
In this article, we will explore several ways to specify the resolution results of specific domain names inside containers. To facilitate demonstration, we first create a Deployment configuration file.
apiVersion: apps/v1
kind: Deployment
metadata:
name: busybox-deployment
labels:
app: busybox
spec:
replicas: 1
selector:
matchLabels:
app: busybox
template:
metadata:
labels:
app: busybox
spec:
containers:
- name: busybox
image: busybox
args:
- /bin/sh
- -c
- "while true; do echo Hello, Kubernetes!; sleep 10;done"
This deployment will create one busybox pod, and the container will print “Hello, Kubernetes!” to the console every 10 seconds.
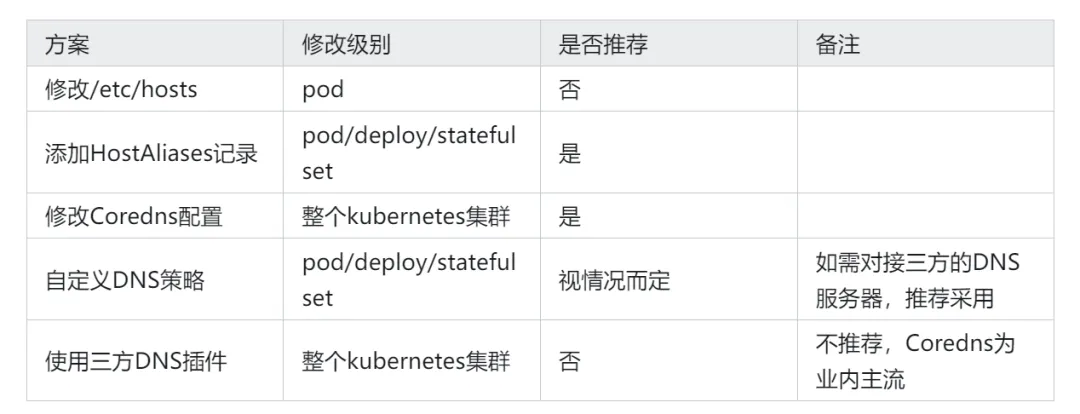
TL;DR
Modify /etc/hosts
Modifying /etc/hosts is the most traditional method, directly changing the corresponding file inside the container to achieve domain name resolution, effective at the Pod level. Due to its poor maintainability (it needs to be manually modified every time the pod restarts), it is not recommended for production environments.
For example, we can add a record like this in /etc/hosts
250.250.250.250 four-250
/ # ping four-250
PING four-250 (250.250.250.250): 56 data bytes
Add HostAliases Records
HostAliases is a field in Kubernetes Pod configuration that provides additional records for the /etc/hosts file of the Pod container. This can be very useful in certain situations, especially when you want to override the resolution results of a hostname or provide resolution for hostnames that are not available in the network.
This can be modified at the Pod, Replica, Deployment, or StatefulSet level, offering slightly better maintainability. For example, we can modify the above yaml to
apiVersion: apps/v1
kind: Deployment
metadata:
name: busybox-deployment
labels:
app: busybox
spec:
replicas: 3
selector:
matchLabels:
app: busybox
template:
metadata:
labels:
app: busybox
spec:
hostAliases:
- ip: "250.250.250.250"
hostnames:
- "four-250"
containers:
- name: busybox
image: busybox
args:
- /bin/sh
- -c
- "while true; do echo Hello, Kubernetes!; sleep 10;done"
At this point, when we check the container’s /etc/hosts, we find that Kubernetes has automatically inserted a record Entries added by HostAliases. This is the implementation principle of HostAliases.
A write action is performed in the kubelet_pods code
func hostsEntriesFromHostAliases(hostAliases []v1.HostAlias) []byte {
if len(hostAliases) == 0 {
return []byte{}
}
var buffer bytes.Buffer
buffer.WriteString("\n")
buffer.WriteString("# Entries added by HostAliases.\n")
// for each IP, write all aliases onto single line in hosts file
for _, hostAlias := range hostAliases {
buffer.WriteString(fmt.Sprintf("%s\t%s\n", hostAlias.IP, strings.Join(hostAlias.Hostnames, "\t")))
}
return buffer.Bytes()
}
Coredns Configuration
We can modify the ConfigMap to achieve the purpose of having the container resolve specific domain names.
Change Coredns Configuration
We can modify the Coredns configuration with the following command:
kubectl edit cm coredns -n kube-system
Existing ConfigMap
Corefile: |
.:53 {
log
errors
health {
lameduck 5s
}
ready
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
fallthrough in-addr.arpa ip6.arpa
ttl 30
}
prometheus :9153
hosts {
192.168.65.2 host.minikube.internal
fallthrough
}
forward . /etc/resolv.conf {
max_concurrent 1000
}
cache 30
loop
reload
loadbalance
}
Add specific records in hosts
250.250.250.250 four-250
If you have not configured the reload plugin, you will need to restart Coredns for the changes to take effect. The default reload time is 30 seconds, defined in the defaultInterval of plugin/reload/setup.go.
Custom DNS Policy
By modifying the DNS policy, you can direct the resolution of specific domain names for individual Pods/Deploys/StatefulSets to specific servers, as shown below, where you can add DNS servers and search domains to the pod
spec:
dnsConfig:
nameservers:
- 1.2.3.4
searches:
- search.prefix
containers:
- name: busybox
image: busybox
args:
- /bin/sh
- -c
- "while true; do echo Hello, Kubernetes!; sleep 10;done"
Using Third-Party DNS Plugins
Not recommended, using other DNS plugins for some fancy custom operations. Currently, Coredns is the mainstream in the industry and has no good alternatives.
This article is reproduced from: 「Huawei Cloud Community」, original text: https://url.hi-linux.com/vLxOd, copyright belongs to the original author. Welcome to contribute, submission email: [email protected].

🚀 Recently, we have established a technical exchange WeChat group. Many experts in the industry have already joined. Interested students can join us for technical exchange by replying directly to 「Join Group」 in the 「Wonderful Linux World」 public account.
📕 Follow「Wonderful Linux World」 public account to start an interesting new life! For more useful and fun software resources, visit https://666666.dev for free.
You might also like
Click the image below to read

Practical tips for gracefully shutting down Node, Java, Python, and other application containers in Docker Click the image above, ‘Meituan|Ele.me’ delivery red envelopes are available for free every day
Click the image above, ‘Meituan|Ele.me’ delivery red envelopes are available for free every day

For more interesting fresh news from the internet, follow the 「Wonderful Internet」 video account to learn all about it!