Continuing from the last time, the principle of device cloud control. Today, I found something good on CoolAPK, shared by the expert Da Nuo Nuo, which is just right as the device in hand has adb available for us to take a look. The so-called Yocto is not pronounced as “yang le duo” but as “yao ke tuo”, abbreviated as “yao”, and also translated as “Yocto-“, which is a prefix in the International System of Units, symbolized by “y”. It represents 10-24 or 0.000000000000000000000001, and was once the smallest unit defined under the International System of Units. This is also the official vision, to fit a sufficiently small Linux into embedded devices.The system has opkg (of course, it is not usable by default, as there are no software sources). We need to log into the system to take a look, and the built-in adb can connect in various ways.
The so-called Yocto is not pronounced as “yang le duo” but as “yao ke tuo”, abbreviated as “yao”, and also translated as “Yocto-“, which is a prefix in the International System of Units, symbolized by “y”. It represents 10-24 or 0.000000000000000000000001, and was once the smallest unit defined under the International System of Units. This is also the official vision, to fit a sufficiently small Linux into embedded devices.The system has opkg (of course, it is not usable by default, as there are no software sources). We need to log into the system to take a look, and the built-in adb can connect in various ways.
adb connect 192.168.1.1:5555adb shellThe IP address is your device’s address, modify it according to your situation.So how is adb started? Let’s take a look at the scripts in /etc/init.d.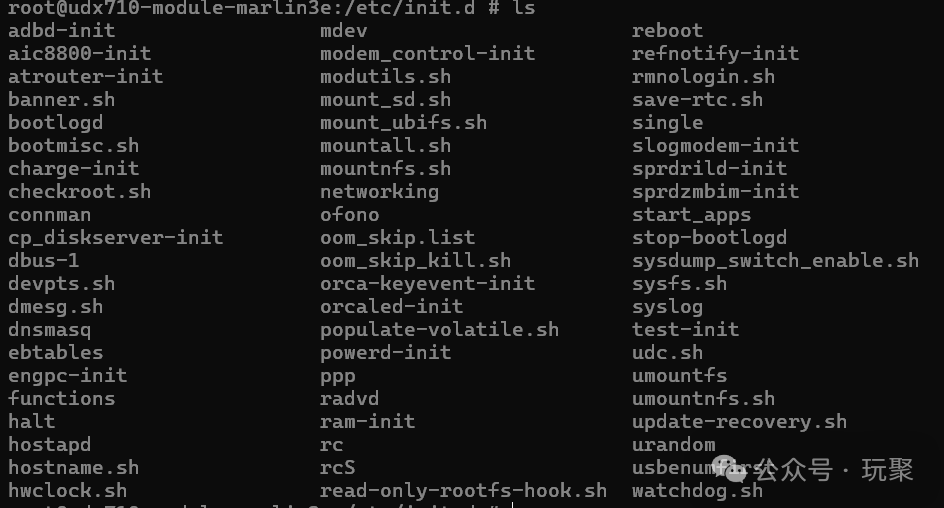 adbd-init is responsible for managing adb.
adbd-init is responsible for managing adb.
#start adb usb#case "$1" in start) echo "Starting adbd..." setprop ro.sprd.debug 1 mount -t configfs none /sys/kernel/config mkdir -p /sys/kernel/config/usb_gadget/g1/functions/ffs.adb mkdir -p /dev/usb-ffs/adb /bin/mount -t functionfs adb /dev/usb-ffs/adb start-stop-daemon --start --background --exec /usr/bin/adbd ;; stop) echo "Stop adbd..." start-stop-daemon --stop --name adbd ;; reload|force-reload) ;; restart) ;; *) echo "Usage: /etc/init.d/adbd {start|stop|reload|restart|force-reload}" exit 1esacexit 0By default, it is not enabled, and many people will add it in/etc/init.d/hostname.sh, as well as other functionalities.
tail -2 /etc/init.d/hostname.shadbd &bash /home/root/loader.sh &Let’s take a look at what loader.sh starts.
/home/root/temp/start.sh &/home/root/busybox-aarch64 crond -b -l 0 -L /tmp/crond.log &/home/root/8080/start.sh &/home/root/fwd/start.sh &/home/root/ttyd/start.sh &Now we are just looking at the files, the things written by the expert later are a bit hard to understand. I will wait until I get the public package of r106 to study further.
However, the new version has some changes. Firstly, the system has a verification (although the verification is not very good, there are ways to bypass it, refer to the public package from Ze Lao, use a hex editor to view the end of the partition or directly search for the keyword loader.sh to find the details), and mounting the system will also cause a reboot. (The verification is personally guessed to be completed in the boot, that is, in the kernel). The verification leads to an inability to change the system, so how to enable adb? It turns out that an expert discovered that directly modifying the web backend configuration file can trigger a shell injection vulnerability, which is the DMZ thing.
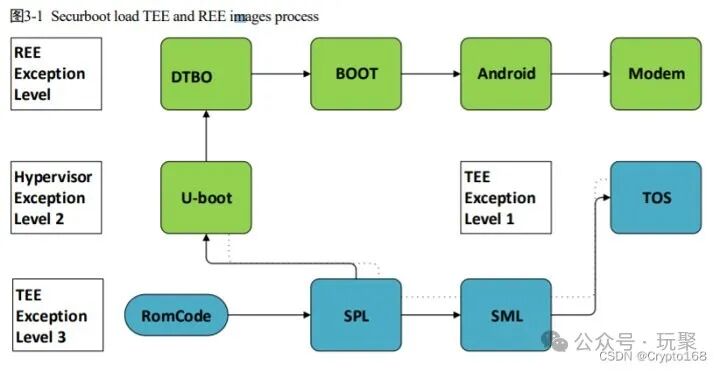
Finally, I will attach the startup flowchart, the image is from CSDN.