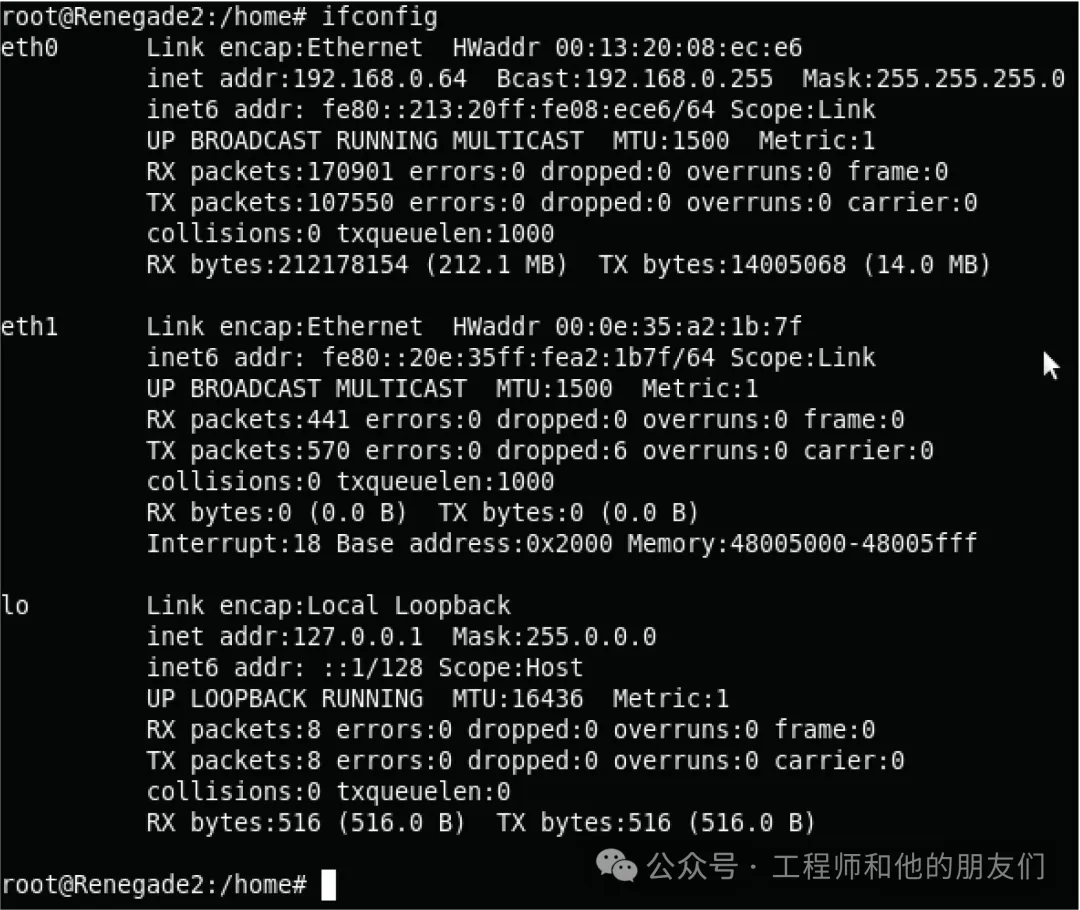
IP Address
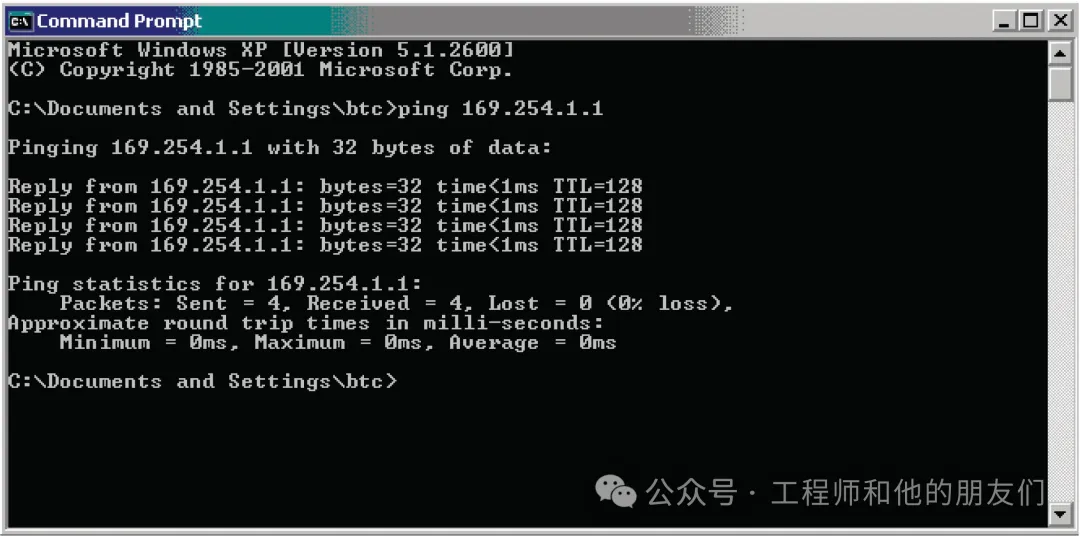
“Ping” Tool
-
The target device is powered on and its IP functionality is working properly -
All network devices (DCE) between your computer and the target device are communicating normally -
All cables used for data communication between the computer and the target device are functioning correctly -
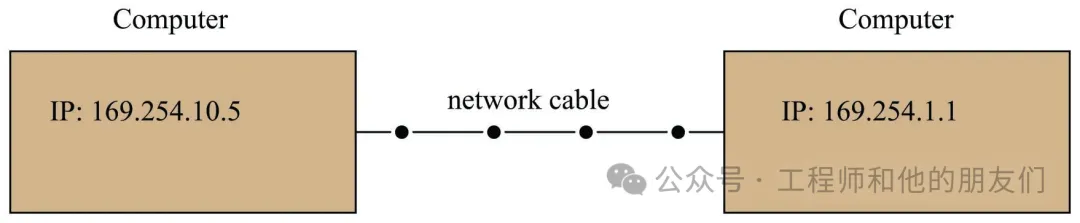
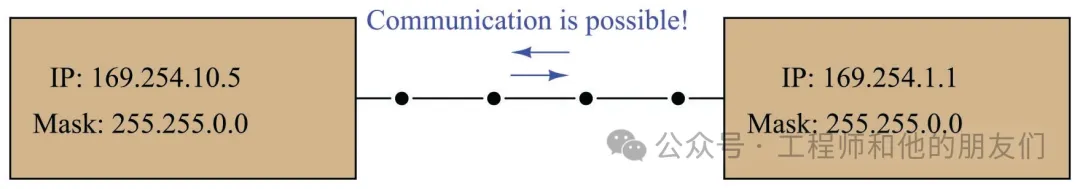
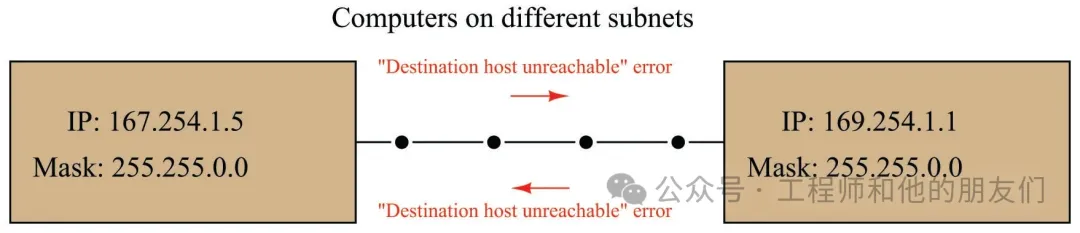
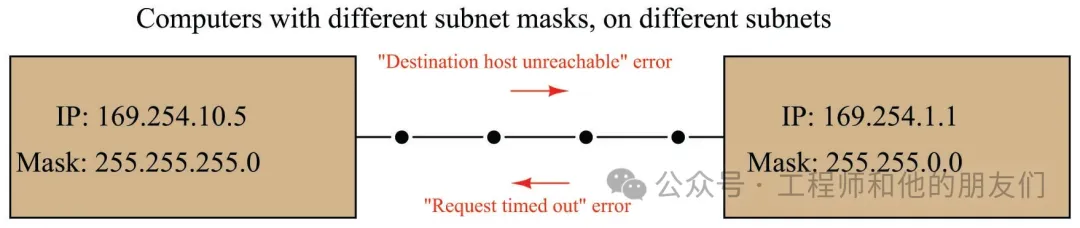
Your computer and the target device are on the same subnet (which we will discuss in detail later)
IPv4 Address Range
-
10.0.0.0 to 10.255.255.255 -
172.16.0.0 to 172.31.255.255 -
192.168.0.0 to 192.168.255.255
Subnets and Subnet Masks
Routing Table
IP Version 6 (IPv6)
ARP
<span>arp -a</span> command will print all (-a) ARP cache entries for you to review. Of course, this will only show what the current computer knows. If the ARP cache has not been recently updated, the address data within it may be outdated or even missing. Below is a partial screenshot of running the <span>arp -a</span> command on a Microsoft Windows computer, showing each IP (“network”) address and its corresponding MAC (“physical”) address in the ARP cache: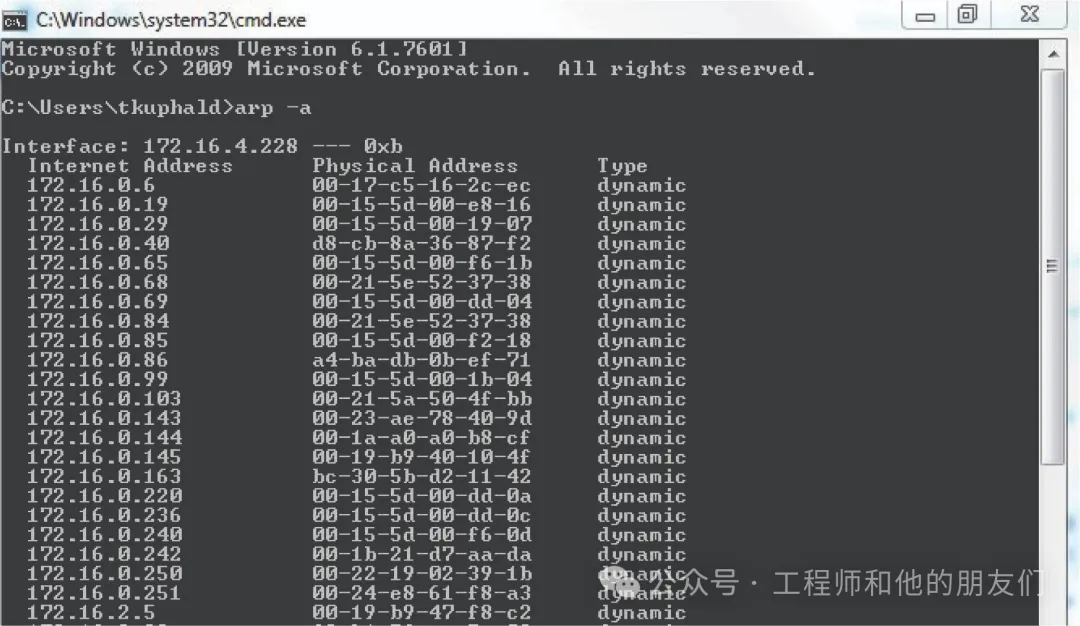
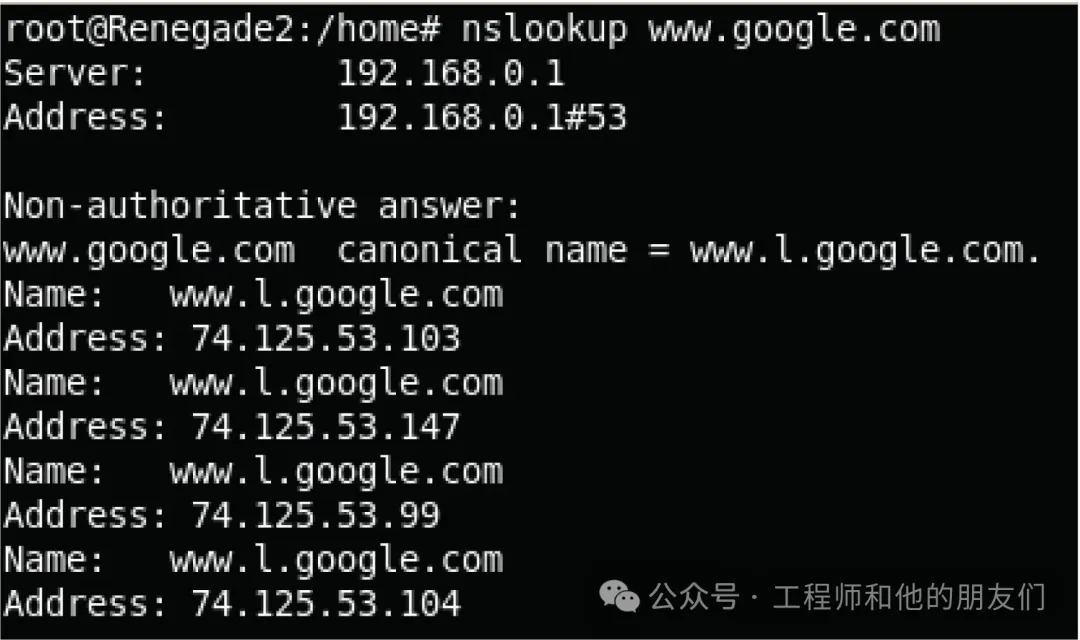
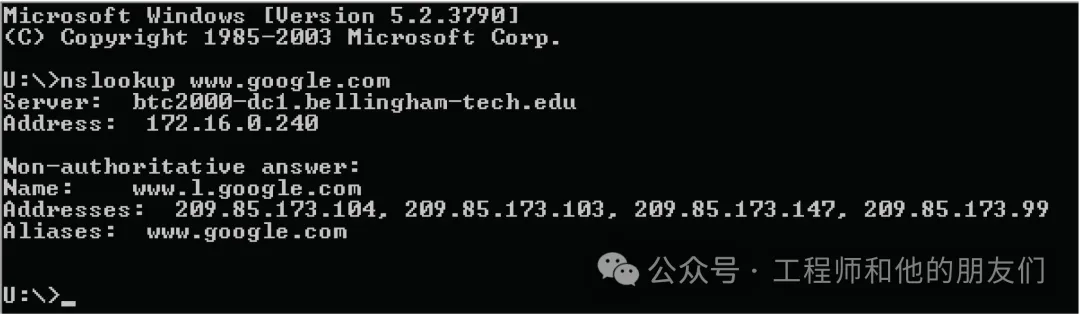
<span>arp -a</span> command to view these cache entries.DNS
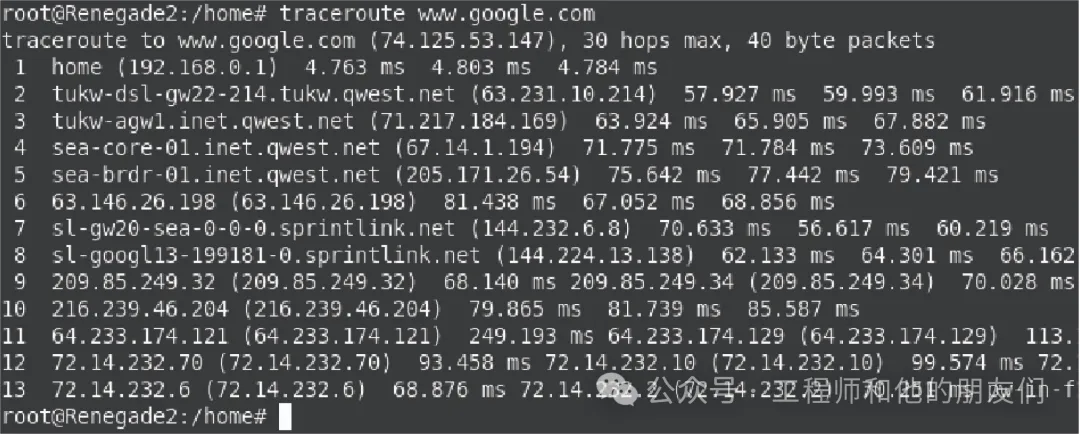
Command Line Diagnostic Tools
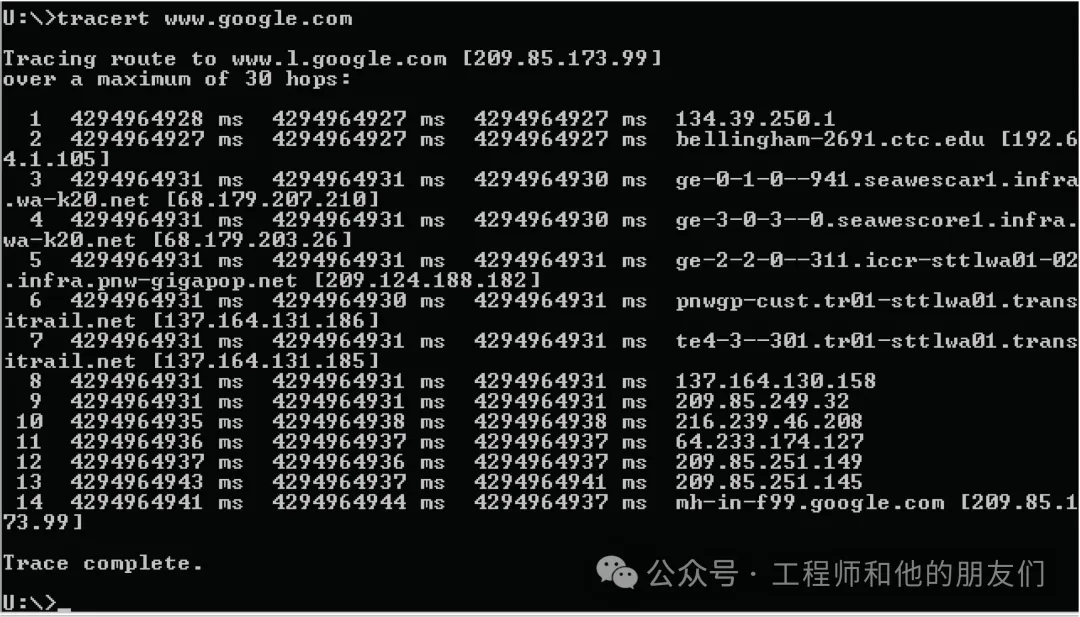
(End)
More Highlights:
Yan Shi│The Impact of Generative AI on Computer Education and Countermeasures
Principal Interview|Rooted in Border Minority Areas, Focusing on Teacher Education to Cultivate High-Quality Applied Talents — Interview with Principal Chen Benhui of Lijiang Normal University
Yan Shi│A Review and Prospect of Computer System Capability Cultivation
Discussion on the Concept of “Student-Centered” Teaching and Its Implementation Path
Principal Interview|Promoting Interdisciplinary Integration to Cultivate Innovative Talents in the New Era — Interview with Professor Ni Mingxuan, Founding President of Hong Kong University of Science and Technology (Guangzhou)
New Year Message from the 7th Editorial Committee
Guidelines for Ideological and Political Teaching in Computer Courses
Academician Chen Guoliang|Cultural Construction of Virtual Teaching and Research Room for Computer Courses in Ideological and Political Education
Professor Chen Daoqu of Nanjing University|Change and Constancy: The Dialectics in the Learning Process
Yan Shi│Reflections and Suggestions on the “Dilemma” of Young Teachers in Colleges and Universities
Xu Xiaofei et al.|Metaverse Education and Its Service Ecosystem
[Directory] Computer Education, Issue 11, 2024
[Directory] Computer Education, Issue 10, 2024
[Directory] Computer Education, Issue 9, 2024
[Directory] Computer Education, Issue 8, 2024
[Editorial Message] Professor Li Xiaoming of Peking University: Reflections from the “Year of Classroom Teaching Improvement”…
Professor Chen Daoqu of Nanjing University: Which is more important, teaching students to ask questions or teaching students to answer questions?
[Yan Shi Series]: Trends in the Development of Computer Disciplines and Their Impact on Computer Education
Professor Li Xiaoming of Peking University: From Fun Math to Fun Algorithms to Fun Programming — A Path for Non-Majors to Experience Computational Thinking?
Reflections on Several Issues in Building a First-Class Computer Discipline
New Engineering and Big Data Major Construction
Lessons from Other Mountains Can Be Used to Attack Jade — A Compilation of Research Articles on Computer Education at Home and Abroad