for optimizing data transmission path planning, reducing transmission delays and packet loss rates, and improving communication efficiency within the network. This is particularly important in urban intelligent traffic WSN applications, as it concerns the smooth transmission of real-time traffic information.
Common Detection Methods
1. Methods Based on Neighbor Node Information: Neighbor Node Count Method:Each sensor node periodically exchanges information with surrounding neighbor nodes to count the number of its neighbor nodes. If the number of neighbor nodes for a certain node is significantly lower than the network’s average neighbor node count threshold and persists for a period, that node is likely to be at a boundary position; if the number of neighbor nodes is zero or very few, it may be located within a hole. This method is simple and direct, with low computational costs, but it is easily affected by uneven node distribution, potentially leading to misjudgments in sparse areas.Neighbor Node Distance Method:Nodes not only understand the number of neighbor nodes but also measure the distances to them. Boundary nodes are typically farther away from some neighbor nodes. By setting a distance threshold, when the distance between a node and its farthest neighbor exceeds the threshold, it is determined to be a boundary node; for hole nodes, an abnormal increase in distances to surrounding neighbor nodes or extremely uneven distribution can serve as judgment criteria. This method requires high accuracy in distance measurement; otherwise, it will affect the accuracy of detection results.
2. Methods Based on Topological Structure:Graph Theory Algorithms:Abstract the WSN as an undirected graph, with nodes as vertices and communication links between nodes as edges. Utilize the connectivity and degree distribution characteristics of the graph to identify boundary and hole nodes. For example, by calculating the degree of a node (i.e., the number of edges connected to it), nodes with a lower degree are more likely to be boundary nodes; for hole detection, concepts such as cut points and bridges in the graph can be used. If removing a certain node leads to an increase in the number of connected components in the graph, then there may be a hole in the area where that node is located. These methods can accurately analyze node characteristics from a macro network topology perspective, but the algorithm complexity is relatively high and requires certain computational resources.Clustering Algorithms:Divide the nodes in the WSN into multiple clusters, with cluster head nodes responsible for managing cluster members and communicating with other clusters. Boundary nodes are often located at the edges of clusters. By monitoring the distribution of cluster members and analyzing inter-cluster communication status, boundary nodes can be identified; holes typically manifest as a very small number of nodes within a cluster or irregular cluster shapes, and these features can be used to locate hole nodes. Clustering algorithms have good operability in large-scale WSNs and can effectively reduce management complexity, but the clustering strategy and parameter selection will affect detection results.
Current Research Status and Challenges
1. Current Research Status:Currently, significant achievements have been made in the research on hole and boundary node detection in WSNs, with various detection methods continuously improving from different perspectives, and detection accuracy gradually increasing. Many methods combine cutting-edge technologies such as machine learning and artificial intelligence, for example, using neural networks to learn and train neighbor node data to more intelligently determine node types. In application fields, detection schemes are customized according to the needs of different industries. For instance, in wearable WSNs in healthcare, methods focusing on low power consumption and real-time performance are emphasized to ensure continuous collection of physiological signals from the human body.
2. Challenges:Poor Adaptability to Dynamic Environments:In actual WSN application scenarios, the environment where nodes are located changes frequently, such as random movement of nodes, the addition of new nodes, unexpected failures of old nodes, and sudden increases in environmental interference factors. Existing detection methods struggle to adapt to these changes in real-time and accurately, leading to delayed or inaccurate detection results, which affects the continuous and stable operation of the network.Trade-off Between Energy Efficiency and Detection Accuracy:Improving detection accuracy often requires nodes to frequently exchange information and perform complex computational operations, which undoubtedly increases energy consumption; however, if energy-saving is overly pursued, it may sacrifice detection accuracy, making it impossible to timely discover critical hole and boundary nodes. Finding a balance between the two, designing solutions that meet high-precision detection requirements while minimizing energy expenditure, is a significant challenge currently faced. The complexity of large-scale networks: As the scale of WSNs continues to expand, the number of nodes increases dramatically, and the network topology becomes increasingly complex. Traditional detection methods face severe challenges in terms of computational complexity, communication overhead, and storage requirements, making it difficult to accurately detect all nodes within acceptable time and resource limits.

02/Operational Results
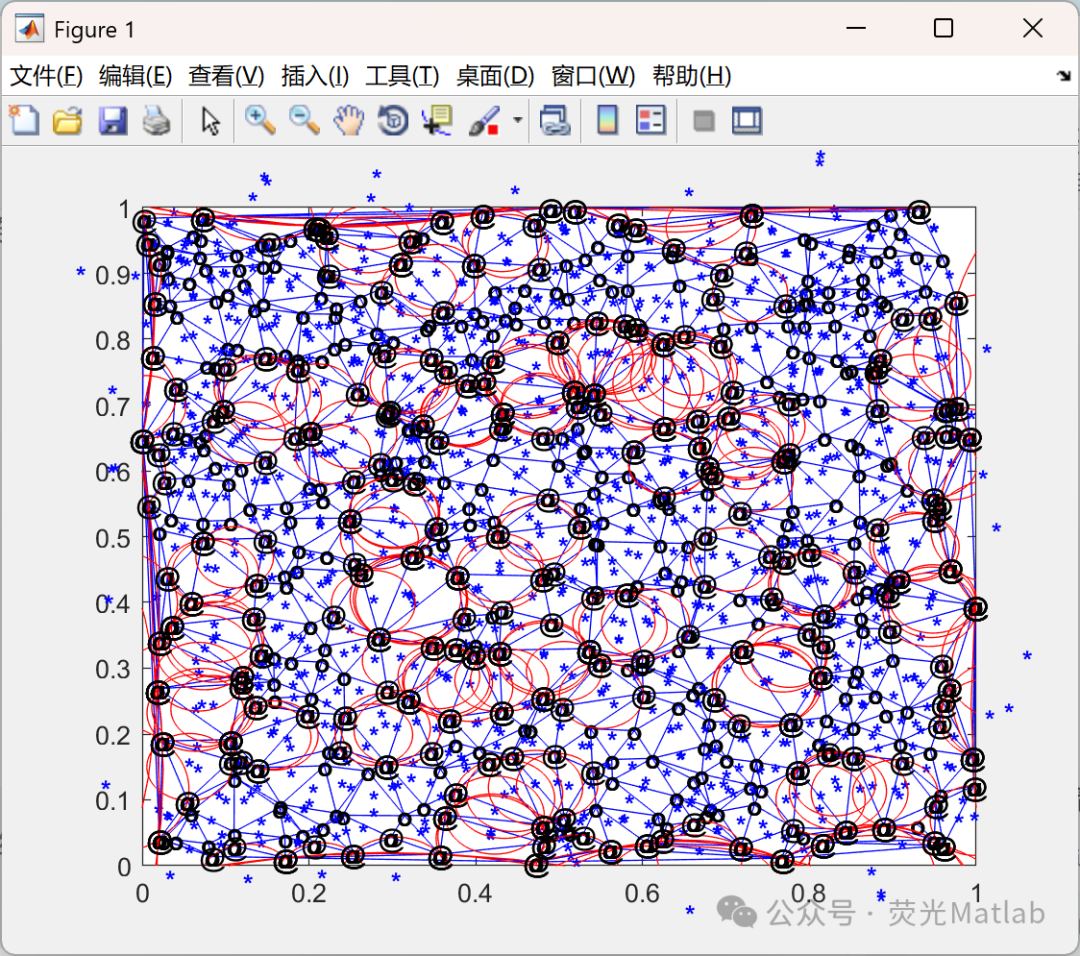

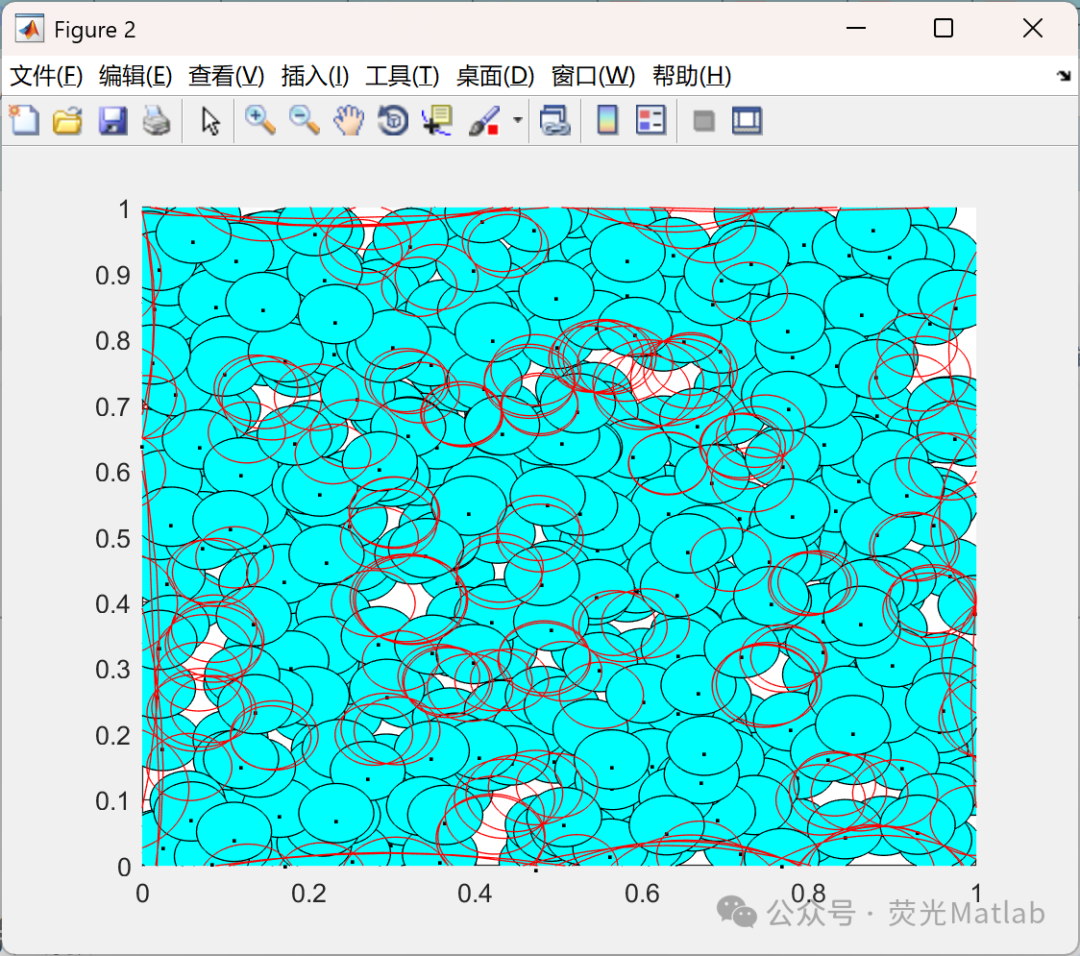







03/Partial Code
n = 500;
x = rand(n,1);
y = rand(n,1);
dt = DelaunayTri(x,y);
figure(1);
triplot(dt);
vxlabels = arrayfun(@(n) {sprintf('o')}, (1:n)');
Hpl = text(x, y, vxlabels, 'FontWeight', 'bold', 'HorizontalAlignment',...
'center', 'BackgroundColor', 'none');
[cc,r]= circumcenters(dt);
numtri = size(dt,1);
trilabels = arrayfun(@(x) {sprintf('*')}, (1:numtri)');
Htl = text(cc(:,1), cc(:,2), trilabels, 'FontWeight', 'bold', ...
'HorizontalAlignment', 'center', 'Color', 'blue');
i = 0;
k = size(r,1);
rs=0.045;
rc = 0;
ra = zeros(1,k);
for l=1:k
if ( cond1(r(l), rs) == 1 )
x = cond2(dt, cc, l, rs);
if x == 0 || x == 1
rc = rc+1;
ra(rc) = l;
circle(cc(l,1), cc(l,2), r(l));
end;
end;
end;
for l=1:rc
x = dt.X(dt.Triangulation(ra(l),:), 1);
y = dt.X(dt.Triangulation(ra(l),:), 2);
xlabels = arrayfun(@(n) {sprintf('@')}, (1:3)');
Hp1 = text(x, y, xlabels, 'FontWeight', 'bold', 'HorizontalAlignment',...
'center', 'BackgroundColor', 'none');
end;
figure(1);
figure(2);
for l = 1:n
x= dt.X(l,1);
y= dt.X(l,2);
plot2(x,y,rs);
end;
for l=1:rc
l1=ra(l);
04/References
[1] Feng Mei. Automatic Control of Access in Wireless Sensor Networks Based on CP-ABE Algorithm[J]. Automation and Instrumentation, 2025, 40(03): 133-137. DOI:10.19557/j.cnki.1001-9944.2025.03.027.
[2] Liu Zhouzhou, Jin Cong, Jiang Guangyi, et al. Anomaly Detection of Wireless Sensor Network Traffic Based on Deep Learning[J/OL]. Journal of Jilin University (Engineering Edition), 1-8 [2025-04-01].https://doi.org/10.13229/j.cnki.jdxbgxb.20250045.
Some content in this article is sourced from the internet, and references will be noted or cited as references. If there are any inaccuracies, please feel free to contact us for removal.


Scan to contact us!