
According to the received threat intelligence report, the hacker group IronShade has launched attacks against Linux servers in the region. To prevent attacks from this APT organization and understand their attack patterns, our team set up a honeypot, exposing weak SSH and ports. As security analysts, we need to conduct a comprehensive intrusion assessment on a compromised Linux server and determine the following issues:
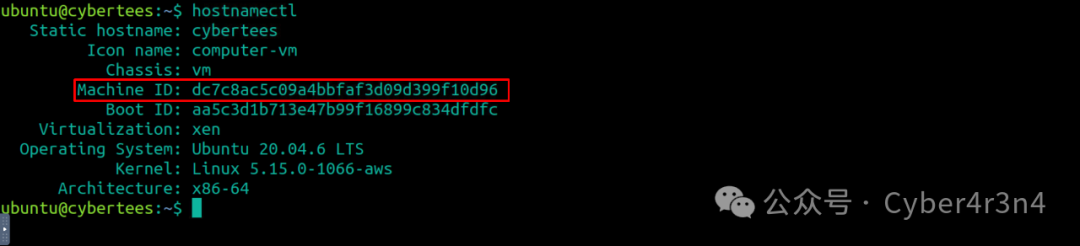
What is the machine ID of the machine under investigation?
What backdoor user accounts have been created on the server?
What cronjob has the attacker set up for persistence?
Check the processes running on the machine. Can you identify any suspicious hidden processes from the backdoor account?
How many processes are running from the backdoor account’s directory?
What is the name of the file hidden in memory in the root directory?
What suspicious services are installed on the server? Format as service a, service b, in alphabetical order.
Check the logs; when was the backdoor account created on this infected system?
From which IP address were multiple SSH connections observed targeting the suspicious backdoor account?
How many failed SSH login attempts were observed on the backdoor account?
Which malicious package is installed on the host?
What password was found in the metadata of the suspicious package?
1. Basic Information Investigation 🔍
Obtain the hostname and basic system information using hostnamectl.
2. Account Investigation 🔍
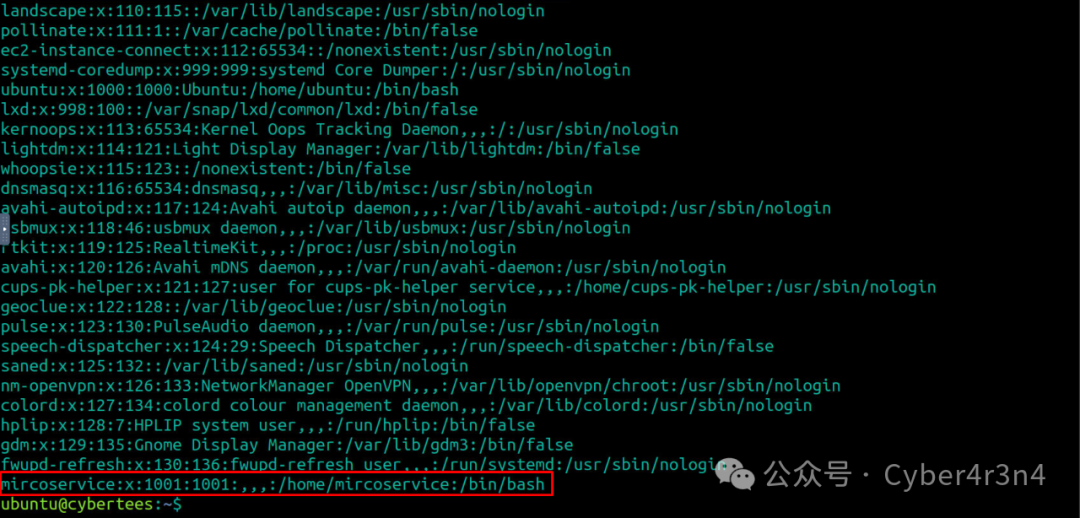
2.1 Check the /etc/passwd file
View the user accounts present in the system, paying special attention to non-system accounts and suspicious accounts. A suspicious account microservice was found, with its shell set to /bin/bash instead of /sbin/nologin, indicating that this account can log into the system.
3. Cron Job Investigation 🔍
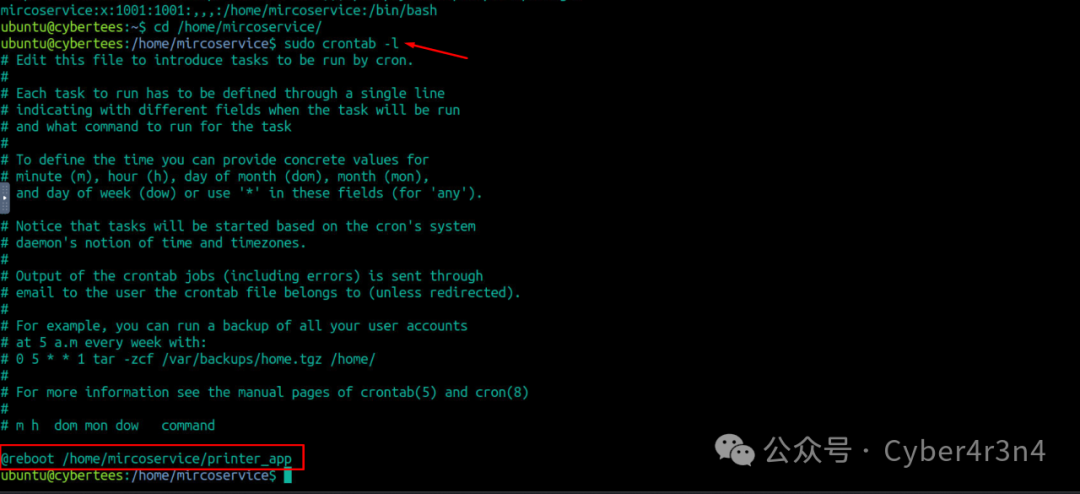
3.1 Check cronjobs
Check the cronjob for the microservice user and found a cronjob: @reboot /home/microservice/printer_app, indicating that the printer_app program will automatically run after the system reboots, possibly a method used by the attacker for persistence.
4. Process Investigation 🔍
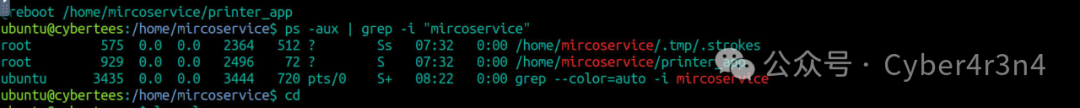
4.1 Check processes related to microservice
Use the command ps -aux | grep -i “microservice” to find running processes related to the suspicious user microservice. A suspicious process /home/microservice/printer_app was found, which matches the program set in the cronjob.
ps -aux | grep -i “/home/microservice” | wc -l counts the number of processes running from the microservice user directory, revealing that there are two suspicious processes running.
5. Service Investigation 🔍
5.1 Check system services
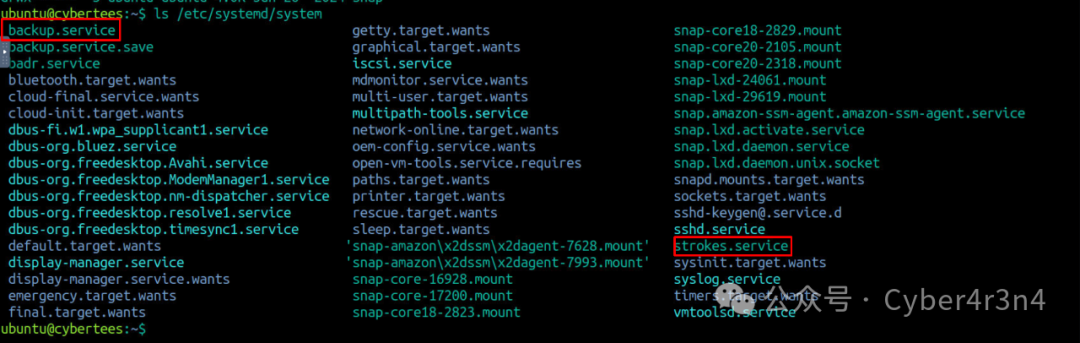
Use ls /etc/systemd/system to list the services installed on the system, discovering two suspicious services backup.service and strokes.service.
6. Log Analysis 🔍
6.1 Check user creation logs
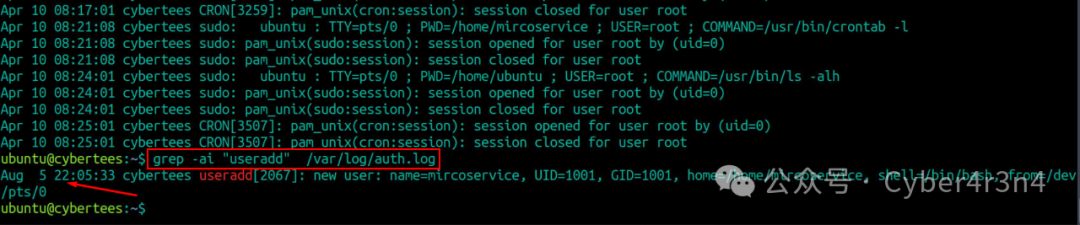
Search for records of user creation to determine the creation time of the backdoor account. grep -ai “useradd” /var/log/auth.log shows that the backdoor account microservice was created at a specific time Aug 5 22:05:33, which helps establish the attack timeline.
6.2 Check SSH login attempts
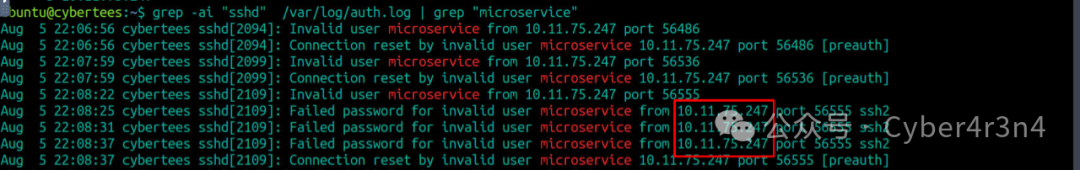
Search for SSH login attempts related to the microservice account. grep -ai “sshd” /var/log/auth.log | grep “microservice” found multiple SSH connection attempts from the IP address 10.11.75.247, indicating that this IP may be the source of the attacker.
6.3 Count failed SSH login attempts
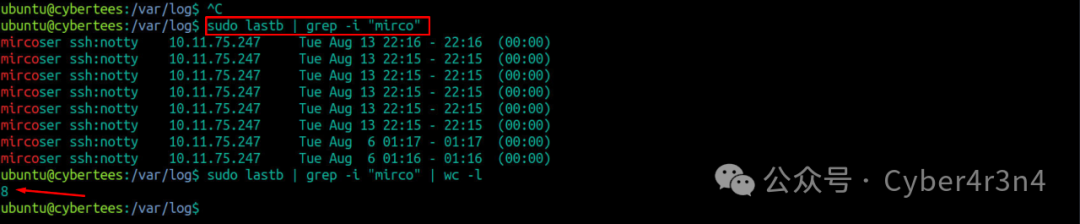
Count the number of failed SSH login attempts for the microservice account. sudo lastb | grep -i “microservice” | wc -l found multiple failed login attempts, possibly indicating that the attacker is trying to crack the password or using brute force tools.
7. Package Check 🔍
7.1 Check installed packages
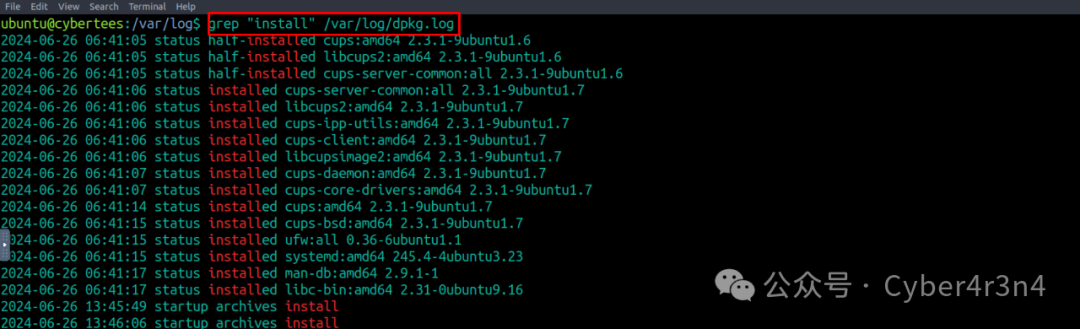
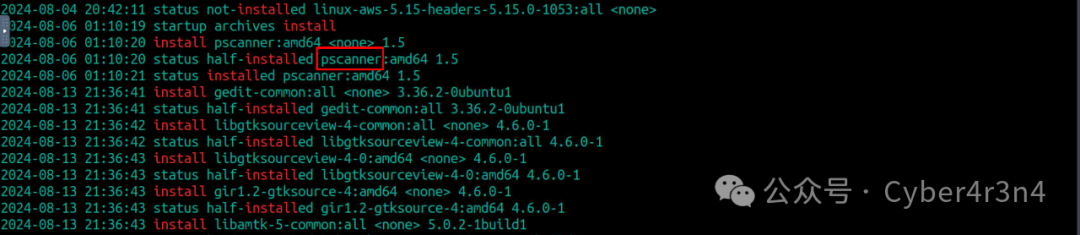
Search for recently installed packages to identify suspicious malicious packages. grep “install” /var/log/dpkg.log found a suspicious package pscanner, which may be a malicious tool for network scanning or exploitation.
7.2 Check package metadata
View the details of the pscanner package to look for possible passwords or other sensitive information. dpkg -l | grep pscanner found a password in the package description or metadata, which may be a backdoor credential left by the attacker.

8. Incident Summary 🖊
Through the intrusion investigation of this Linux server, it was confirmed that it has been compromised.
The attacker created the backdoor account “microservice” and achieved persistence through a cronjob (@reboot /home/microservice/printer_app), ensuring that the malicious program runs automatically after the system reboots.
The attacker also installed malicious services “backup.service” and “strokes.service”, as well as the malicious package “pscanner”, which contains a password as a backdoor credential.
Log analysis shows that the attacker initiated multiple SSH login attempts from the IP address 10.11.75.247 and successfully created the backdoor account on Aug 5 22:05:33.